Virtual private topology control method, device and system
A technology of virtual private network and topology control, applied in the field of communication, can solve the problems of wasting network resources, ambiguity, waste of network resources, etc., and achieve the effect of saving network resources and realizing control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
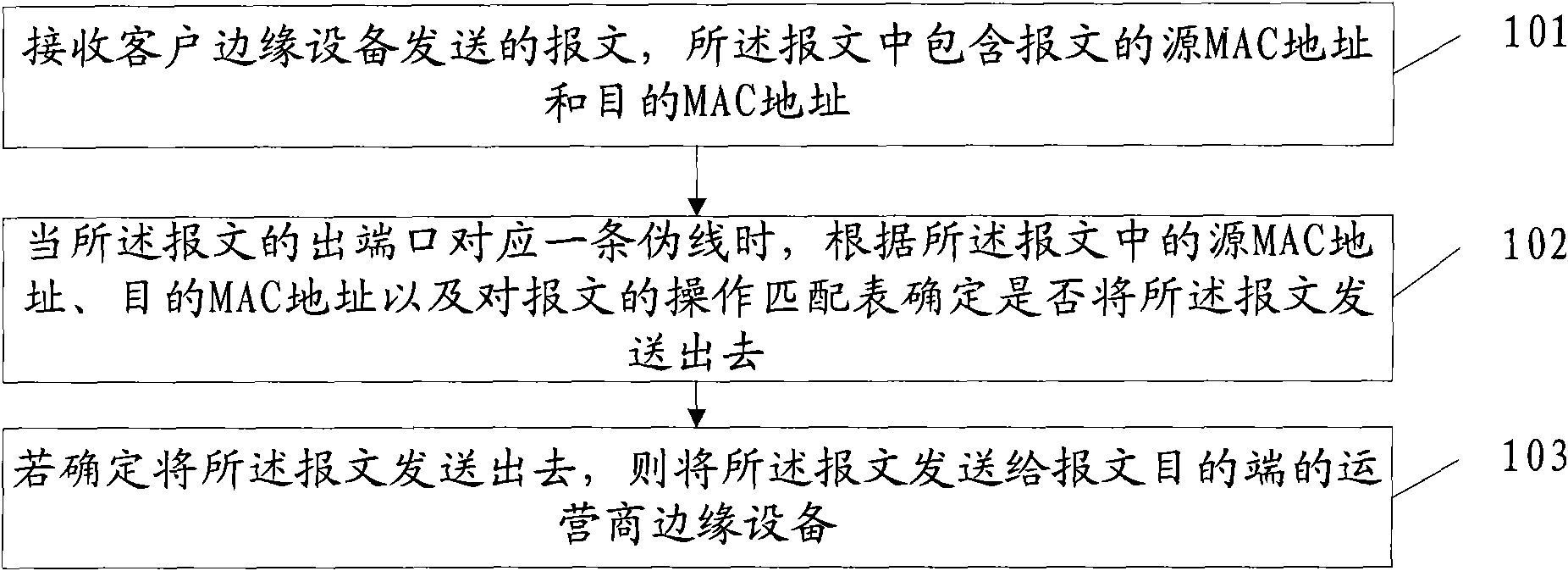
[0043] An embodiment of the present invention provides a virtual private network topology control method, such as figure 1 As shown, the method includes:
[0044] 101. Receive a packet sent by a client edge device, where the packet includes a source MAC address and a destination MAC address of the packet.
[0045] 102. When the egress port of the message corresponds to a pseudowire, determine whether to send the message according to the source MAC address, the destination MAC address in the message, and the operation matching table for the message.
[0046] Wherein, the operation matching table for the message includes: an uplink access control list or a filtering table; the uplink access control list includes a message source MAC address, a destination pseudowire, a message destination MAC address, and an operation for matching a message ; The filtering table includes the message source port attribute, the destination pseudowire, the port attribute of the remote operator's e...
Embodiment 2
[0056] The embodiment of the present invention provides a virtual private network topology control method, the method is a message source end virtual private network topology control method, specifically, the message source PE (Provider Edge, operator edge equipment) according to the upstream ACL (Access Control List, access control list) determines whether to send out the virtual private network topology control method of the message, such as image 3 As shown, the method includes:
[0057] When implementing the embodiment of the present invention, it is first necessary to set up the uplink ACL table. After the uplink ACL table is set up, when the PE at the source end of the message receives the message sent by CE (Customer Edge, customer edge device), and determines When the outgoing port of the message is PW (Pseudo Wire, pseudowire), the PE at the source end of the message is based on the message source MAC address and message destination MAC address contained in the messa...
Embodiment 3
[0106] The embodiment of the present invention provides a virtual private network topology control method, the method is a virtual private network topology control method at the source end of the message, specifically, the PE (Provider Edge, operator edge device) at the source end of the message determines whether to The virtual private network topology control method that the message is sent out, such as Figure 8 As shown, the method includes:
[0107] When implementing the embodiment of the present invention, it is first necessary to set a filter table. After the filter table is set, when the PE at the source end of the message receives the message sent by CE (Customer Edge, customer edge device), and determines the When the outgoing port of the message is a PW (Pseudo Wire, pseudowire), the PE at the source end of the message is determined according to the message source MAC address contained in the message and the message destination MAC address and the filter table set ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com