Method, device and system for anonymizing gateway node
A gateway node and anonymization technology, applied in the field of Internet of Things, to achieve the effect of protecting location privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
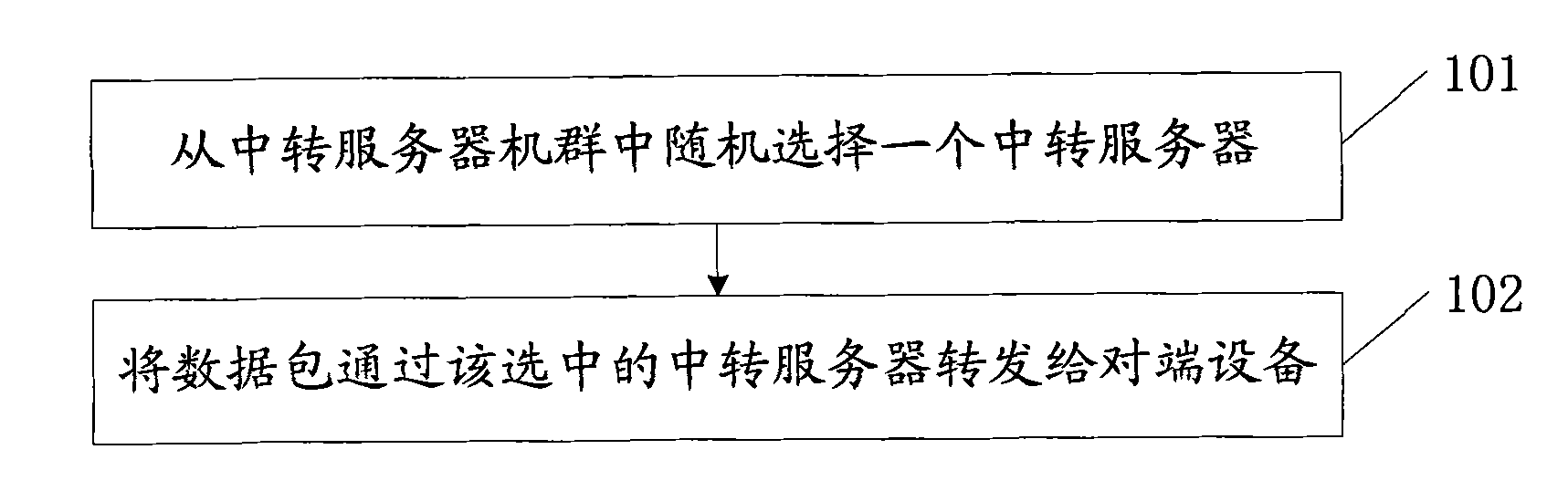
[0067] see figure 1 , this embodiment provides a method for anonymizing a gateway node, including:
[0068] 101: Randomly select a transit server from the transit server fleet;
[0069] 102: Forward the data packet to the peer device through the selected transit server.
[0070] Specifically, this method may be executed by a central server or a gateway node, and correspondingly, the peer devices are respectively a gateway node and a central server.
[0071] In the method provided in this embodiment, the central server or the gateway node randomly selects a transit server from the transit server cluster, and forwards the data packet to the peer device through the selected transit server. The link of the network is stretched into irregular multiple temporary links, so that the attacker cannot know the whereabouts of the data, thus hiding the location of the destination gateway node in the Internet, thereby protecting the location privacy of the objects behind the destination g...
