Patents
Literature
150 results about "Event (computing)" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, an event is an action or occurrence recognized by software, often originating asynchronously from the external environment, that may be handled by the software. Computer events can be generated or triggered by the system, by the user or in other ways. Typically, events are handled synchronously with the program flow, that is, the software may have one or more dedicated places where events are handled, frequently an event loop. A source of events includes the user, who may interact with the software by way of, for example, keystrokes on the keyboard. Another source is a hardware device such as a timer. Software can also trigger its own set of events into the event loop, e.g. to communicate the completion of a task. Software that changes its behavior in response to events is said to be event-driven, often with the goal of being interactive.
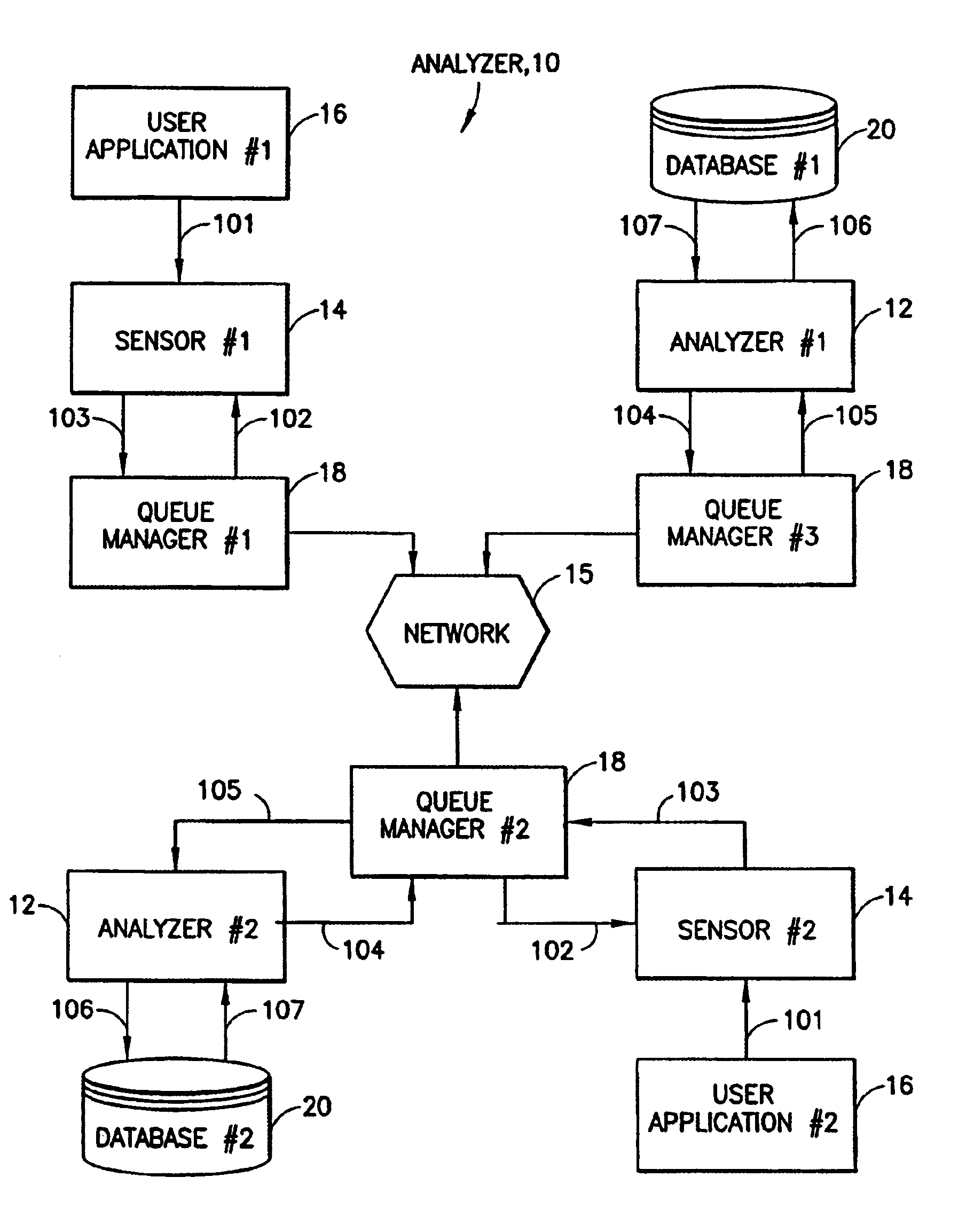
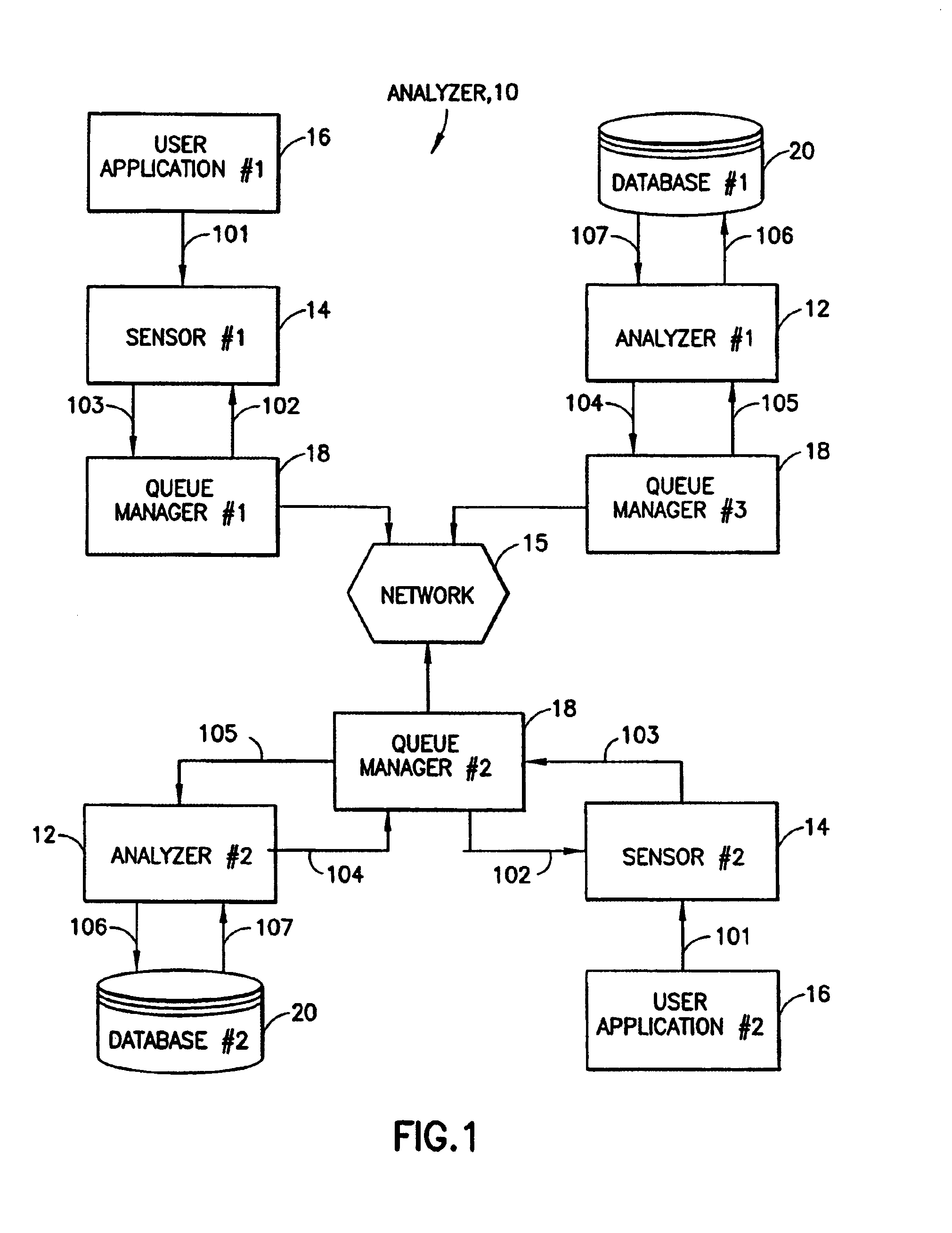
Method and apparatus for correlation of events in a distributed multi-system computing environment
InactiveUS7003781B1Overcome problemsHardware monitoringProgram controlData processing systemApplication software
A method and system is disclosed for monitoring an operation of a distributed data processing system. The system can include a plurality of applications running on a plurality of host processors and communicating with one another, such as through a message passing technique. The method includes steps executed in individual ones of the plurality of applications, of (a) examining individual ones of generated API calls to determine if a particular API call meets predetermined API call criteria; (b) if a particular API call meets the predetermined API call criteria, storing all or a portion of the content of the API call as a stored event; (c) processing a plurality of the stored events to identify logically correlated events, such as those associated with a business transaction; and (d) displaying all or a portion of the stored API call content data for the logically correlated events.
