Access point (AP) and method for securely connecting wireless workstation (STA) with AP
A wireless workstation and secure connection technology, applied in security devices, access restrictions, connection management, etc., can solve the problems of hidden dangers in the network and the inability to distinguish between legitimate users and illegal users, and achieve the effect of ensuring secure connections
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
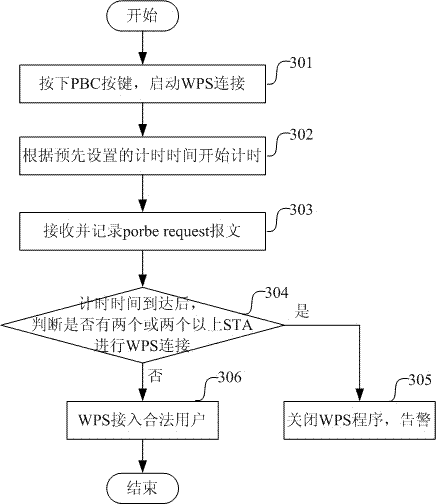
[0033] The invention provides the following technical solutions:
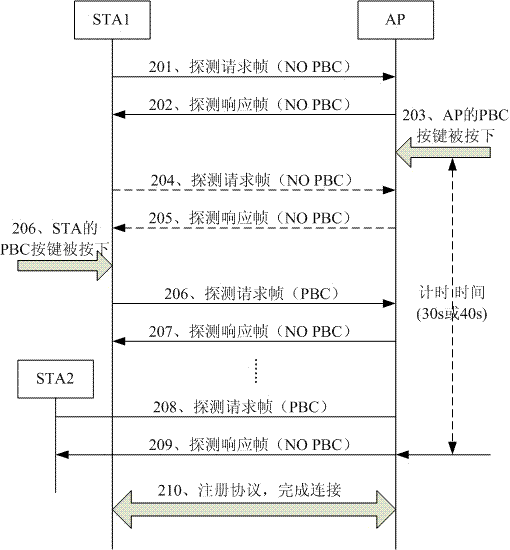
[0034] During the WPS connection process, when the AP opens the WPS connection, it starts timing, and does not perform WPS connection within the timing time. After the timing time is up, if there are two or more STAs detected within the timing time ( Workstation) opens the WPS connection, then terminates the WPS connection process.
[0035] After the timing time arrives, if it is detected that only one STA has opened the WPS connection within the timing time, the STA is allowed to perform the WPS connection, that is, completes the WPS connection with the STA.
[0036] Preferably, when the AP terminates the current WPS connection process, it also issues an alarm.
[0037] The timing time is a delay time preset on the AP, preferably greater than or equal to 30 seconds and less than or equal to 60 seconds.
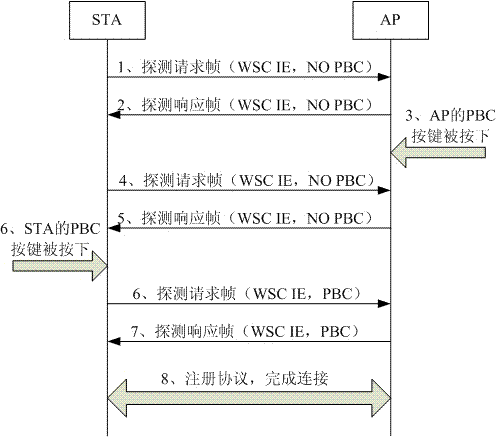
[0038] During this period of time, after receiving the probe response message with PBC information (the P...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com