Distributed protocol for authorisation
A technology for authorizing data and authorization requests, applied in the field of authorized recursive distributed protocols, can solve problems such as not meeting the needs of ad hoc networks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be described in relation to UWB wireless networks. However, it should be appreciated that the invention is equally applicable to any wireless network that performs distributed authorization.
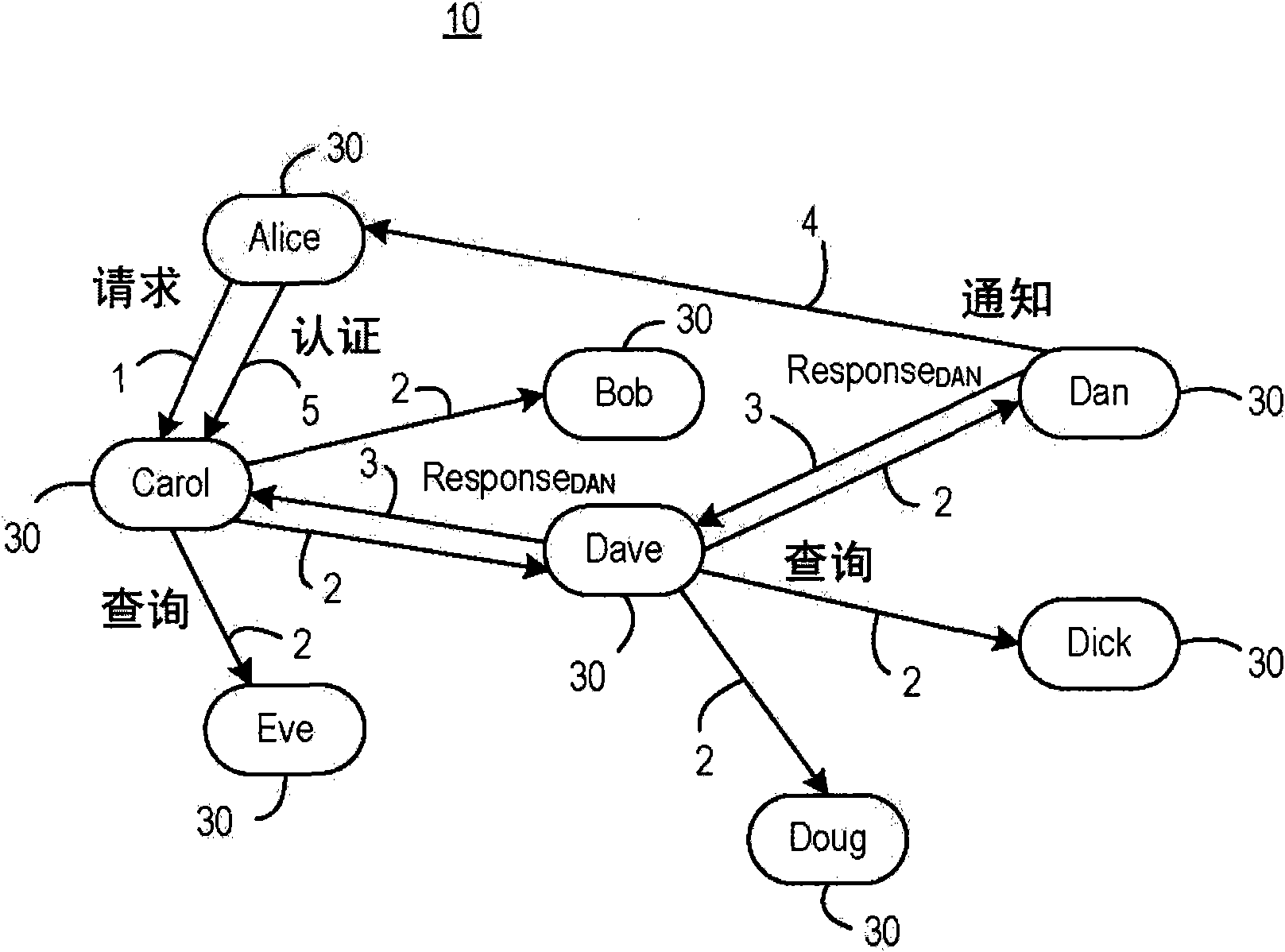
[0029] FIG. 3 shows a wireless network 10 with a plurality of wireless devices 30 . For purposes of illustration, wireless devices 30 are identified by their usernames in this example. For example, wireless network 10 in FIG. 3 has wireless devices 30 labeled Alice, Carol, Bob, Dave, Eve, Dan, Dick, and Doug. As described below, the protocol for performing distributed authorization includes multiple stages, some of which in turn have multiple steps.
[0030] In the example of Figure 3, the method for performing distributed authorization comprises five main steps, with steps 2 and 3 having multiple messages.
[0031] In step 1, an unauthorized user, eg Alice, requests access to a network, device or service controlled by a service providing device (eg C...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com