Root alarm data analysis method and system
A technology of data analysis and root alarm, applied in the direction of digital transmission system, transmission system, data exchange network, etc., can solve the problems of limited number of rules, heavy workload, low efficiency, etc., and achieve the effect of reducing the number of alarms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
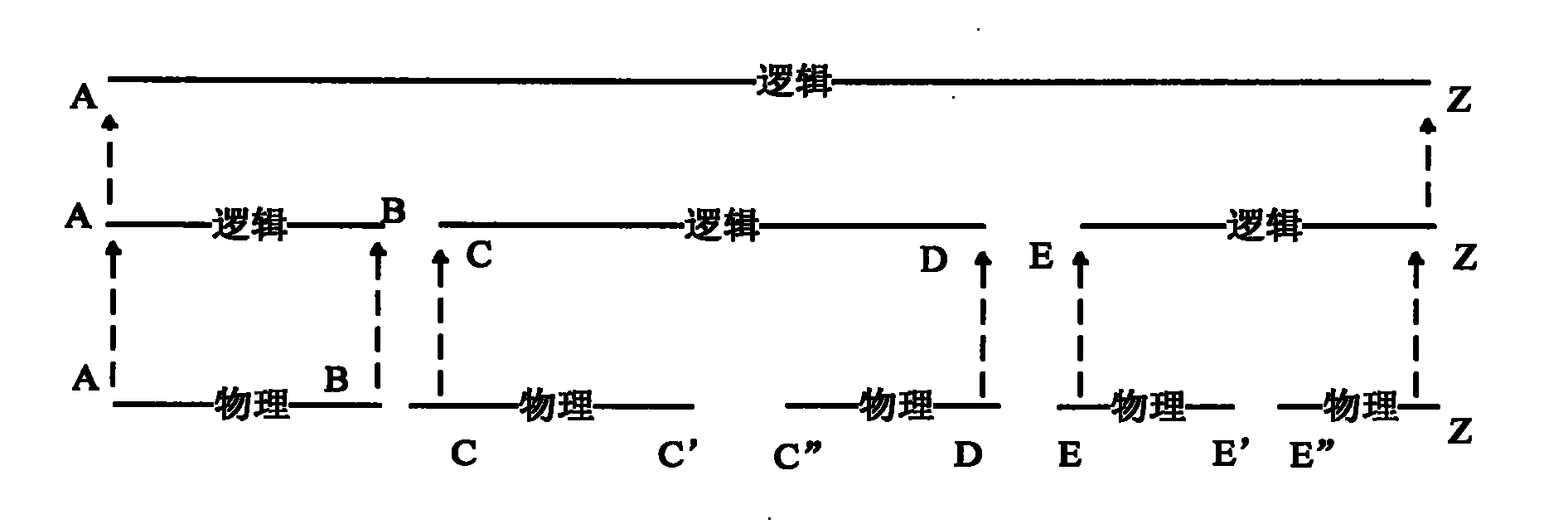
[0027] End-to-end is the logical communication link between the source and the destination. This logical link may have gone through a very complicated physical route, such as figure 1 As shown, it is a typical end-to-end model connection. The end-to-end model management of the integrated network management mainly manages the end-to-end logical