Face recognition based method for authenticating identity
A face recognition and identity authentication technology, applied in the field of identity authentication based on face recognition, can solve the problems of large amount of transmitted image data for face authentication, inability to control the angle and size of the face, increasing the amount of calculation and processing difficulty, etc. Achieve the effect of good calculation and identification features, fast processing speed, and reduced calculation amount
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
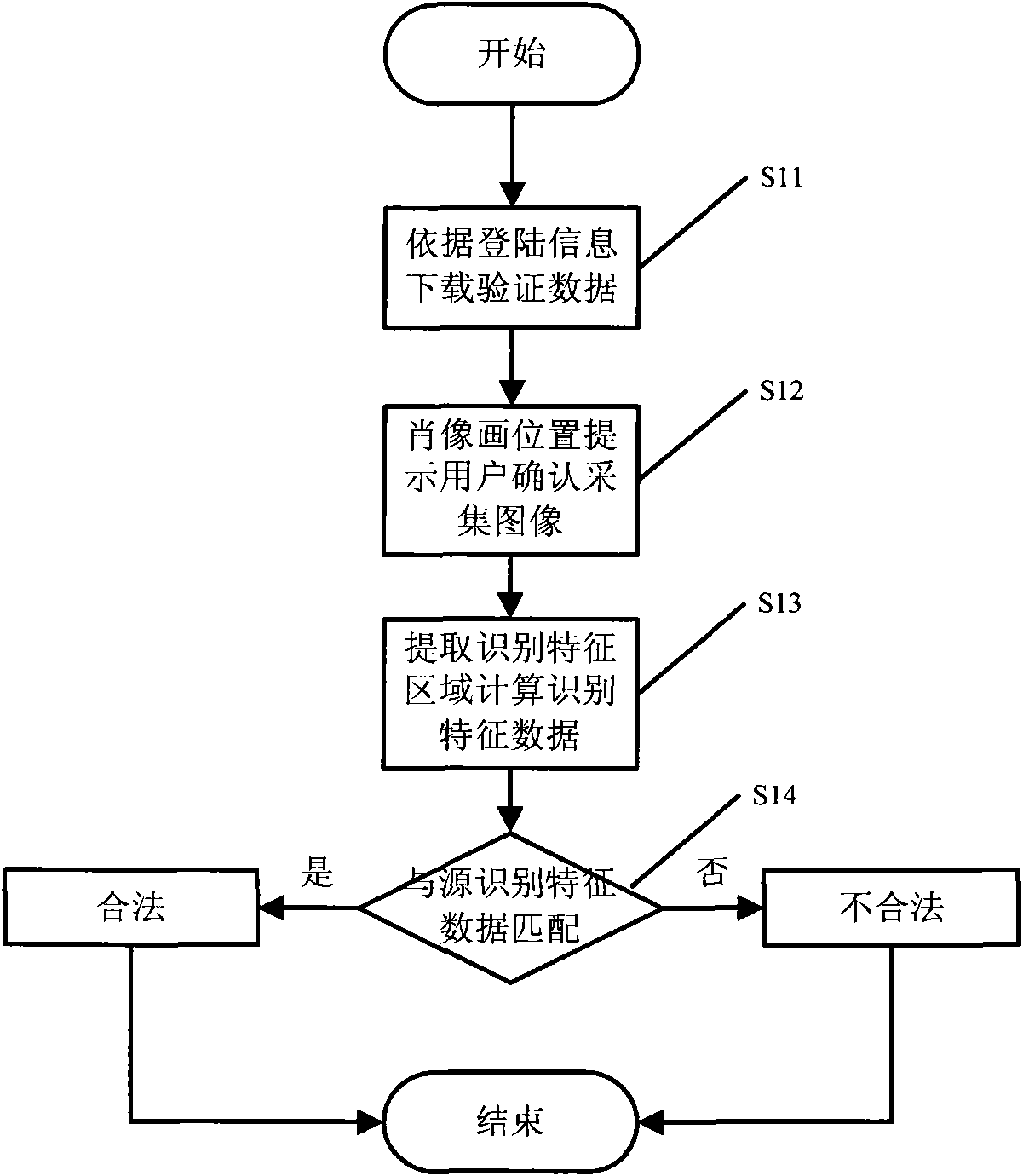
[0029] An identity authentication method based on face recognition mainly includes two parts: the face recognition verification feature extraction for the verified person, and the use of the extracted feature data to verify whether the identity of the registered person is legal.
