Signing method and system thereof
An algorithm and client-side technology, applied in the field of information security, can solve problems such as damage to users' legitimate interests, and achieve the effect of increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0088] This embodiment provides a signature method. In this embodiment, the online transaction process between the client computer (referred to as the client) and the server computer (referred to as the server) by the user using online banking is taken as an example. The USB Key connected to the client uses the method provided by the embodiment of the present invention to sign the transaction data involved in the process, so as to improve the security of network data transmission. Wherein, it is assumed that the client has pre-installed the online banking control corresponding to the used online banking, and the USB Key software used in conjunction with the USB Key. In this embodiment, preferably, a hash algorithm is used when calculating the digest during the signature process. see figure 1 , the method includes:
[0089] Step 101: When the user conducts an online transaction, the user initiates an online transaction through the client computer and receives a transaction me...
Embodiment 2
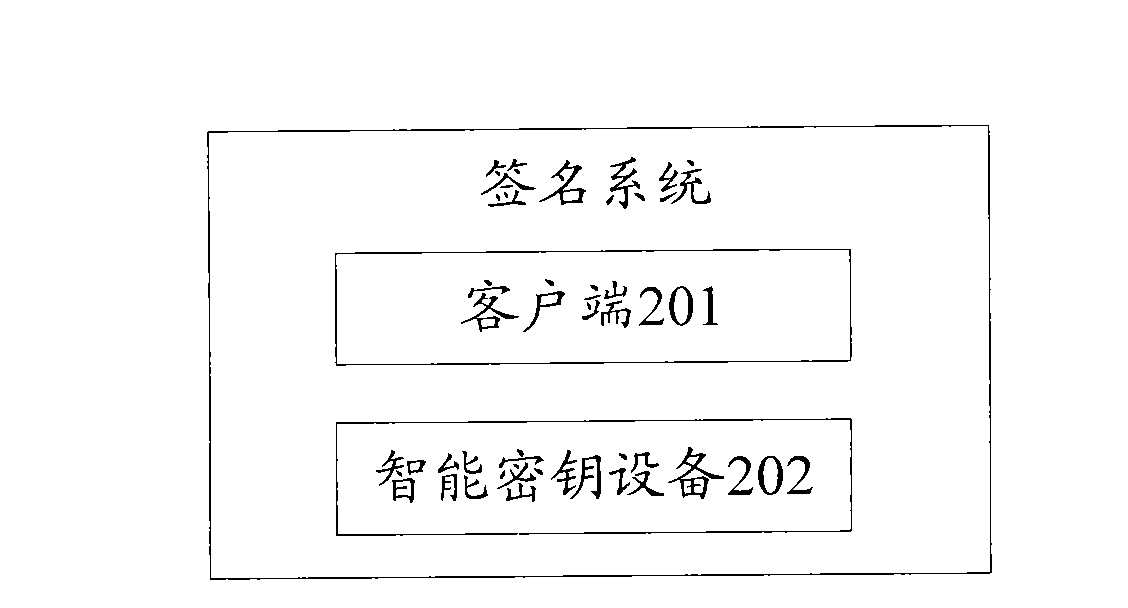
[0154] Referring to the description of method implementation in Embodiment 1, this embodiment provides a signature system, see figure 2 , the system includes: a client 201 and a smart key device 202 connected to the client 201 .
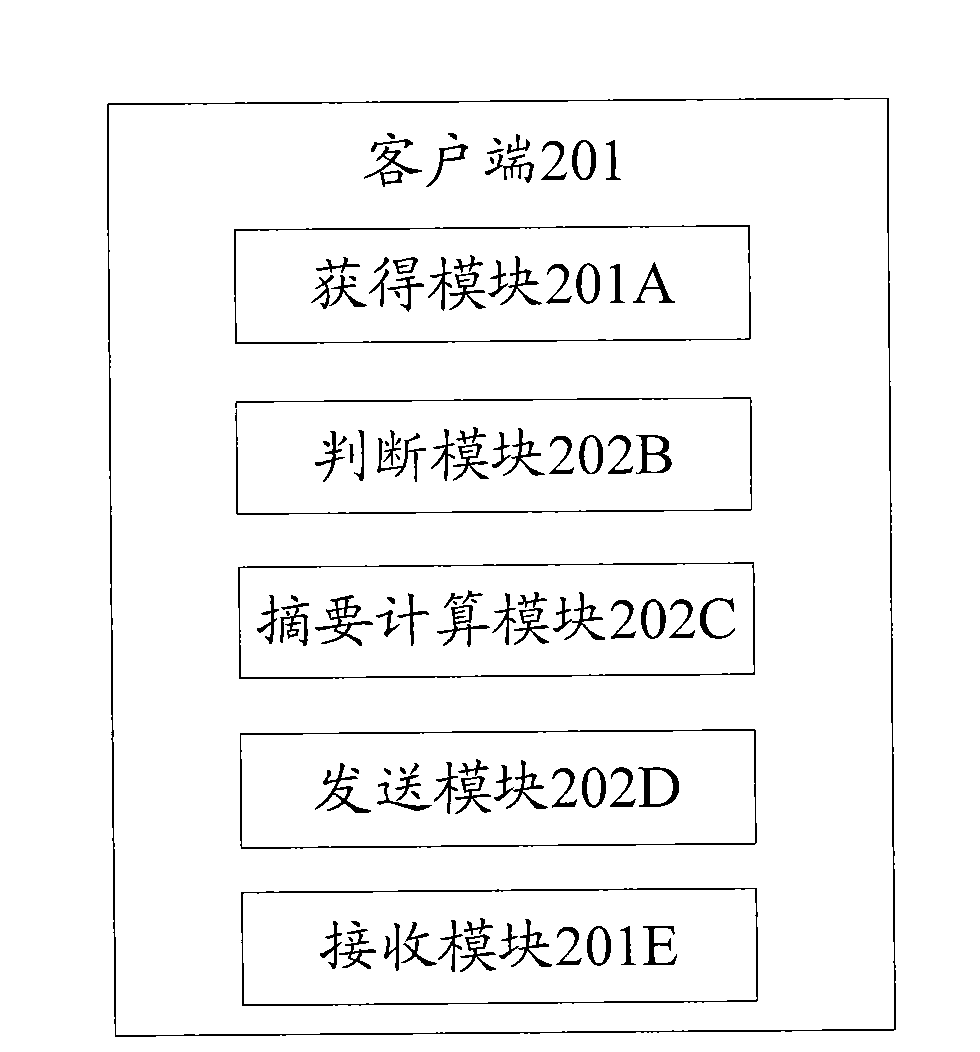
[0155] see image 3 , client 201 includes:
[0156] Obtaining module 201A, used to obtain the signature original package;
[0157] Judging module 201B, for judging whether there is second information in the signature original package;
[0158] A digest calculation module 201C, configured to calculate a digest for the first information to obtain a first digest value when the second information exists;
[0159] A sending module 201D, configured to send the second information and the first digest value to the smart key device;
[0160] The receiving module 201E is used to receive the signature result sent by the smart key device;
[0161] see Figure 4 , the smart key device 202 includes:
[0162] A receiving module 202A, configured to receive t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com