Method for disordering, splitting, storing, combining and mutually validating files
A file and random order technology, applied in the direction of digital data protection, etc., can solve the problems of forged secret information, secret leakage, lack of file integrity detection and mutual integrity detection, etc., to achieve high security performance and high security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0115] To further illustrate the present invention, specific examples are given as follows. But the content of the present invention is not limited to the content involved in the embodiment.
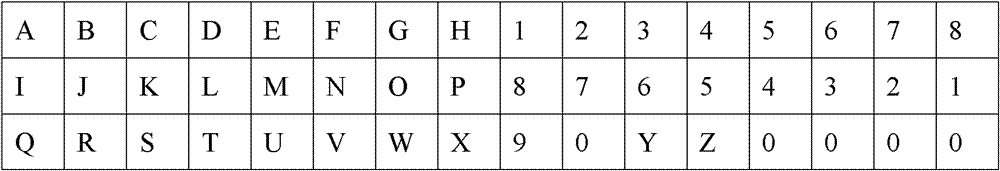
[0116] Explanation 1: For the sake of illustration, it is assumed that the object to be processed is a text file (a file storage format), its file name is example.txt, its length is 44 bytes, and its content is "ABCDEFGH12345678IJKLMNOP87654321QRSTUVWX90YZ" 44 characters.
[0117] Explanation 2: Put the file into a 16-column matrix in units of characters, and fill in 0 for the insufficient elements in the last row. See the attached file for the storage format figure 1 .
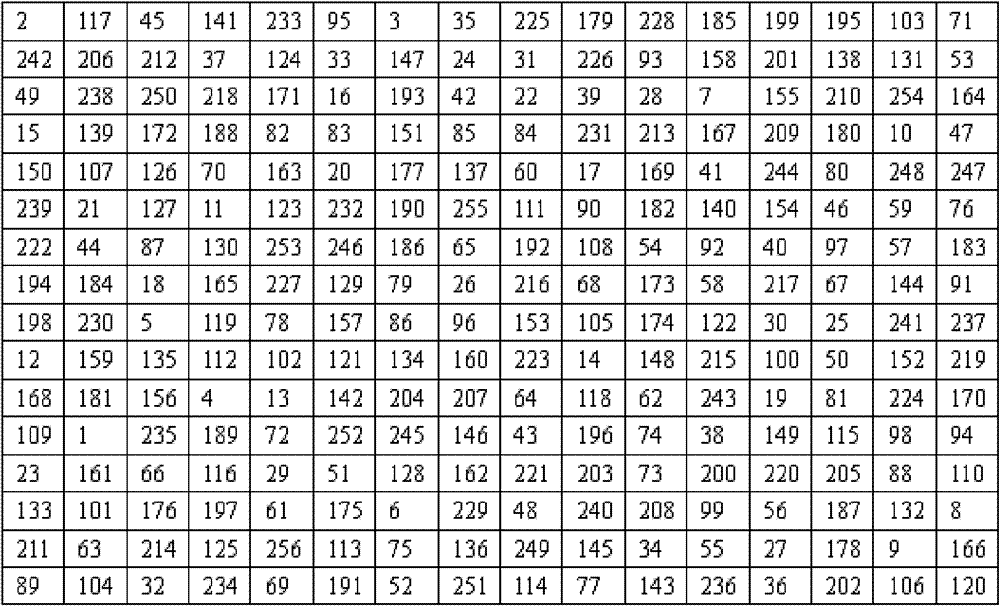
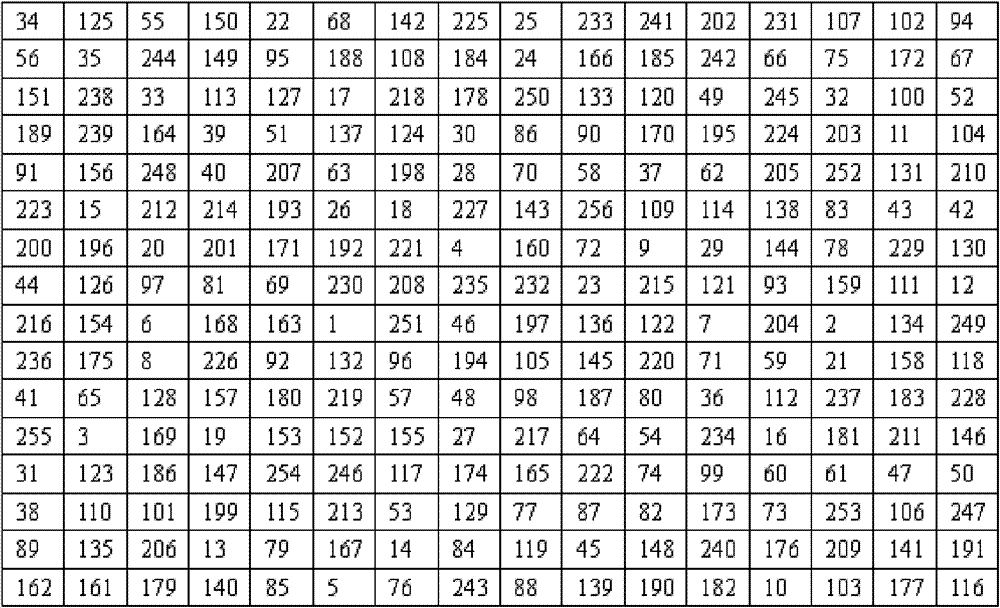
[0118] Explanation 3: Assume that the user needs to divide the file example.txt into three parts to generate three random magic squares M 1 , M 2 , M 3 , see attached figure 2 , attached image 3 , attached Figure 4 .
[0119] An example of magic square mixing in the file example.txt.
[0120]Process 1: Accor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com