Verification method and verification device
A verification method and a verification device technology, applied in the direction of electrical components, transmission systems, etc., can solve problems that affect system performance, session information cannot be shared, and achieve the effect of protecting interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] Hereinafter, referring to the preferred embodiments of the present invention in detail, examples of the preferred embodiments will be described based on the accompanying drawings.
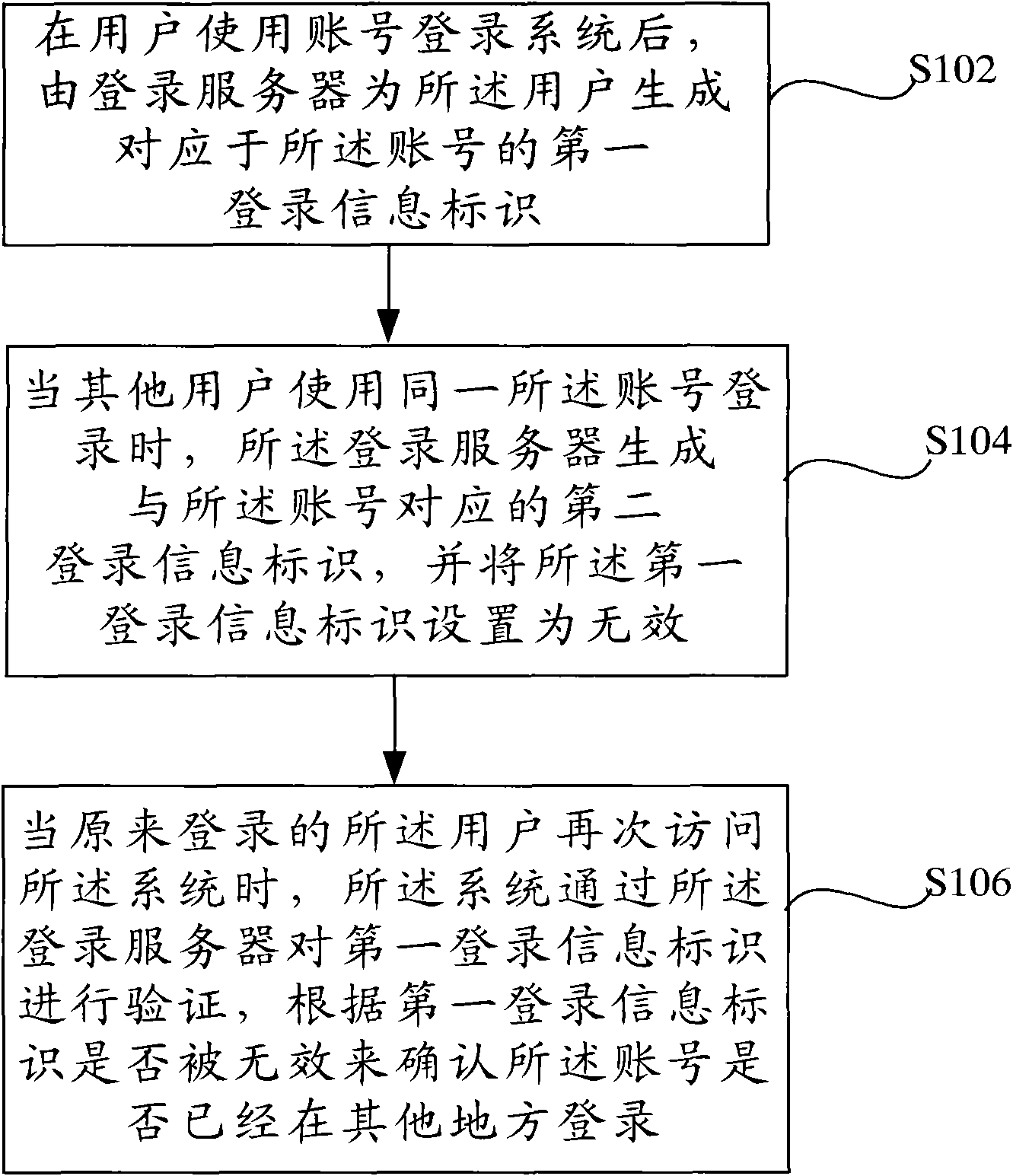
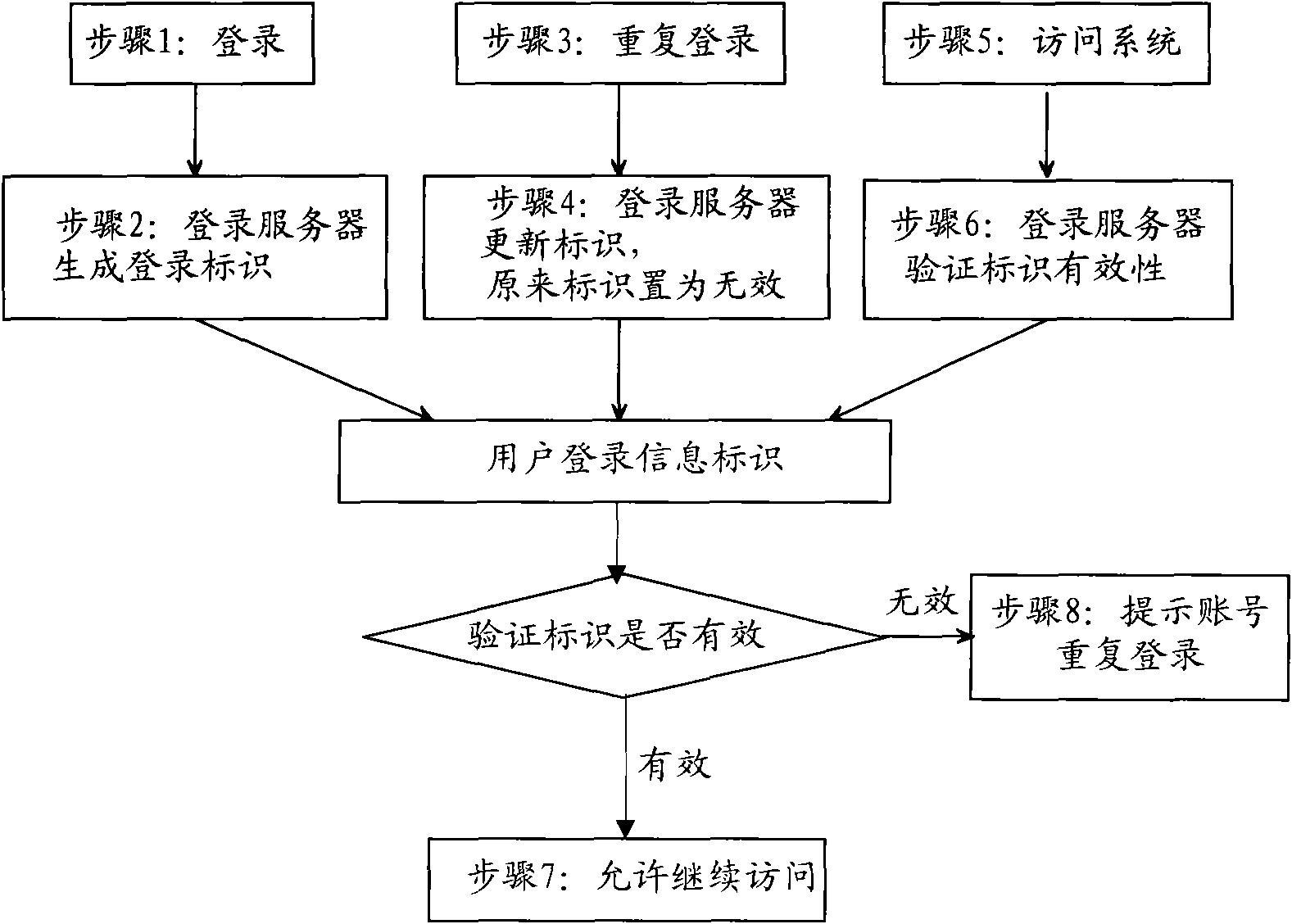
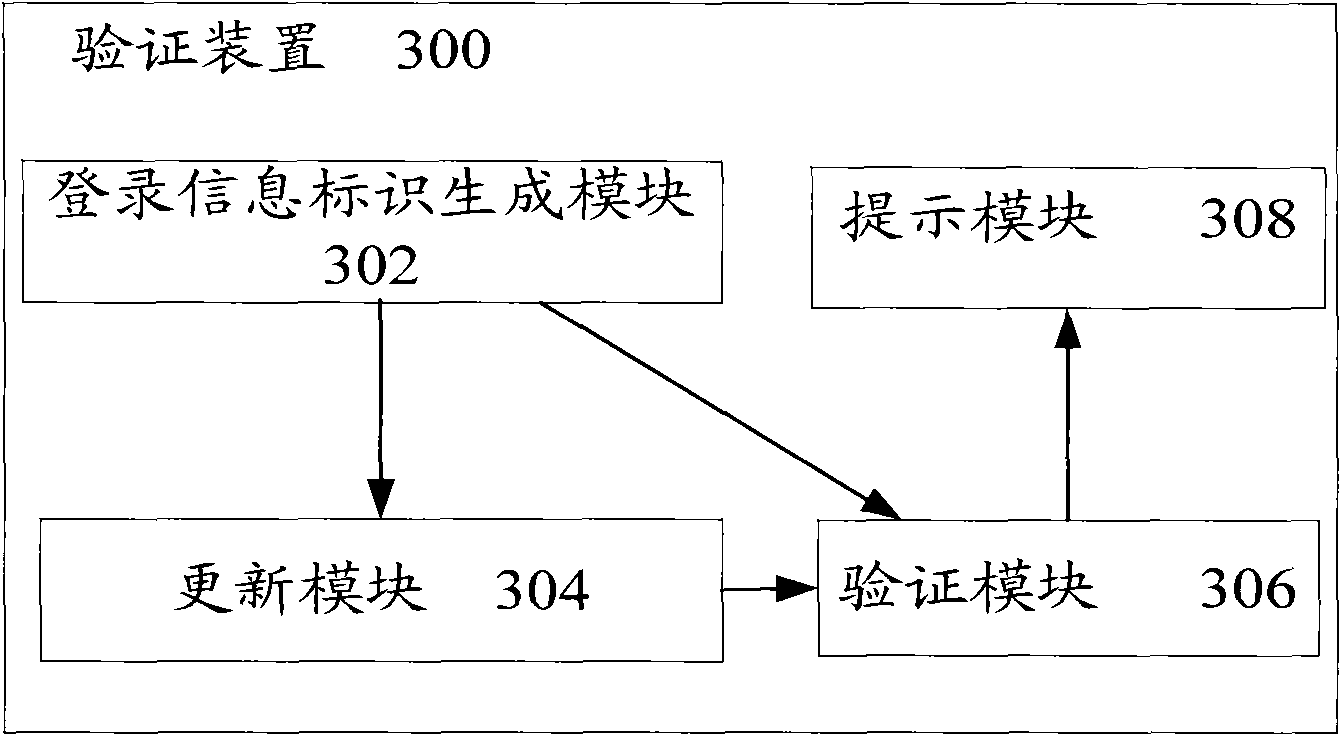
[0022] figure 1 It is a flowchart of the verification method according to the present invention. Such as figure 1 As shown, the verification method for restricting repeated logins of the same user name in multiple applications in the B / S architecture according to the present invention includes: step S102, after the user logs in to the system using the account, the login server serves the user Generate a first login information identifier corresponding to the account; step S104, when other users log in using the same account, the login server generates a second login information identifier corresponding to the account, and sends the first login information The identifier is set to be invalid; and step S106, when the originally logged-in user accesses the system again, the system verifies the l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com