connection across multiple network elements and the physical connection between adjacent network elements on which the logical connection is based.
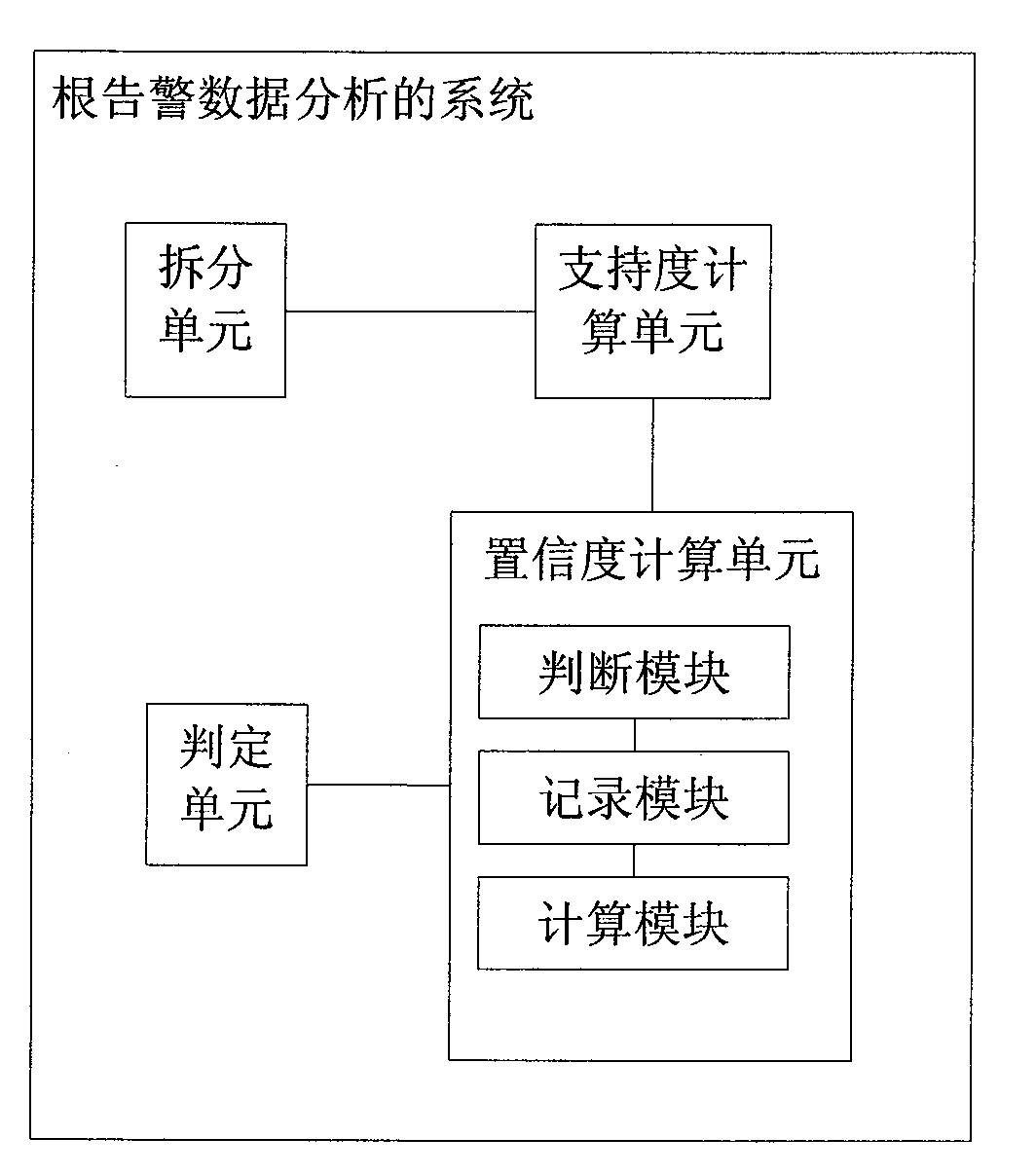
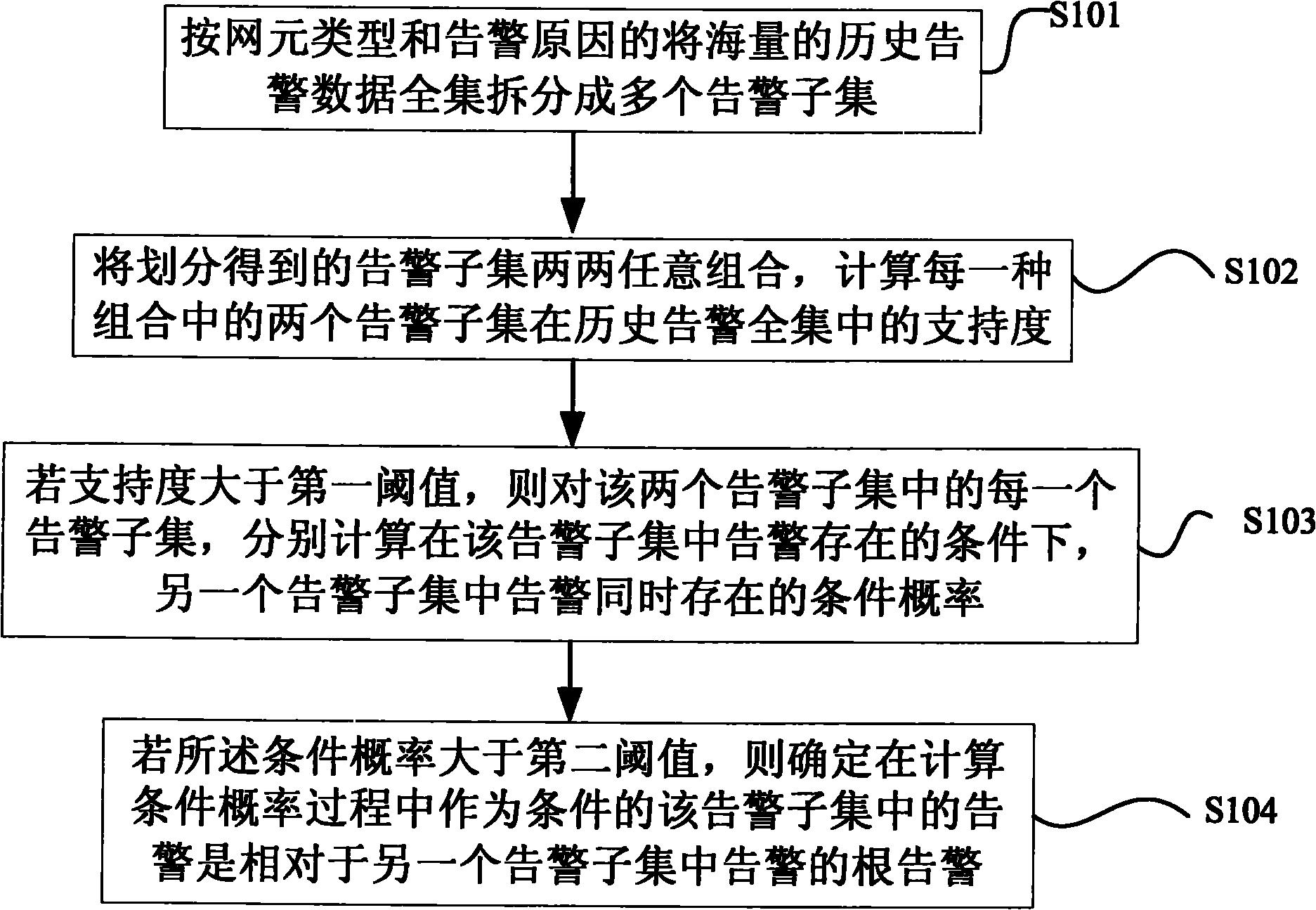
[0028] The root alarm data analysis method provided by the present invention mainly uses the existing massive historical alarm data sent by network elements in the end-to-end model and the connection relationship of network elements in the end-to-end model to realize automatic determination of root alarms through data mining Correlation rules with redundant alarms.
[0029] The technical solutions of the present invention will be described in more detail below in conjunction with the accom...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com