Unsupervised anomaly detection method and system based on improved CURE clustering algorithm
A clustering algorithm and anomaly detection technology, applied in transmission systems, calculations, computer components, etc., can solve problems such as models not being updated, unsatisfactory normal behavior models, and time-consuming problems, and achieve rapid and accurate judgments
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] Such as Figure 1-Figure 4 As shown, the unsupervised anomaly detection method based on the improved CURE clustering algorithm of the present invention comprises steps:
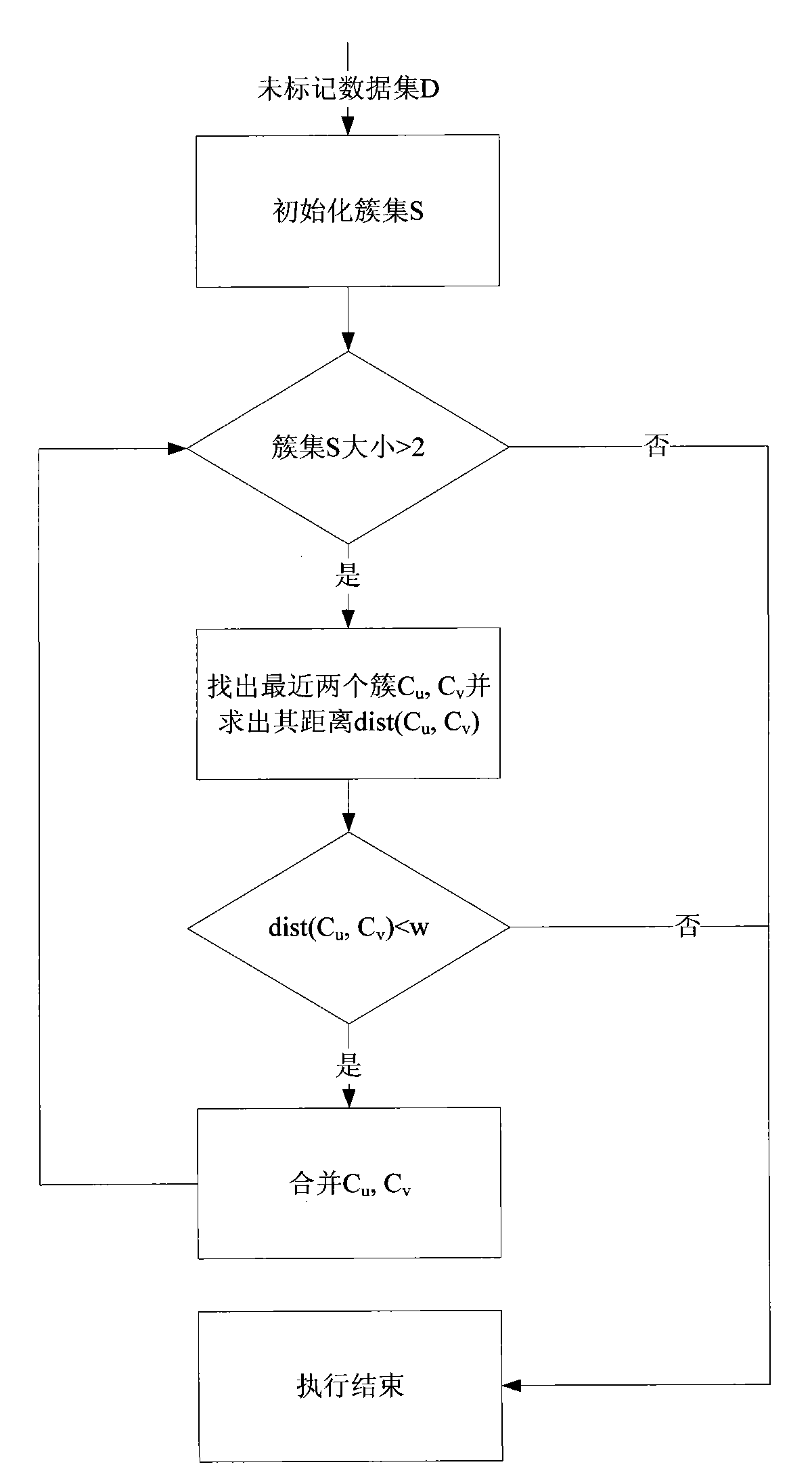
[0027] A: Use the improved CURE clustering algorithm to cluster the training set, classify abnormal behavior data and normal behavior data, and generate clusters;
[0028] B: Mark the clusters according to the percentage of normal data estimated in advance in the entire data set;
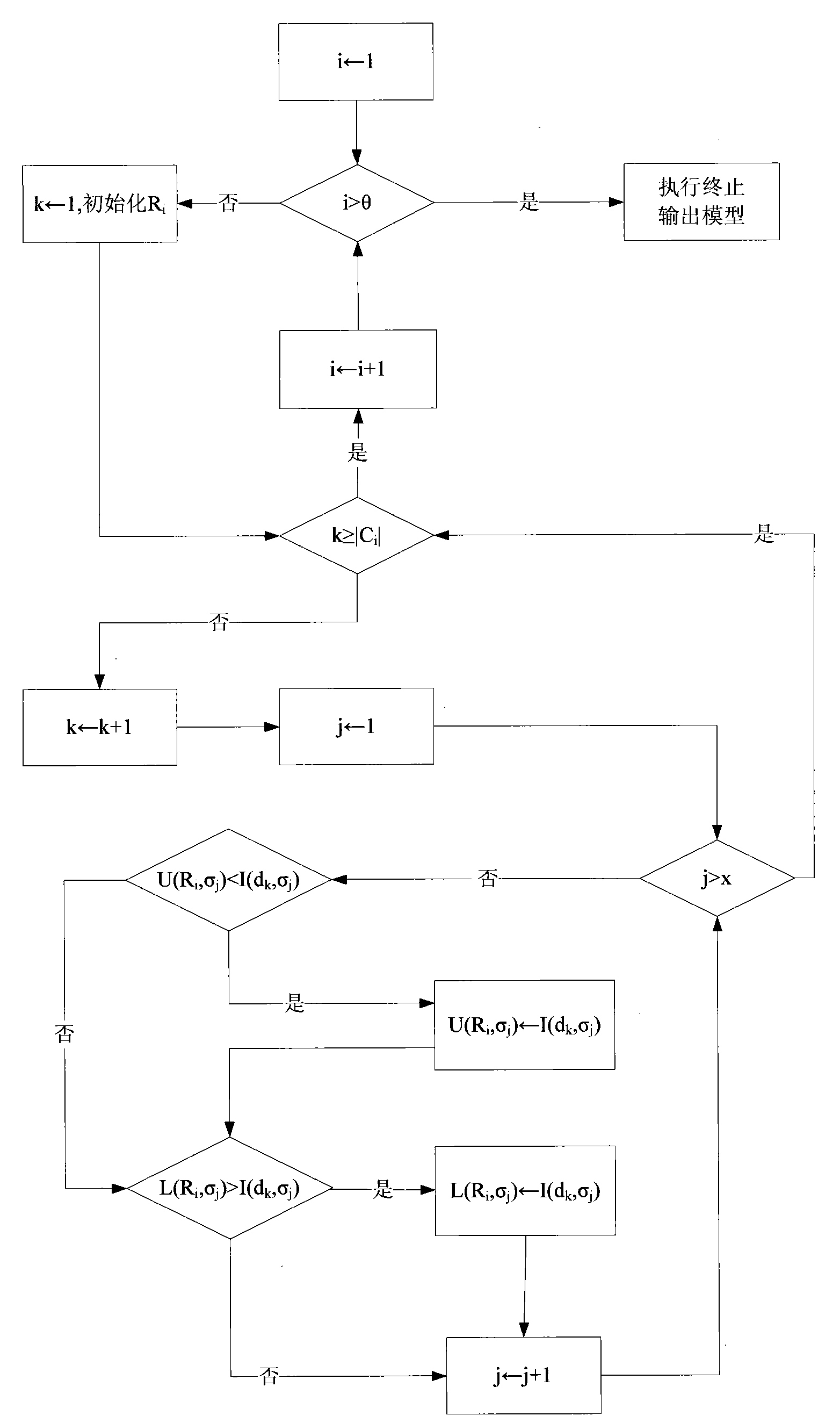
[0029] C: Modeling is based on clusters marked as normal behavior, and its modeling algorithm is a hyperrectangle-based modeling algorithm;
[0030] D: Compare the data to be detected with the normal behavior model to determine whether it is abnormal data.
