Method for encrypting application software private area of EVDO (evolution-data optimized) data card end
A technology of application software and private area, applied in digital data authentication, electronic digital data processing, computer components, etc., can solve problems such as poor security performance of EVDO data cards, and achieve security that is difficult to crack, good security, and safe high performance effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0039] Embodiment Encryption of application program private area of EVDO data card
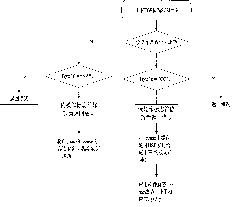
[0040] The EVDO data card end encryption scheme in this embodiment includes a secure read-write interface and a private area encryption scheme. Such as figure 1 , the application program of PC uses SCSI commands to read and write the private area of the application software to follow the Bulk-Only transmission protocol, and some instructions on the read and write interface are as follows.
[0041] The command block packet structure transmitted between the host and the EVDO data card is shown in the following table:
[0042]
[0043] Among them, dCBWSignature: indicates that the current sending is a CBW, which is the sign of CBW, and the fixed value is 0x43425355. All CBW values are sent in LSB order when transmitted on the USB bus, that is, the low bit is sent first, and then the high bit is sent. DCBWTag: Generated by the host and sent to the device, the device will fill this value...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com