Method and device for detecting malicious remote procedure call (RPC) behaviors
A technology of remote procedure call and detection method, applied in the field of computer network, can solve the problems of poor detection effect of malicious RPC behavior and many false negatives, and achieve the effect of improving effectiveness and strengthening security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
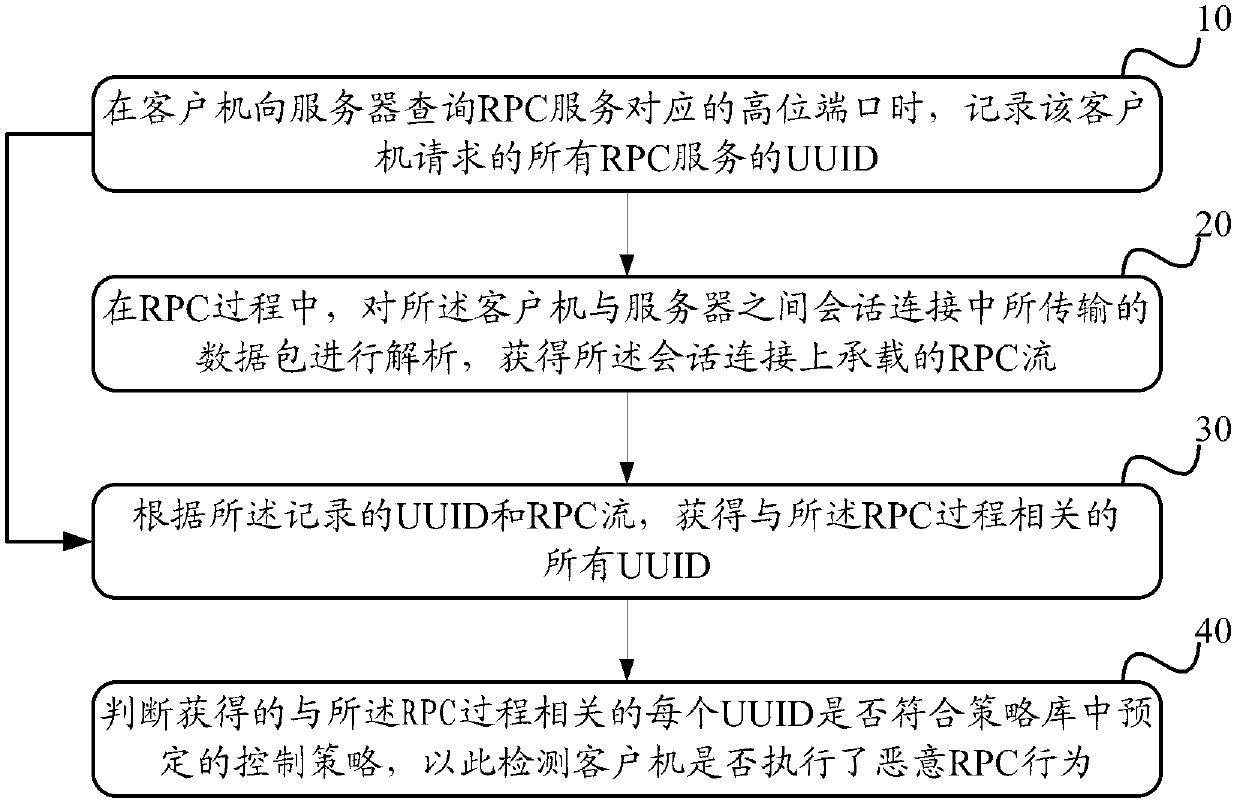
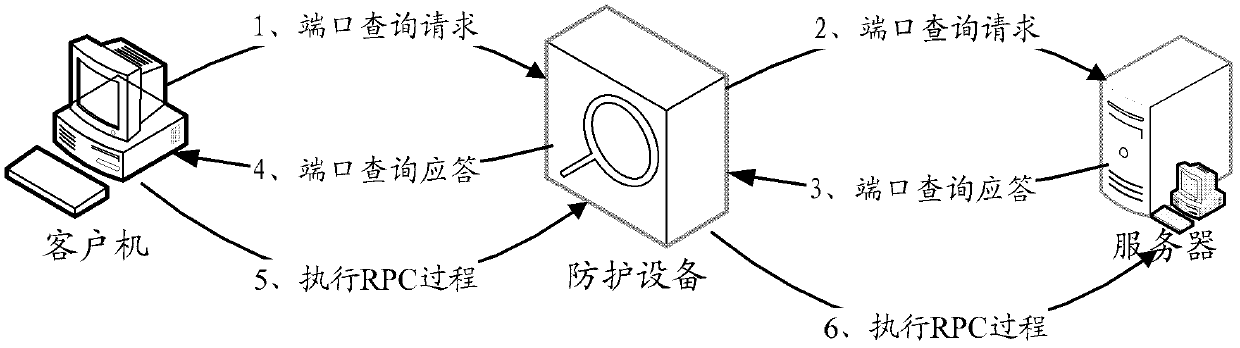
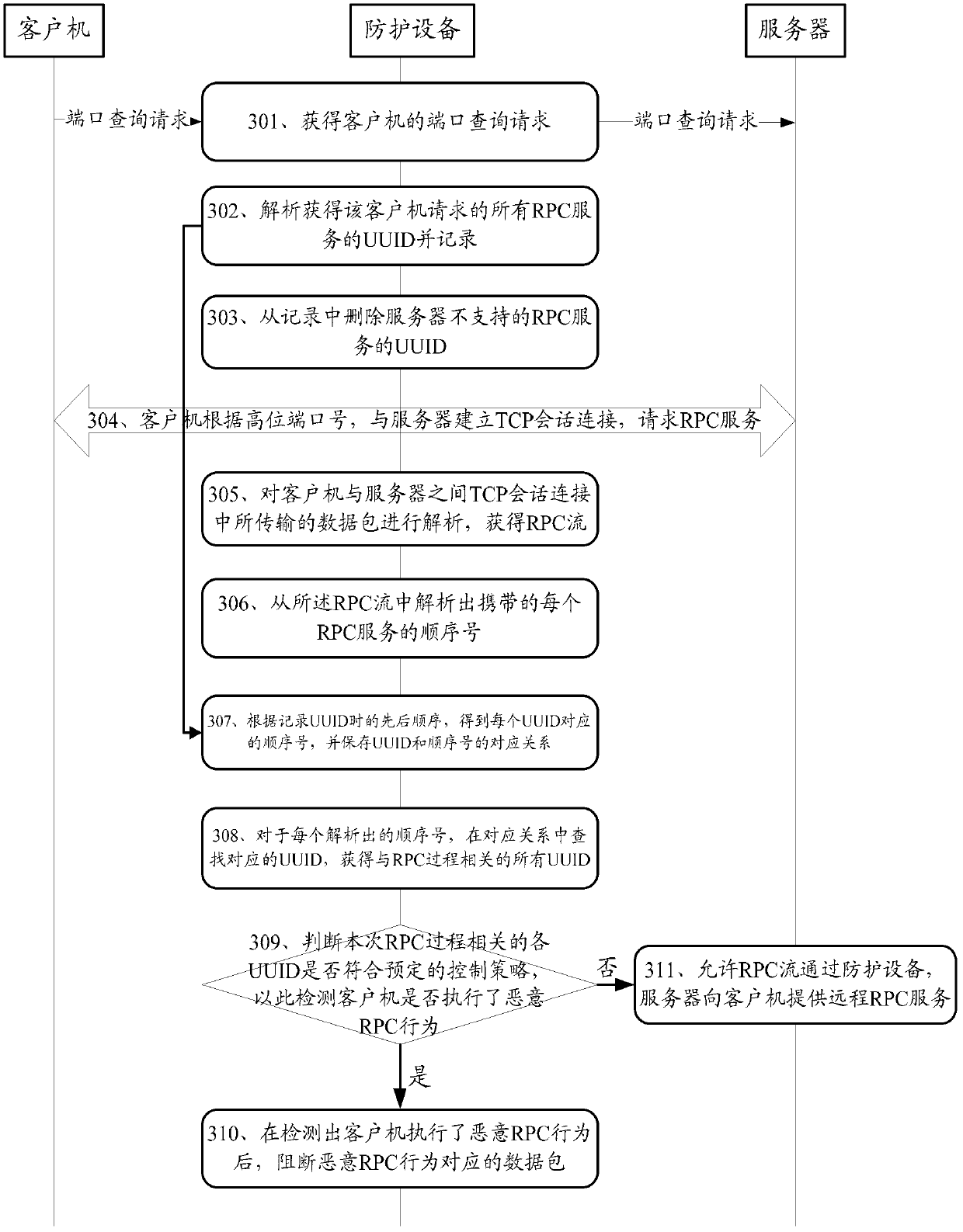
[0028] The inventor conducted an in-depth analysis of the fact that the existing IPS cannot effectively detect the malicious RPC service call behavior when multiple UUIDs are bound in the RPC process, and found that the reason is: in view of the fact that the RPC call process needs to use UUID, and the The port number corresponding to the UUID registration is a parameter, and the connection is established to provide services. Therefore, the design premise of the existing IPS is that only one UUID is bound in the process of an RPC call, that is, a TCP session connection that transmits RPC content. As long as the IPS detects the first UUID carried in it, the purpose of protecting against malicious RPC calls can be achieved.
[0029] However, a malicious client can evade detection by binding multiple UUIDs in one RPC call. As long as the RPC service corresponding to the first UUID is allowed, the IPS will determine that the RPC call is non-malicious. Malicious clients can achieve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com