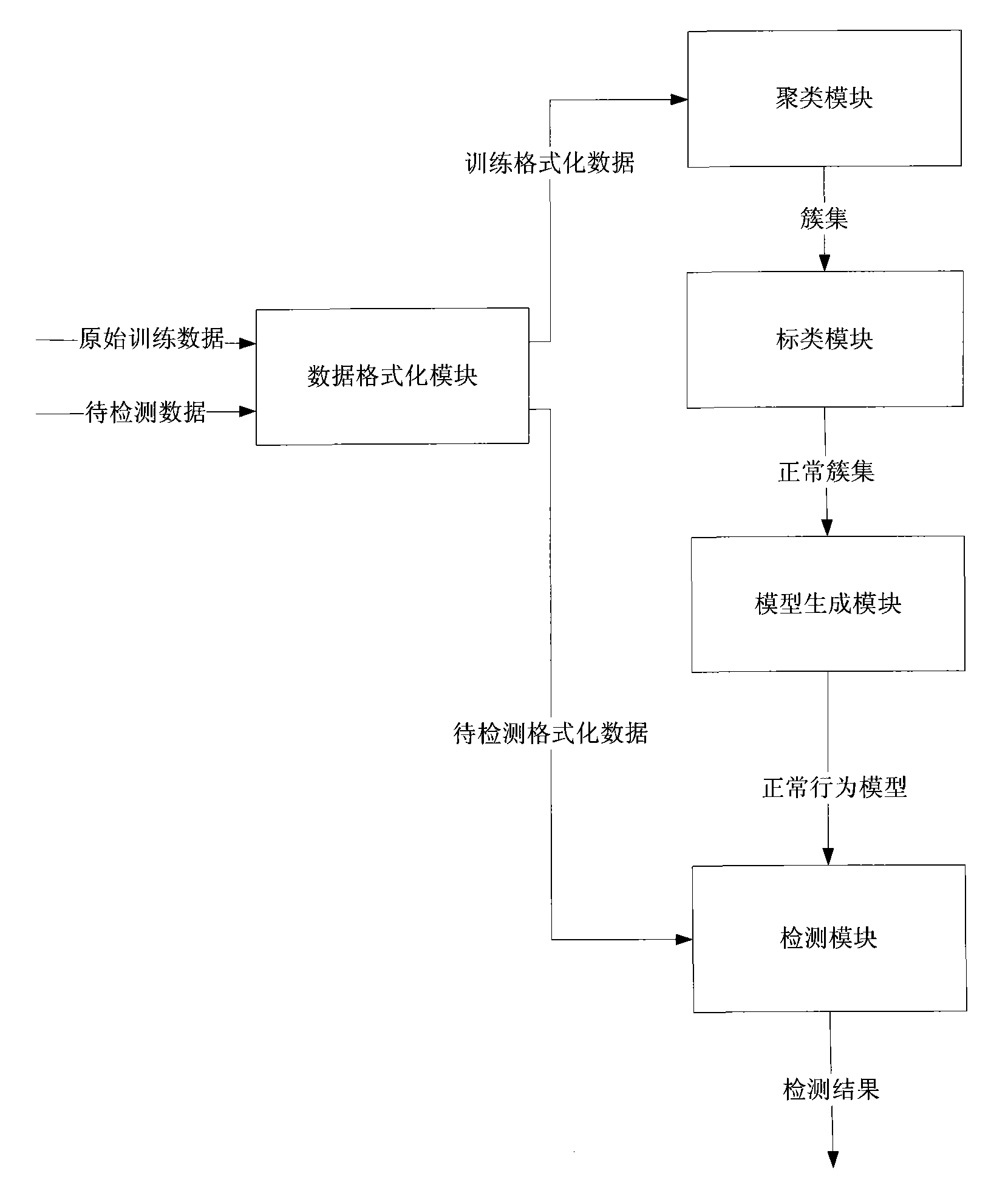
[0031] The anomaly detection system according to the present invention includes a data formatting module, a clustering module, a labeling module, a model generation module and a detection module.
[0032] The data formatting module generates formatted data by preproce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com