Embodiment 2
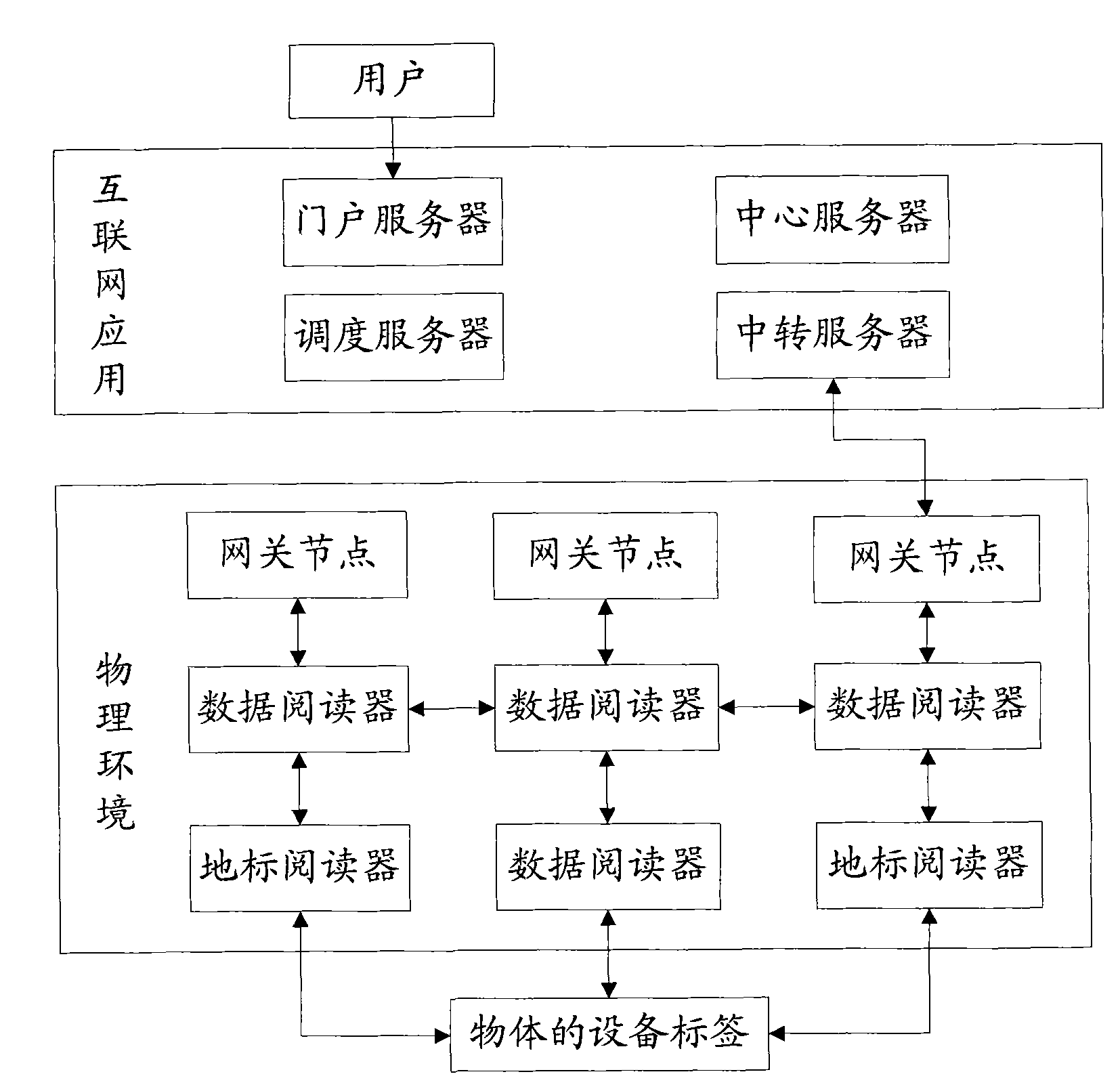
[0107] see Image 6 , this embodiment provides a central server, including:
[0108] The first selection module 401 is configured to randomly select a transit server from the transit server cluster;
[0109] The first forwarding module 402 is configured to forward the data packet to the destination gateway node through the selected transit server.