Owner:MICRO FOCUS LLC
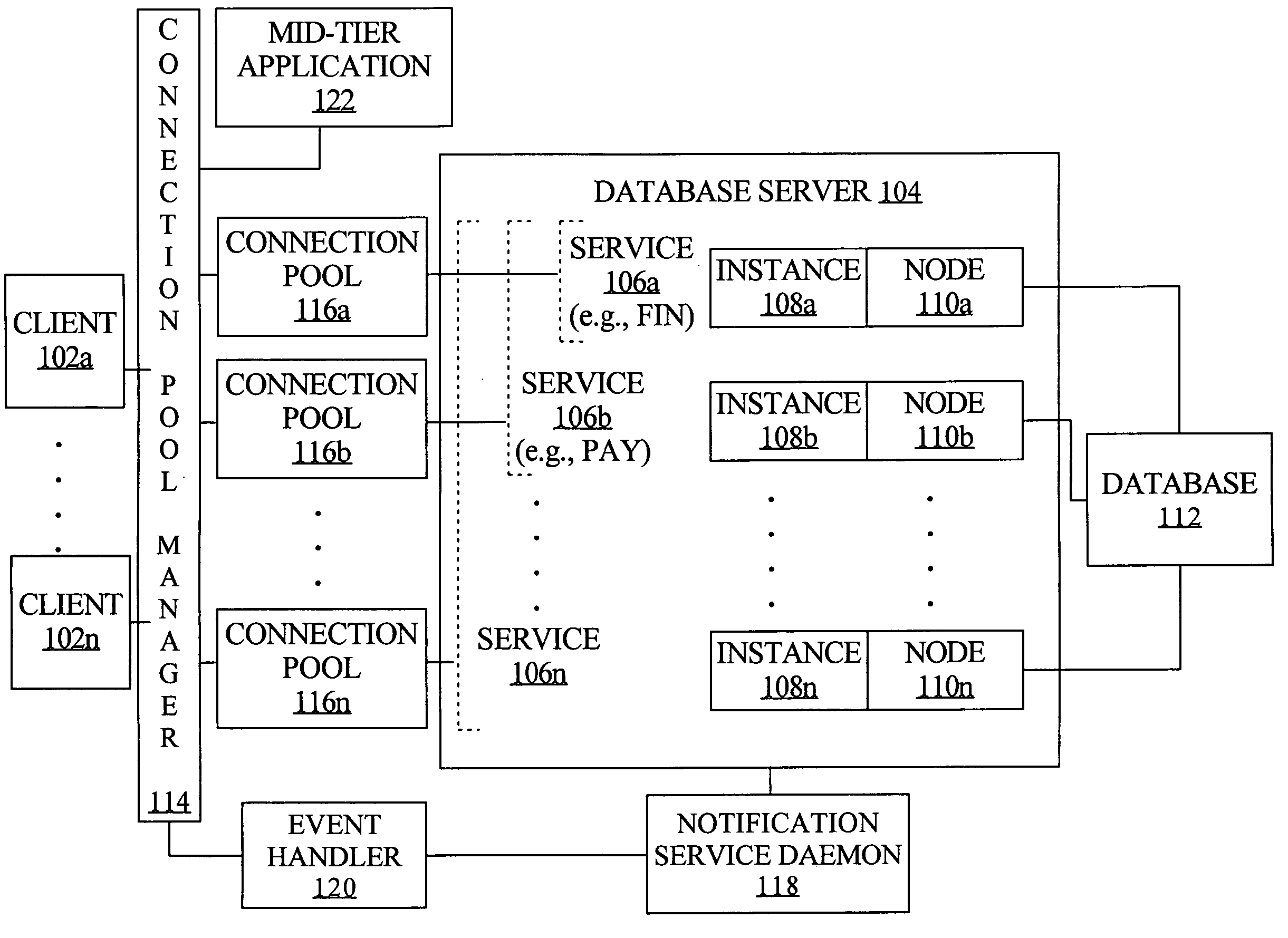
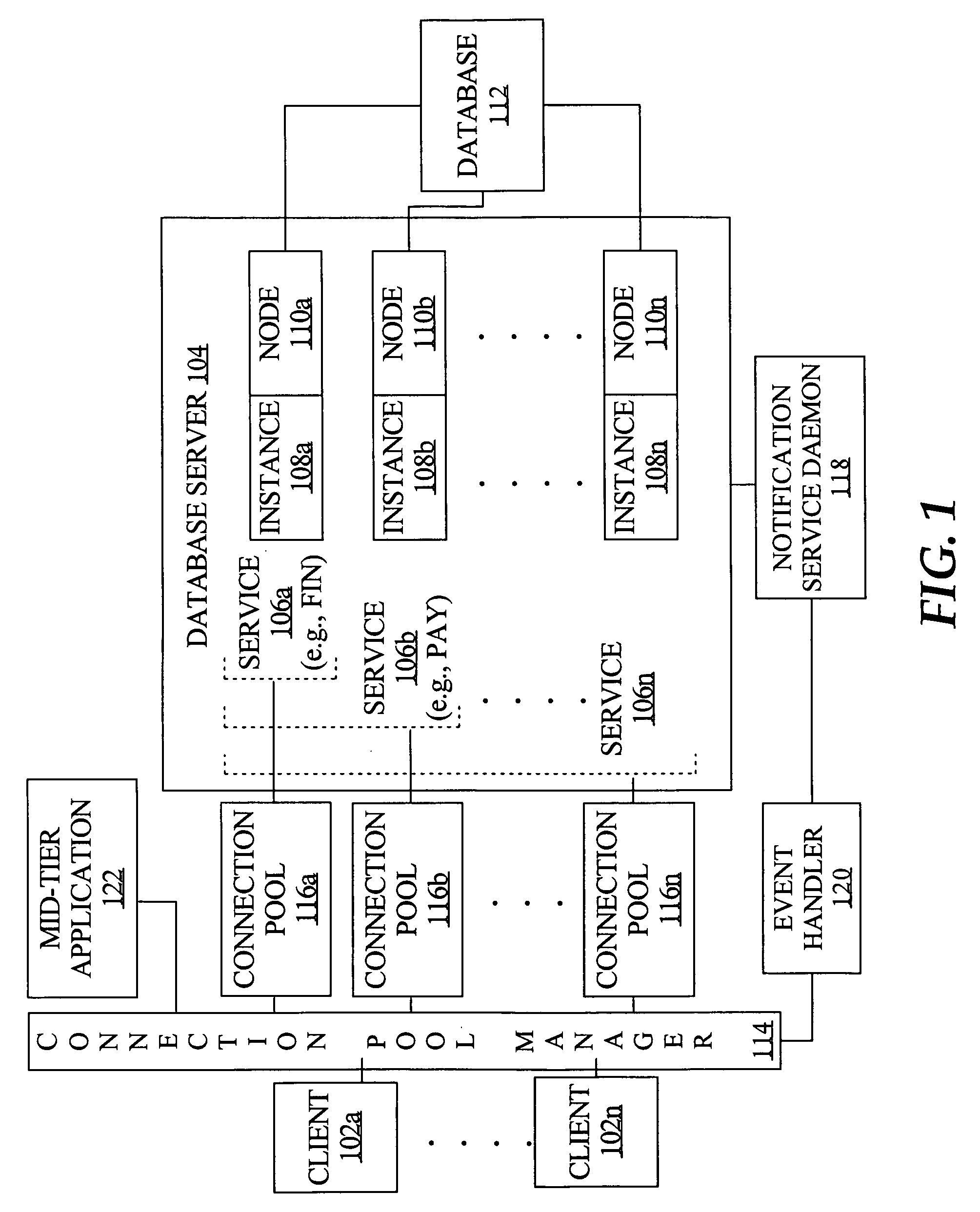
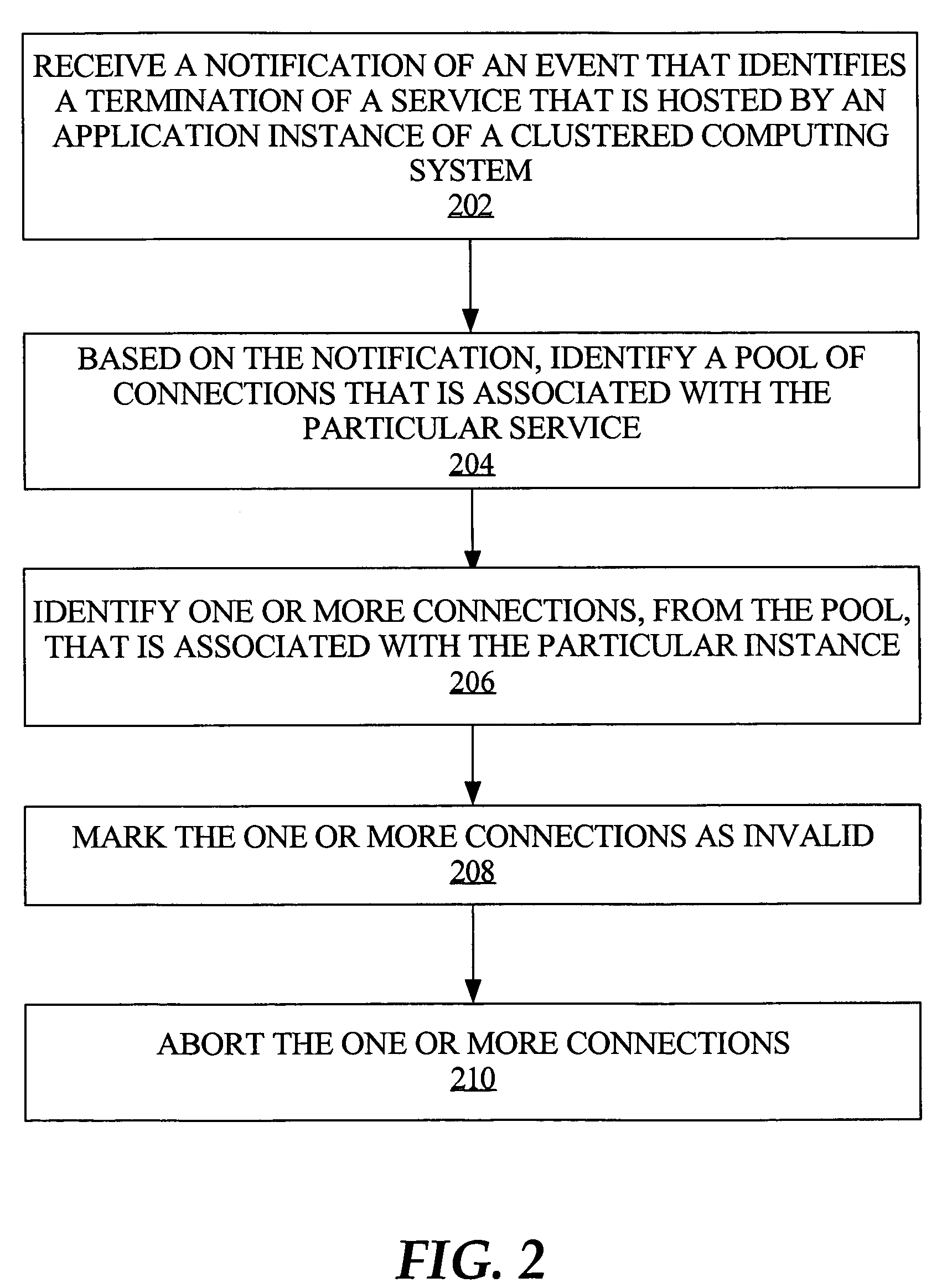
Fast reorganization of connections in response to an event in a clustered computing system
ActiveUS20050038801A1Easy to handleRapid positioningError detection/correctionDigital data processing detailsParallel computingConnection pool
Techniques for fast recovery and / or balancing of connections to a clustered computing system provide management of such connections by determining a number of connections to load balance across nodes and by triggering creation of such connections. In one aspect, a notification of an event regarding the clustered computing system is received by a connection pool manager, a pool of connections to the system is identified based on the notification, and one or more connections from the pool are processed in response to the event. According to an embodiment, the notification comprises the identities of the service, database, server instance and machine that correspond to the event.
