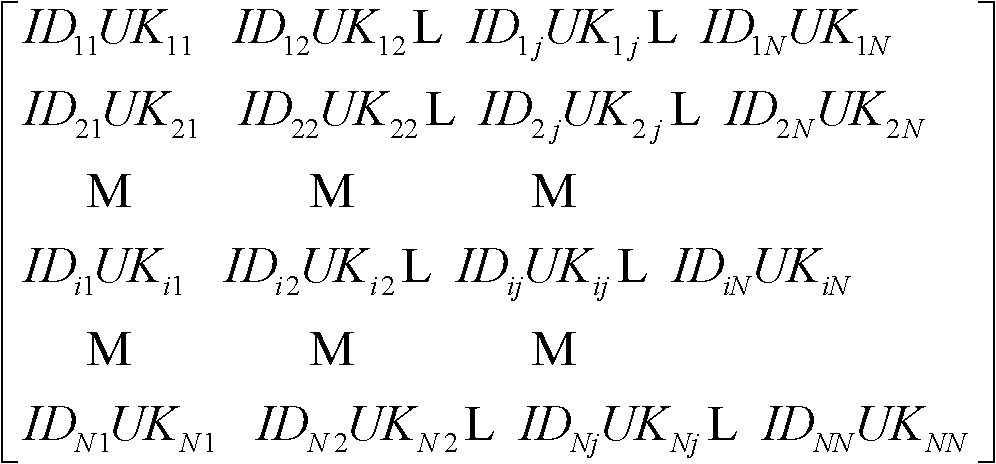Secret key management method for distributed wireless sensor network based on one-way function
A wireless sensor, one-way function technology, applied in the field of wireless network information security, can solve problems such as low key probability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The technical solutions of the present invention will be described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the embodiments.
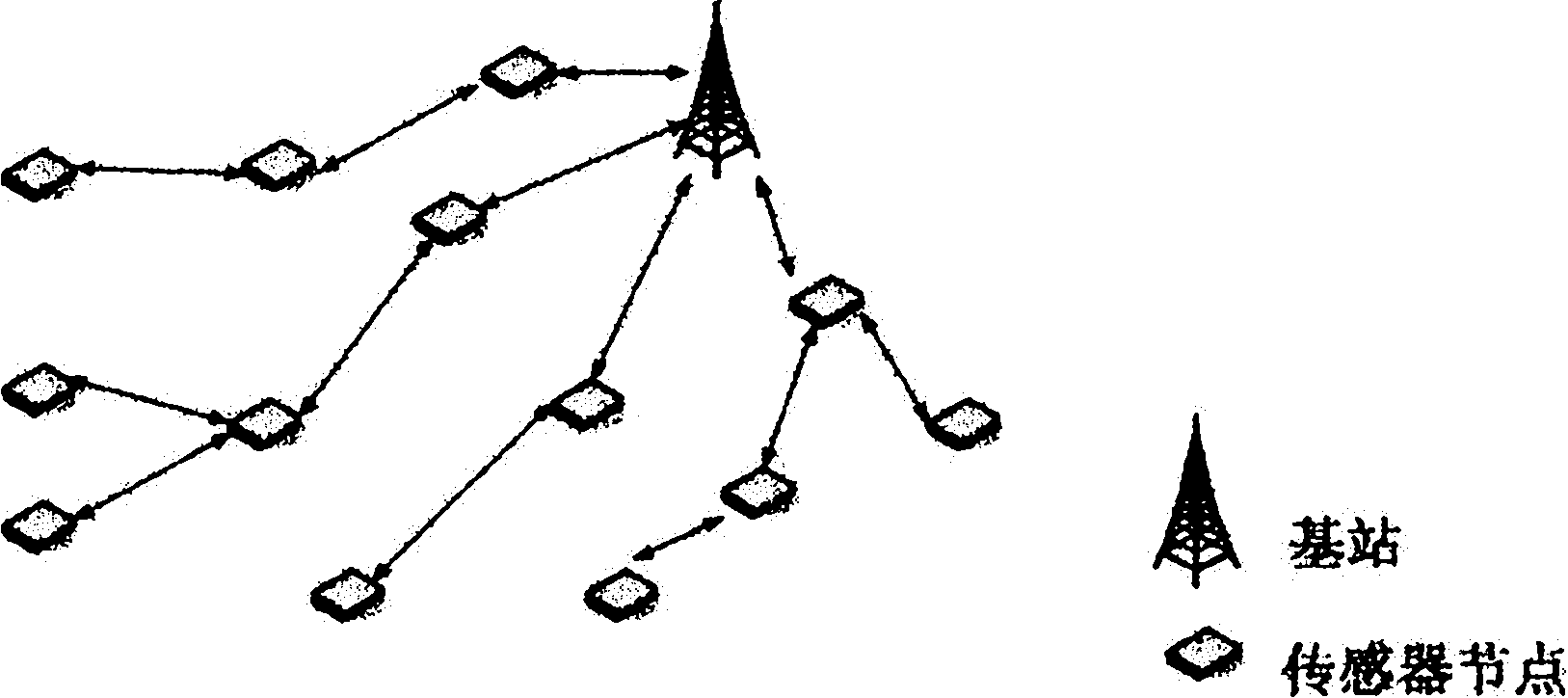
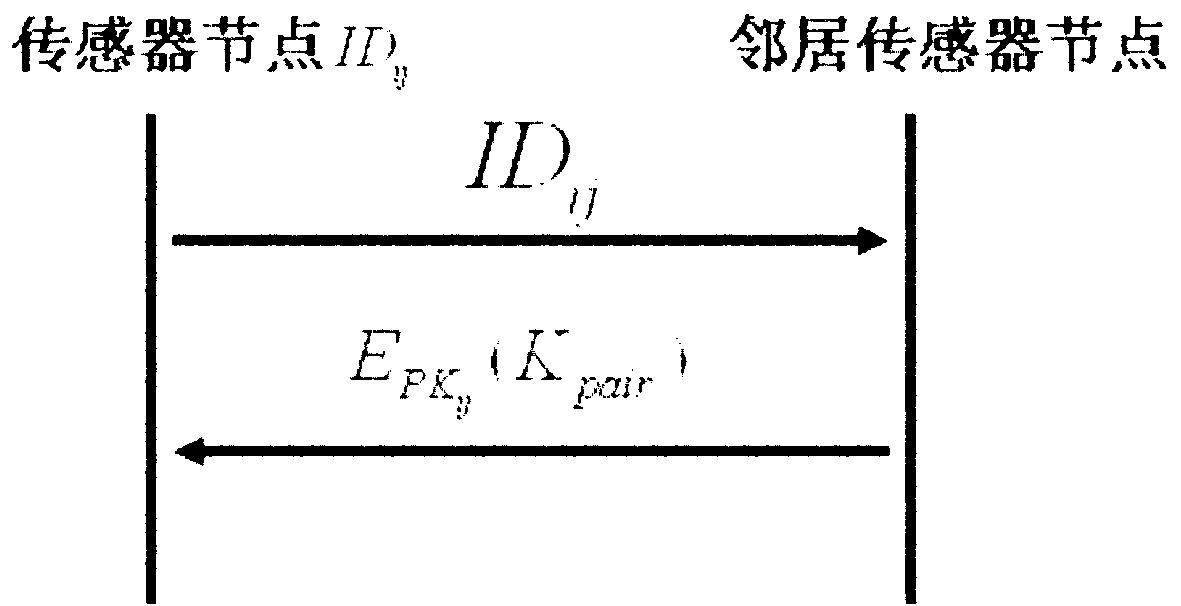
[0034] like figure 1 , figure 2 As shown, the wireless sensor network of the present invention includes two types of nodes, base station and sensor node, and each node has a unique identity number ID ij .
[0035] In the present invention, the distributed wireless sensor network includes a base station and a large number of sensor nodes; the base station is the management center of the whole network, and the data convergence center is a gateway connecting the wireless sensor network with other networks; Monitor the area, upload the collected information, complete the data transfer, and finally gather the data to the base station.
[0036] All nodes are randomly distributed in the monitored area, and the method does not depend on knowing the geographic l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com