A malicious code intrusion detection and prevention method for a mobile application
A malicious code and mobile application technology, applied in the field of malicious code intrusion detection and prevention, can solve problems such as high false positives and false negatives, rule generation dependencies, hindered analysis, etc., to improve detection capabilities, improve anti-interference capabilities, reduce The effect of false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The principles and features of the present invention will be described below in conjunction with the accompanying drawings, and the enumerated embodiments are only used to explain the present invention, and are not intended to limit the scope of the present invention.
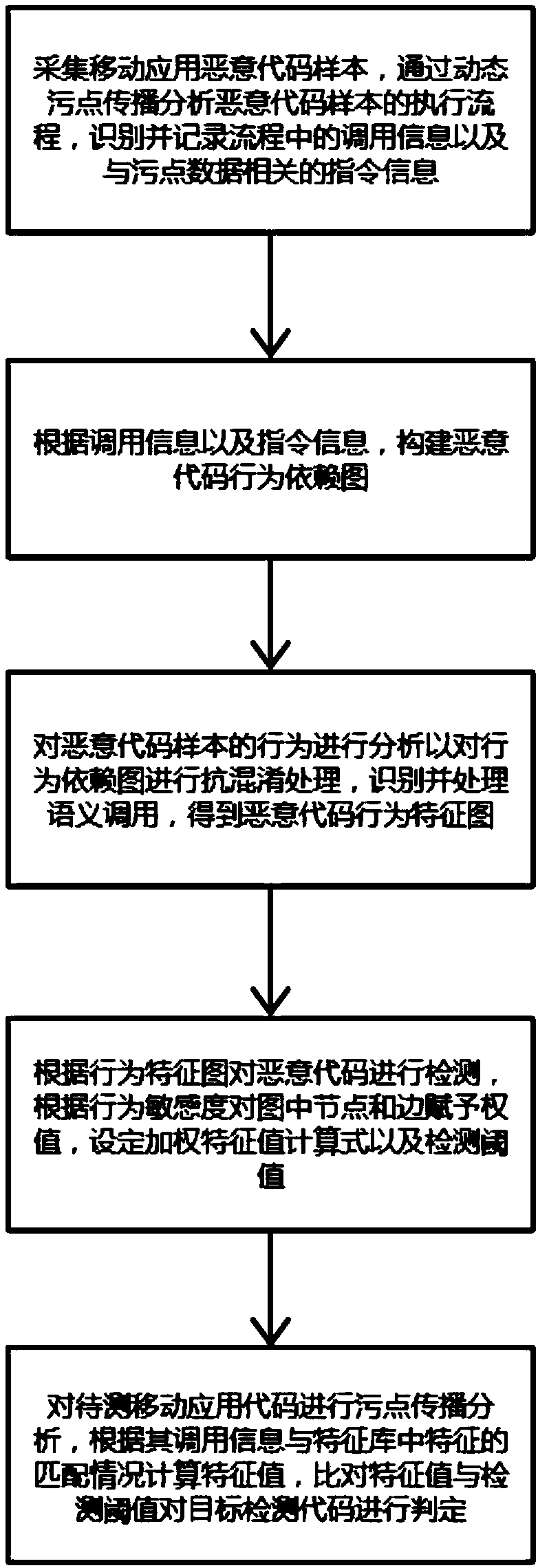
[0026] refer to figure 1 , the present invention provides a malicious code intrusion detection and prevention method for mobile applications, the method comprising the following steps:
[0027] S1. Collect mobile application malicious code samples, analyze the execution process of malicious code samples through dynamic taint propagation, identify and record the call information in the process and instruction information related to tainted data;
[0028] S2. Construct a malicious code behavior dependency graph according to the call information and instruction information;
[0029] S3. Analyze the behavior of the malicious code sample to perform anti-obfuscation processing on the behavior dependency graph...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com