Device for defending invasive attack
An intrusive, signal technology, applied in the direction of measuring devices, instruments, measuring electricity, etc., can solve the problem of loss of protection, and achieve the effect of improving safety and preventing leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
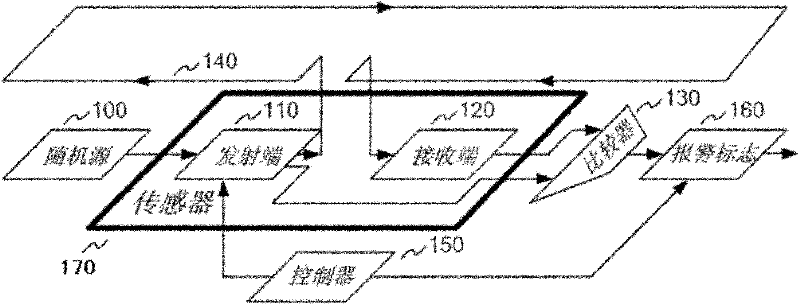
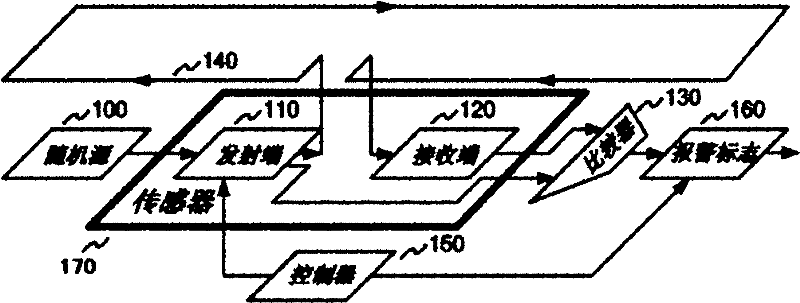
[0018] see figure 1 As shown, in an embodiment, the device for defending against invasive attacks includes: one or more metal wires 140 , a random source 100 , a comparator 130 , a sensor 170 , a controller 150 , and an alarm flag 160 .
[0019] The metal wire 140 covers the protected circuit, one end of the metal wire 140 is connected to the signal transmitting end 110 of the sensor 170 , and the other end is connected to the signal receiving end 120 of the sensor 170 .
[0020] The controller 150 controls the sensor 170 to periodically detect the connectivity of the metal wire 140 , and when it is found that the connectivity of the metal wire 140 is abnormal, the alarm flag 160 becomes valid.
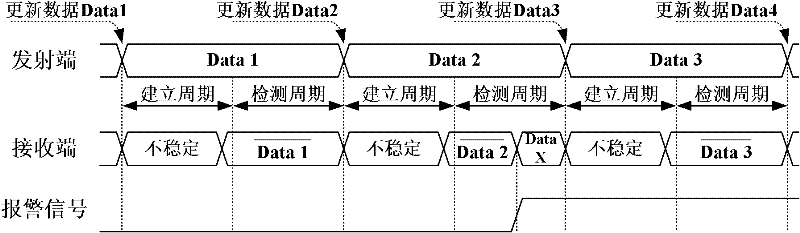
[0021] see figure 2 As shown, a detection cycle is divided into two phases - the signal establishment phase and the signal detection phase.
[0022] In the signal establishment stage, the controller 150 obtains a random signal (random number) from the random source 100, and uses th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com