Owner:ORACLE INT CORP
System, method, and apparatus for improving application-launch latencies
InactiveUS20140143791A1Shorten launch timeMultiprogramming arrangementsLocation information based serviceOut of memorySoftware engineering
Owner:QUALCOMM INNOVATION CENT
Method, system and program product for correlating data between operating environments
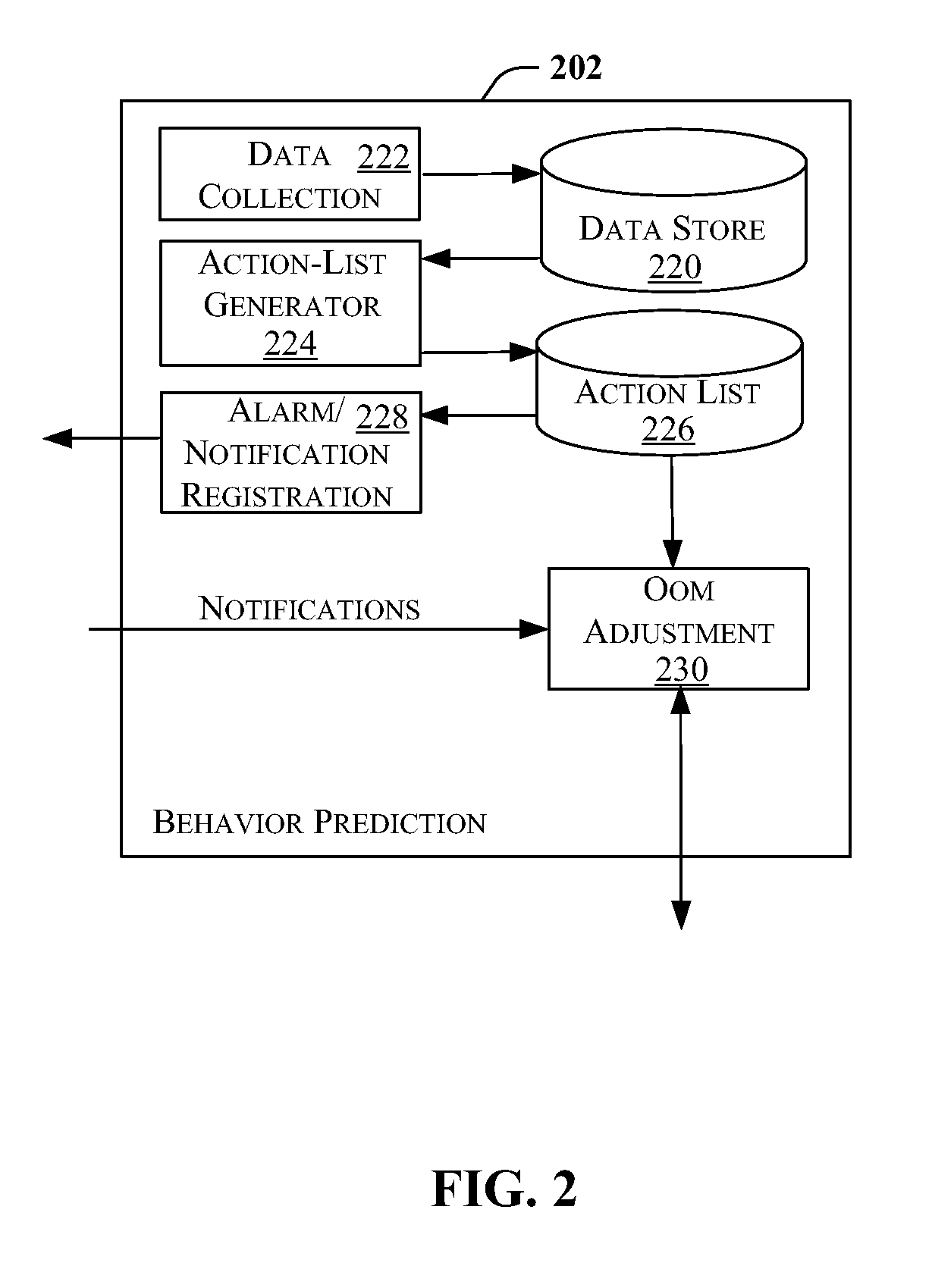
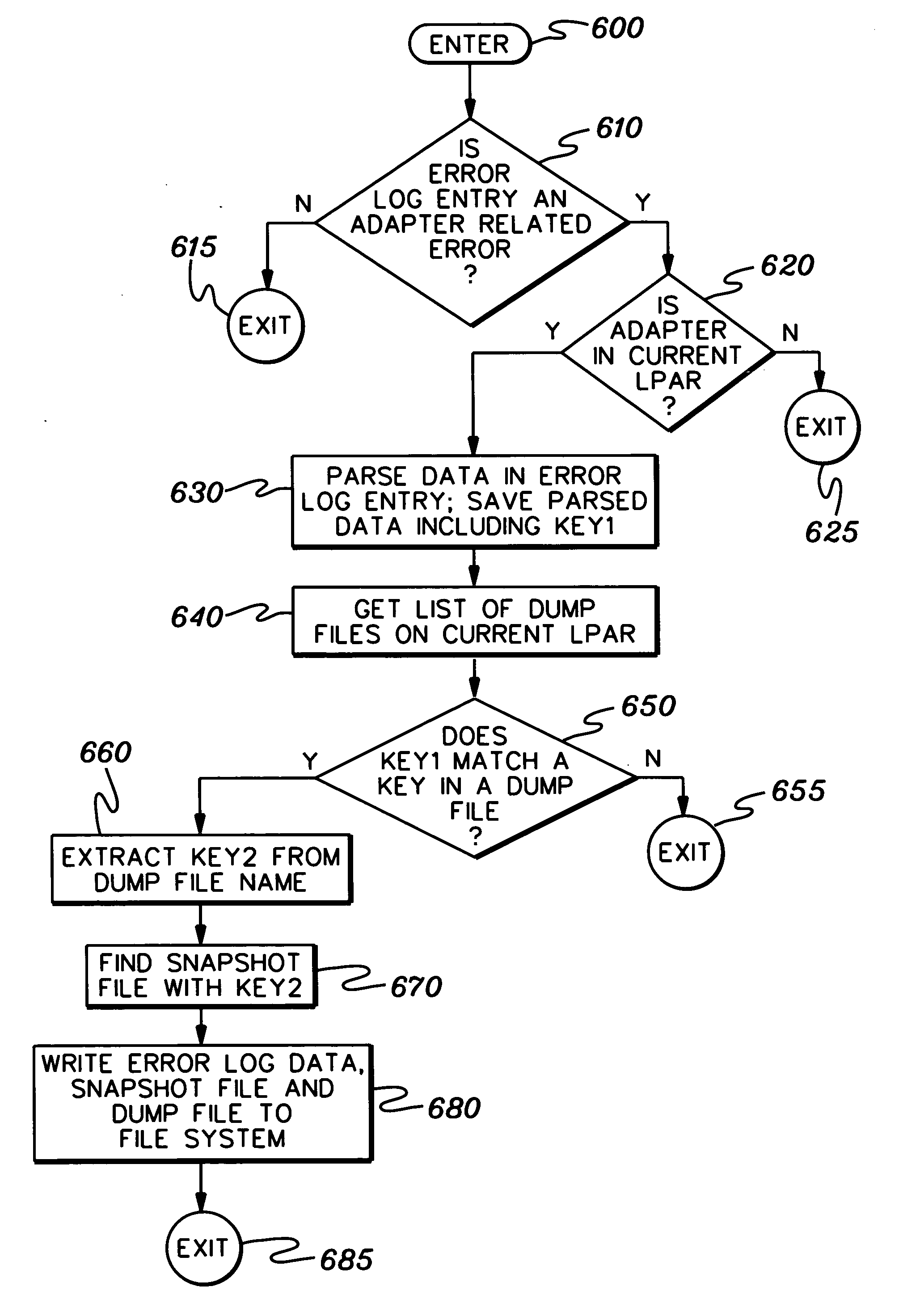
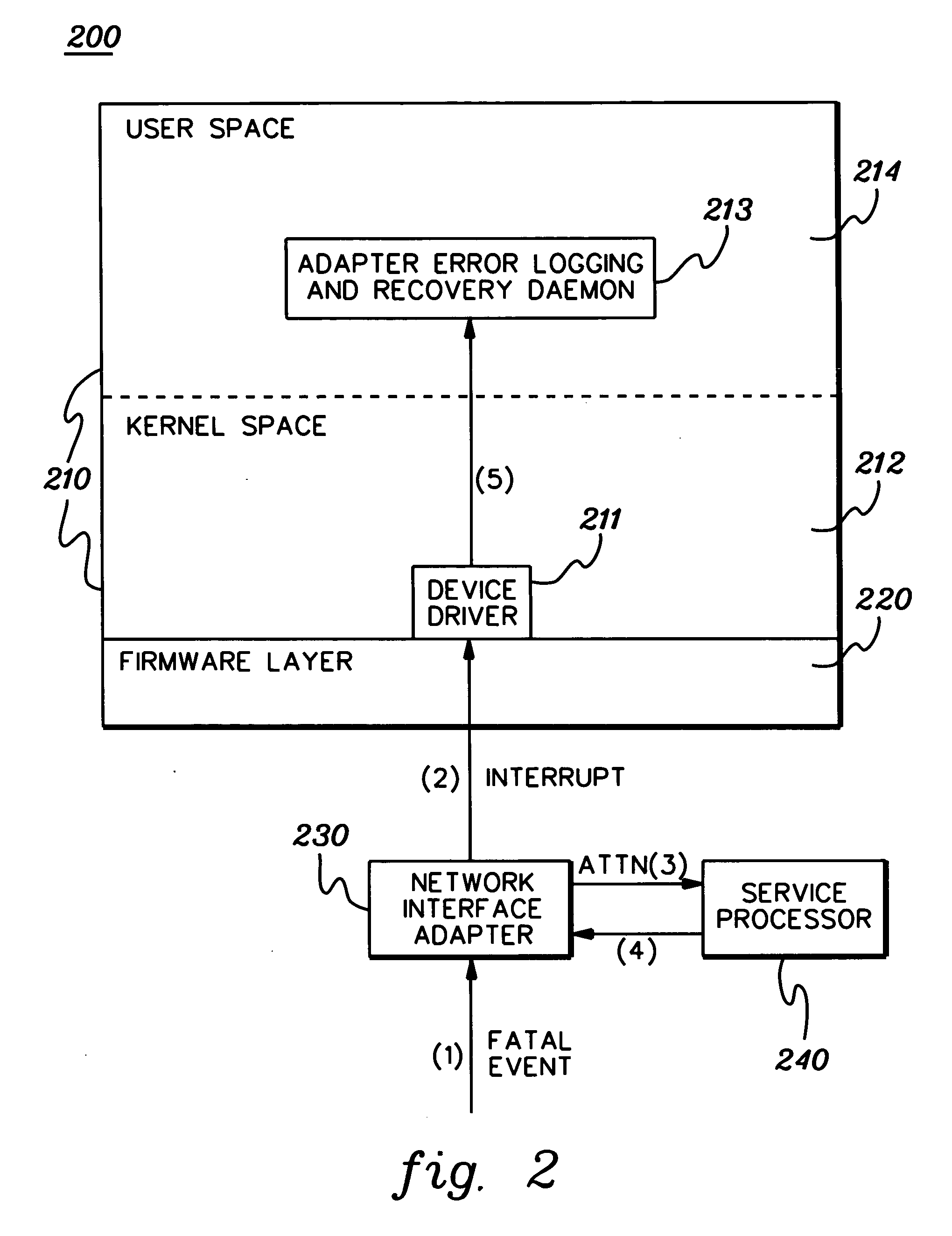
A data correlation technique is provided for a computing environment having multiple independent operating environments. The technique includes associating by a first operating environment a first key to a set of data to be obtained responsive to an identified event within the computing environment; obtaining by a second operating environment the set of data with the associated first key, and associating a second key therewith; and using the set of data with the associated first key and second key to match to the set of data at least one other set of data obtained by the first operating environment or the second operating environment responsive to the event. The at least one other set of data has only the first key or the second key associated therewith. In one implementation, the event is a fatal event at a network interface adapter.
