Virus killing method and virus killing system with multiple antivirus engines
A virus-killing engine and anti-virus technology, which is applied in the anti-virus method and system field of multiple anti-virus engines, can solve the problems of inability to detect and kill viruses, file size limitations, and infectivity, and achieve the effect of high-speed multi-anti-virus engine killing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
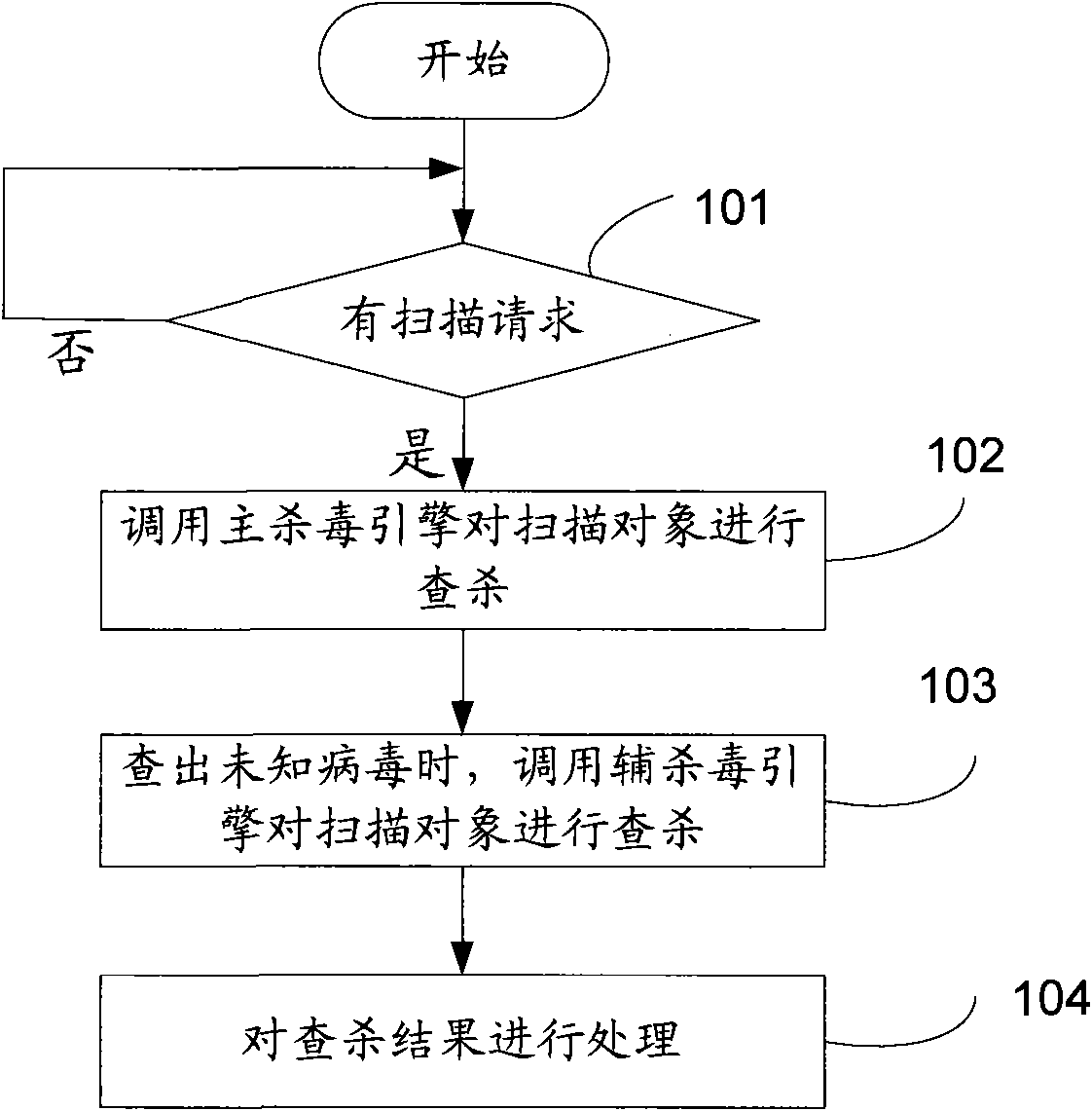
[0056] Embodiment one, see figure 1 , the antivirus method provided by the embodiment of the present invention, comprises the following steps:
[0057]Step 101: Detect whether there is a virus scanning command, if there is the virus scanning command, go to step 102, otherwise continue to detect.
[0058] Step 102: according to the virus scanning command, invoke the main antivirus engine of at least two antivirus engines to scan and kill the object required to be scanned by the virus scanning command.
[0059] Step 103: When the virus detected by the main antivirus engine is an unknown virus, invoke the auxiliary antivirus engine of the at least two antivirus engines to scan and kill at least one object required to be scanned by the virus scanning command.
