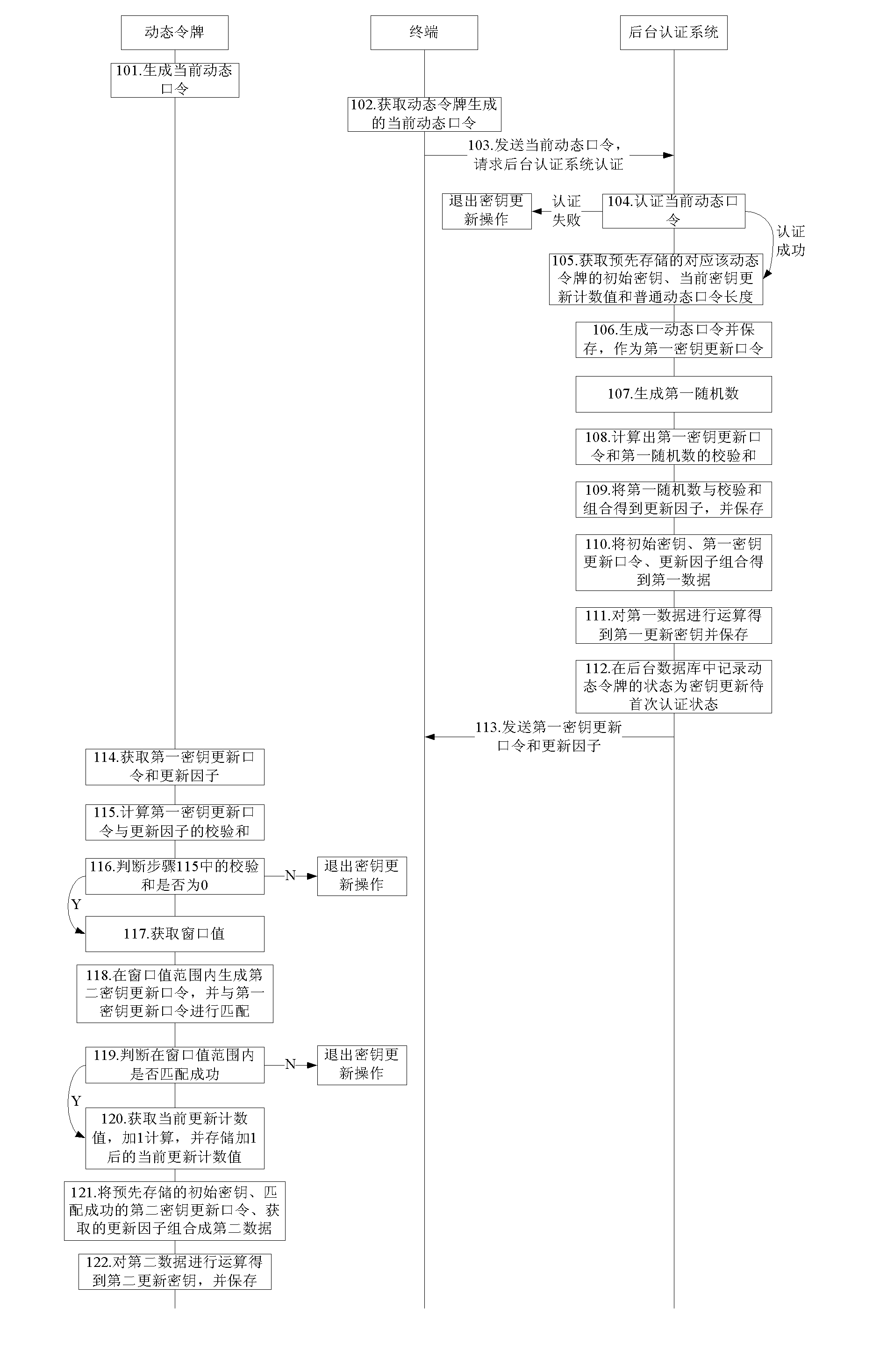Method for updating key and system
A technology for renewing keys and renewing keys, which is applied in the field of information security to achieve the effect of improving security and flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0030] Embodiment 1 of the present invention provides a method for updating a key.
[0031] see figure 1 ,Specific steps are as follows:
[0032] Step 101: the dynamic token generates the current dynamic password;
[0033] Specifically, in this embodiment, when the user applies for a key update service to the terminal, the terminal prompts the user to input a dynamic password;
[0034] Step 102: the terminal obtains the current dynamic password generated by the dynamic token;
[0035] Step 103: The terminal sends the current dynamic password to the background authentication system, and requests the background authentication system to authenticate the current dynamic password;
[0036] Step 104: the background authentication system authenticates the current dynamic password, and if the authentication succeeds, step 105 is executed, and if the authentication fails, the key update operation is exited;
[0037] Step 105: the background authentication system obtains the pre-sto...
