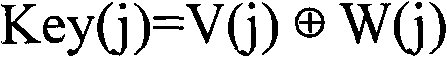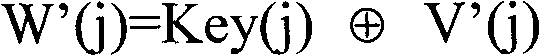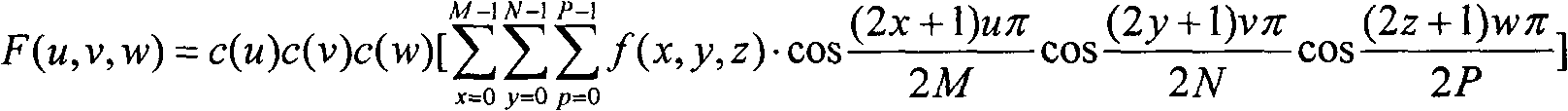Three-dimensional discrete cosine transform (DCT)-based geometric attack resistant volume data watermark realization method
A technology of anti-geometric attack and implementation method, applied in the field of multimedia signal processing, to achieve strong anti-geometric attack ability, strong anti-conventional attack ability, and wide application range
Inactive Publication Date: 2011-06-15
HAINAN UNIVERSITY
View PDF4 Cites 11 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
In short, the algorithm for embedding a digital watermark in 3D volume data that is resistant to geometric attacks such as rotation, scaling, translation, shearing, and distortion is still blank and has not been publicly reported.
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses a three-dimensional discrete cosine transform (DCT)-based geometric attack resistant volume data watermark realization method, which belongs to the field of multimedia signal processing. The method comprises the steps of watermark embedding and watermark extraction. The watermark embedding step further comprises the following steps of: (1) performing global three-dimensional DCT on original volume data, and extracting a geometric attack resistant characteristic vector from a transform coefficient; and (2) obtaining a binary logic sequence through a Hash function by utilizing the characteristic vector and watermarks to be embedded, and storing the binary sequence to a third party. The watermark extraction step further comprises the following steps of: (3) performing the global three-dimensional DCT on tested volume data, and extracting the geometric attack resistant characteristic vector from the object; and (4) extracting the watermarks by utilizing the characteristics of the Hash function and the binary logic sequence stored in the third party. The method relates to a three-dimensional DCT-based volume data digital watermarking technology, is proved by experiments to have relatively higher geometric and conventional attach resistance, also relates to a zero-watermark technology, and avoids the watermark embedding changing the contents of the volume data.
Description
A Realization Method of Volume Data Watermarking Based on 3D DCT Against Geometry Attack technical field The invention relates to a digital watermark technology based on three-dimensional DCT transformation and volume data image features, is a multimedia data protection method, and belongs to the field of multimedia signal processing. technical background With the rapid development of digital technology and Internet technology, various digital media such as text, image, sound, video, etc. can be transmitted quickly and conveniently through the Internet. It also makes the tampering and piracy of these information very easy. How to protect the copyright of digital products and maintain the security of network information has become a top priority. As an effective means, digital watermark technology realizes the copyright protection of digital works. Therefore, this technology has become a research hotspot in the field of multimedia information security. But most research...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G06T1/00
Inventor 李京兵杜文才陈延伟
Owner HAINAN UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com