[0110] Wherein, the first selection module 401 includes:
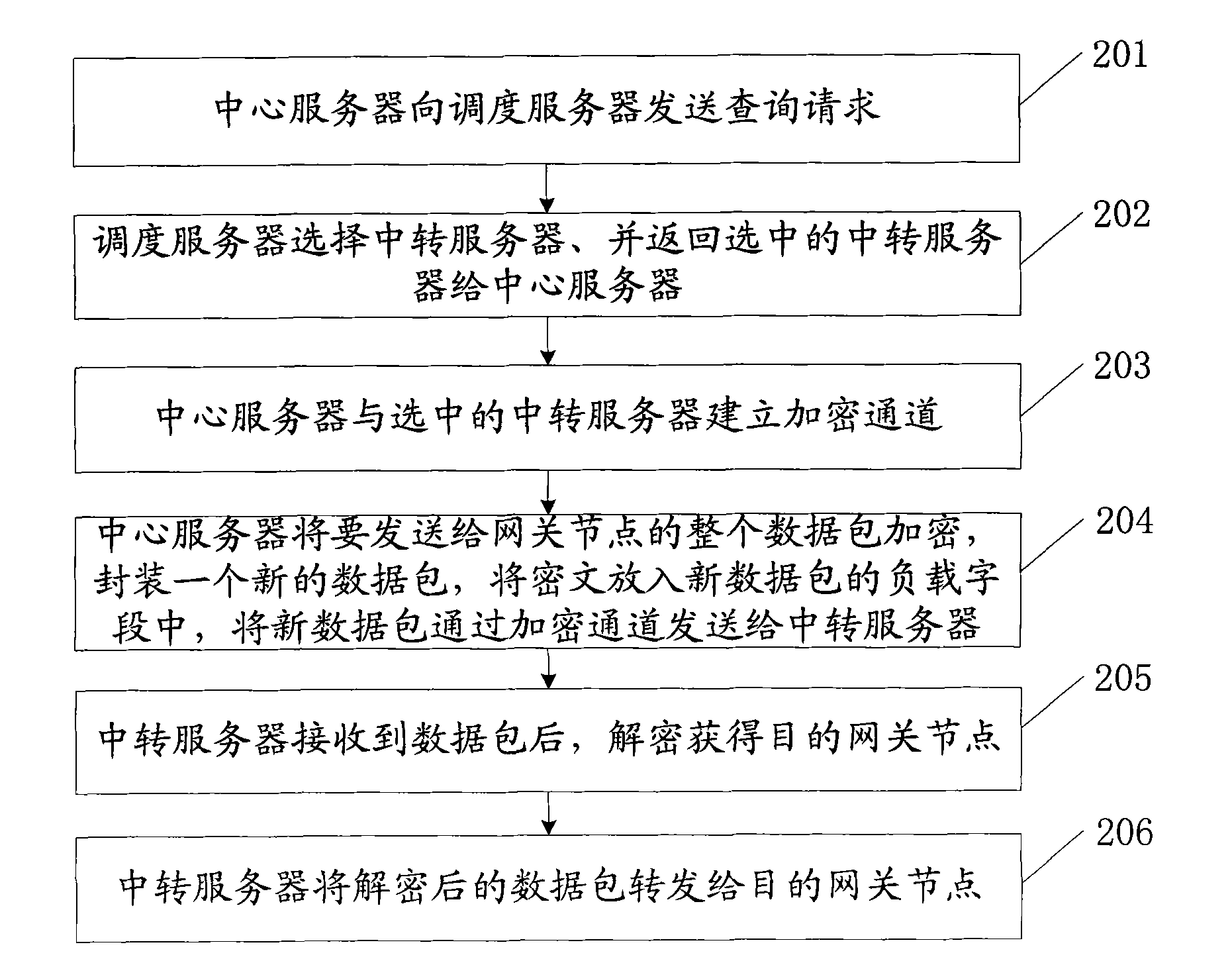
[0111] The requesting unit is used to send a query request to the scheduling server, and the query request carries the network address of the destination gateway node; after the scheduling server receives the query request, it obtains the corresponding destination gateway node according to the network address; obtains the first set of the transit server cluster; Generate a first random number, and compare the first random number with a preset probability; when the first random number is less than or equal to the preset probability, select the preset number of the closest ...
Embodiment 3
[0117] see Figure 7 , this embodiment provides a gateway node, including:
[0118] The second selection module 501 is used to randomly select a transit server from the transit server cluster;
[0119] The second forwarding module 502 is configured to forward the data packet to the central server through the selected transit server.
[0120] Wherein, the second selection module 501 includes:
[0121] An acquisition unit, configured to acquire the first set of transit server clusters from its own cache;
[0122] The selection unit is used to generate a second random number, and compare the second random number with a preset probability; when the second random number is less than or equal to the preset probability, select the preset closest to its own network from the first set number of transfer servers as the second set of transfer server clusters; when the random number is greater than the preset probability, the first set is used as the second set of transfer server clust...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com