Method and system for enhancing security of network transactions
A network transaction and security technology, applied in transmission systems, commerce, instruments, etc., can solve problems such as illegal tampering, loss, and theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
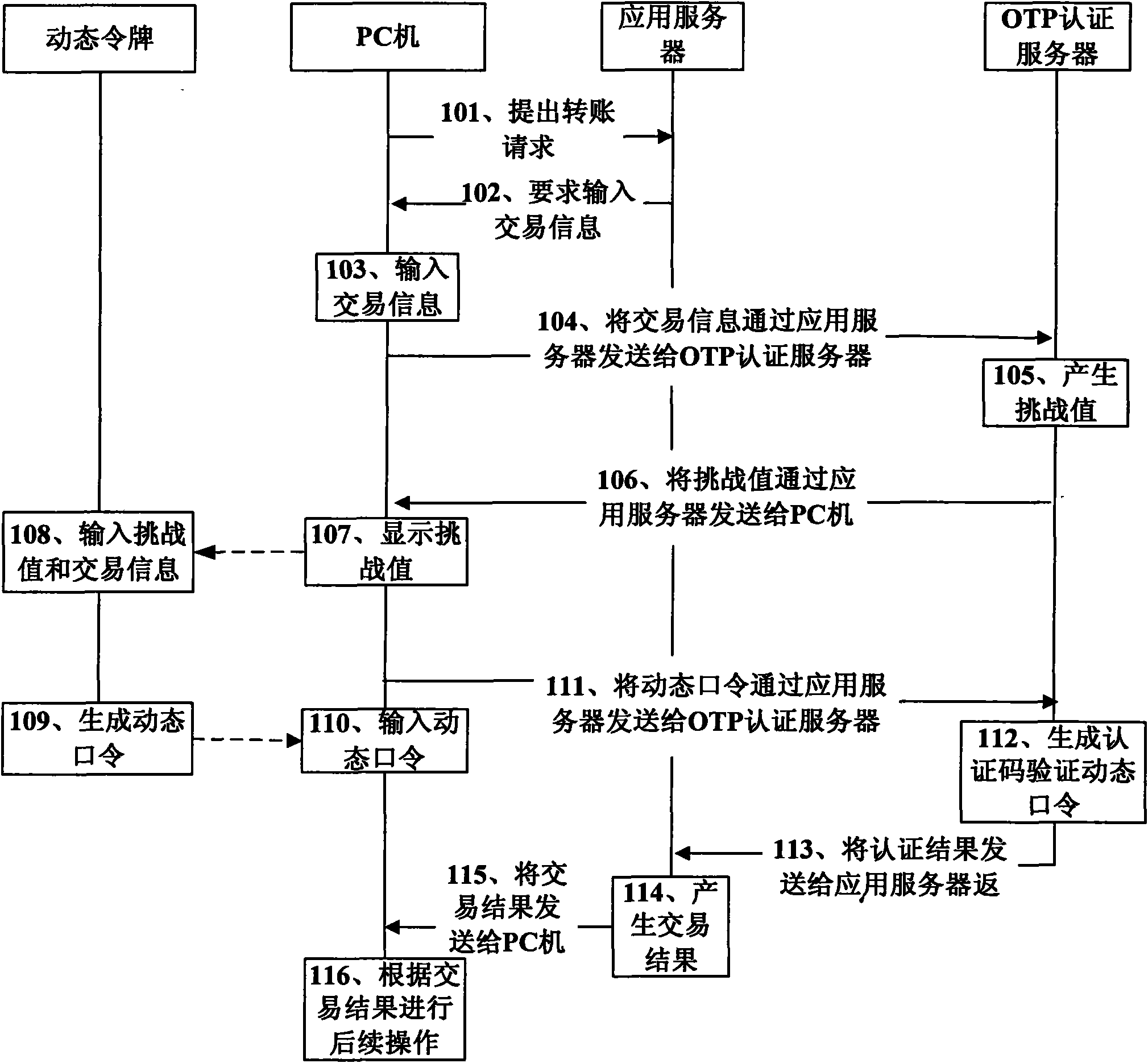
[0164] This embodiment provides a method for improving the security of network transactions, including:
[0165] The client sends a service request to the first server, and sends the first information input by the user to the second server through the first server, and the information of the security device is pre-registered in the second server;
[0166] After receiving the first information, the second server generates second information according to a preset algorithm, and returns the second information to the client through the first server, and the client provides the second information to the user;
[0167] The safety device receives the first information and the second information input by the user, generates an intermediate value according to the first information and the second information, and processes the intermediate value to generate third information and provide it to the user;
[0168] The client receives the third information input by the user, and sends the t...