Owner:IBM CORP
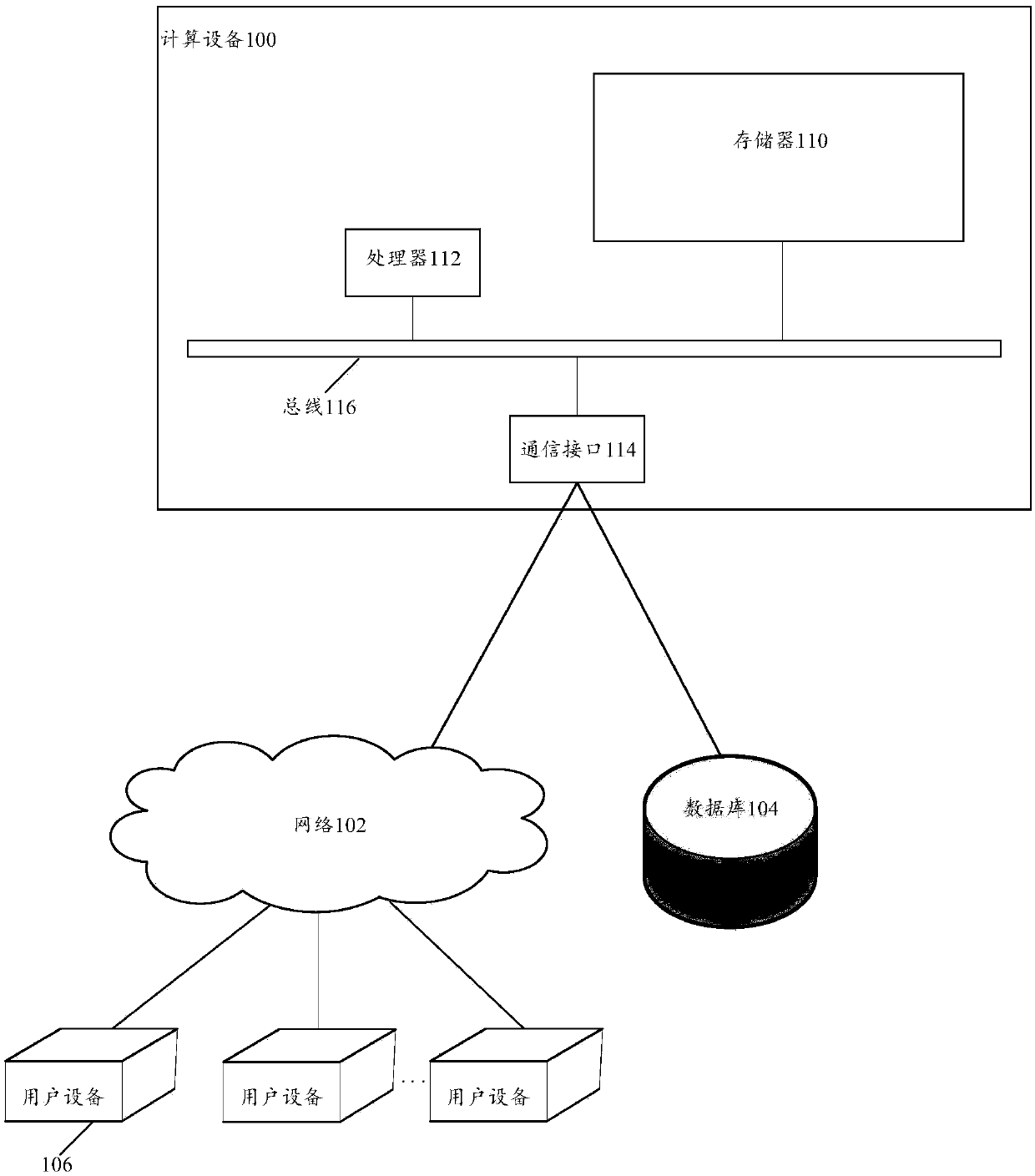
Event element extraction method and device, computing equipment and storage medium
ActiveCN109582949AImprove experienceSemantic analysisSpecial data processing applicationsFeature vectorEvent type
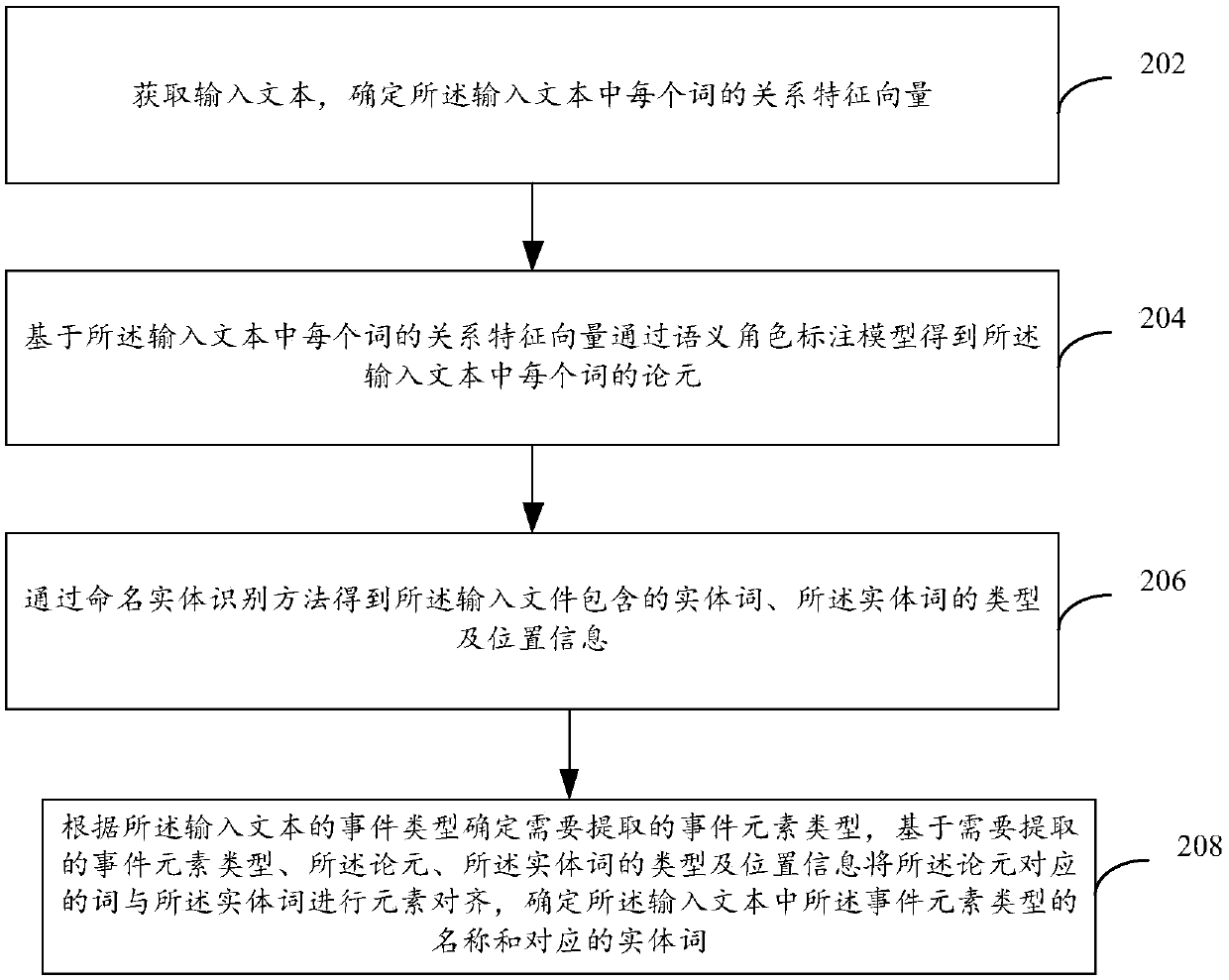
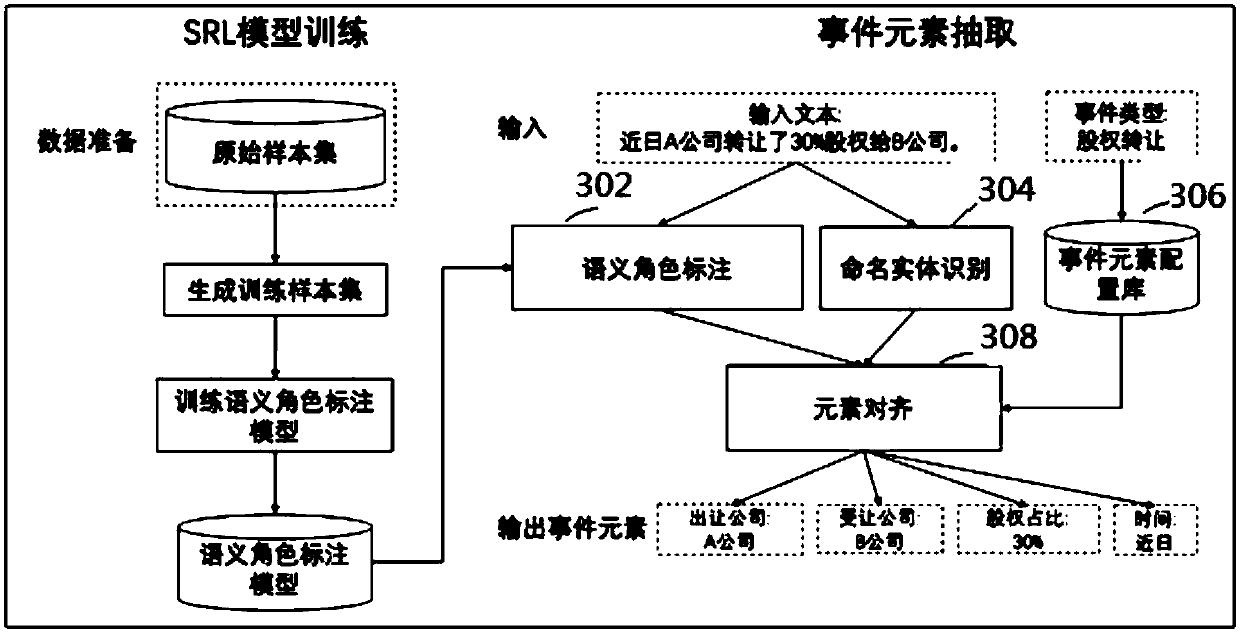
The invention provides an event element extraction method and device, computing equipment and a storage medium, and the event element extraction method comprises the steps: obtaining an input text, and determining a relation feature vector of each word in the input text; Obtaining argument of each word in the input text through a semantic role labeling model based on the relation feature vector ofeach word in the input text; Obtaining entity words contained in the input file and types and position information of the entity words through a named entity recognition method; Determining an eventelement type needing to be extracted according to the event type of the input text, and performing element alignment on the words corresponding to the arguments and the entity words based on the typesof the event elements needing to be extracted, the arguments and the types and position information of the entity words, and determining names of the types of the event elements and the correspondingentity words in the input text.
