Method for multicast transport in Internet protocol secure tunnel and device
An Internet protocol and tunnel technology, applied in the field of data communication, can solve the problem of wasting actual bandwidth and encryption resources, GRE tunnel does not support dynamic IP address, adding and other problems, to avoid data traffic and waste of resources, simplify the configuration of ACL rules Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
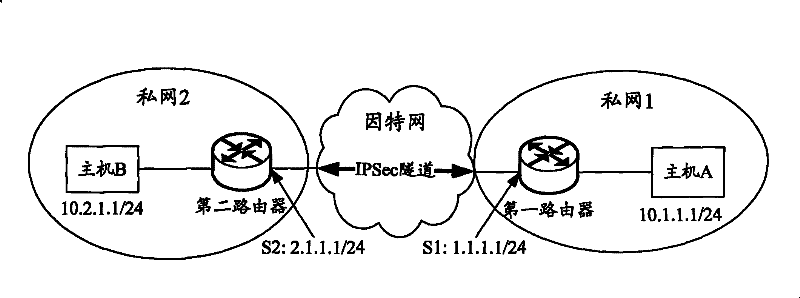
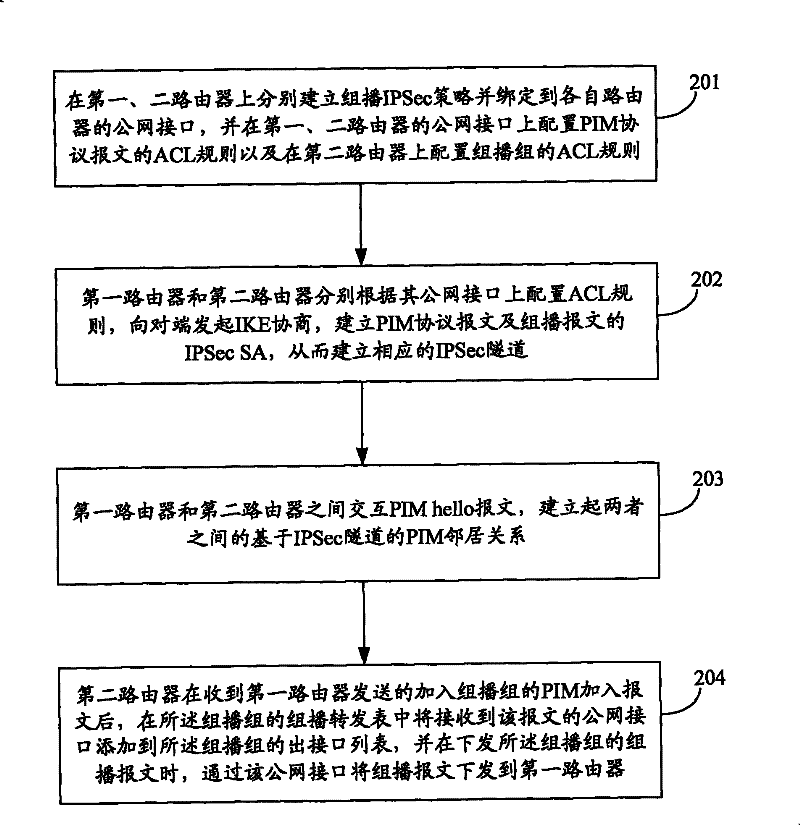
[0047] First of all, it needs to be explained that the ACL rules mentioned in the present invention specifically refer to the ACL rules used for IPSec. In the present invention, IPsec uses the ACL rules to determine which data needs to be encrypted. Packets that match the ACL rule (permit) will be encrypted by IPSec, and packets that do not match the ACL rule (deny) will not be encrypted. Moreover, in order to decrypt data encrypted at one end at the opposite end, it is required that the ACL rules configured on the local and remote routers correspond to each other (that is, they are mirror images of each other).
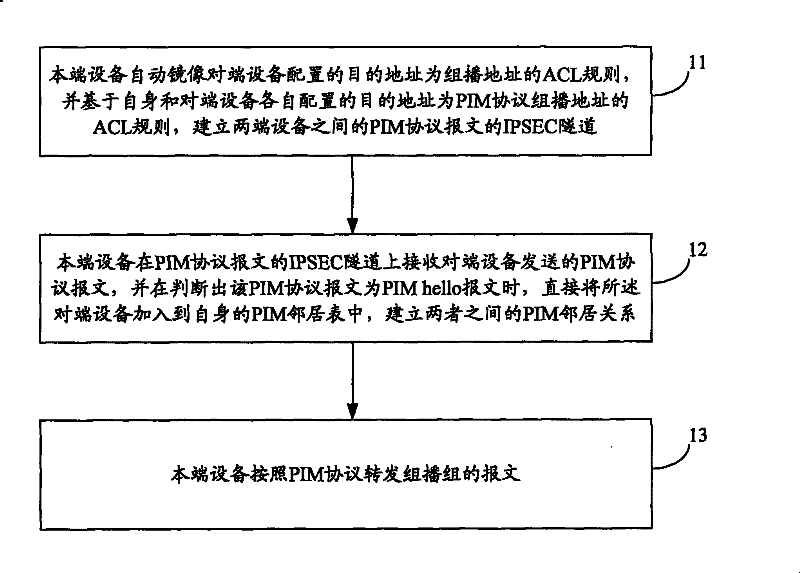
[0048] In the embodiment of the present invention, the existing PIM protocol is modified and improved, and the PIM neighbor relationship based on the IPSec tunnel is added to the PIM neighbor relationship, and the IPSec node device can exchange PIM hello messages through the IPSec tunnel to establish an IPSec tunnel The PIM neighbor relationship enables the two priva...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com