Method for detecting illegal AP (Assembly Program) under centralized WLAN (Wireless Local Area Network) environment
A detection method and centralized technology, which is applied in the field of detection of illegal APs, to achieve the effect of protecting Internet security, protecting interests, and optimizing WLAN networks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
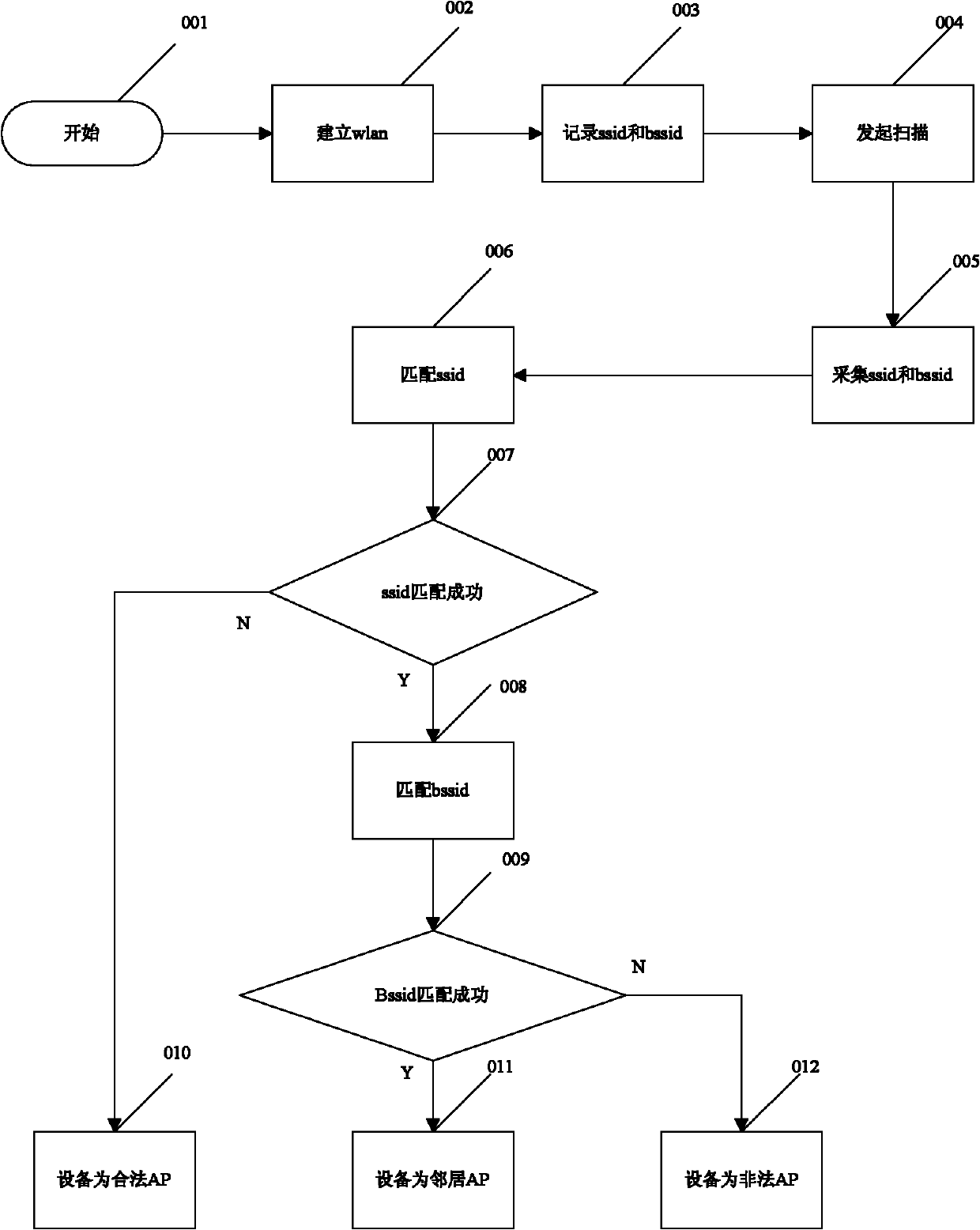
[0050] Below in conjunction with accompanying drawing and embodiment describe in detail:
[0051] 1. Detection system
[0052] 1. Overall
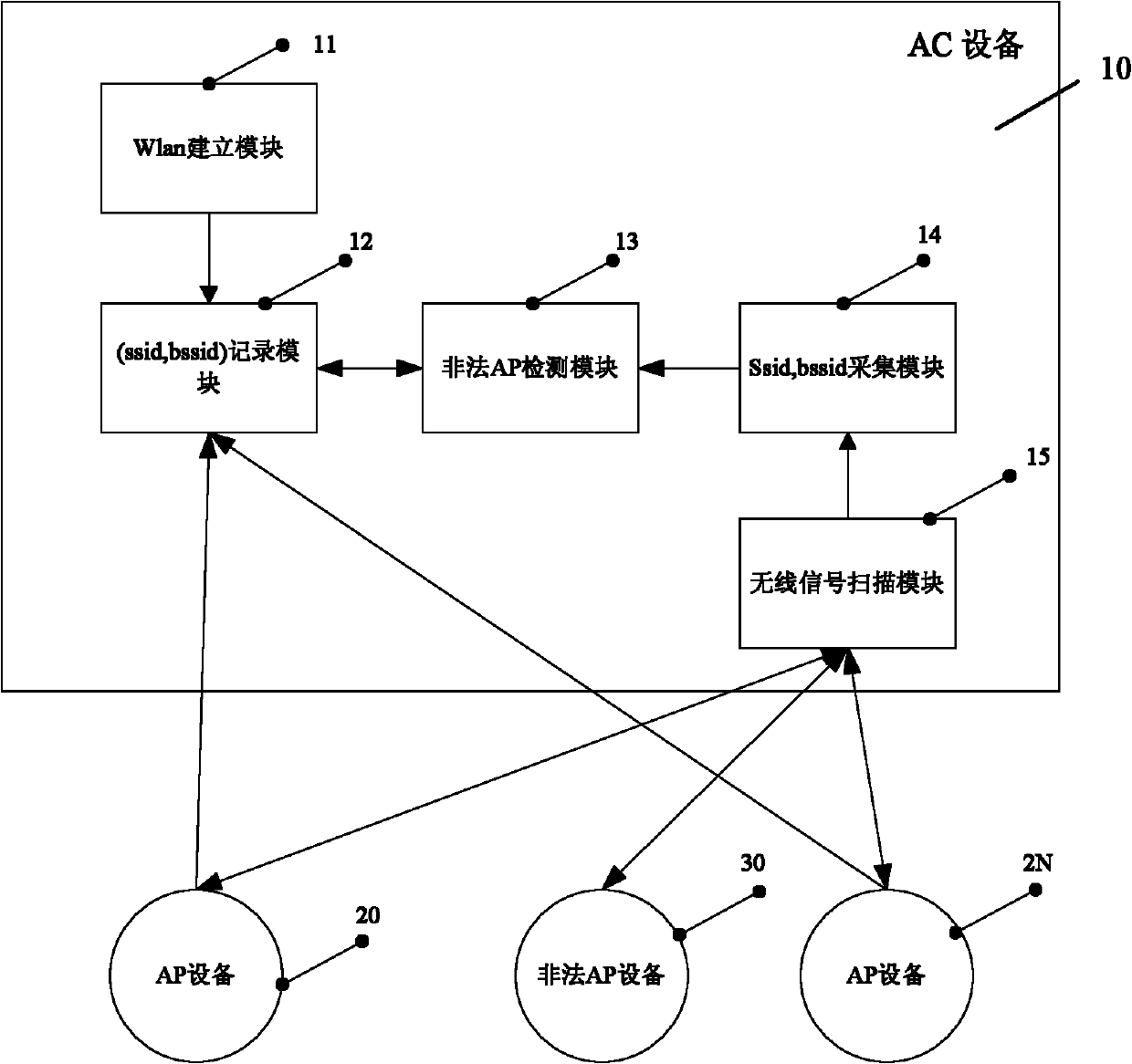
[0053] Such as figure 1 , the detection system includes an AP device 20 and an illegal AP device 30;
[0054] AC equipment 10 is provided;
[0055] The AC device 10 is a wireless controller for managing APs, establishing WLANs, and detecting illegal APs, including sequentially interacting WLAN establishment module 11, binary recording module 12, illegal AP identification module 13, collection module 14 and wireless scanning module 15;
[0056] The binary recording module 12 interacts with the AP device 20;
[0057] The wireless scanning module 15 interacts with the AP device 20 and the illegal AP device 30 respectively.
[0058] 2. Function block
[0059] 1) AC equipment 10
[0060] ① The WLAN establishment module 11 is a module for assembling and creating a message code stream of a WLAN, which is used for the AC device to send a m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com