Owner:ADVANCED NEW TECH CO LTD
Apparatus, systems, and methods for distributed application orchestration and deployment
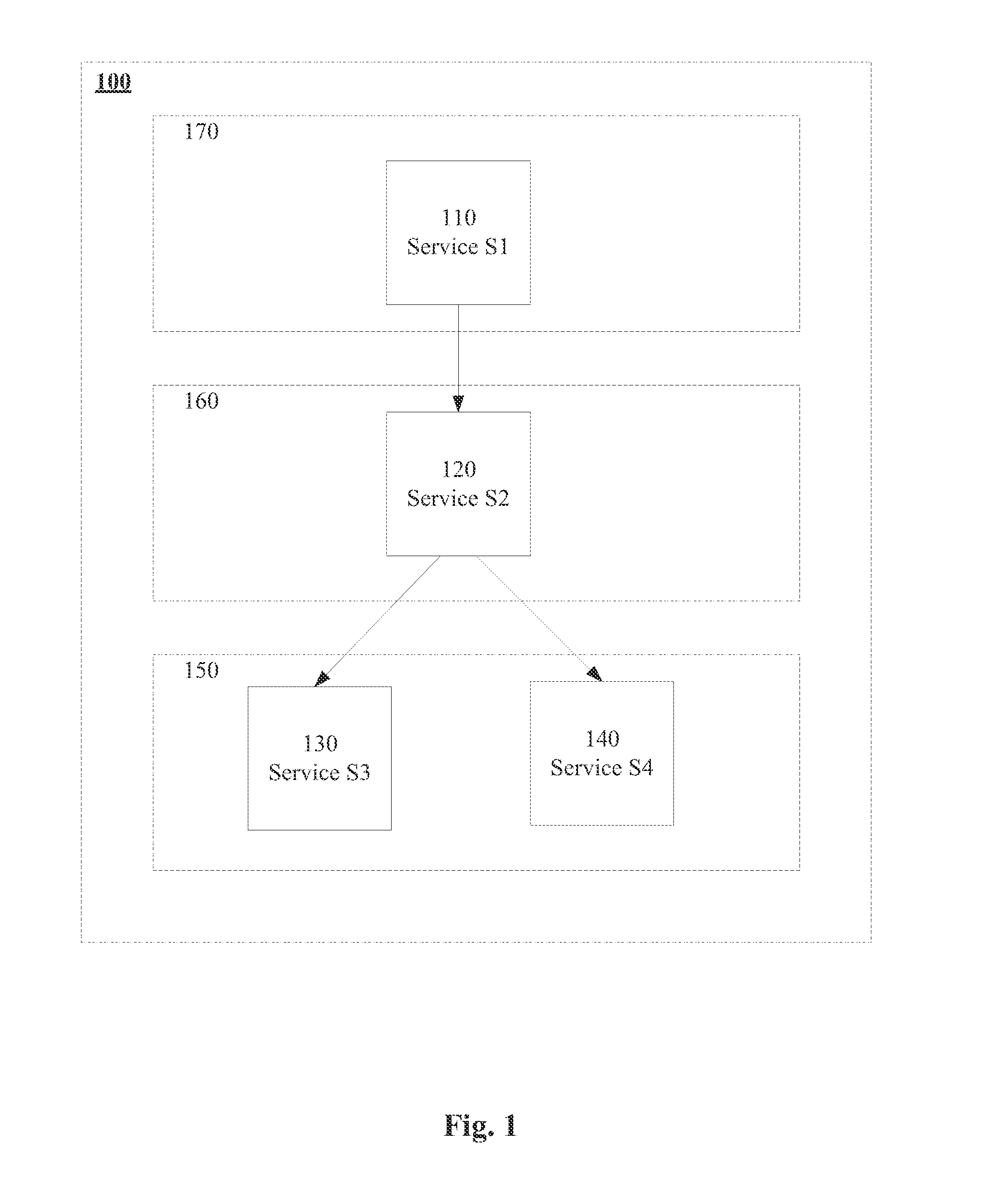
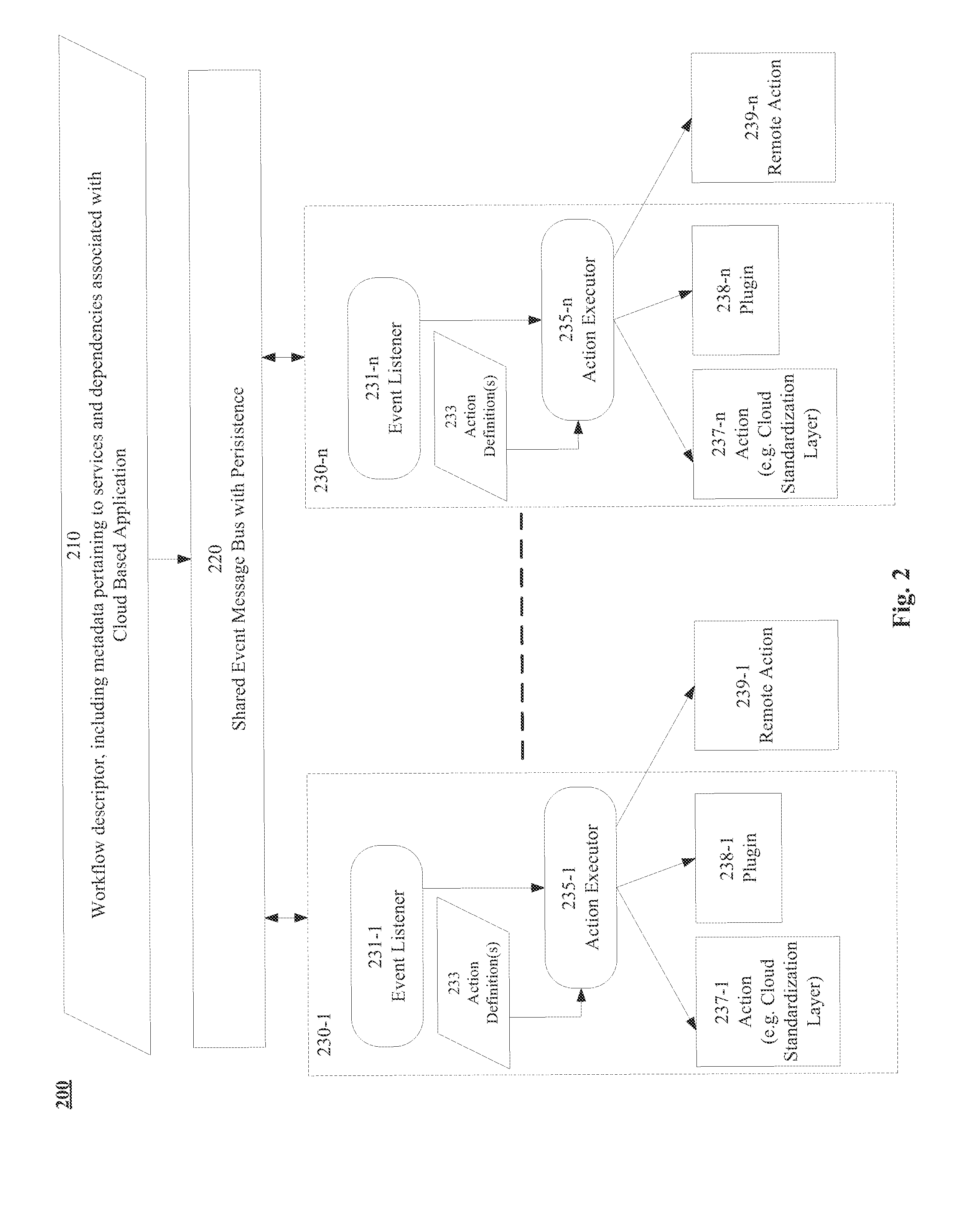
Embodiments disclosed facilitate distributed orchestration and deployment of a cloud based distributed computing application. In some embodiments, the distributed orchestration may be based on a cloud agnostic representation of the application. In some embodiments, an ordered set of events may be obtained based on a starting sequence for the plurality of components, where each event in the ordered set is associated with a corresponding set of prerequisites for initiating execution of the event. Event identifiers corresponding to the ordered set of events may be placed on an event message bus with persistence that is shared between a plurality of distributed nodes associated with a cloud. Upon receiving an indication of completion of prerequisites for one or more events, a plurality of nodes of a distributed orchestration engine may select the one or more events corresponding to the one or more selected event identifiers for execution on the cloud.
Owner:CISCO TECH INC
Task tracing in a distributed computing environment
InactiveUS20050091373A1Reduce chanceReduce riskError detection/correctionDigital computer detailsInformation repositoryDistributed Computing Environment
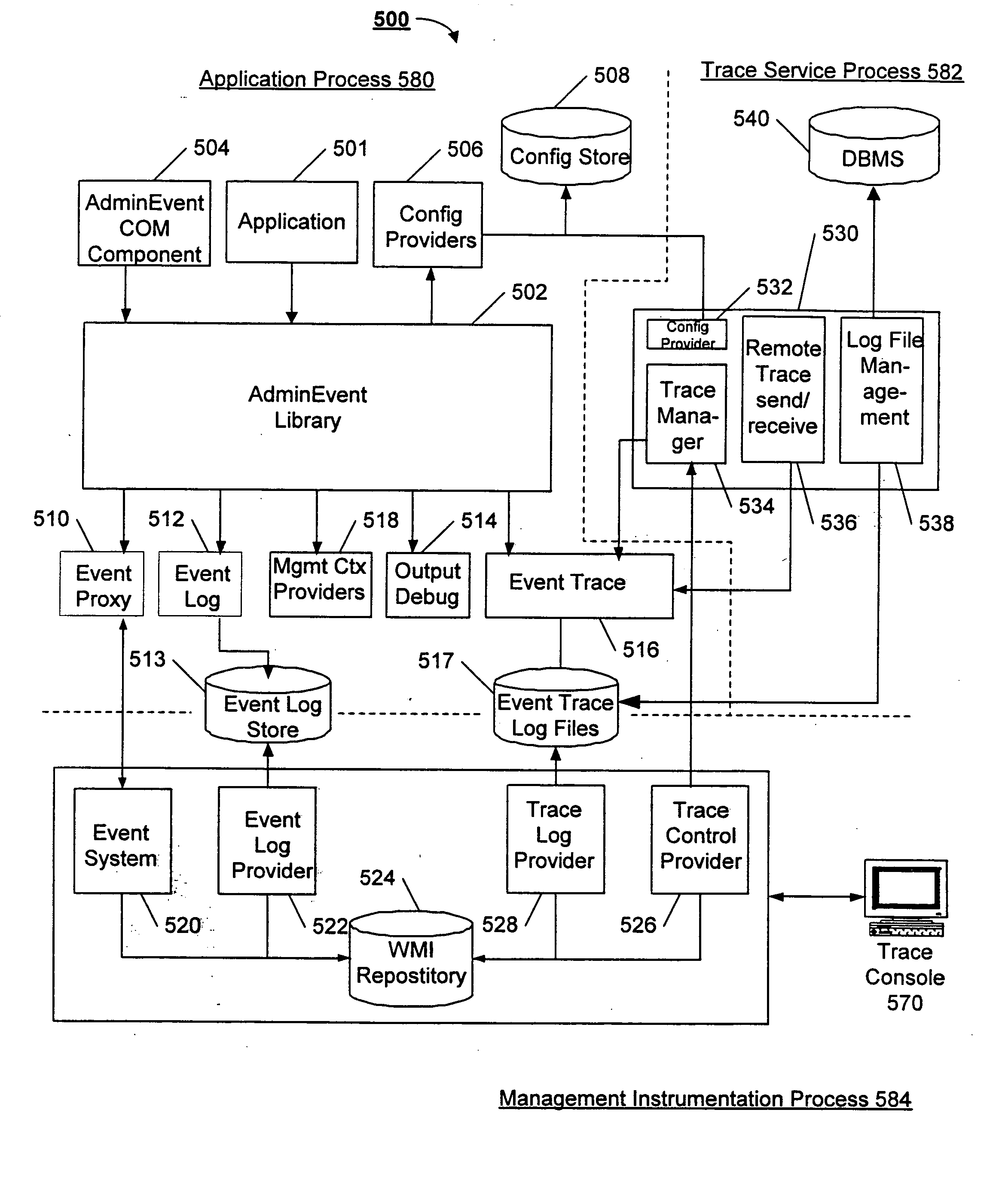
An architecture that supports the instrumentation of software to generate structured information about its operation. A library of methods and data structure definitions is provided to a developer of a piece of software. The developer includes calls to the methods in order to signal the fact that a given event has occurred. The developer may also cause the program to provide information descriptive of the event by populating data structures defined in the library. The library methods may also contribute to the population of these data structures. In a distributed computing environment in which tasks are performed through a series of calls to remote computers, “per-task” tracing may be performed by sending trace instructions to the remote computers along with the remote calls.