Embodiment 2
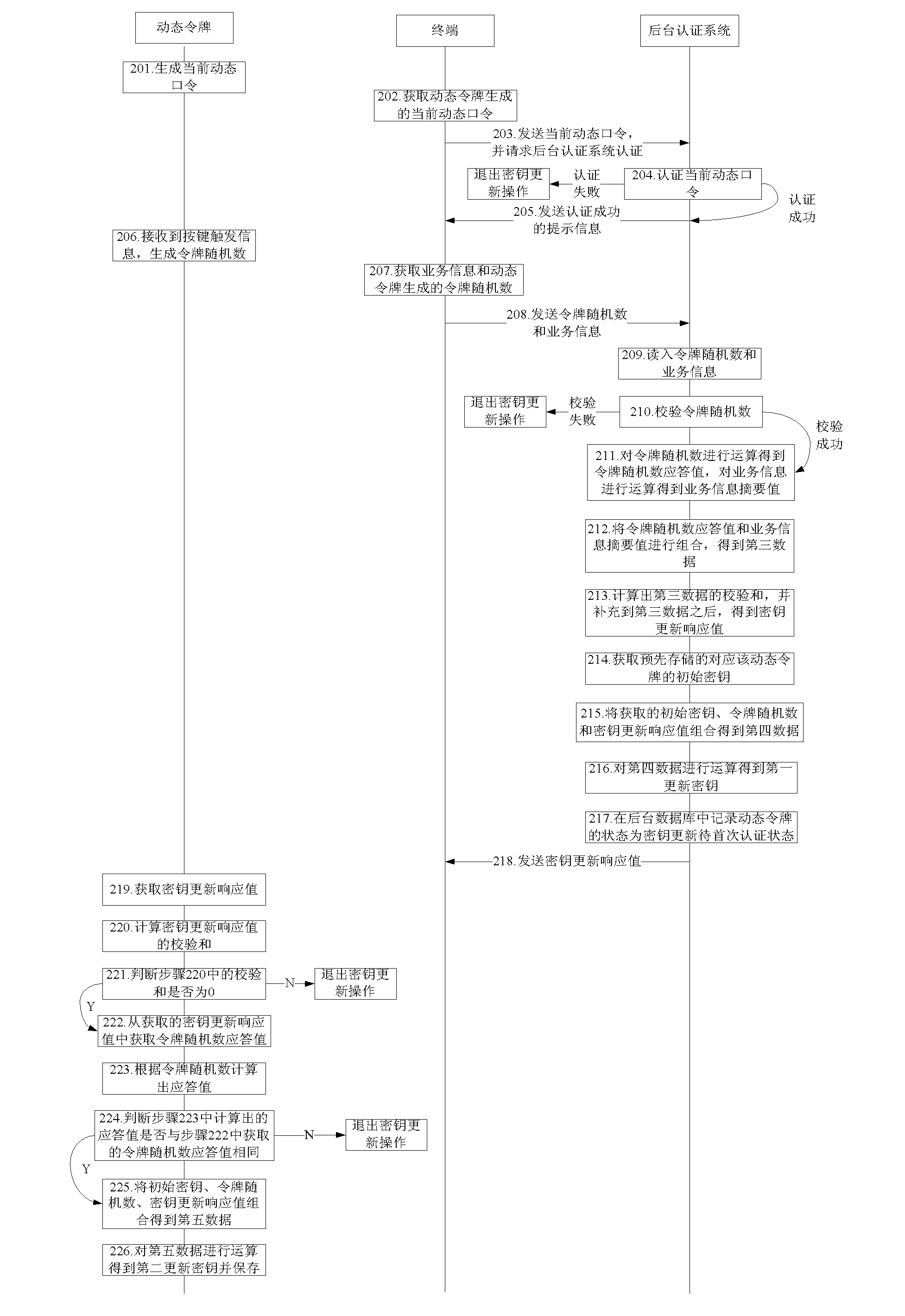
[0091] Embodiment 2 of the present invention provides another method for updating keys.
[0092] see figure 2 ,Specific steps are as follows:
[0093] Step 201: the dynamic token generates the current dynamic password;
[0094] Specifically, in this embodiment, when the user applies for a key update service to the terminal, the terminal prompts the user to input a dynamic password;
[0095] Step 202: the terminal acquires the current dynamic password generated by the dynamic token;
[0096] Step 203: The terminal sends the current dynamic password to the background authentication system, and requests the background authentication system to authenticate the current dynamic password;
[0097] Step 204: the background authentication system authenticates the current dynamic password, and if the authentication succeeds, step 205 is executed, and if the authentication fails, the key update operation is exited;
[0098] Step 205: the background authentication system returns the ...