[0060] In the embodiment of the present invention, the main anti-virus engine is the anti-virus engine with the highest detection and killing rate among the many local anti-virus engines, and all engines except the main an...
Embodiment 2
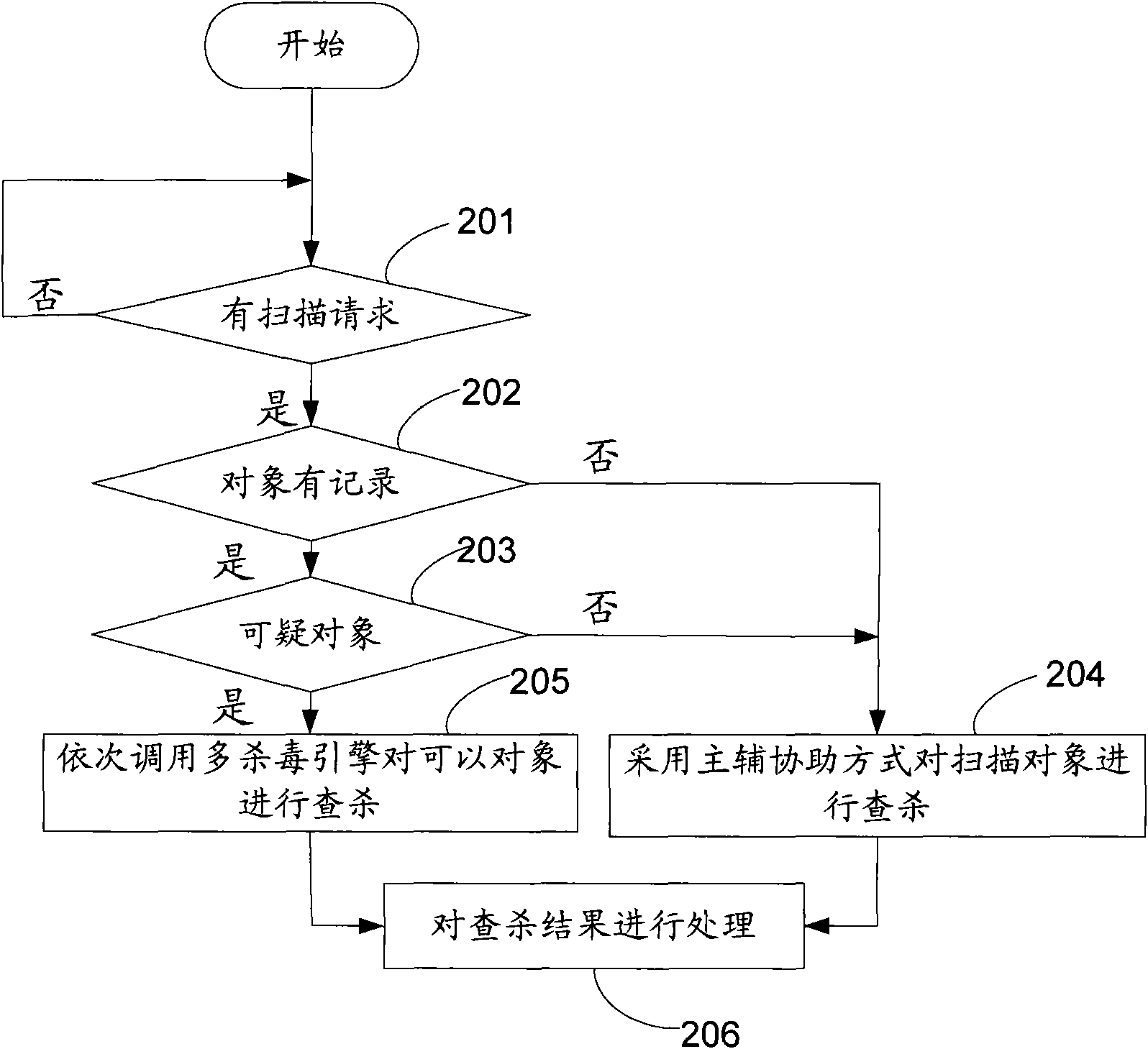
[0067] Embodiment 2. In practical applications, different methods may be used to scan the object required to be scanned according to the suspiciousness of the object required to be scanned by the virus scanning command. See figure 2 , the method specifically includes:
[0068] Step 201: Detect whether there is a virus scanning command, if so, go to step 202, otherwise go back to step 201 to continue detection.
[0069] Step 202: Determine whether the scanned object required by the virus scanning command has a record of being infected by a virus, if not, go to step 204; otherwise, go to step 203.
[0070] Step 203: Determine whether the object is a suspicious object, if not, go to step 204; if yes, go to step 205.
[0071] The suspicious object refers to an object whose virus infection rate is higher than a preset threshold.
