Globally valid measured operating system launch with hibernation support
A technology for computing equipment and log files, used in transmission systems, digital transmission systems, security communication devices, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
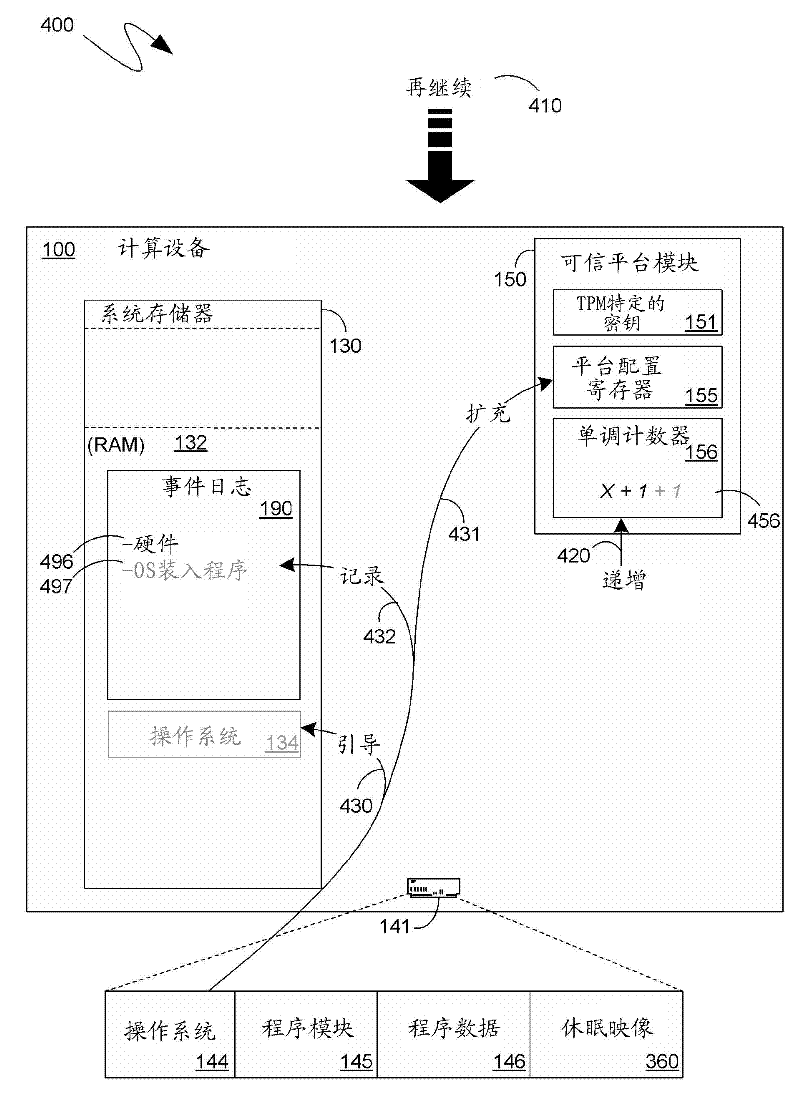
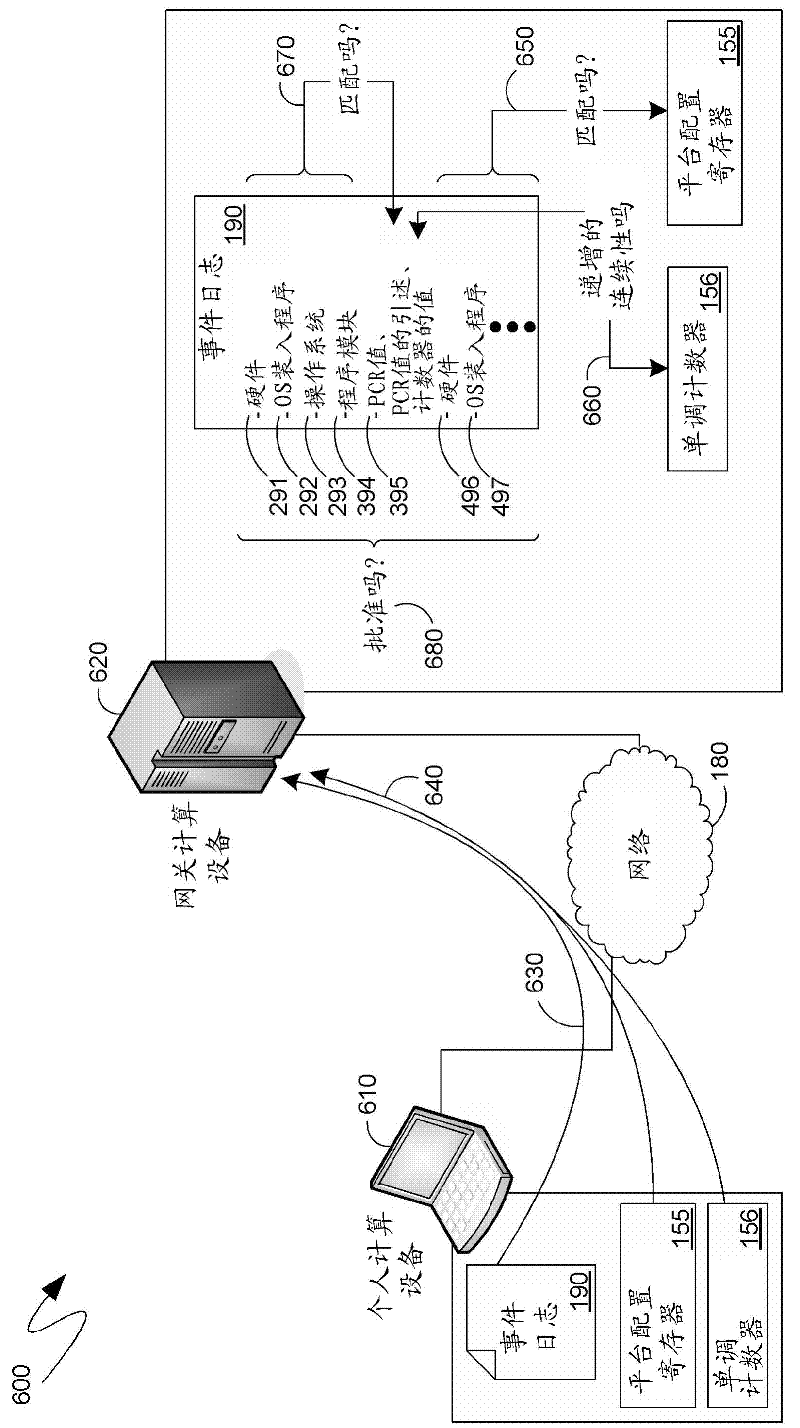
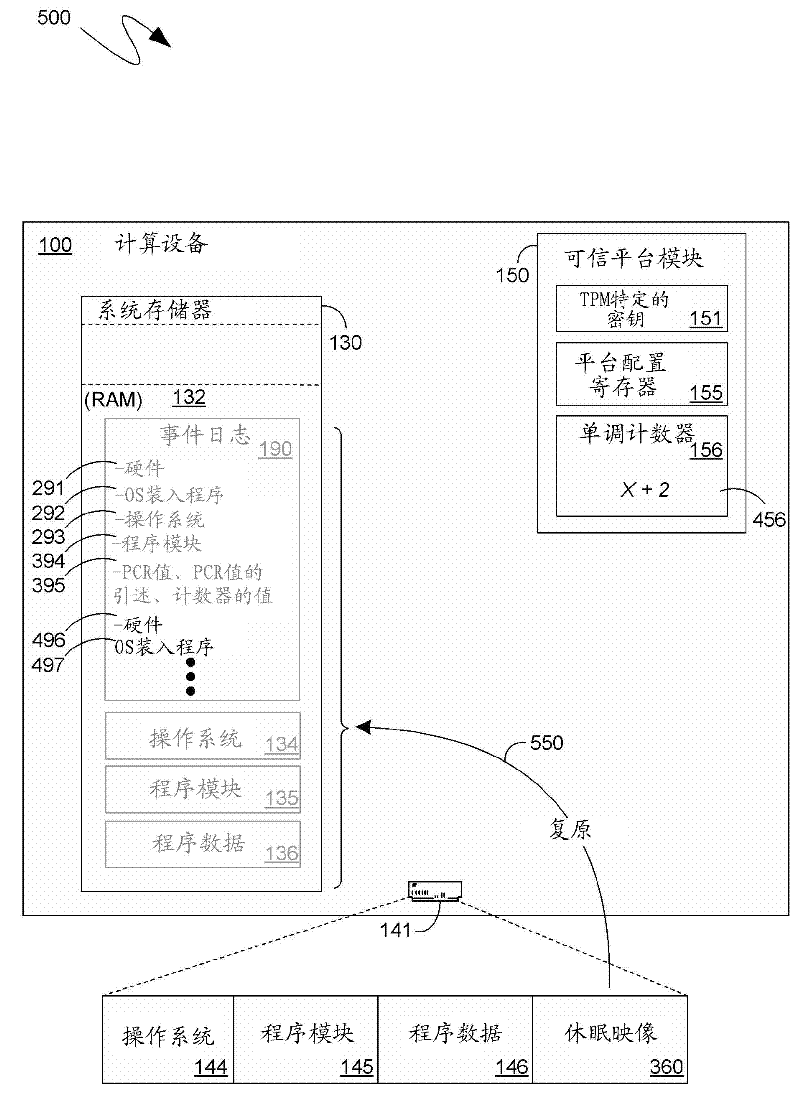
[0022] The following description involves setting the values of at least some of the Platform Configuration Registers (PCRs) of the Trusted Execution Environment, together with the Trusted Execution Environment's The value of the monotonic counter is recorded in the event log. Just then and thereafter, the previous event log into which this information was entered—saved as part of the hibernation image—can be concatenated with the current event log, thereby providing a secure record of at least A mechanism for computing the history of a device since the most recent power-on or reboot.
[0023] The mechanisms described here focus on, but are not limited to, actual computing devices entering a low power "sleep" mode or state. Indeed, the following teachings are equally applicable to virtual computing devices that emulate the operation of actual computing devices, and can be applied not only across hibernate and resume cycles, but also across where the state of the computing d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com