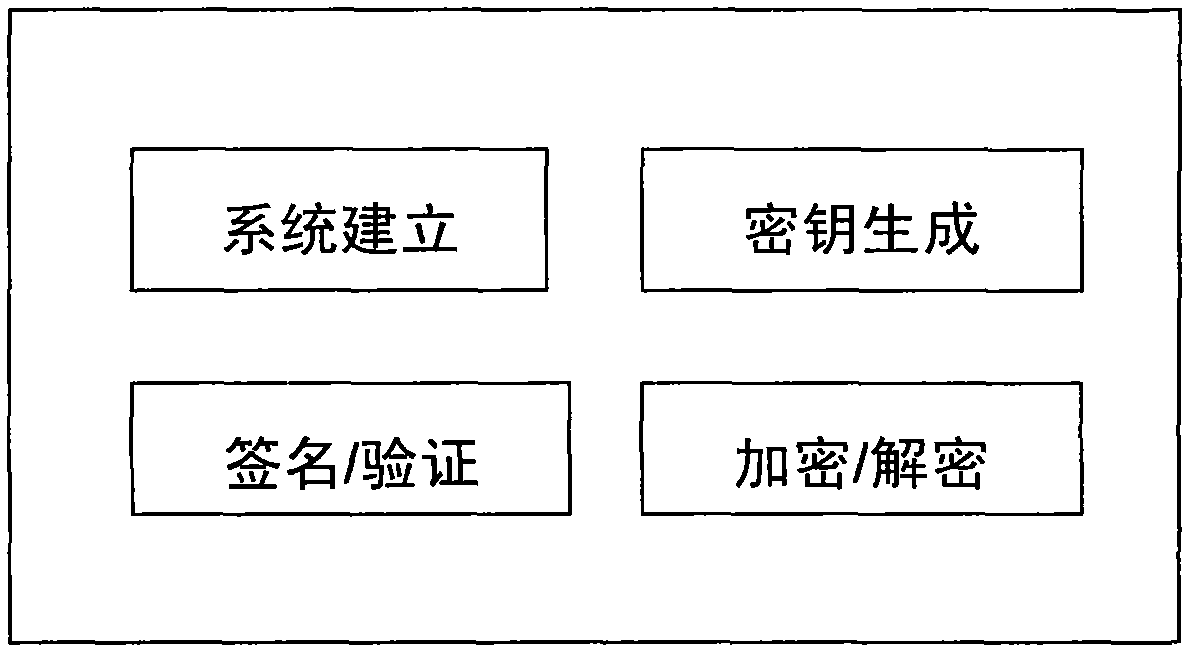
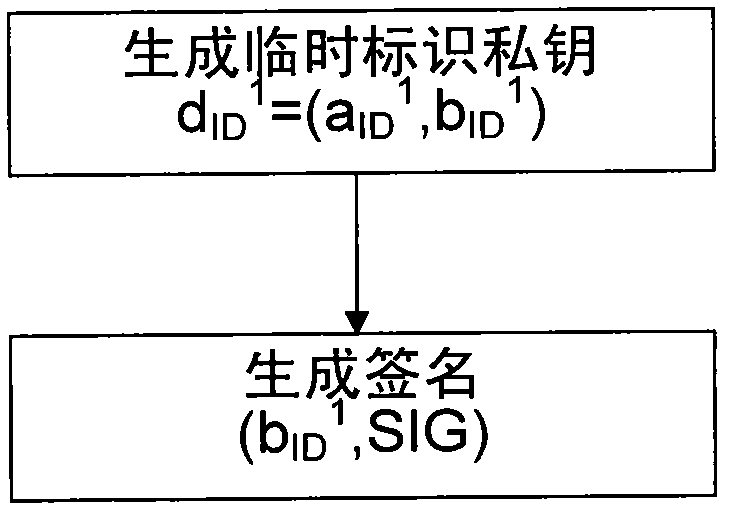
Method for constructing certificateless public key cryptography
A public key cryptography, certificateless technology, applied in the direction of public key of secure communication, user identity/authority verification, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] Various details involved in the technical solution of the present invention will be described in detail below in conjunction with specific embodiments. It should be pointed out that the described embodiments are only intended to facilitate the understanding of the present invention, rather than limiting it in any way.
[0051] Take the randomizable signature BBS04+ proposed by Zhou-Lin in "Unlinkable Randomizable Signature and Its Application in Group Signature" (Inscrypt'07, LNCS 4990, pages 328-342, 2008) as an example.
[0052] The steps to build the system are as follows:
[0053] Step 1. The key center selects the BBS04+ signature scheme;
[0054] Step 2. Select the private key of the key center as sk c =x, the public key of the key center is pk c ={p,g,g 1 , h 1 , e, w, G 1 , G 2}, where w=g 1 x , e is G 1 ×G 1 to G 2 bilinear map of
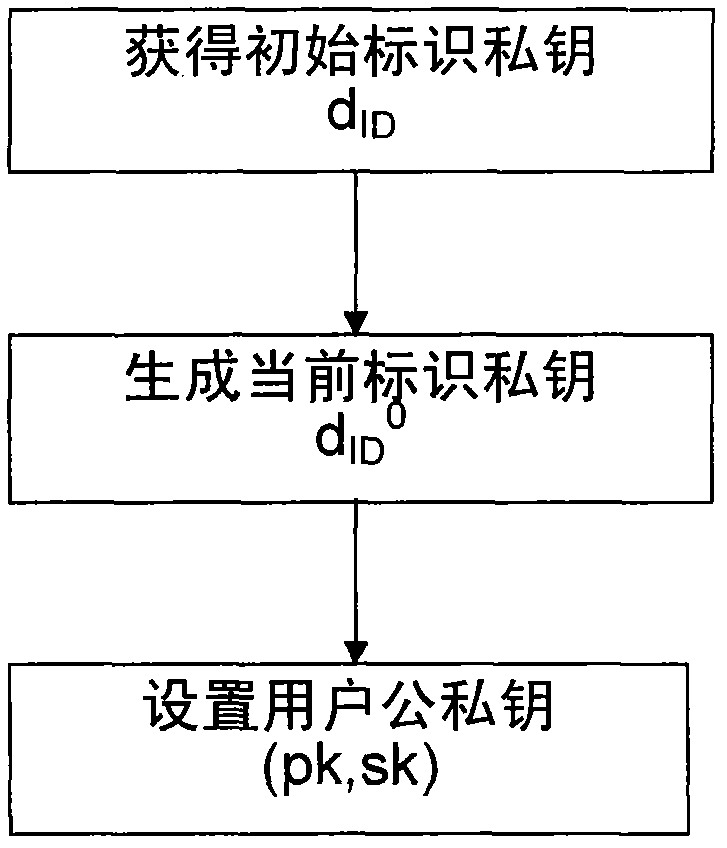
[0055] The key generation steps are as follows:
[0056] Step 1. Obtain the initial private key of identification: t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com