[0072] Wherein, in step 202, it is judged whether the object that the virus scanning command requires to scan is a possible object is specifically:
...
Embodiment 3
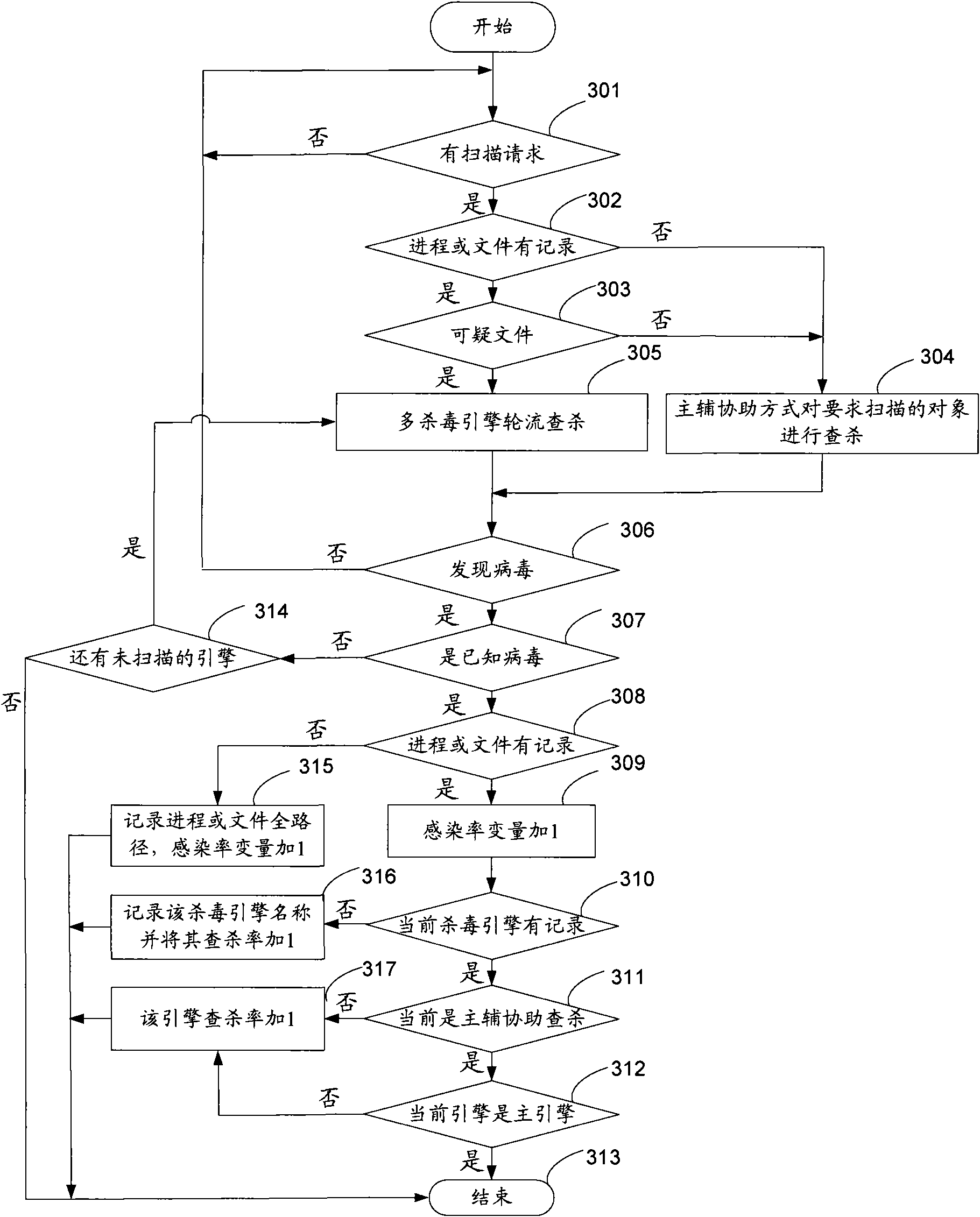
[0083] Embodiment three, see image 3 , the antivirus method that realizes many antivirus engines that this embodiment provides comprises:
[0084] Step 301: Detect whether there is a virus scanning command. If there is the virus scanning command, go to step 302; otherwise, return to step 301 to continue detection.
[0085] Step 302: Determine whether the object scanned by the virus scanning command has a virus infection record, if not, go to step 304; otherwise, go to step 303.
[0086] Step 303: Determine whether the object is a suspicious object, if not, go to step 304; if yes, go to step 305.
[0087] Step 304: The master and assistant assist in scanning and killing the object required to be scanned, and proceed to step 306.
[0088] Step 305: Invoke the at least two antivirus engines in turn to detect and kill the suspicious objects, and proceed to step 306.
[0089] Step 306: Determine whether a virus is found, if not, go to step 301; otherwise go to step 307.
[009...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com