Method and system for protecting digital content
A technology of digital content and digital signature, which is applied in digital transmission system, program/content distribution protection, transmission system, etc. It can solve problems such as low difficulty in cracking, difficult for authentication service center to adapt to the development of terminal equipment, and low security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
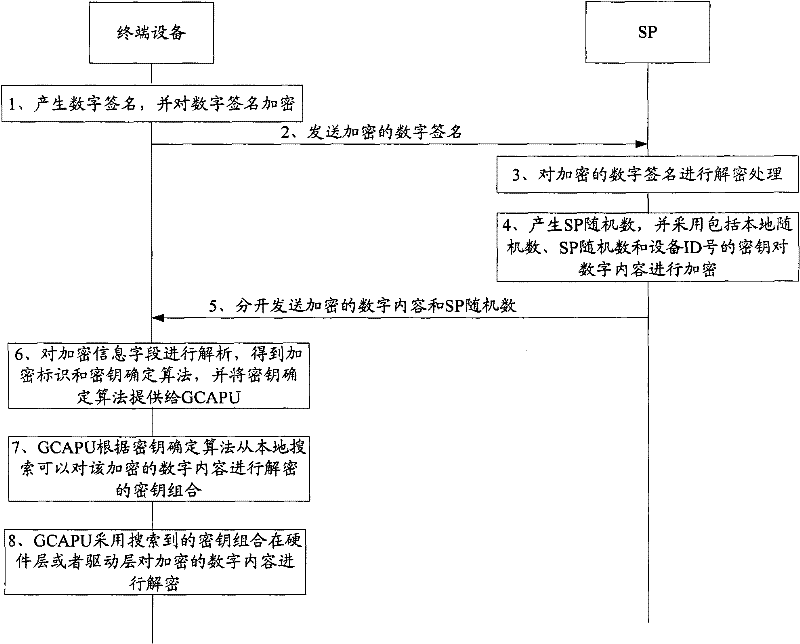
[0033] figure 2 The implementation flow of the digital content protection method provided by the first embodiment of the present invention is shown, and the details are as follows:
[0034] 1. The core processor of the terminal device generates a digital signature, and encrypts the digital signature to obtain an encrypted digital signature.
[0035] The digital signature includes a device identification (Identify Number, ID) number (also called a device identity authentication number) and a local random number. The device ID number is used to mark a unique terminal device core processor. The device ID number consists of binary codes with a length of several bits. When the core processor leaves the factory, it will be programmed and burned into the device ID number at one time. After the core processor leaves the factory, the device ID number will not be changed. The field of the device ID number mainly includes two parts, that is, the device type and the device serial numb...
Embodiment 2
[0059] image 3 The implementation flow of the digital content protection method provided by the second embodiment of the present invention is shown, and the details are as follows:
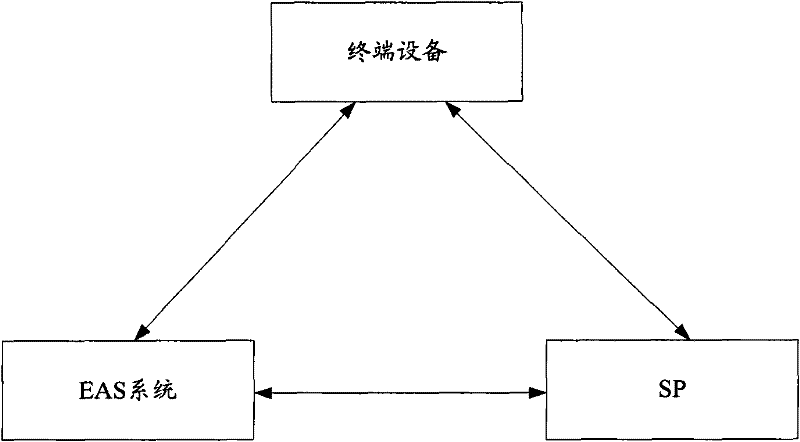
[0060] In order to further improve the difficulty of deciphering digital signatures including device ID numbers and local random numbers, isolate the communication relationship between the encryption and decryption algorithms between SP and terminal equipment suppliers, reduce the complexity of the encryption algorithm of terminal equipment, and facilitate terminal equipment The upgrade and maintenance of the encryption algorithm reduces the calculation burden of the SP decrypting the digital signature. In the embodiment of the present invention, the digital signature is decrypted through the EAS system.
[0061] Among them, the EAS system is a system with powerful decryption computing capability and security notification capability, which is used to decrypt digital signatures. When the digital ...
Embodiment 3
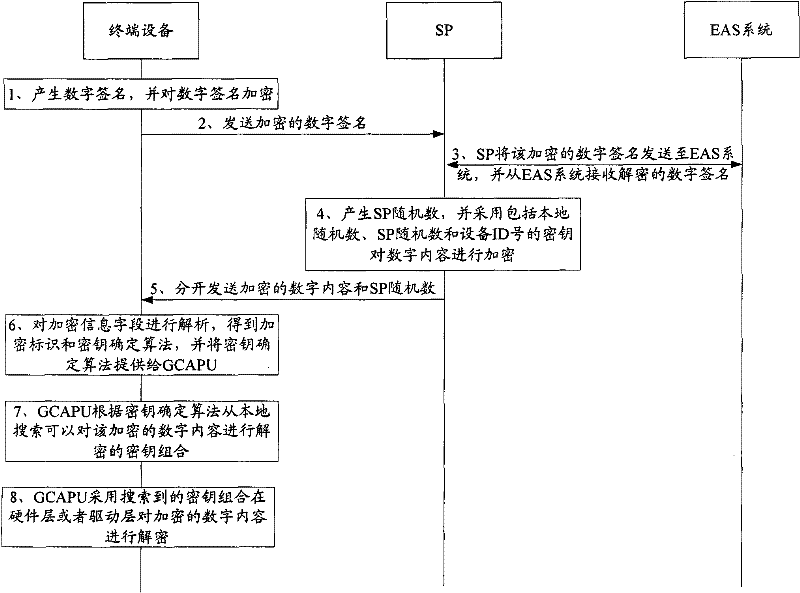
[0079] Figure 4 The implementation flow of the digital content protection method provided by the third embodiment of the present invention is shown, and the details are as follows:
[0080] 1. The terminal device generates a digital signature through its GCAPU, and encrypts the digital signature to obtain an encrypted digital signature. The specific steps are as described above and will not be repeated here.
[0081] 2. The terminal device sends the encrypted digital signature to the SP, so as to request the SP to download the specified digital content.
[0082] 3. The SP sends the encrypted digital signature to the EAS system, and receives the decrypted digital signature from the EAS system. The decrypted digital signature includes a device ID number and a local random number.
[0083] In another embodiment of the present invention, this step may also be replaced by the SP decrypting the received encrypted digital signature to obtain a digital signature including the devi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com