Audio-content-based non-uniform discrete cosine transform audio reliability authentication method
A technology of discrete cosine transform and authentication method, which is applied in the field of non-uniform discrete cosine transform audio reliability authentication based on audio content, which can solve problems such as false alarms, failure to meet authentication and authentication, and inability to tamper with positioning, so as to achieve the effect of strengthening security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0032] 1. Generation of watermark.
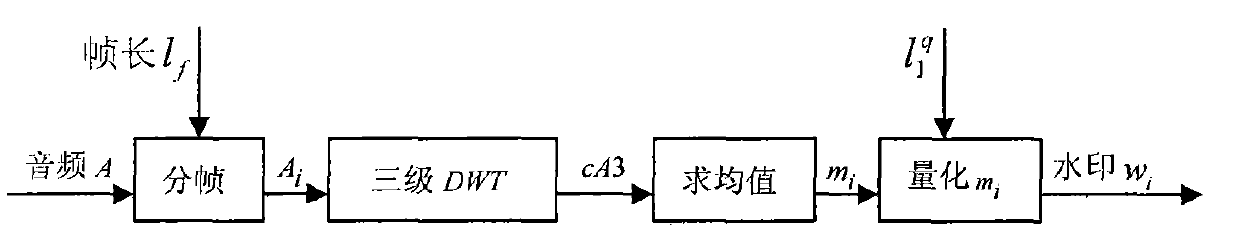
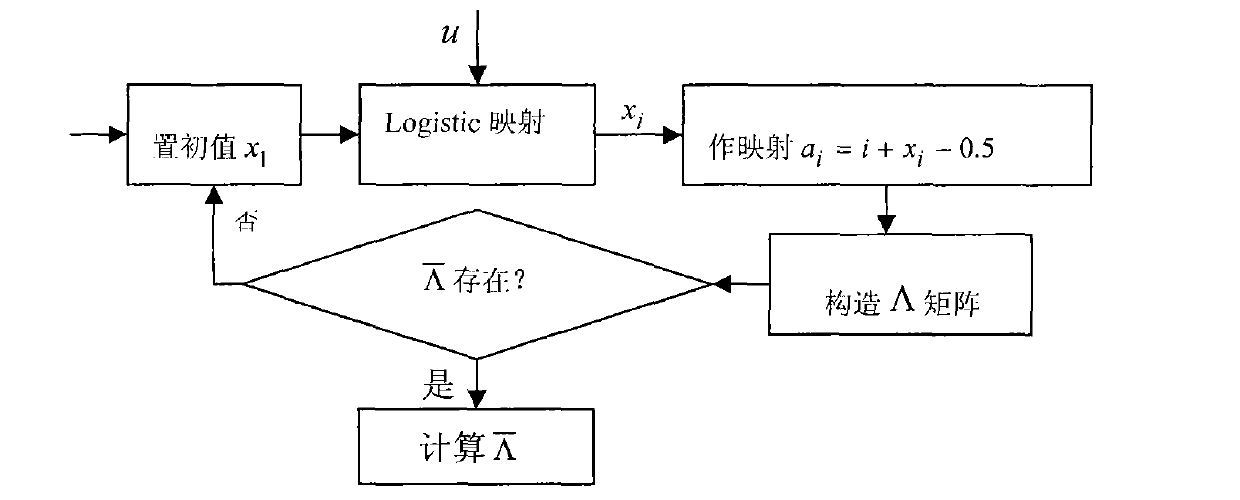
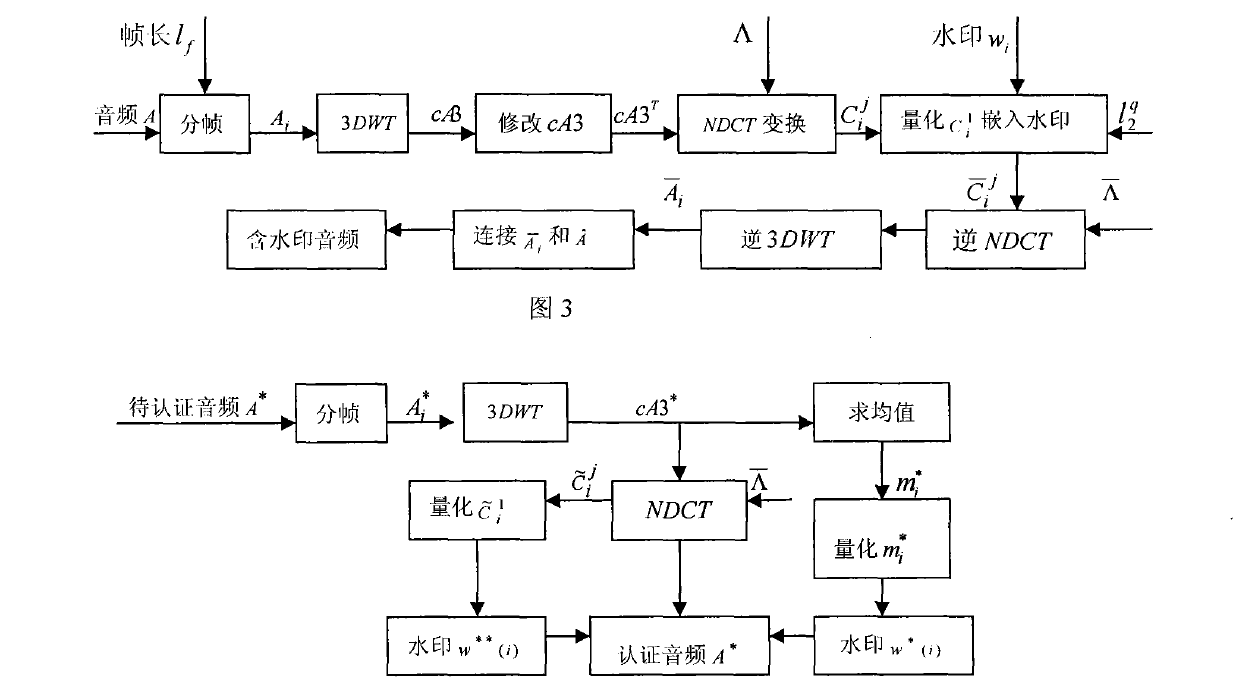
[0033] by such as figure 1 process to generate watermarks. Audio with A={a i |a i , 1≤i≤l a} means that l a is the length of the audio. frame length l f For known, in the example of the present invention l f =256. The number of frames is the length of the watermark Indicates the rounding down function, each audio frame after framing uses A i express. to A i For 3DWT, use cA3(i, j) to represent the coefficient of the approximate component after three-level wavelet decomposition, i represents the frame number, and j represents the jth wavelet coefficient of the frame, and then calculate the average value m of the approximate component cA3 of the three-level wavelet coefficient in each frame i , and according to the parity quantization principle, quantize m according to formula...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com