Embodiment 2
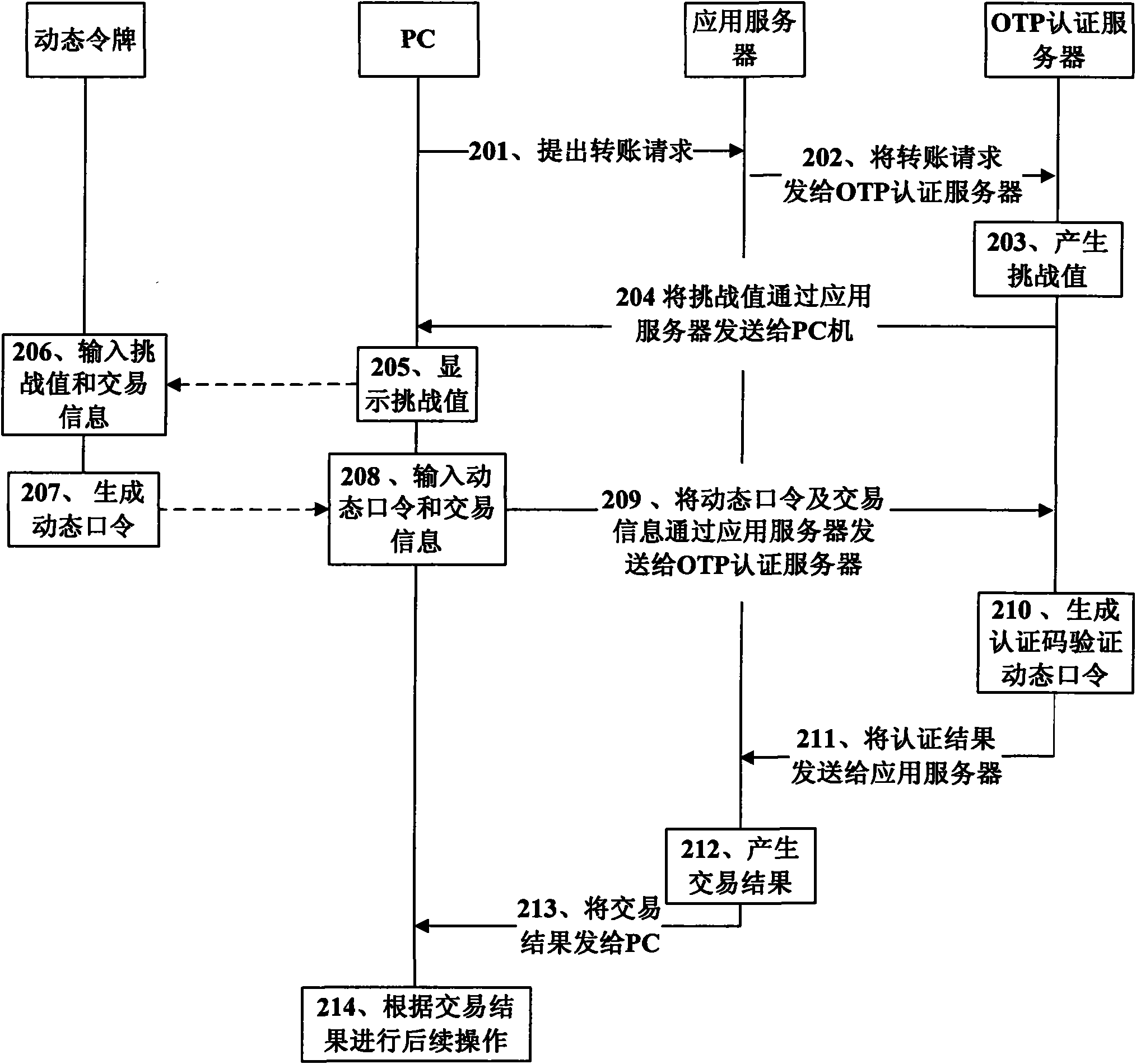
[0239] This embodiment provides a method for improving the security of network transactions, including:
[0240] The client sends a service request to the first server, and the first server forwards the service request to the second server, and the information of the security device is pre-registered in the second server;
[0241] After receiving the service request, the second server generates second information according to a preset algorithm, and returns the second information to the client through the first server, and the client provides the second information to the user;
[0242] The safety device receives the first information and the second information input by the user, generates an intermediate value according to the first information and the second information, and processes the intermediate value to generate third information and provide it to the user;
[0243] The client receives the third information and the first information input by the user, and sends the th...
