Mobile user position privacy protection method for avoiding attacks performed through circular region overlapping parts
A mobile user and user technology, applied in the direction of location information-based services, security devices, electrical components, etc., can solve the problems of increasing user workload, privacy leakage, etc., to reduce query time, protect location privacy, and improve query efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] Combine below attached drawing A further detailed description of the implementation of the technical solution of the implementation case:
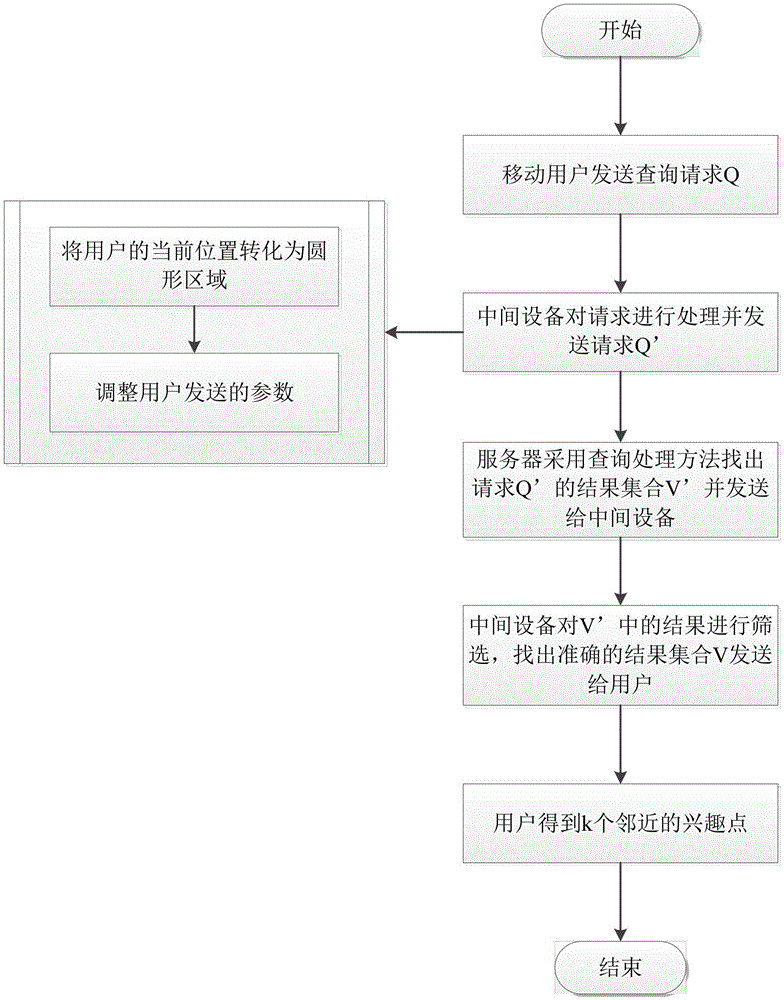
[0018] This implementation case adopts user viewing record collection, user personal social relationship analysis, and program recommendation based on content matching to accurately provide personalized TV program push. Such as figure 1 , figure 2 As shown, this method includes the following steps:
[0019] Step 10, the user sends his own position l, the required confidence level cl and the number k of interest points to be queried to the intermediate device.
[0020] Step 20, the intermediate device performs fuzzy processing on the user's location, converts the real location l into a circular area CR, and processes the parameters, specifying a value greater than the execution level cl and the number of query results k required by the user cl' and k' (set the value of the execution level cl' to the maximum value 1, and set ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com