Method and device for detecting structured query language injection attack
A structured query and injection attack technology, applied in the field of network communication, can solve the problems of many false negatives, difficult to find SQL injection vulnerabilities, unable to hit SQL attack features, etc., to achieve the effect of reducing false negatives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
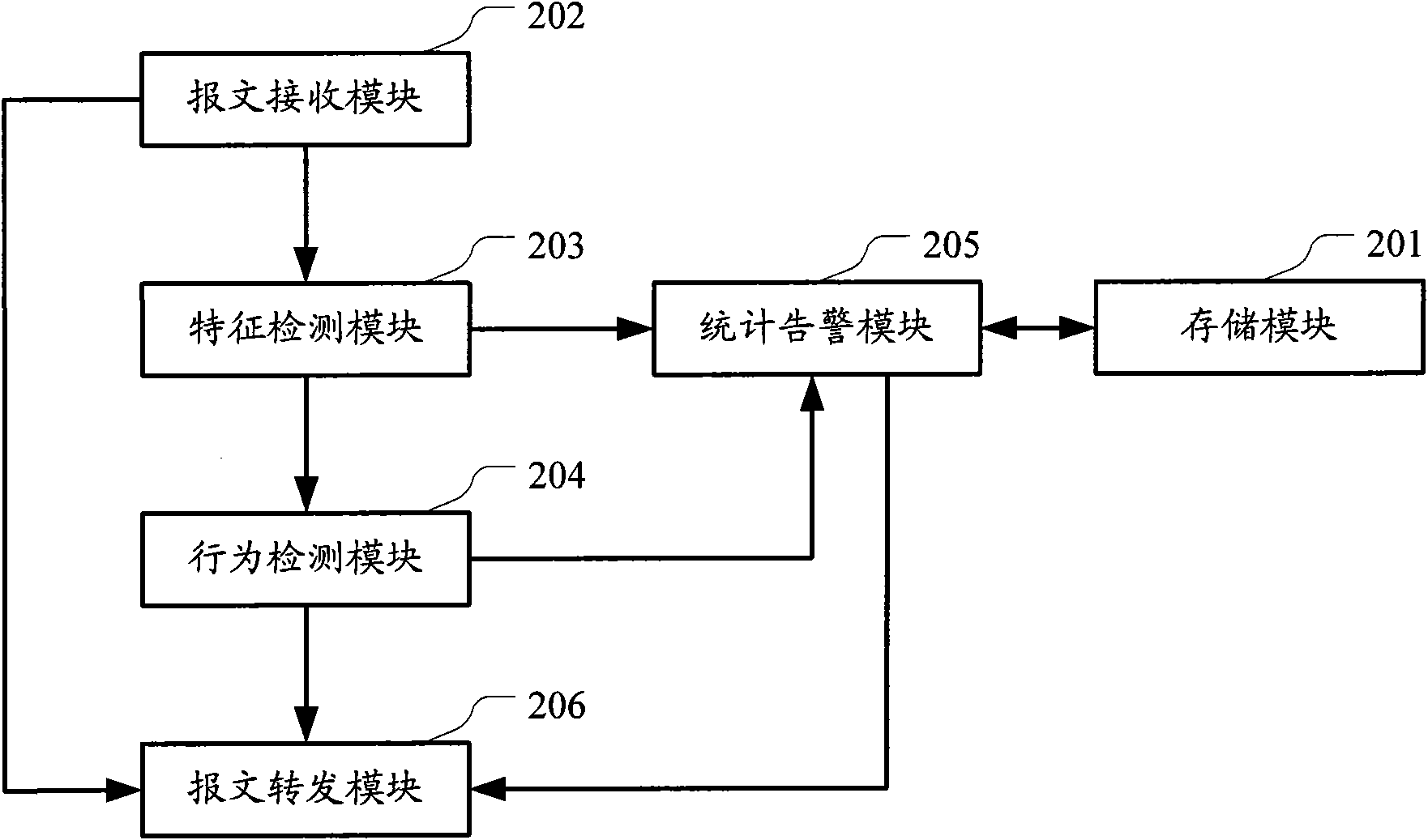
Image
Examples
Embodiment Construction
[0029] Therefore, the core idea of the present invention is to detect whether there is an SQL injection attack in the message in the network by using a combination of feature detection and behavior detection.
[0030] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below.