Owner:MICROSOFT TECH LICENSING LLC
Implementing event processors
ActiveUS7870167B2Improve performanceImprove scalabilityDigital data information retrievalDigital data processing detailsComputer architectureApplication software
Owner:ORACLE INT CORP
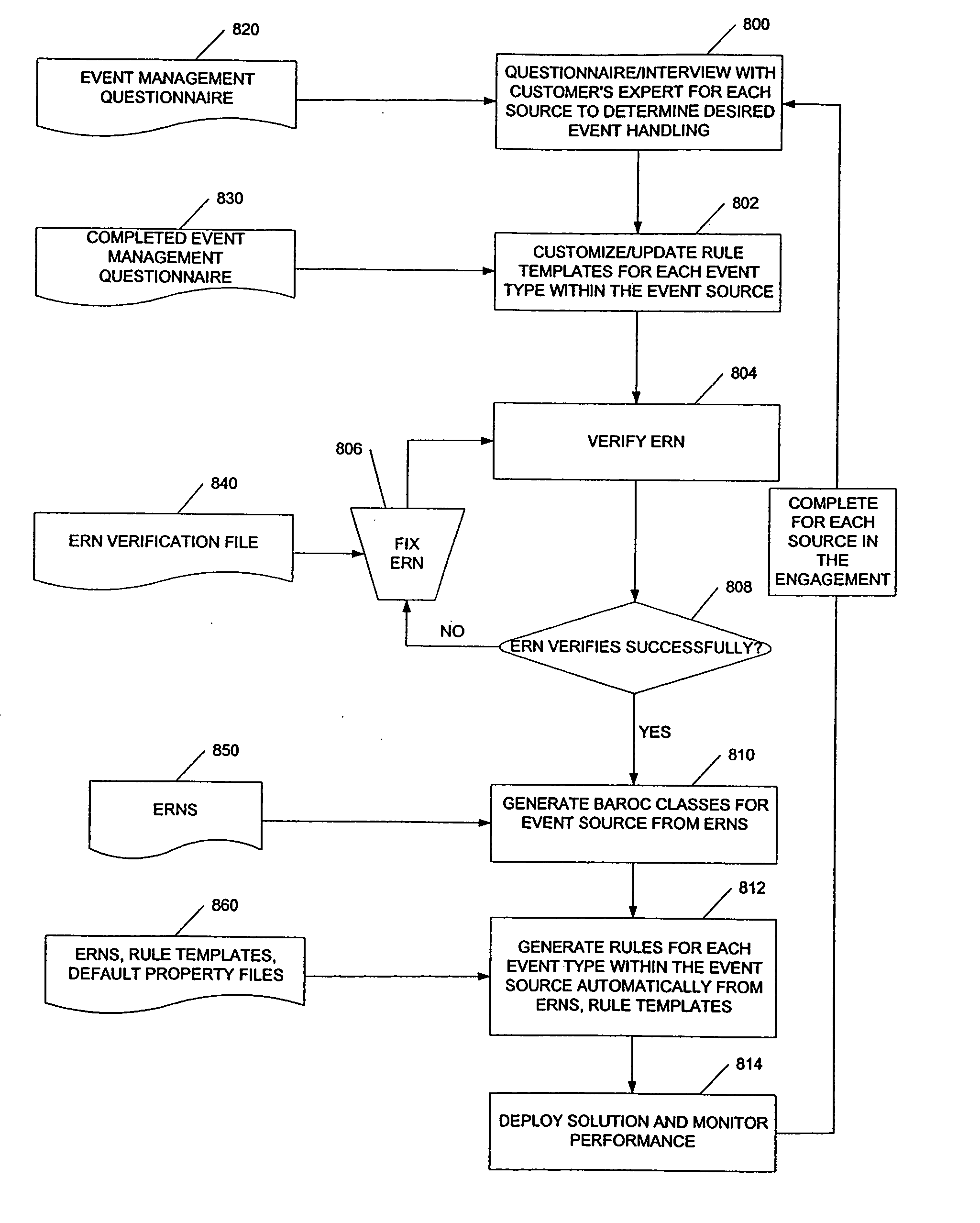
Hierarchical connected graph model for implementation of event management design
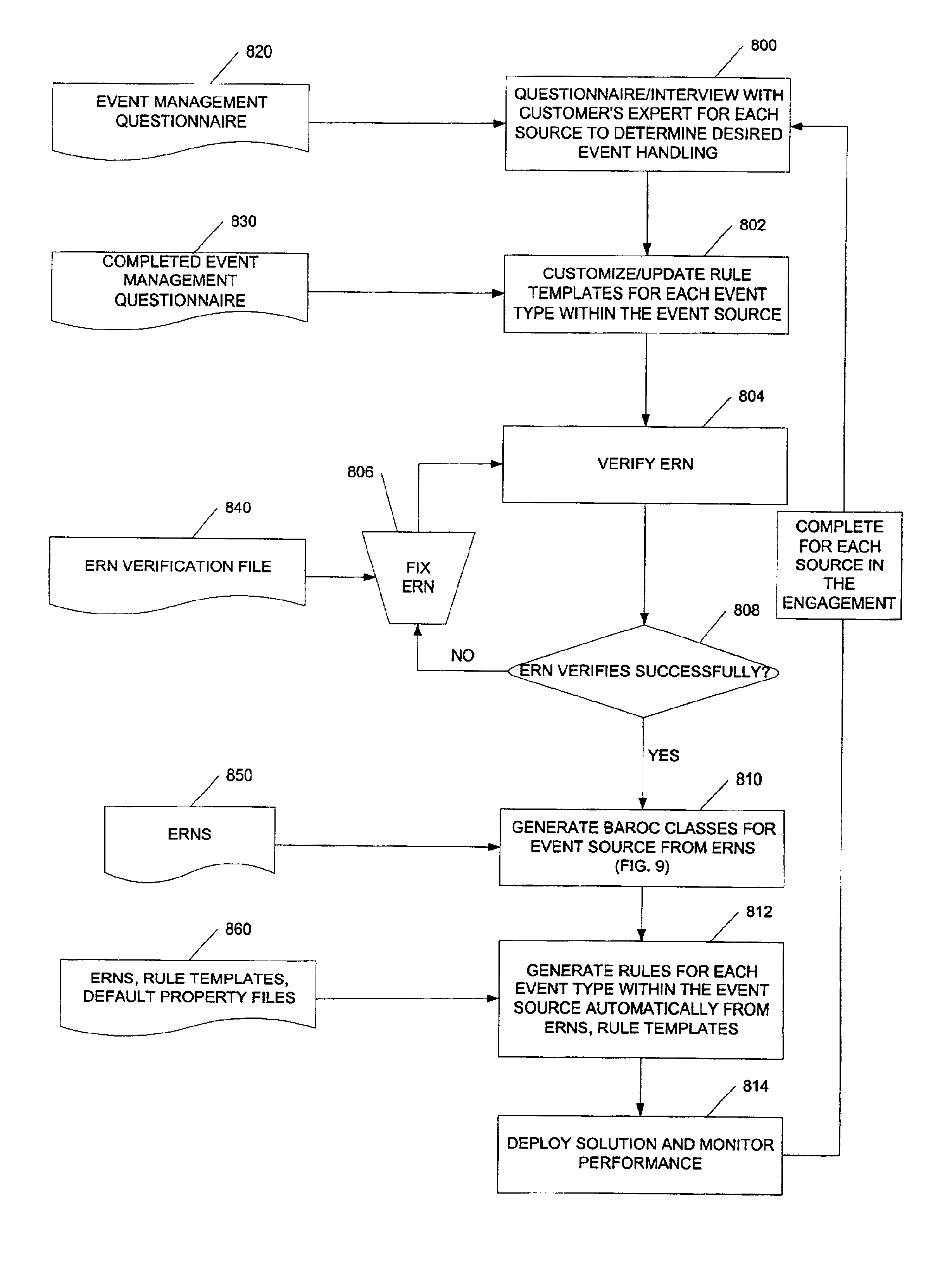
An automated method and system for the implementation of a hierarchical event relationship network for correlation analysis in a distributed computing environment in which events are defined based on a connected graph model. Event handling information for each event type to be monitored is used to customize a plurality of rule templates for each type within an event source, where the event source is a hardware component, an application software component or an operating system platform. A plurality of event relationship network rules are verified to ensure they do not violate an event protocol. A hierarchical class definition and naming structure is generated from the plurality of event relationship network rules for each event source. Event management rules are then generated automatically for each event type from the event relationship network rules and the rule templates. The event management rules are loaded into a rule-based event manager. The performance of the rule-based event manager is then monitored.
Owner:KYNDRYL INC
Monitoring method and device of JAVA application system in running
InactiveCN102122263AReduce hardware overheadDoes not affect normal operationHardware monitoringOriginal dataConfigfs
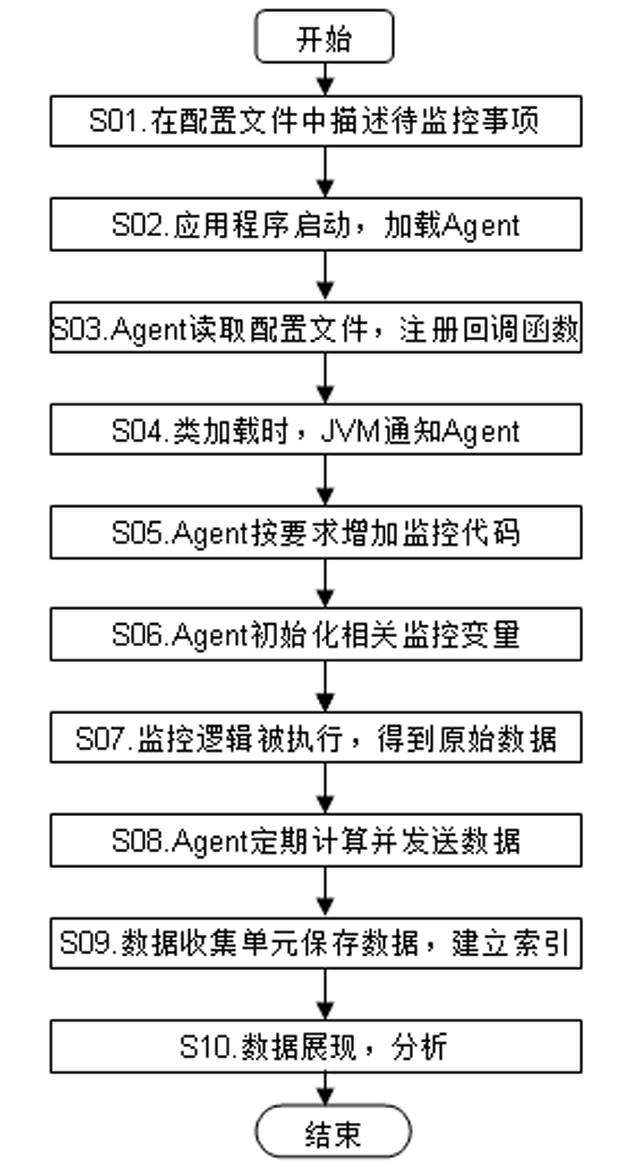
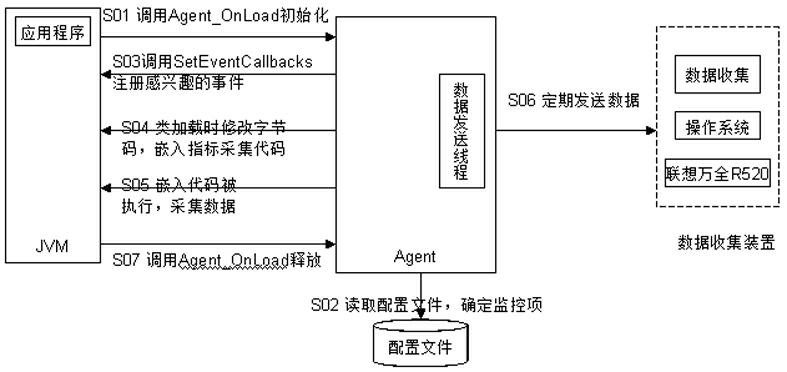
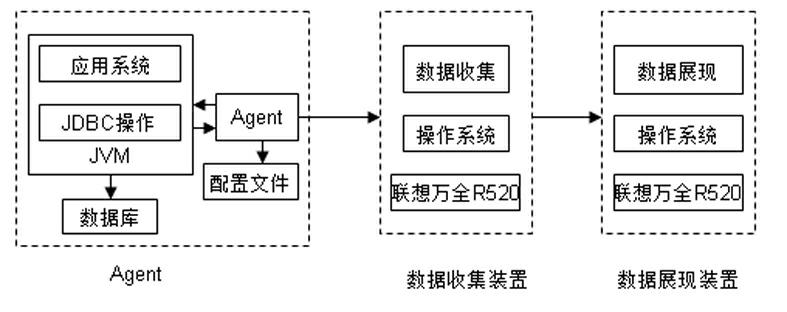
The invention discloses a monitoring method and device of a JAVA application system in running. The JAVA application system monitoring method mainly comprises the steps of: describing a monitored class or method and a monitor control index through a configuration file; (2) modifying starting parameters of an application program, and loading Agent when a JVM (Java Virtual Machine) is started; (3) reading the configuration file by the Agent, and registering an event to be noticed according to a monitoring requirement; (4) obtaining a notice by the Agent when the application program runs and a specified class is loaded; (5) modifying a bytecode of a corresponding class by the Agent, and adding a logic required in monitoring; (6) initializing relevant index variable by the Agent; (7) automatically executing the monitoring logic when the monitored method is called, and obtaining the original data of the relevant index; and (8) computing the value of the relevant index by the Agent according to the description of the configuration file. By applying the JAVA application system monitoring method disclosed by the invention, the ability of an IT (Information Technology) operation and maintenance staff for diagnosing, analyzing, positioning and solving faults of an IT system can be improved remarkably.