Embodiment 3
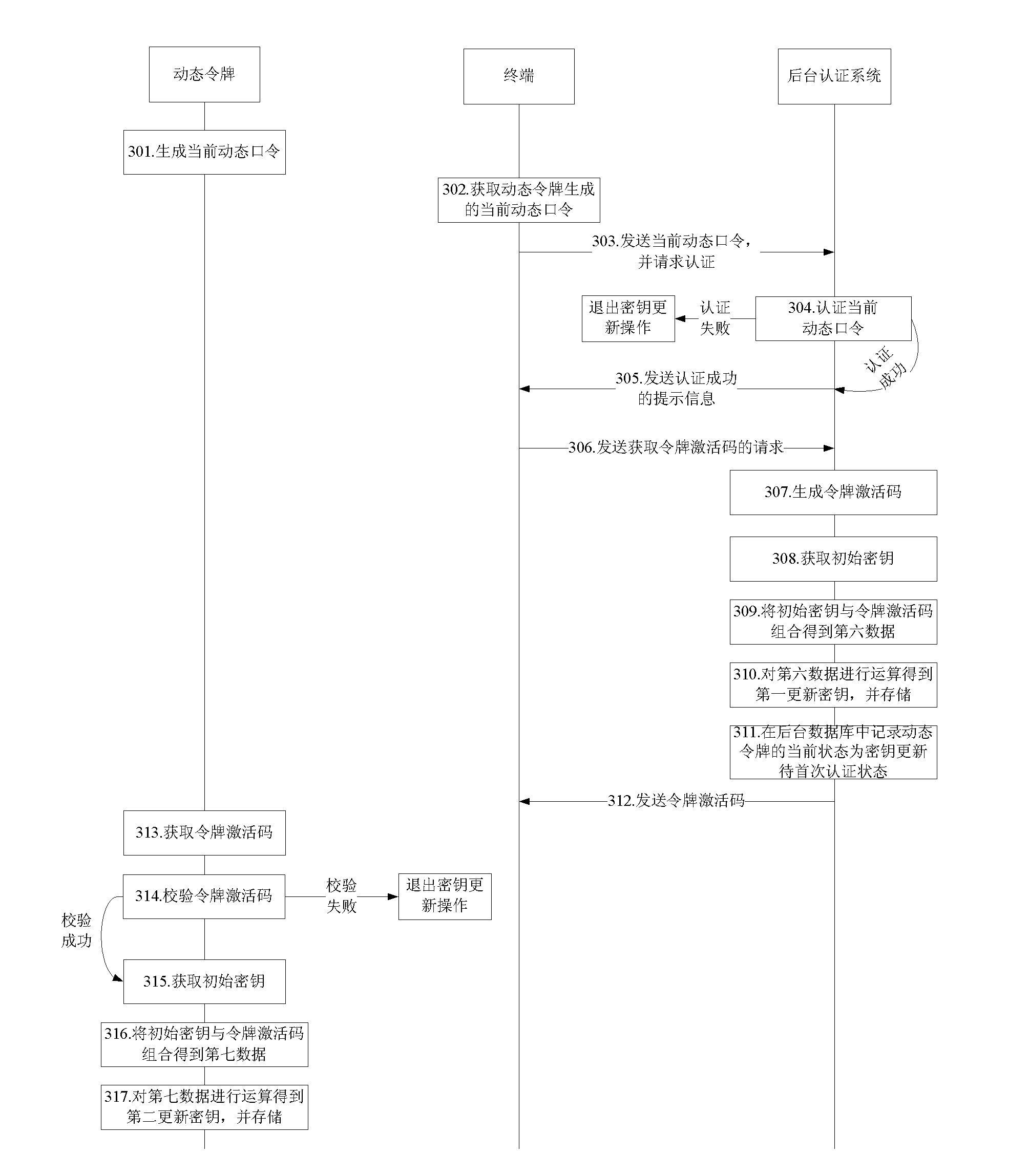
[0147] Embodiment 3 of the present invention provides yet another method for updating keys.
[0148] see image 3 ,Specific steps are as follows:
[0149] Step 301: the dynamic token generates the current dynamic password;
[0150] Specifically, in this embodiment, when the user applies for a key update service to the terminal, the terminal prompts the user to input a dynamic password;
[0151] Step 302: The terminal obtains the current dynamic password generated by the dynamic token;
[0152] Step 303: The terminal sends the current dynamic password to the background authentication system, and requests the background authentication system to authenticate the current dynamic password;
[0153] Step 304: the background authentication system authenticates the current dynamic password, and if the authentication succeeds, step 305 is executed, and if the authentication fails, the key update operation is exited;
[0154] Step 305: the background authentication system sends a pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com