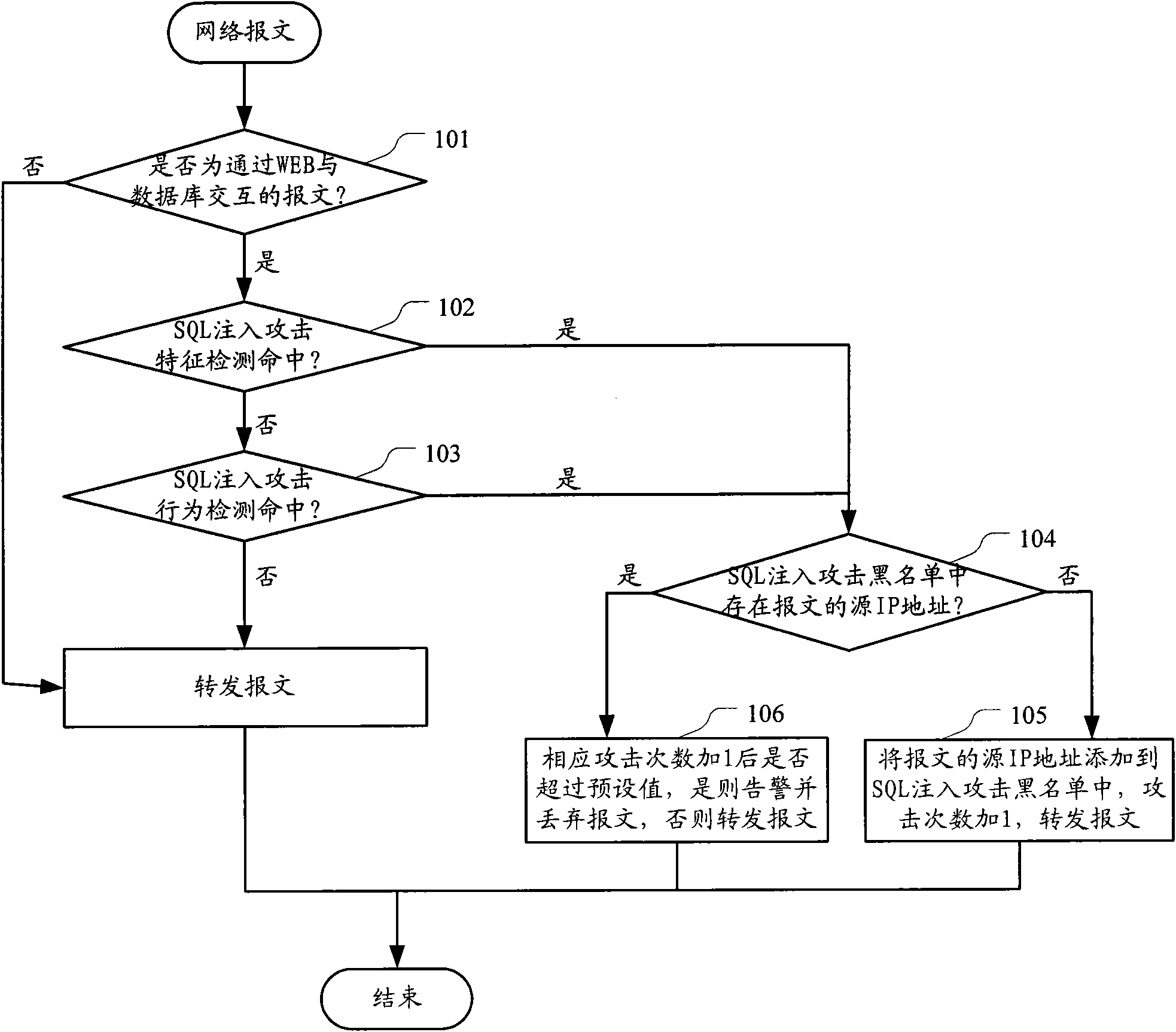
[0031] figure 1 It is a flowchart of an SQL injection attack detection method according to an embodiment of the present invention. This method is implemented in the IPS device. First, a SQL injection attack blacklist is established to record the attacker's IP address and the number of attacks. Then, for the network message received by the IPS device, the following steps are executed: figure 1 The following steps are shown:
[0032] Step 101, detecting whether the received message is a message interacting with the database through the World Wide Web WEB, if yes, execute step 102, otherwise, directly...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com