Owner:勤智数码科技股份有限公司
Process automation action repository and assembler
ActiveUS10606687B2Programme-controlled manipulatorNon-redundant fault processingTime conditionSoftware engineering
Owner:BANK OF AMERICA CORP
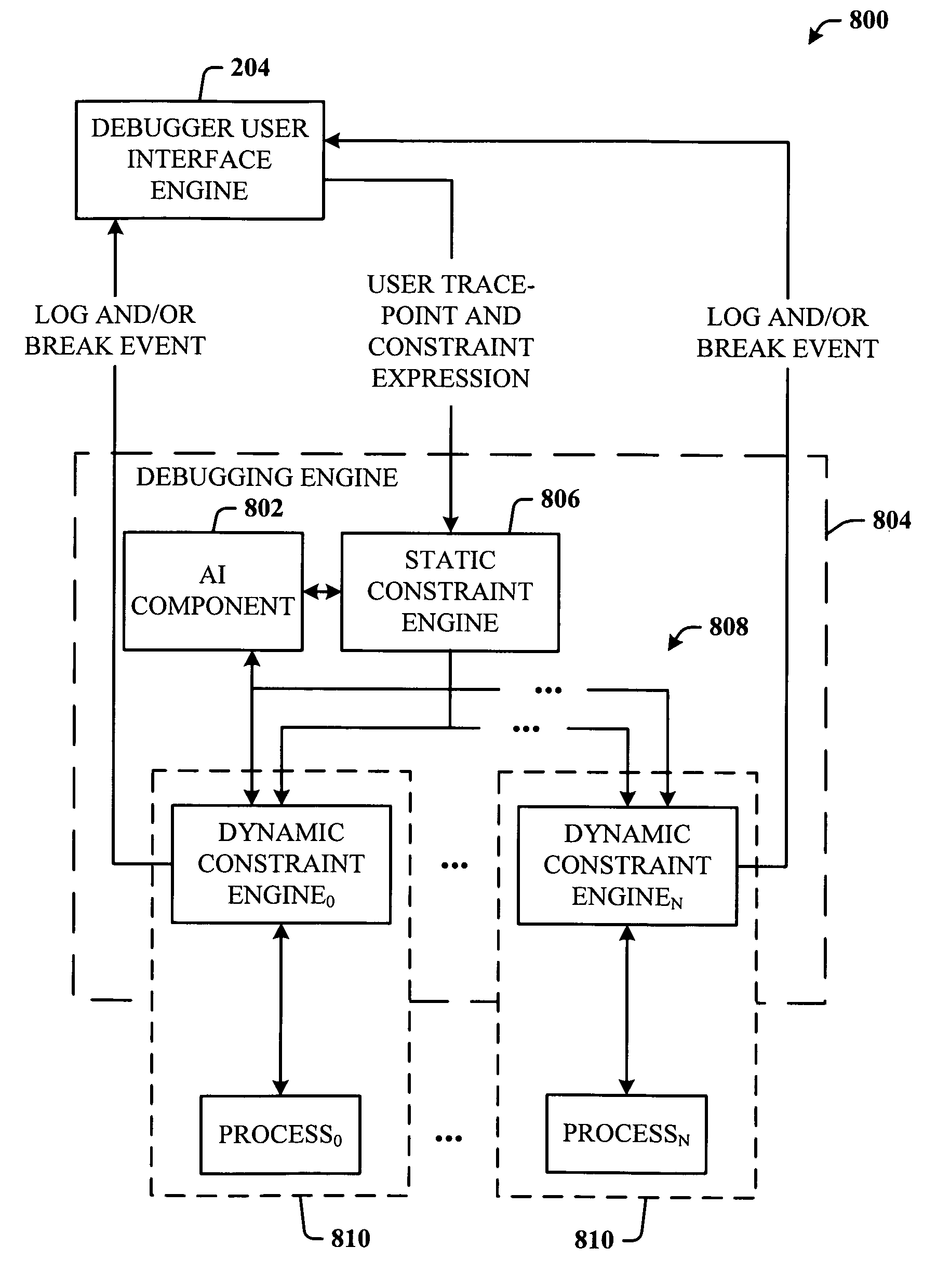
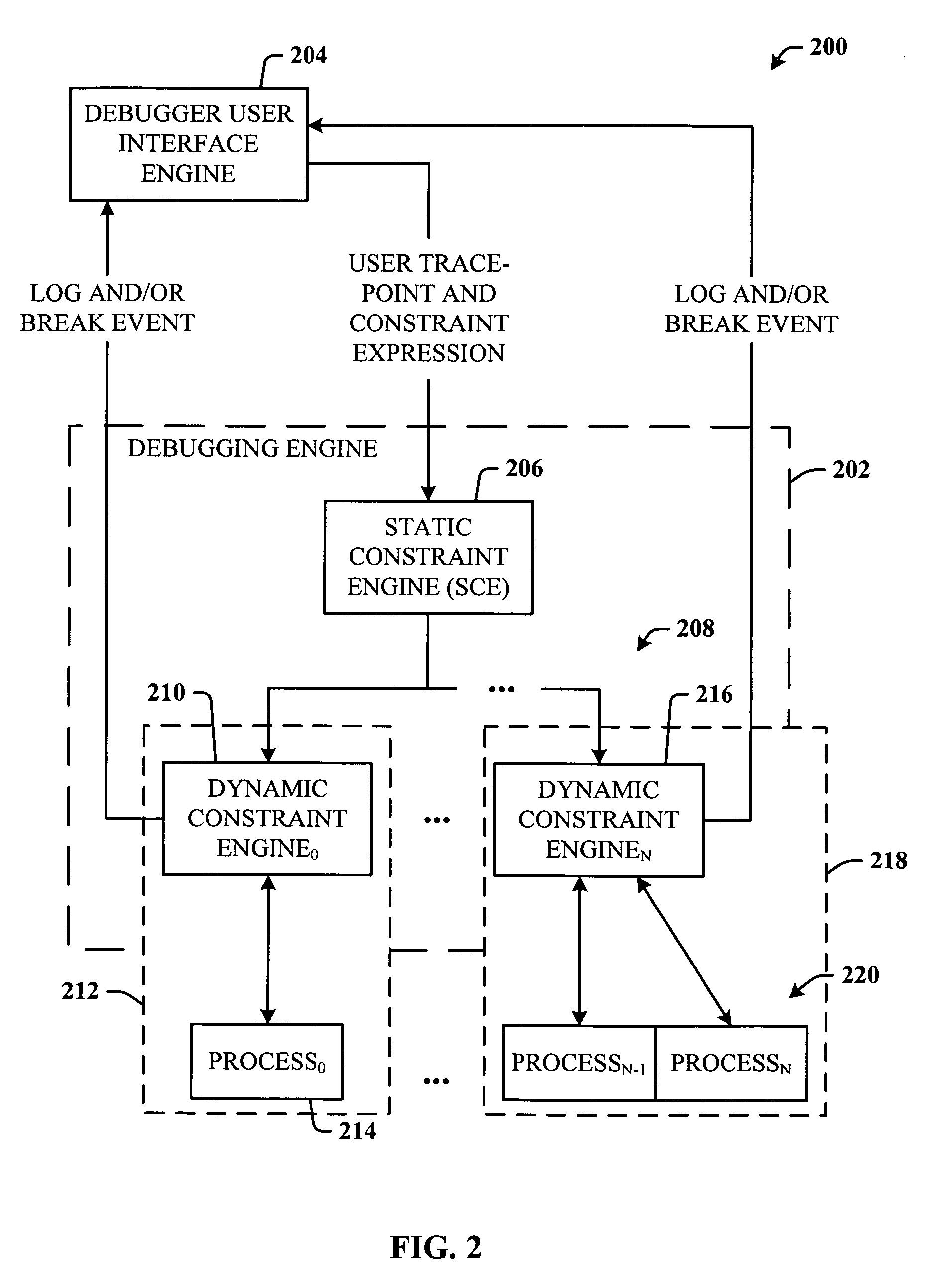
Breakpoint logging and constraint mechanisms for parallel computing systems
InactiveUS7634761B2Error detection/correctionSpecific program execution arrangementsConcurrent computationParallel computing
Owner:MICROSOFT TECH LICENSING LLC
Cluster monitoring system with content-based event routing
InactiveUS20060179059A1Reduce and eliminate numberError detection/correctionProgram controlMonitoring systemClient-side
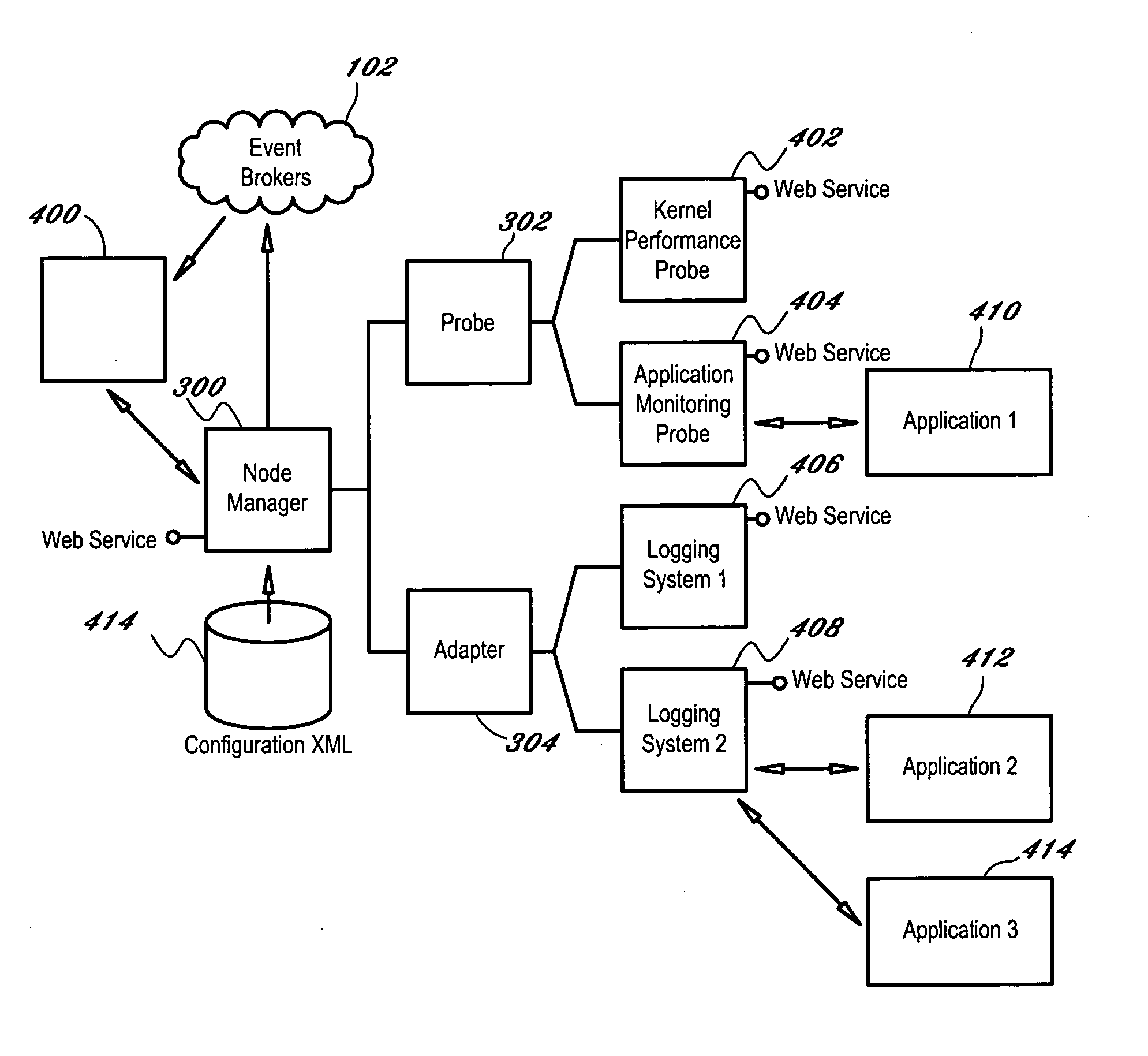
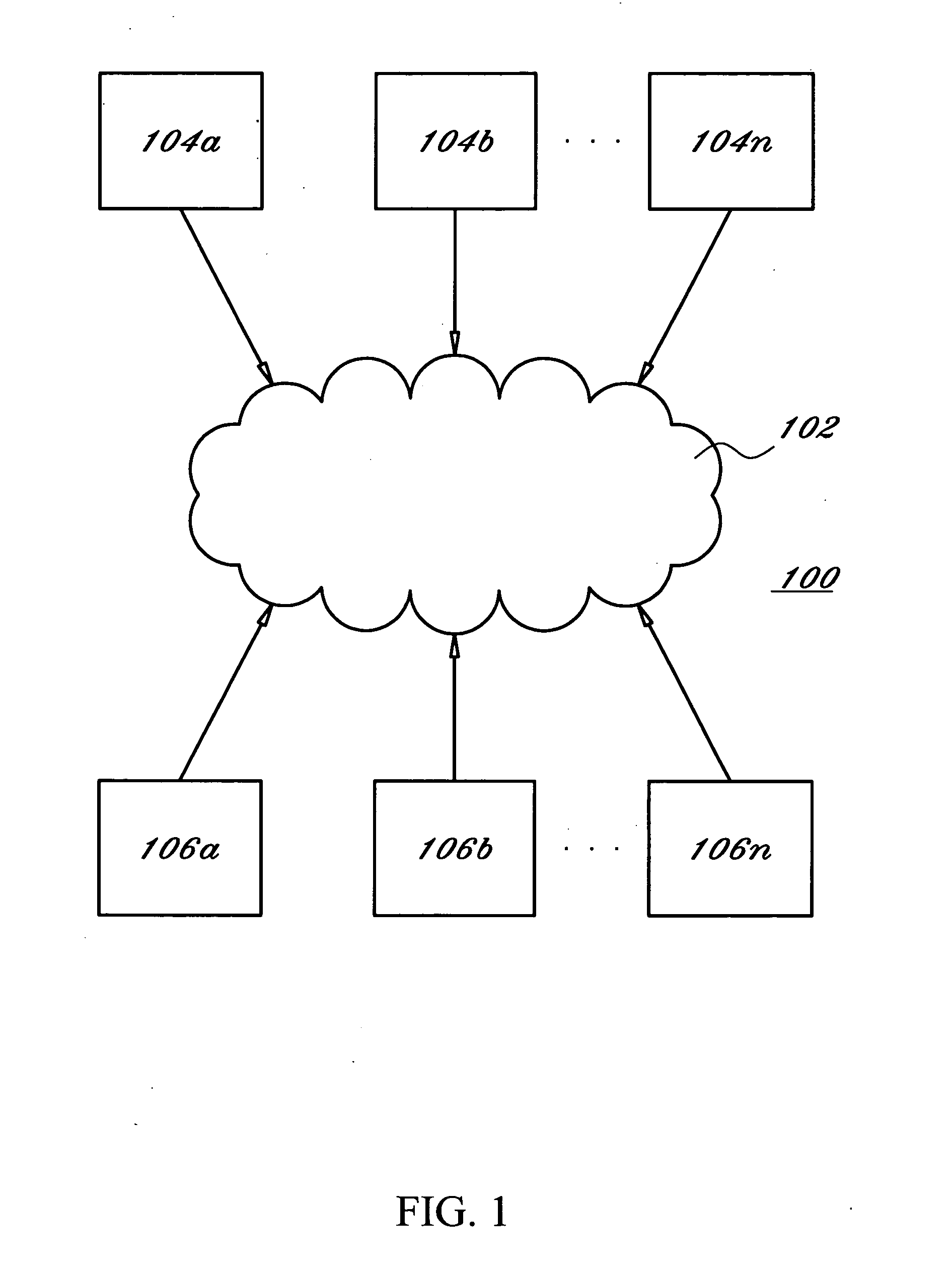
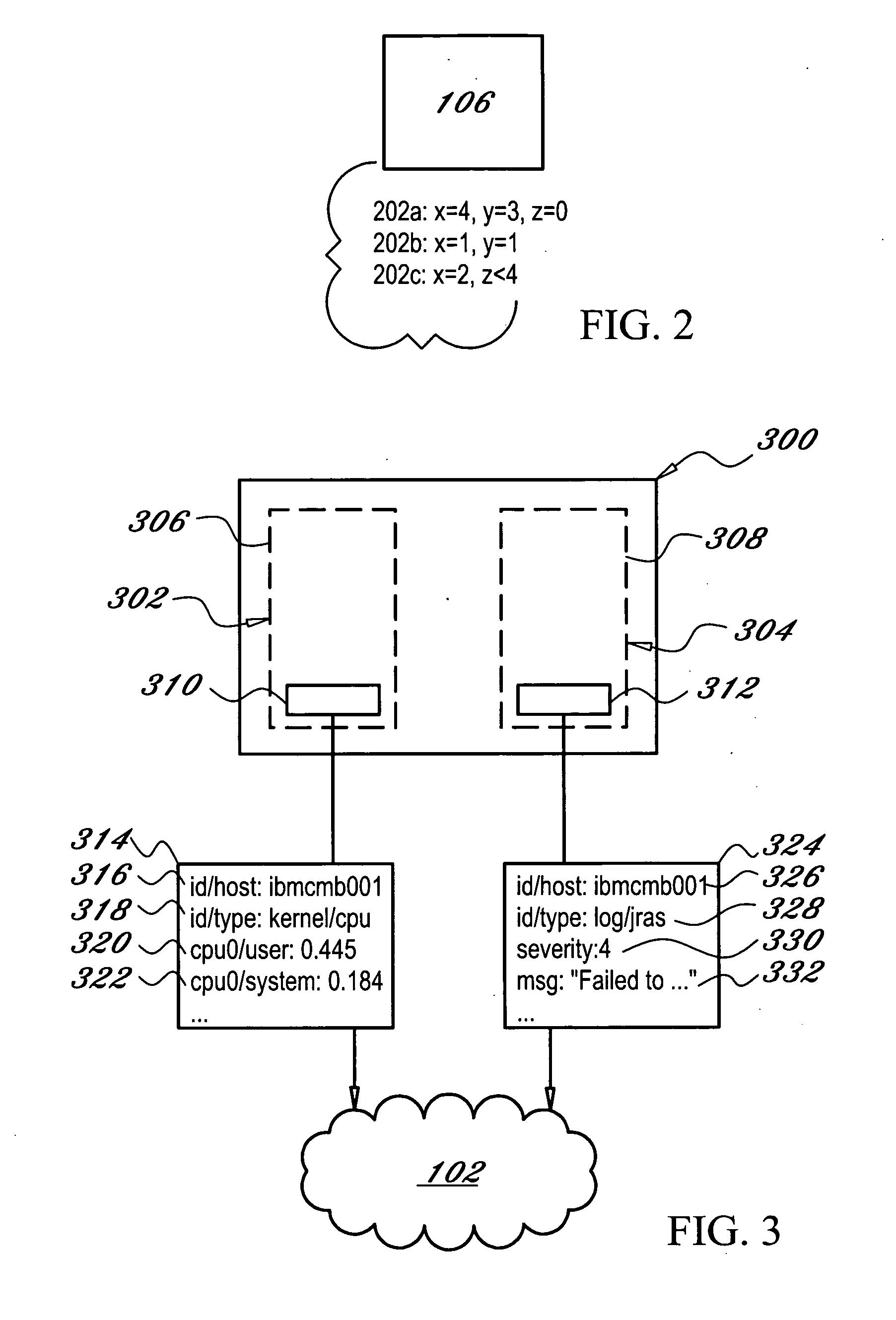
