Encryption method for realizing support of FGAC (Fine Grained Access Control)
An access control and encryption method technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of monotonous encryption of files, complex key distribution and management, and inability to realize flexible control functions of access control technology, and achieve easy expansion and fine-grained Access control function, rich effect of access control operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
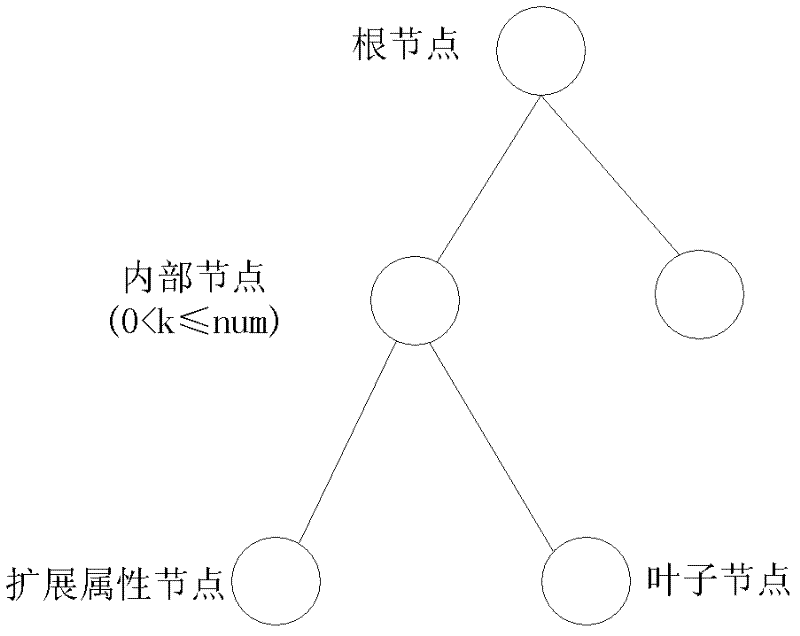
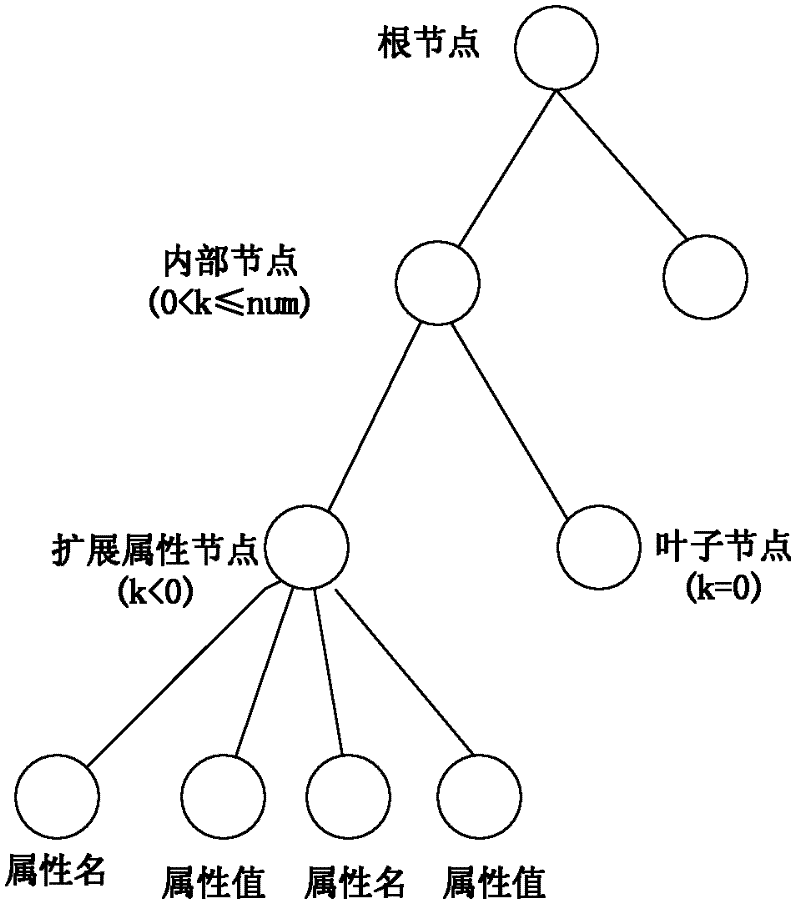
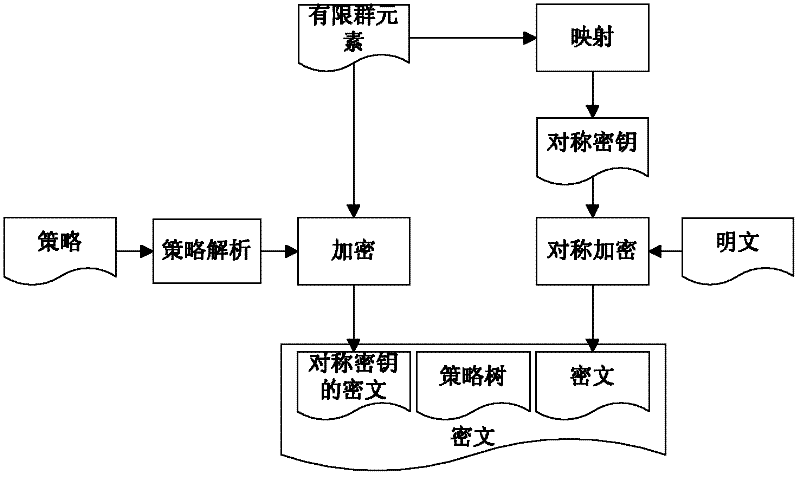
[0031] The core idea mainly included in the present invention is to realize rich access control operations by extending the access control tree in the original attribute-based encryption scheme, and using the range of the threshold value k<0 to represent the extended access control operations, so as to realize flexible, Fine-grained encryption algorithm-based access control.
[0032] Before describing the scheme, define the following entities and methods:
[0033] 1. Key Generation Center (PKG): Responsible for publishing public parameters, generating private keys, managing user attribute information and verifying extended attributes submitted by users, it must be trusted.
[0034] 2. Let the threshold of the node be k, where the range of 0
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com