Method and system for safely downloading certificate
A certificate and security technology, applied in the field of information security, can solve problems such as single authentication method and counterfeit smart key equipment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
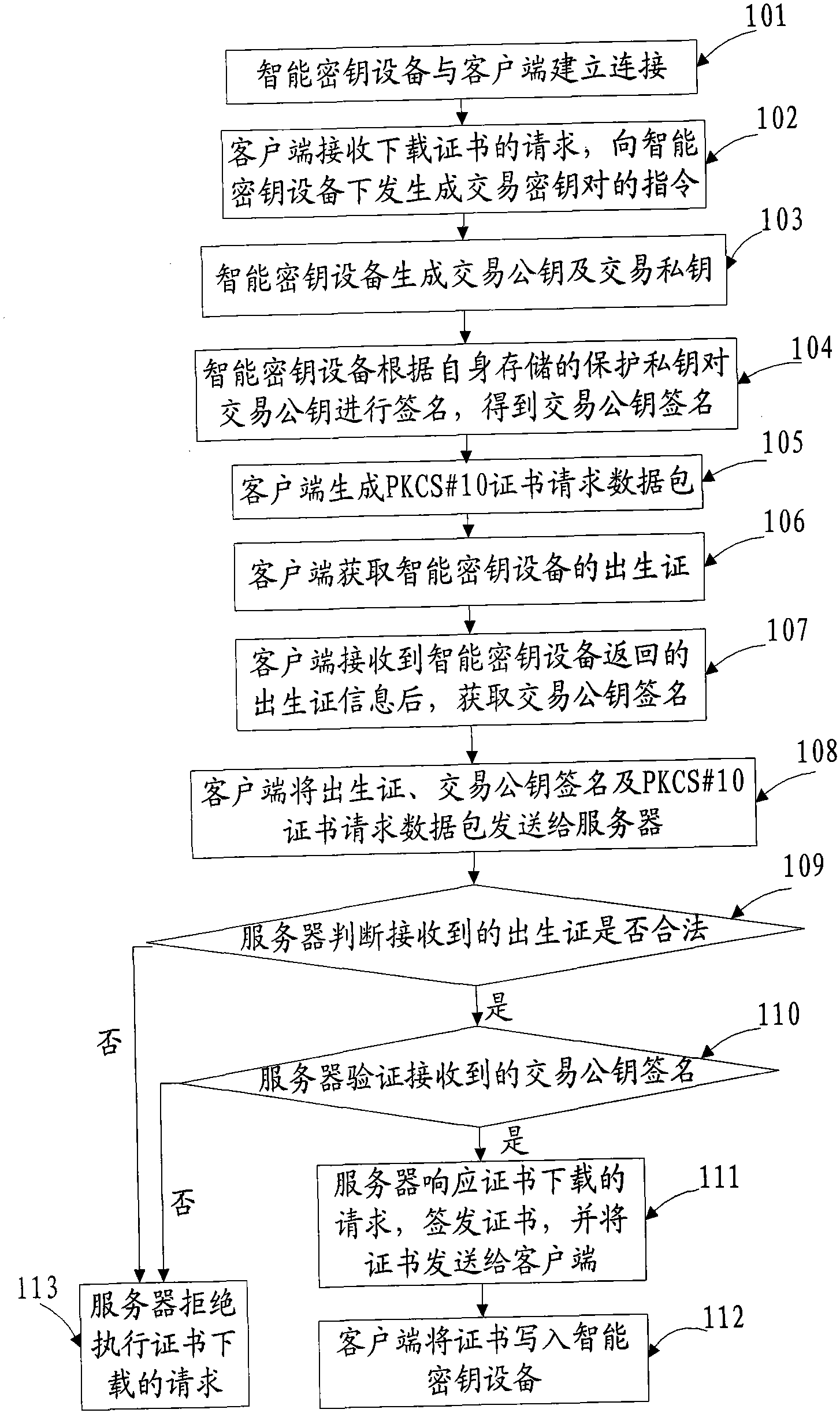
[0112] see figure 1 , this embodiment provides a method for securely downloading certificates, the specific process is as follows:
[0113] 101. The smart key device establishes a connection with the client;
[0114] Preferably, the client establishes a connection with the smart key device by calling CryptAcquireContext of a CSP (Cryptographic Service Provider, encryption service provider) interface.
