High availability for network security devices
A technology of network equipment and high availability, which is applied in the field of computer networks, and can solve problems such as preventing the active use of high availability of IDP equipment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
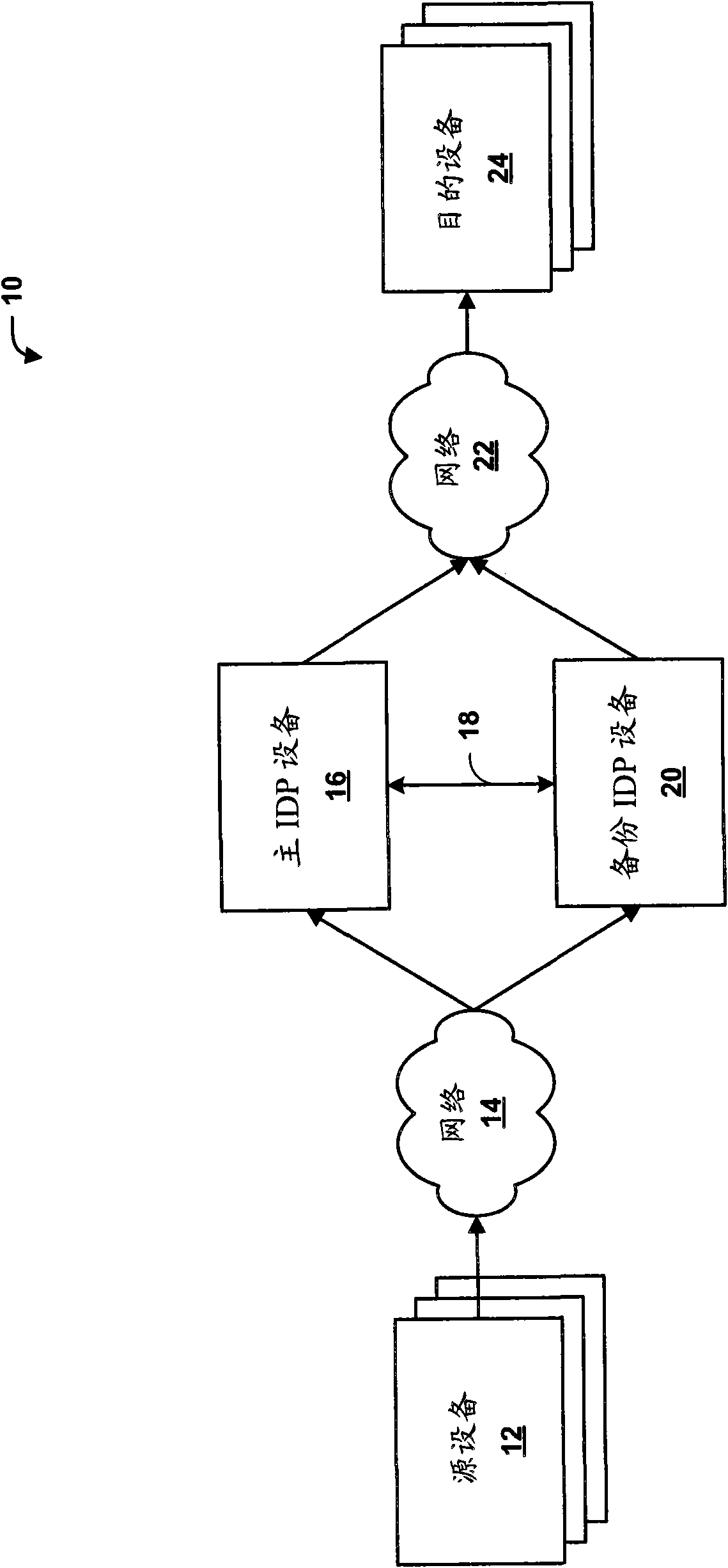
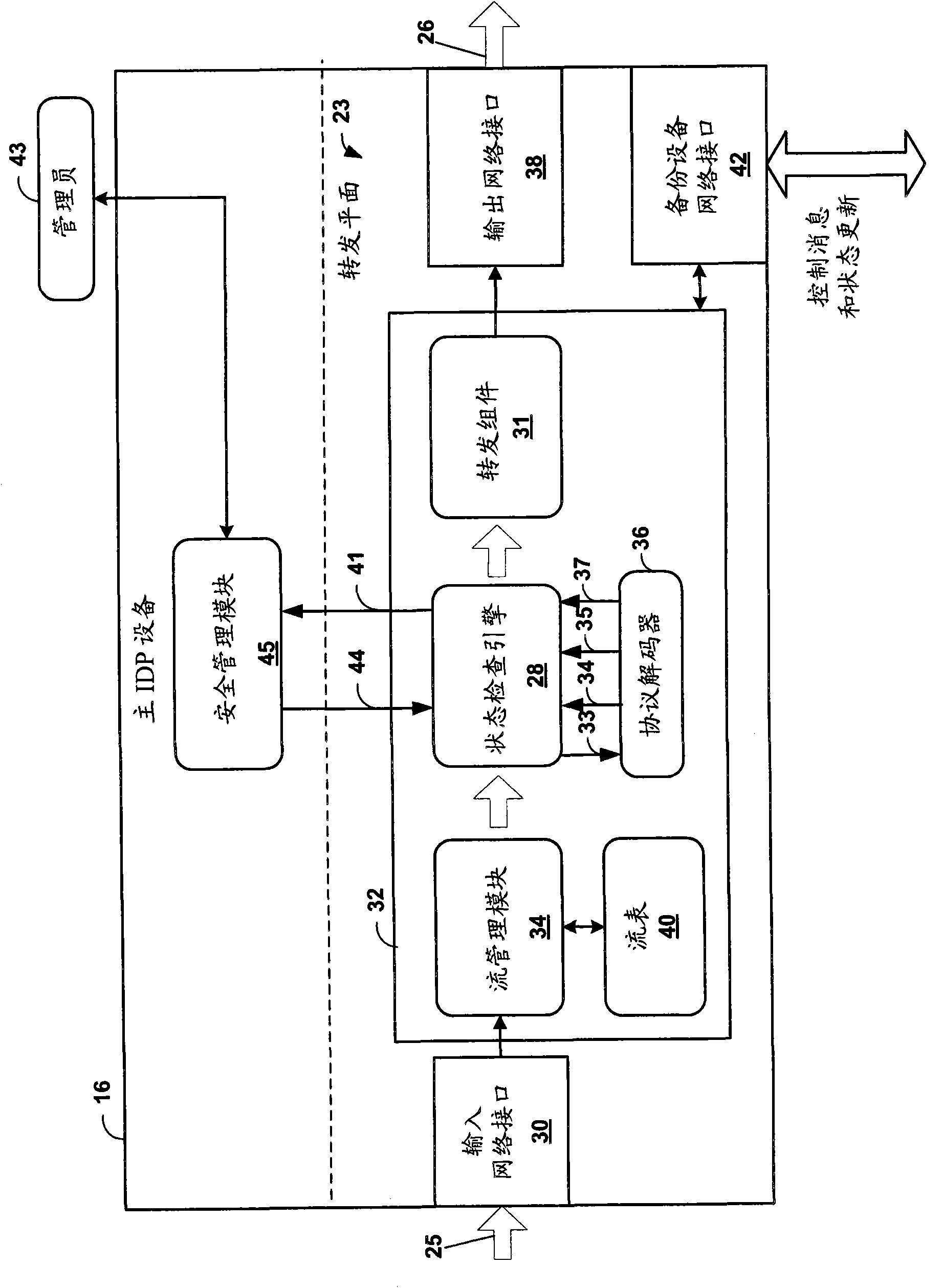
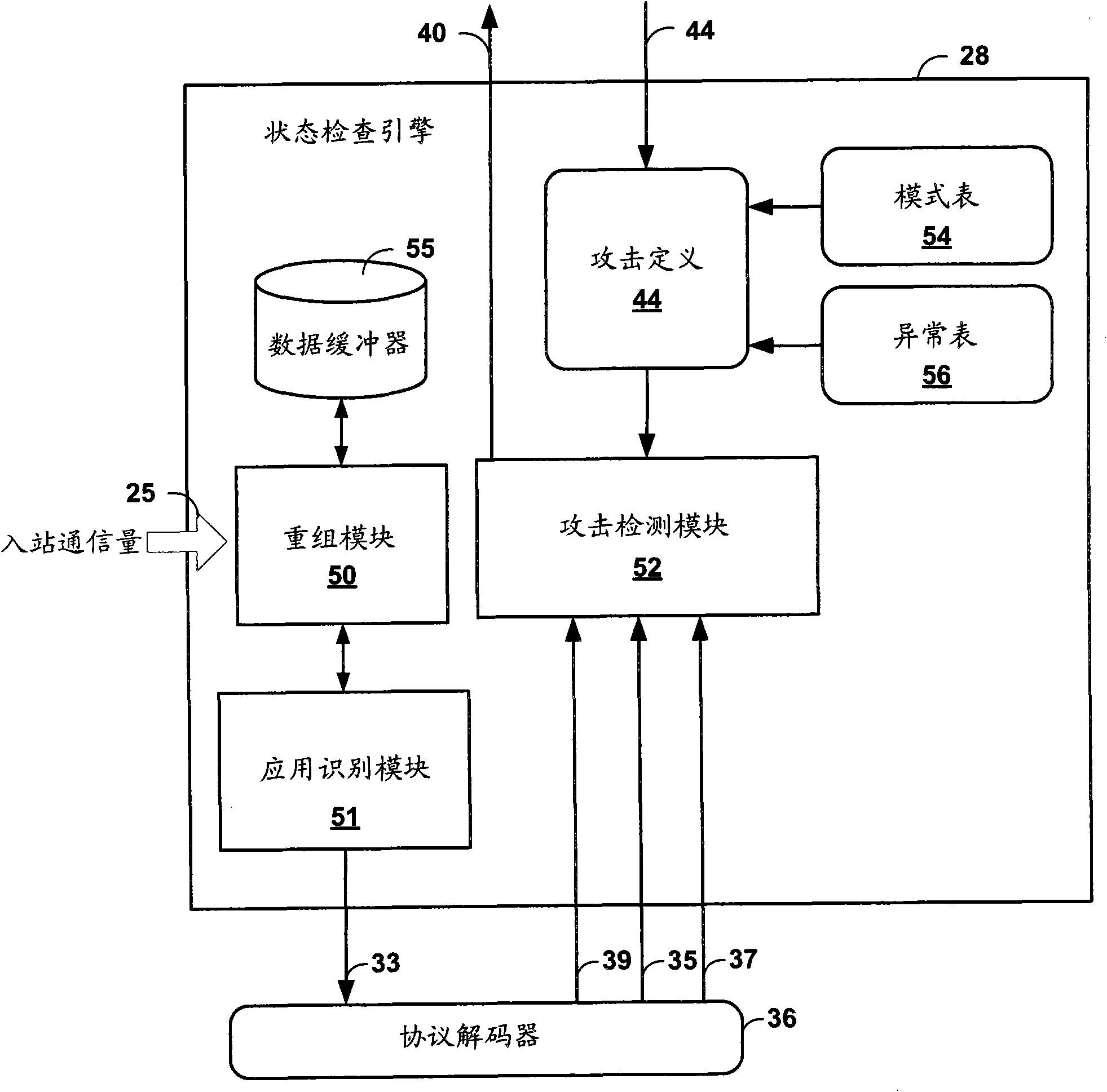
[0026] figure 1 is a block diagram illustrating an embodiment in which a primary intrusion detection and prevention (IDP) device 16 and a backup IDP device 20 provide active, high-availability IDP services within a computing environment 10 . As described herein, primary IDP device 16 and backup IDP device 20 synchronize the application layer IDP state of intercepted network sessions flowing between source device 12 and destination device 24 . Typically, primary IDP device 16 performs stateful inspection of the application layer data of the packet flow between source device 12 and destination device 24 . Each of source devices 12 may establish an application layer communication session with one or more destination devices 24, where each communication session typically includes a pair of packet flows between a source device and a destination device.
[0027] The term "packet flow" refers to a group of packets originating from a particular source device 12 and sent to a particul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com