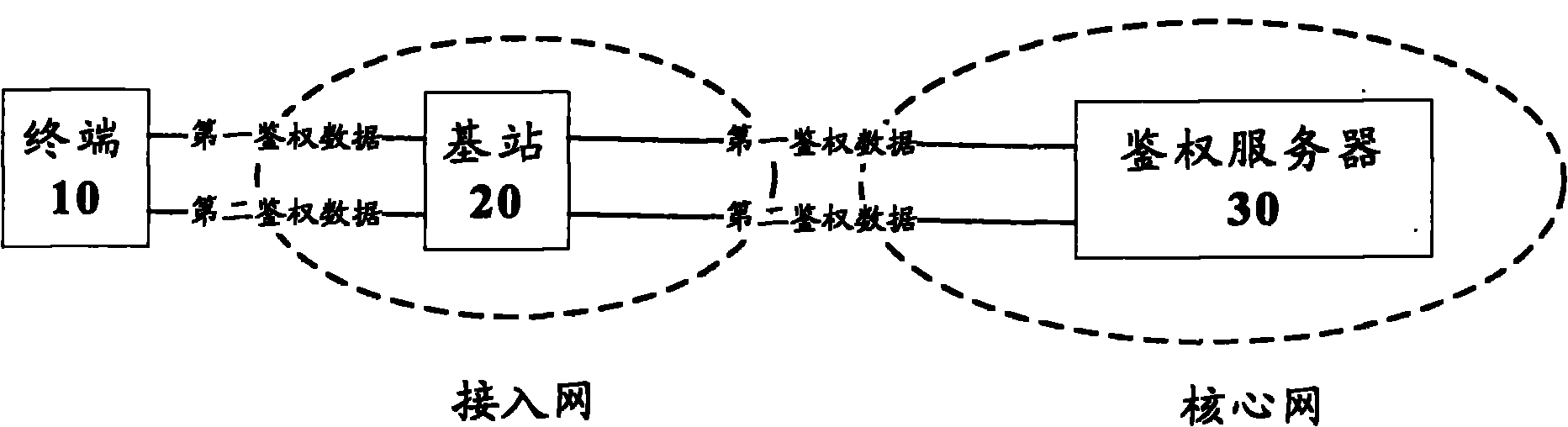
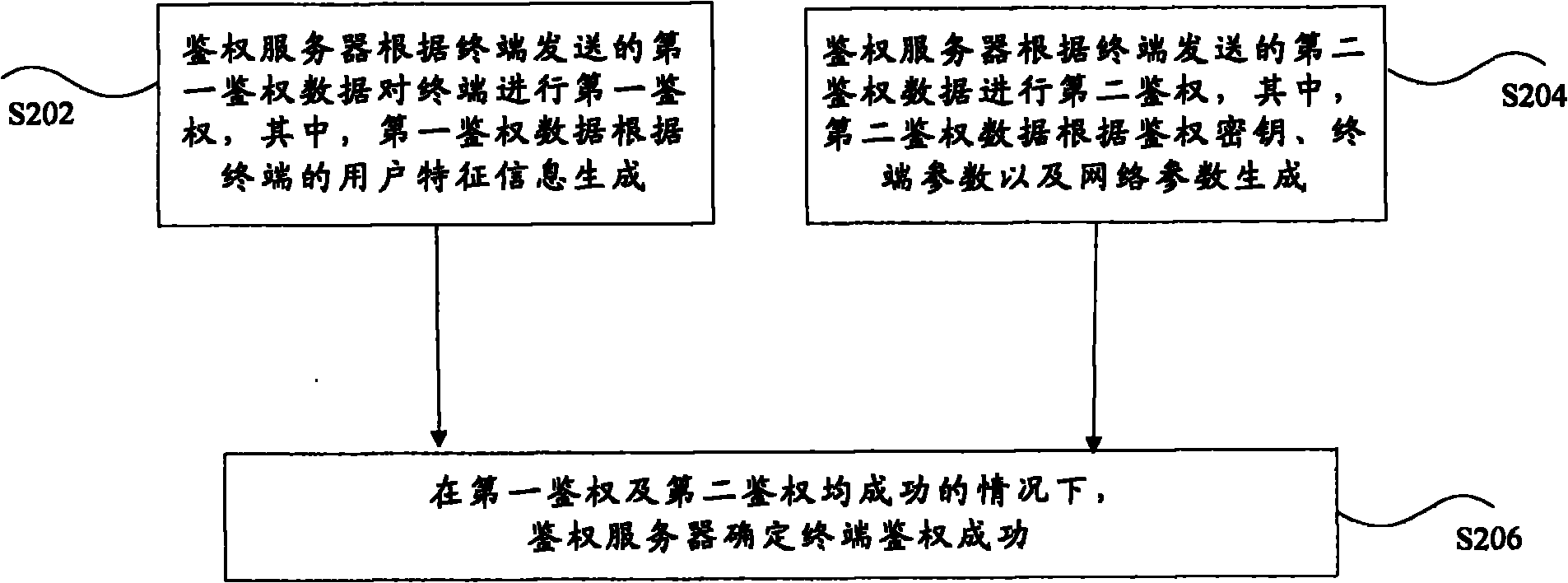
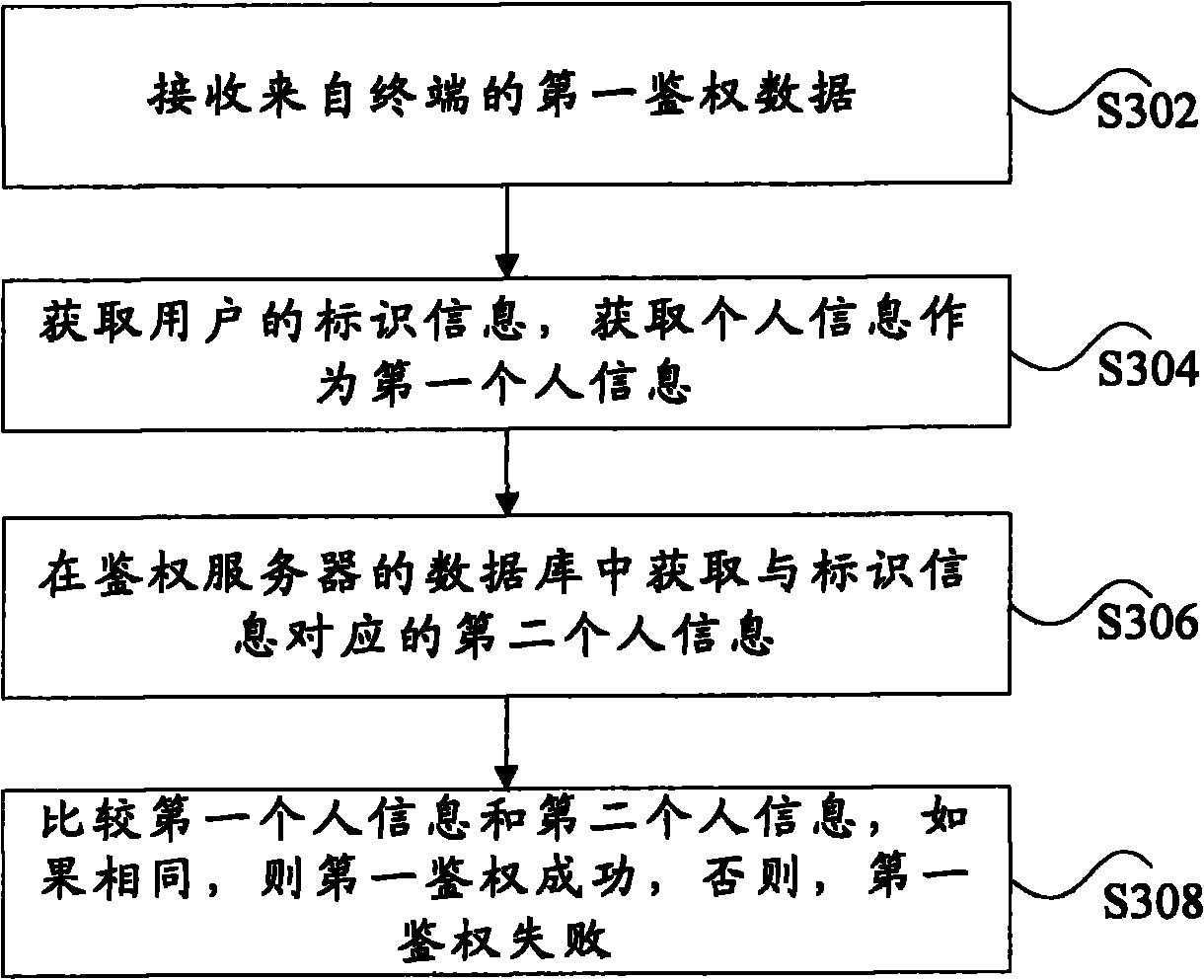
Terminal authentication method and system
An authentication and terminal technology, applied in transmission systems, safety devices, electrical components, etc., can solve the problem that the terminal authentication mechanism is not enough to ensure the security of the terminal user's use of the network, the legitimate rights and interests of the operator, and achieve the protection of legal Benefits and Benefits, Enhanced Security, Effectiveness of Enhanced Protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0065] In this embodiment, the authentication server is selected to first perform the first authentication, and if the first authentication succeeds, the second authentication is triggered. Figure 5 is a flow chart of terminal authentication according to Embodiment 1 of the present invention, such as Figure 5 As shown, the process includes:
[0066] Step S501, the terminal is turned on.
[0067] Step S502, the terminal uses communication network services (network registration, voice, short message, data, etc.).
[0068] Step S503, according to the returned system message, the terminal determines whether to perform the first authentication.
[0069] Step S504, if the network requires the terminal to perform the first authentication, the terminal generates the first authentication data according to the personal information preset by the user including terminal information and card information combined with a specific encryption algorithm, and executes step S505; otherwise, ...
Embodiment 2
[0077] In this embodiment, the authentication server is selected to perform the second authentication first, and if the second authentication succeeds, the first authentication is triggered. Image 6 is a flow chart of terminal authentication according to Embodiment 2 of the present invention, such as Image 6 As shown, the process includes:
[0078] Step S601, the terminal is turned on.
[0079] Step S602, the terminal uses communication network services (network registration, voice, short message, data, etc.).
[0080] Step S603, the terminal sends the second authentication data, and the authentication server executes the second authentication operation, if the second authentication is successful, executes the step S604, otherwise, prompts the user to prohibit using the network service.
[0081] Step S604, according to the returned system message, the terminal determines whether to perform the first authentication.
[0082] Step S605, if the network requires the terminal ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com