Method and device for inquiring authority
A query method and query device technology, applied in computer security devices, instruments, digital data authentication, etc., can solve the problems of reduced space storage, single inheritance relationship, and inability to adapt to a large number of complex user authority controls, etc., to achieve less The effect of data space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] Embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
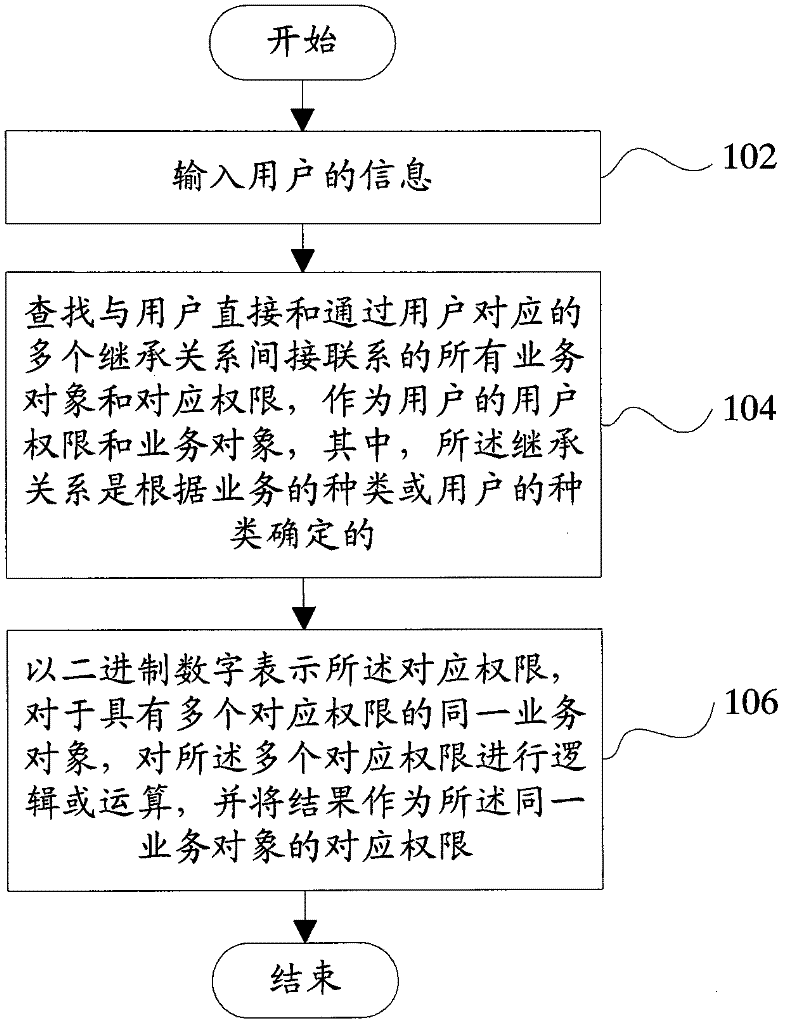
[0024] figure 1 It is a flow chart of the authority query method according to the present invention.
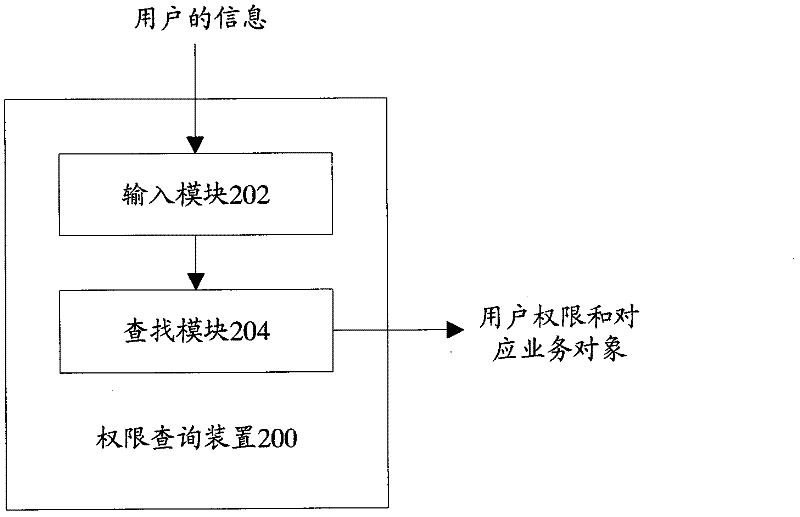
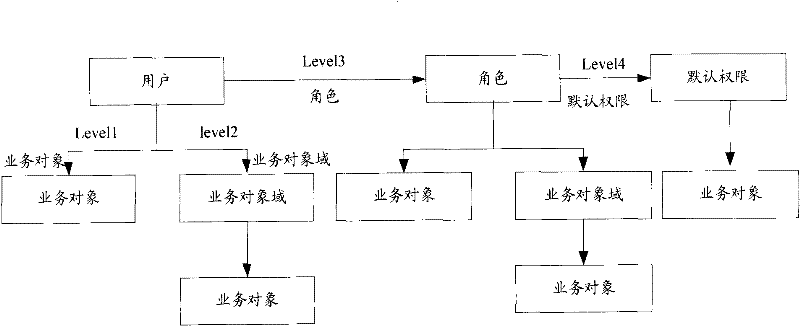
[0025] Such as figure 1 As shown, the present invention provides a permission query method, including: step 102, input user information; step 104, according to the user information, find multiple inheritance relationships directly and through the user corresponding to the user All indirectly related business objects and corresponding permissions of all business objects are used as user permissions of the user and business objects corresponding to the user permissions. In this technical solution, multiple inheritance relationships are used to respectively contact users and business objects, which can effectively reduce the space occupied by storing authority data.
[0026] In the above technical solution, it also includes: step 106, expressing the cor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com