Authentication method and device
一种身份认证、置信概率的技术,应用在安全通信装置、计算机安全装置、用户身份/权限验证等方向,能够解决回答错误、答案不准确、增加客户额外负担等问题,达到增加灵活性、良好正交性、提高安全性和可靠性的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
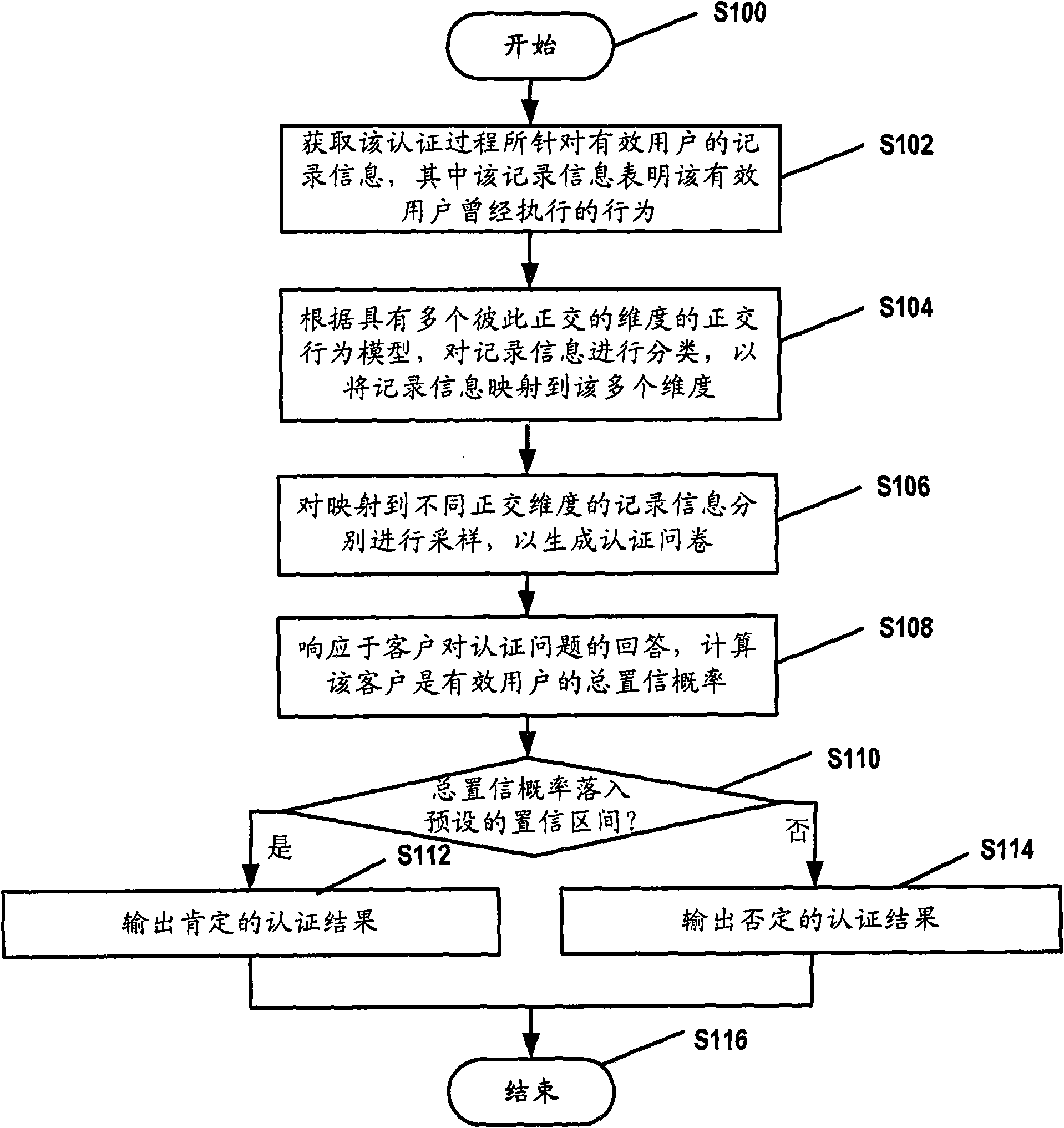
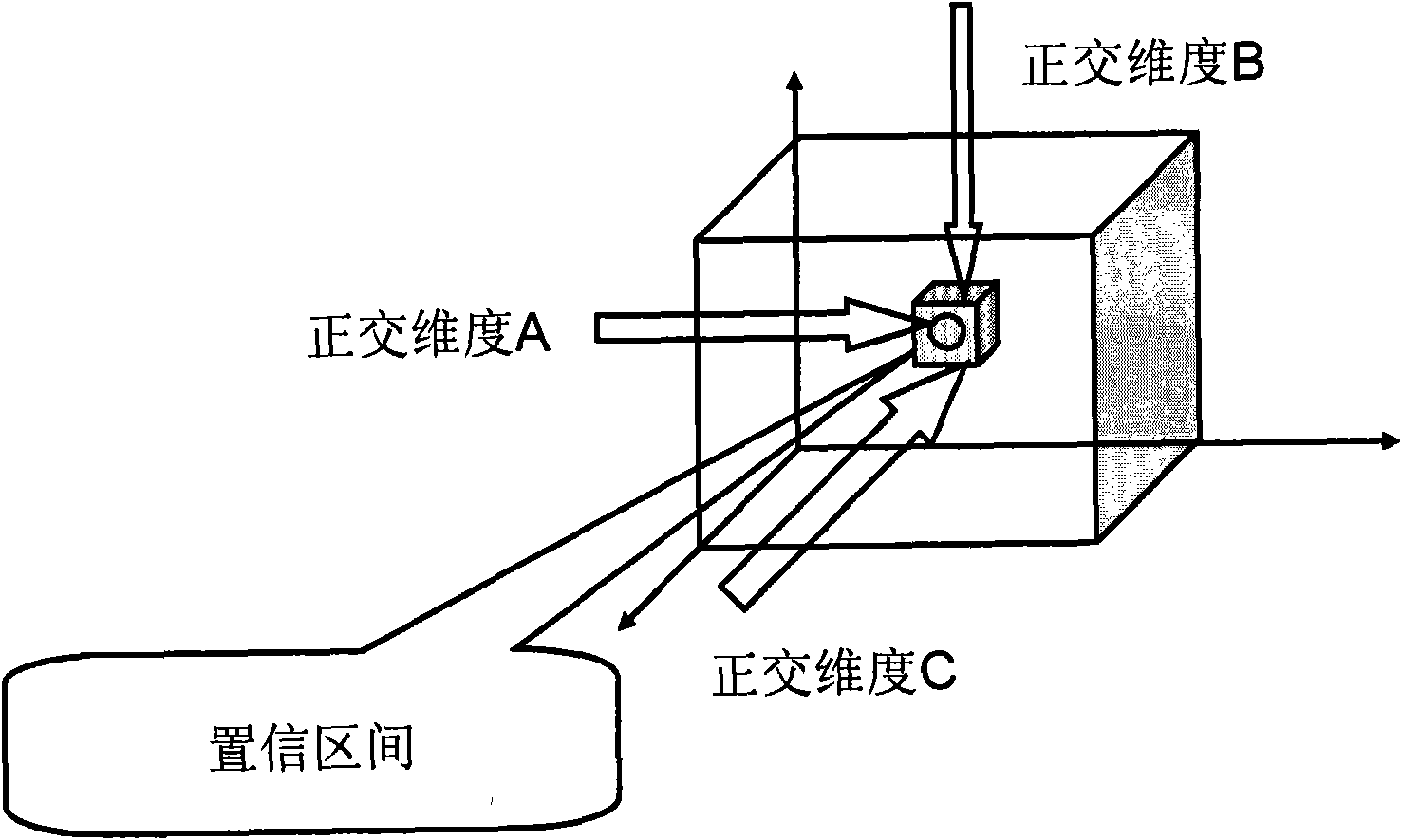
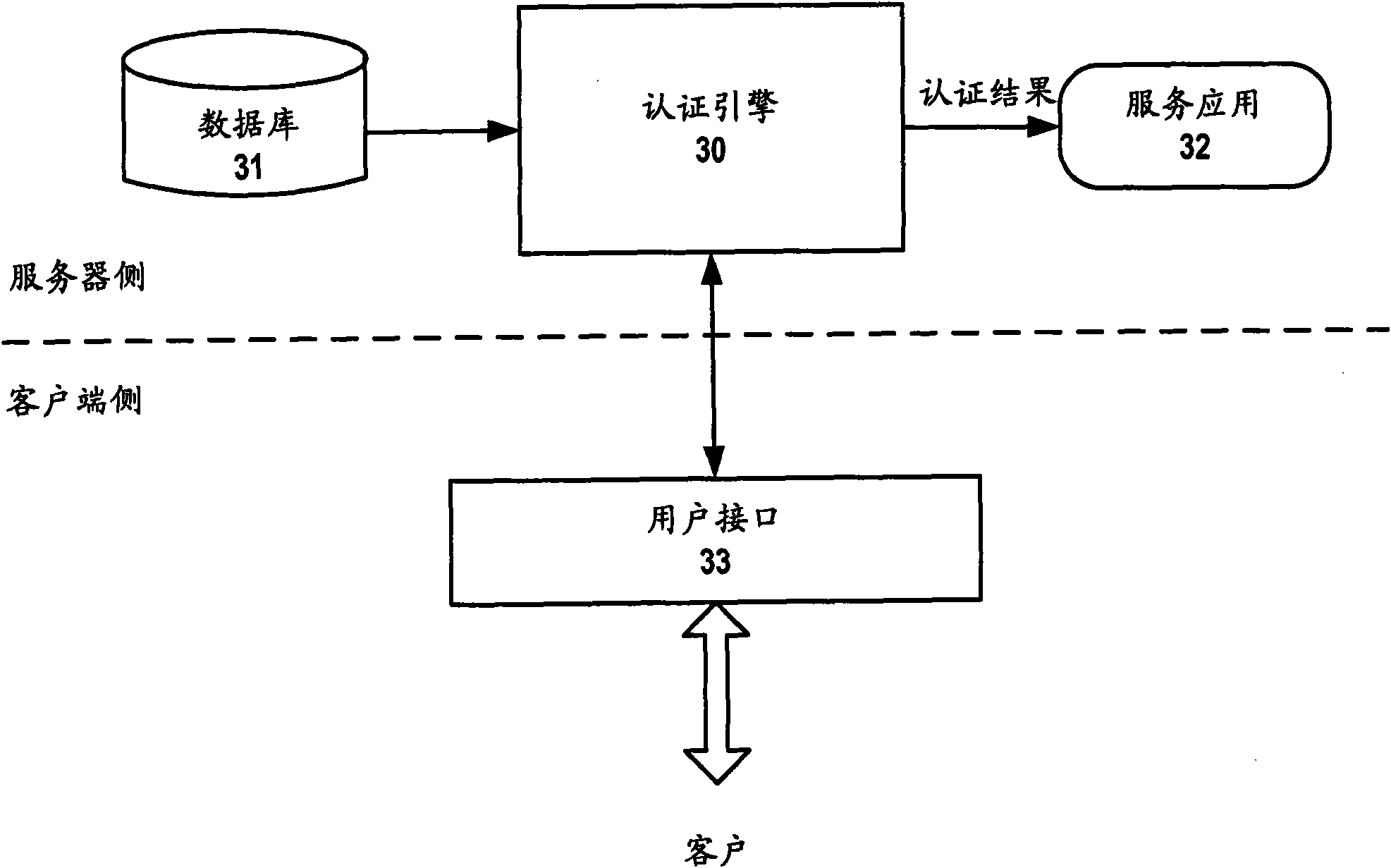
[0022] Because the existing authentication mechanism is based on limited static information, it is easy for criminals to steal the information and pass the authentication. However, the inventors have noticed that when users use service applications such as games and e-commerce, a large number of "footprints", that is, recorded information, will be left in the database of the network. These record information are, for example, transaction records stored in network databases, event logs, or any other electronic records. These recorded information as "footprints" are different from user to user and unique to each user. In particular, the recorded information changes with the user's behavior on the network. That is to say, specific users can be identified by virtue of these dynamically changing record information. Therefore, a main idea of the present invention is to verify the user's identity based on various record information left by the user when using a specific service. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com