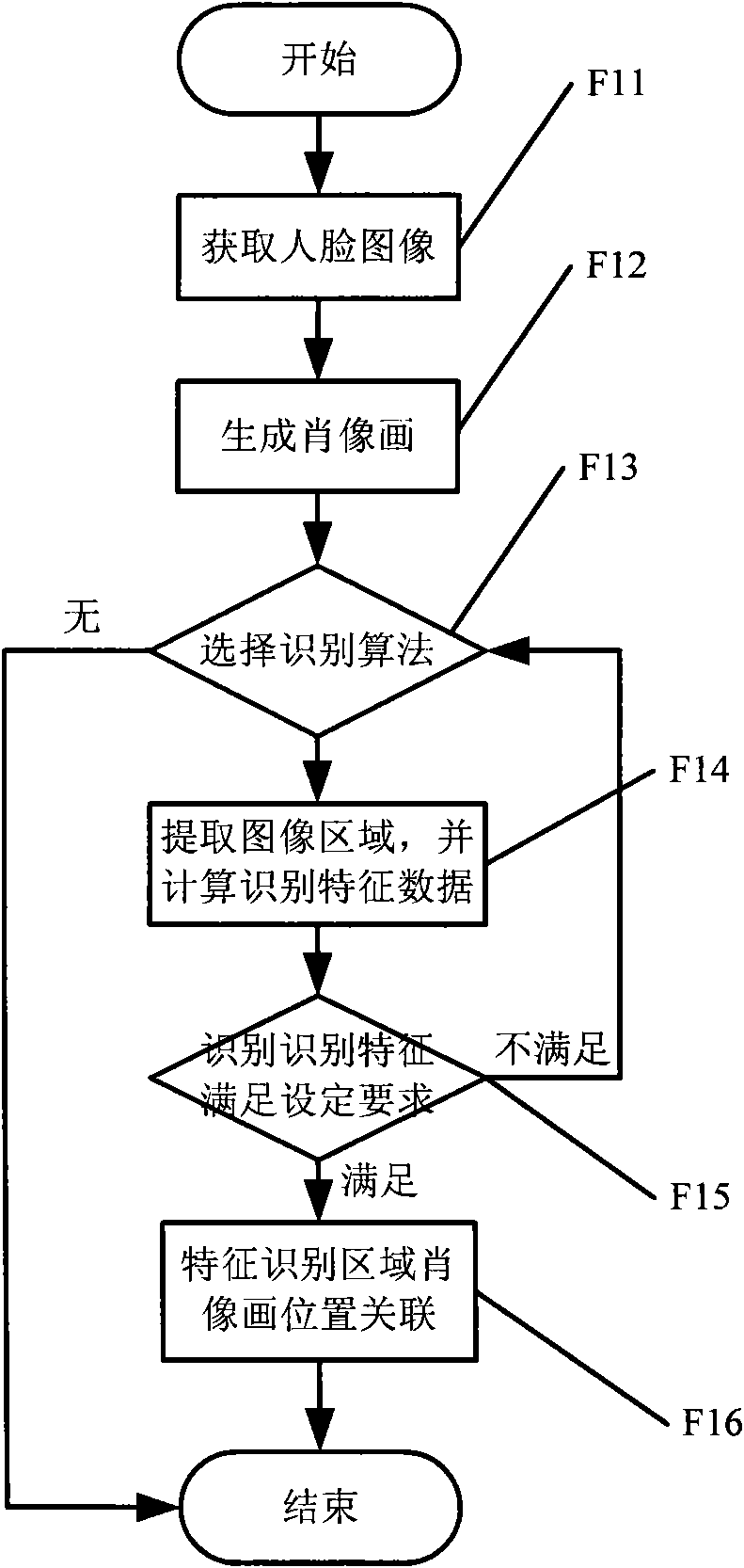
[0030] Such as figure 1 As shown, a face recognition verification feature extraction method in identity authentication based on face recognition, comprising the following steps:
[0031] F11: The face image of the verified person is acquired by the video acquisition terminal.
[0032] The specific implementation steps are: first input the information of the person being verified, so that the corresponding verification information can be indexed. The face image is obtained from a video capture device, and the video device is a commonly used video device, such as a ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com