Multilevel security policy conversion method
A security policy and conversion method technology, applied in the field of multi-level security policy conversion, can solve problems such as difficulty in ensuring security and heavy workload, and achieve the effect of improving efficiency and reducing labor costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
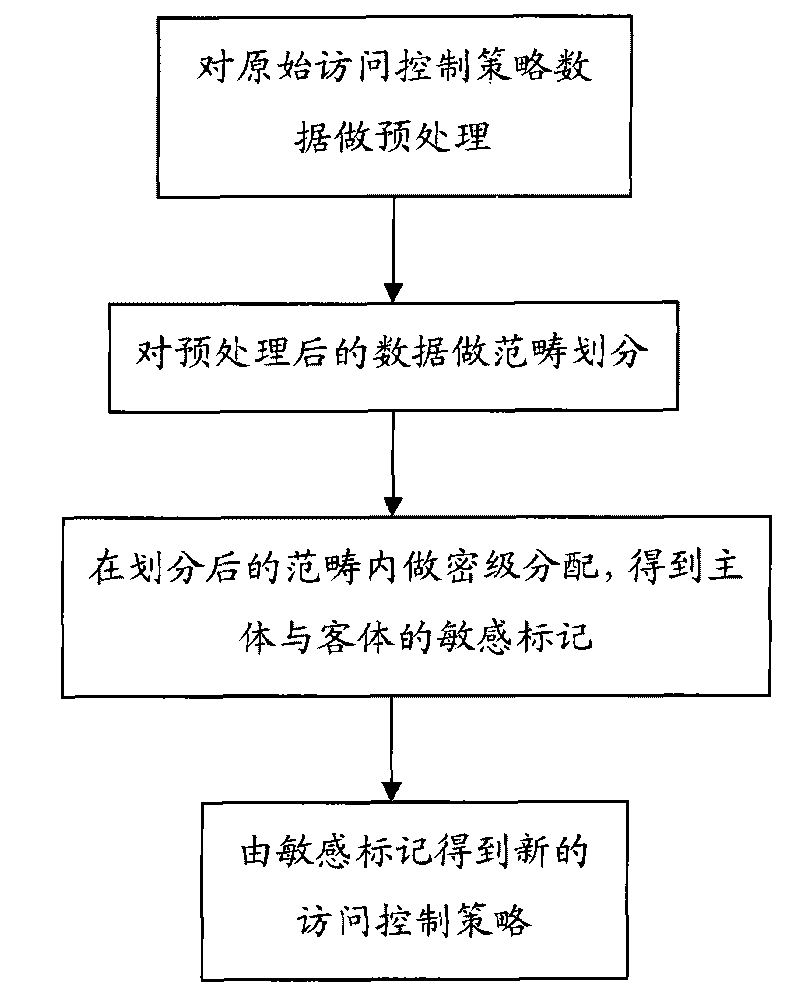
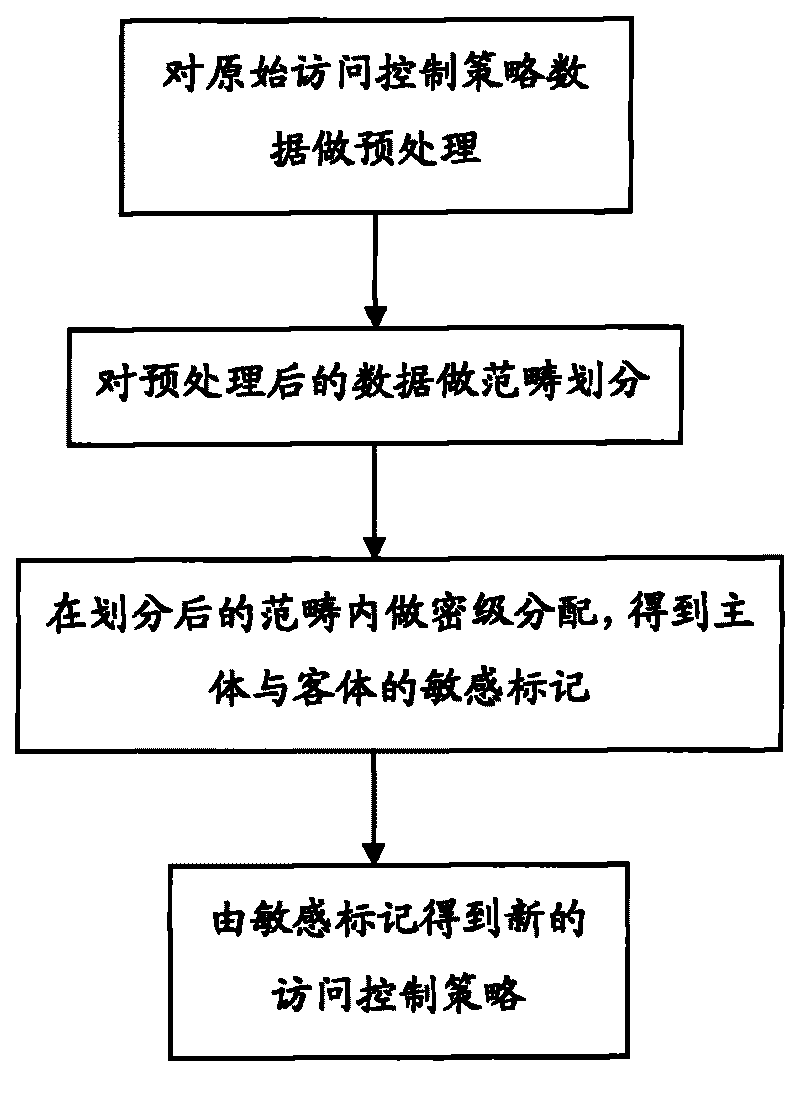
[0022] The present invention will be described below in conjunction with the accompanying drawings and specific embodiments.
[0023] Before describing the specific implementation of the present invention in detail, some concepts involved in the present invention will be described uniformly.