[0115] 102. The client receives the request for downloading the certificate submitted by the user, and sends an instruction to the smart key device to generate a transaction key pair;
[0116] 103. The smart key device generates a transaction public key and a transaction private key after receiving the instruction;
[0117] It should be noted that the transaction private key is used to sign the transaction information during the transaction.
[0118] 104. The smart key device signs the transaction public key according to its stored protection private key, and obtains the tran...
Embodiment 2
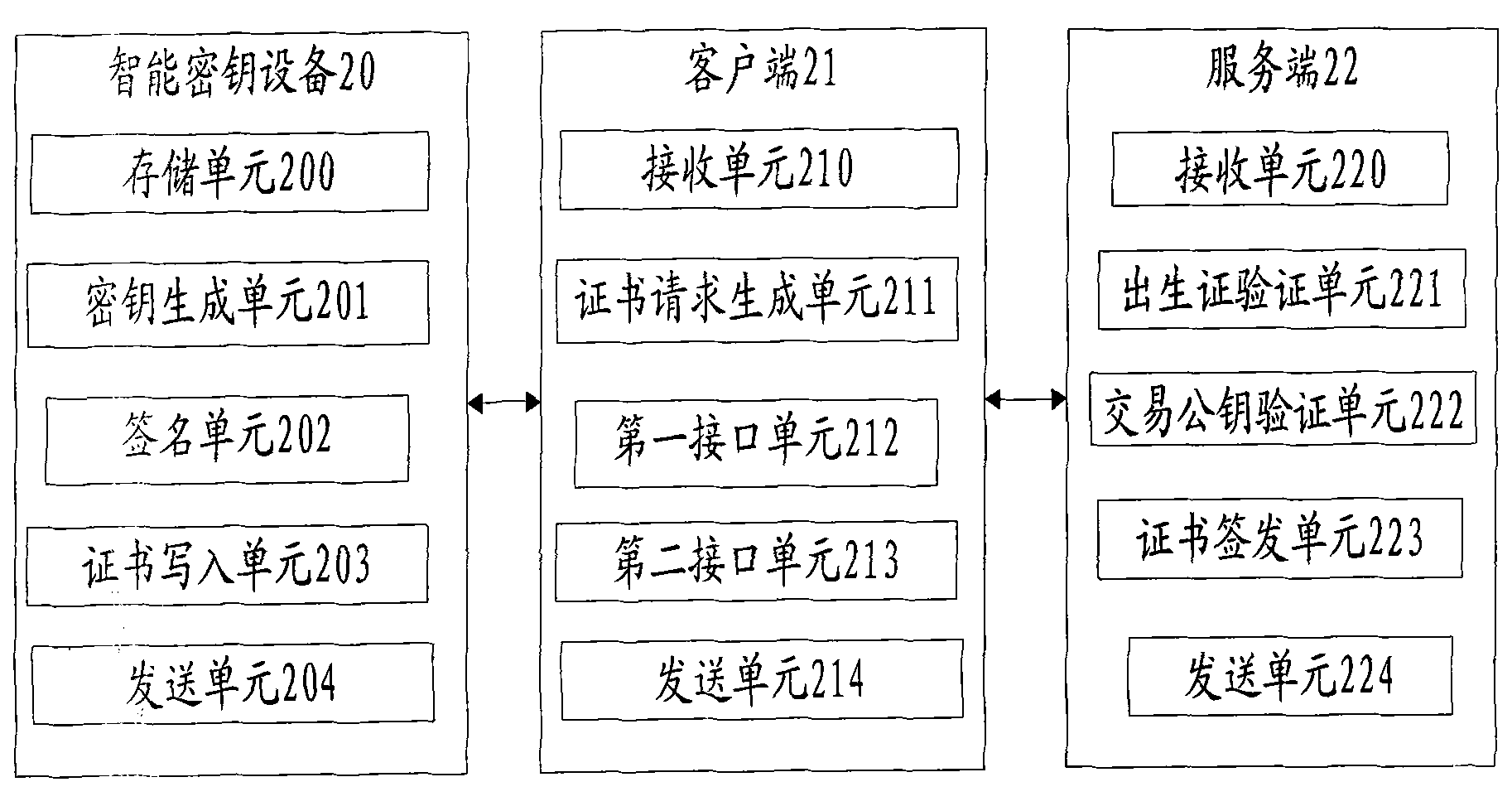
[0239] This embodiment provides a system for securely downloading certificates, see figure 2 , including: a smart key device 20, a client 21 and a server 22; wherein, the functions of each device are as follows:
