SQL injection detection method based on convolution neural network algorithm
A convolutional neural network and detection method technology, applied in the field of SQL injection detection, can solve the problems of low detection rate of mutation attack and low recognition rate of mutation attack, and achieve the effect of high recognition rate and reduced impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
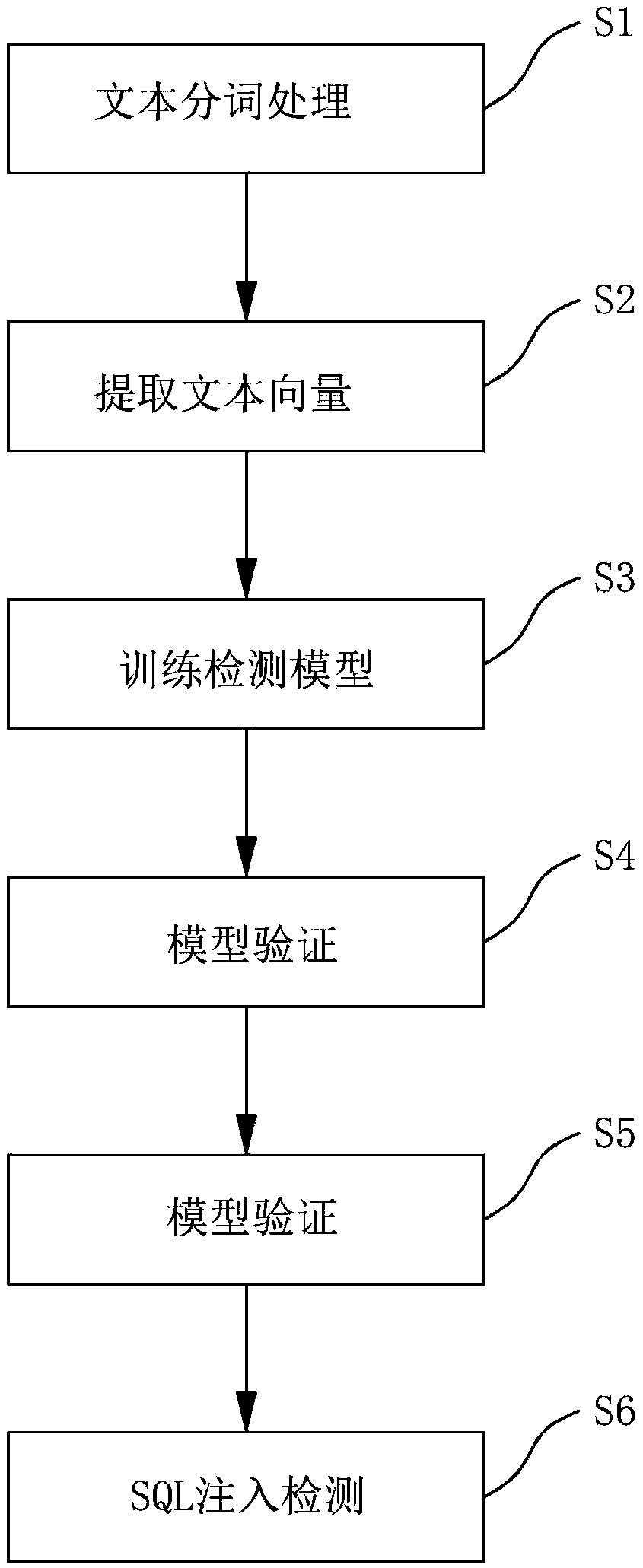
[0035] Such as figure 1 As shown, the present invention discloses a SQL injection detection method based on a convolutional neural network algorithm, including:
[0036] Step 1, text word segmentation processing, which includes:
[0037] Step 1-1. Perform URL decoding on the collected training samples; when the browser sends data to the server, the client will package and encode the parameters input by the user before sending them to the server, so the collected training samples are often encoded For processing, decoding is required before training, and the recursive URL decoding method is used to parse the training samples with multiple URL encodings to ensure the consistency of data encoding.
[0038] Step 1-2, normalize the decoded data, which specifically includes: replacing the number in the URL with '0'; replacing the hyperlink in the URL with the form of 'http: / / u'; Unified and standardized processing to reduce the number of word segmentation after word segmentation. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com