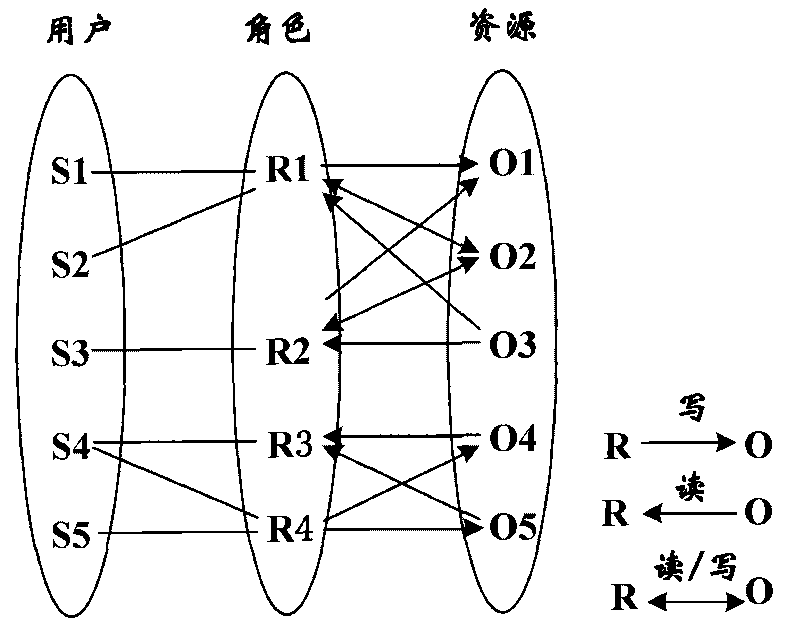
[0024] Sensitive mark: In multi-level security, both subject and object will be marked with sensitive mark, which includes category and confidentiality level. The set of sensitive flags is expressed as L = { ( c , k ) | c ∈ C , k ⊆ K } , Among them, the confidentiality level C is a linear sequence with comparable size, such as {public, secret, confidential, top secret}, and the confidentiality level is getting higher and higher from "public" to "top secret". The categories in the category set K are no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com