Secure access control method and device for wireless network
A wireless access and secure access technology, applied in security devices, wireless communications, electrical components, etc., can solve the problems of more than 200,000 RMB, difficult security and usability trade-offs, and high cost of wireless access control solutions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
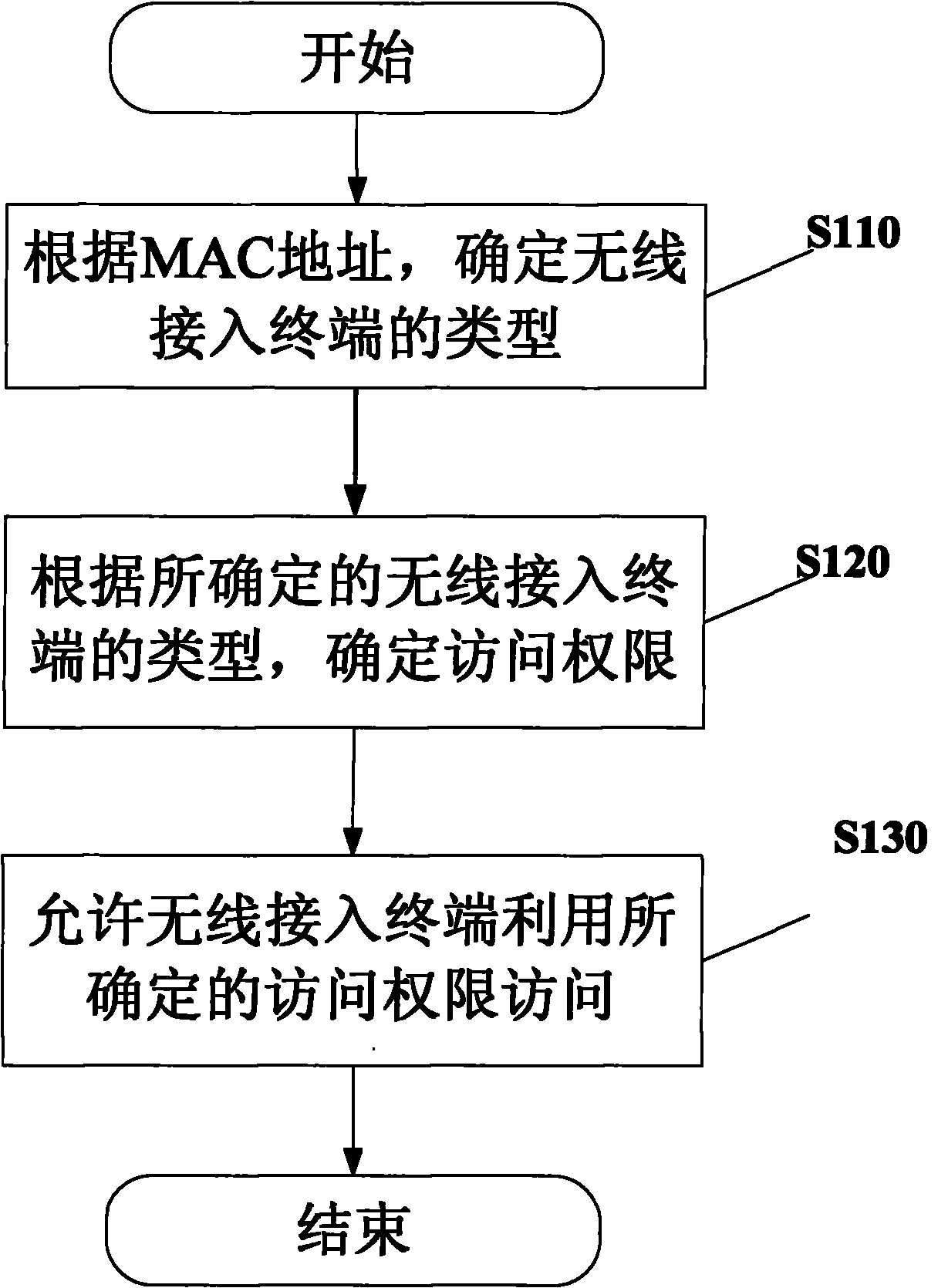
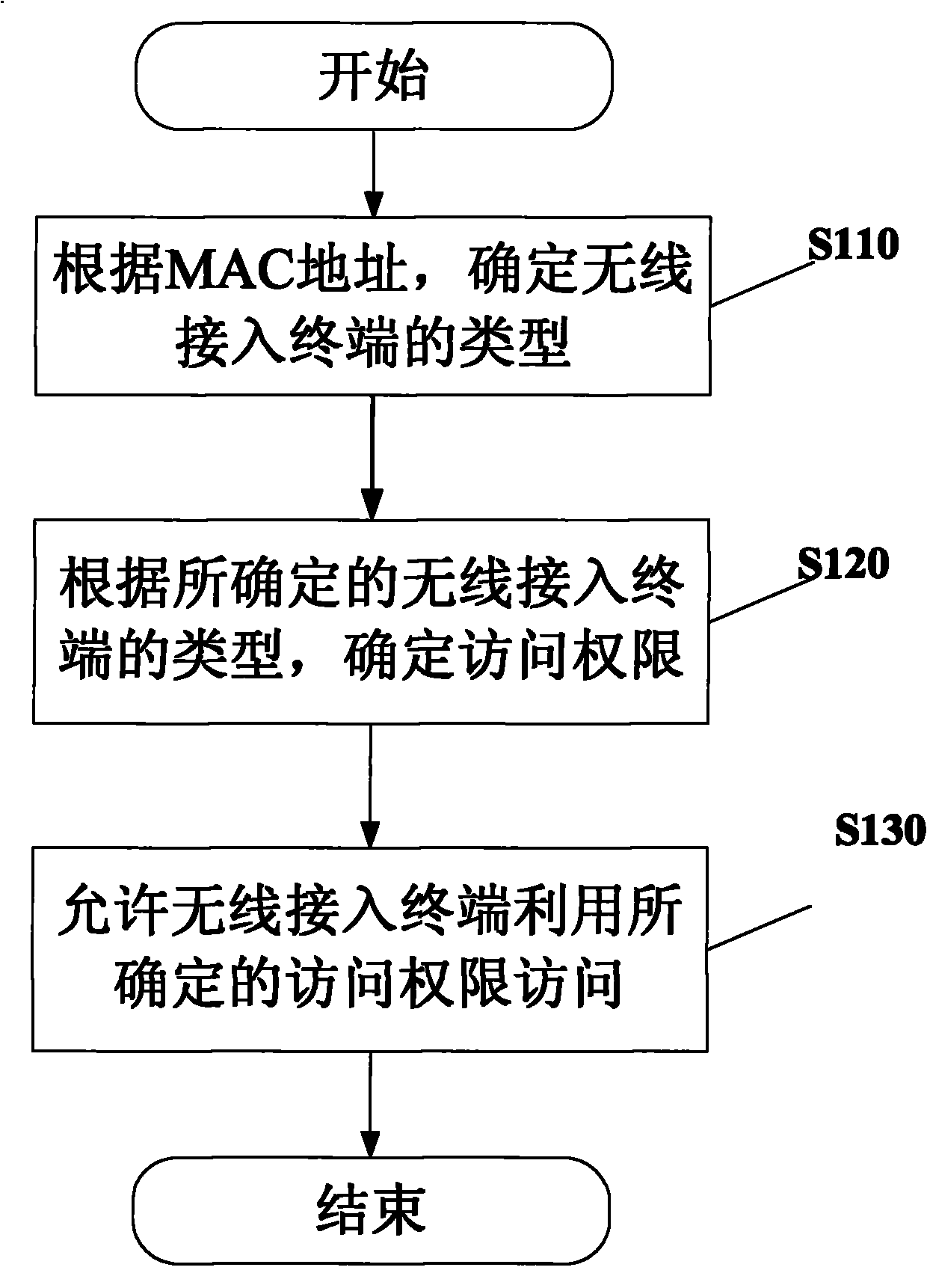
[0023] figure 1 A flow chart of the wireless network security access control method according to the present invention is shown.
[0024] Such as figure 1 As shown, when a wireless access terminal wishes to access a wireless network within an enterprise, first, in step S110, the type of the wireless access terminal is determined according to the MAC address of the wireless access terminal. For example, wireless access terminals can be classified as mobile terminals or notebook computers according to their MAC addresses. Of course, wireless access terminals can also be subdivided into many other types, such as mobile terminals into enterprise test mobile terminals, enterprise employee test mobile terminals, and notebook computers into enterprise notebook computers, enterprise employee notebook computers, or temporary Guest laptop. Then, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com