[0240] Smart key device 20 includes:
[0241] The storage unit 200 is used to store the birth certificate, the protection private key and the certificate, wherein the birth certificate and the protection private key have been generated and stored when the smart key device leaves the factory;
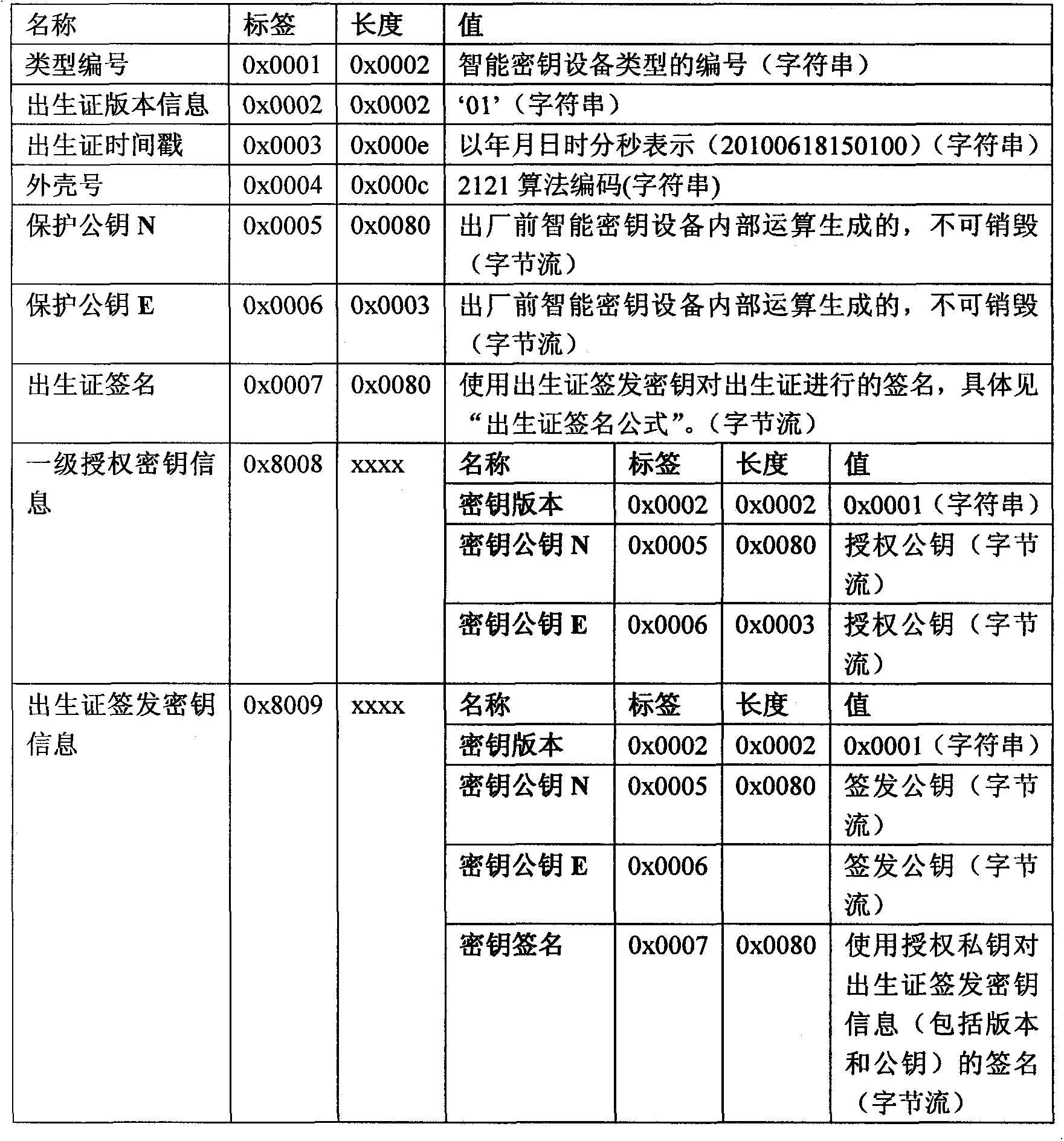
[0242] Specifically, the birth certificate includes: type number, birth certificate version information, birth certificate time stamp, shell number, protection public key, first-level authorization key, birth certificate issuance key information, and birth certificate signature. For the description of the item, refer to the relevant description in Embodiment 1, and do not repeat them here;
[0243] It should be noted that when the smart key device generates a protected priva...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com