Embodiment 3
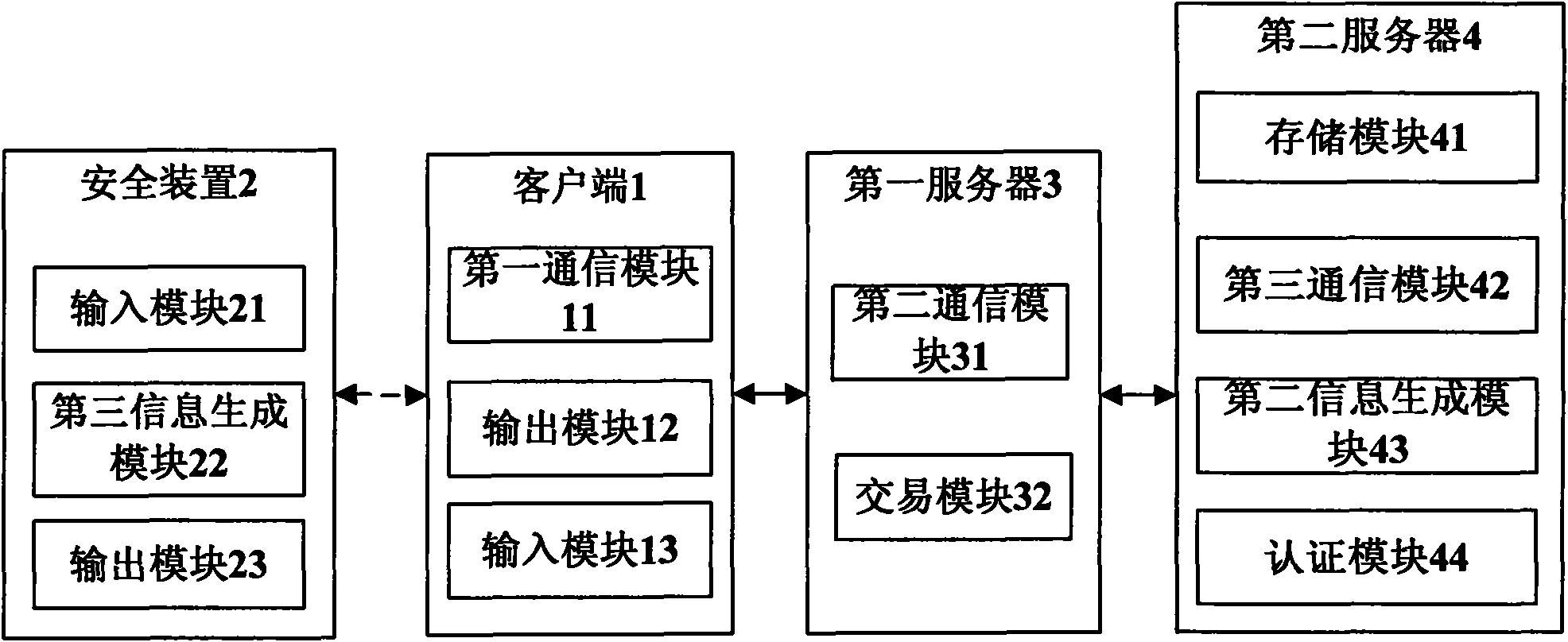
[0263] see image 3 , the present embodiment provides a system for improving the security of network transactions, including: a client 1, a security device 2, a first server 3 and a second server 4;
[0264] Client 1 includes:
[0265] The first communication module 11 is configured to send a service request to the first server, send the first information input by the user to the first server, receive the second information returned by the first server, and send it after the user inputs the third information To the first server, receive the transaction result returned by the first server;
[0266] An output module 12, configured to provide the second information received by the first communication module to the user;
[0267] The input module 13 is configured to receive the first information and the third information input by the user;
[0268] Safety device 2 includes:
[0269] An input module 21, configured to receive first information and second information input by a u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com