A node manager (300) resides on a node (104) in a cluster computing system (100) and transfers information and events being communicated across the node (104) to a broker (102) coupled to the node manager (300). The broker (102) transmits information to client devices (106) who subscribe to particular events. The node manager (300) includes an adapter (304) that interprets events occurring on the system and publishes messages to the broker, and a system probe (302) that publishes information to the broker (102) in accordance with a configurable schedule. An autonomic agent (400) measures the rate of information loss between the node (104) and client (106) and regulates the rate of information by adjusting one or more information flow control points within the system once an overload state is detected.
Owner:IBM CORP
Monitoring system and method for monitoring the operation of distributed computing components
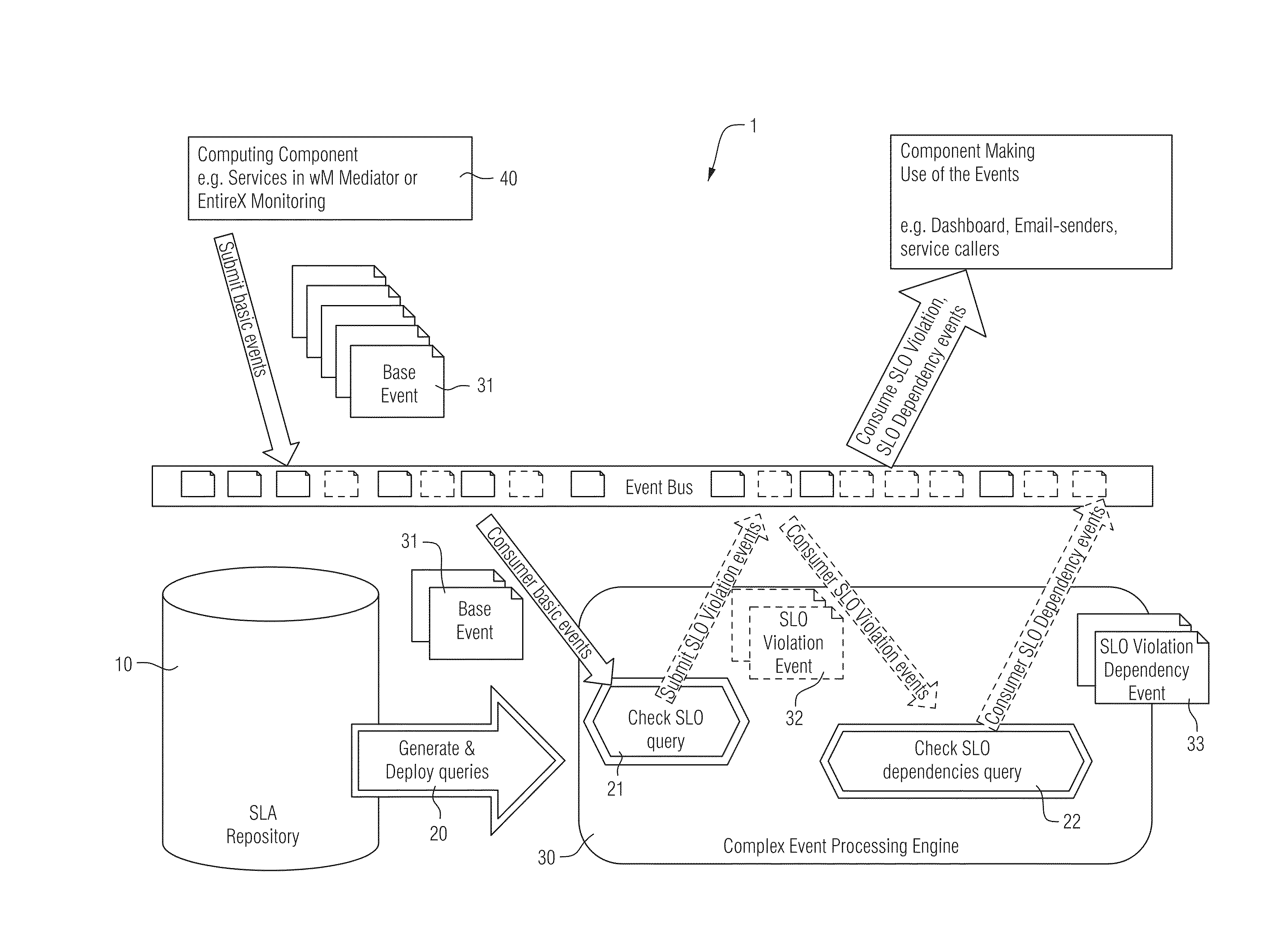
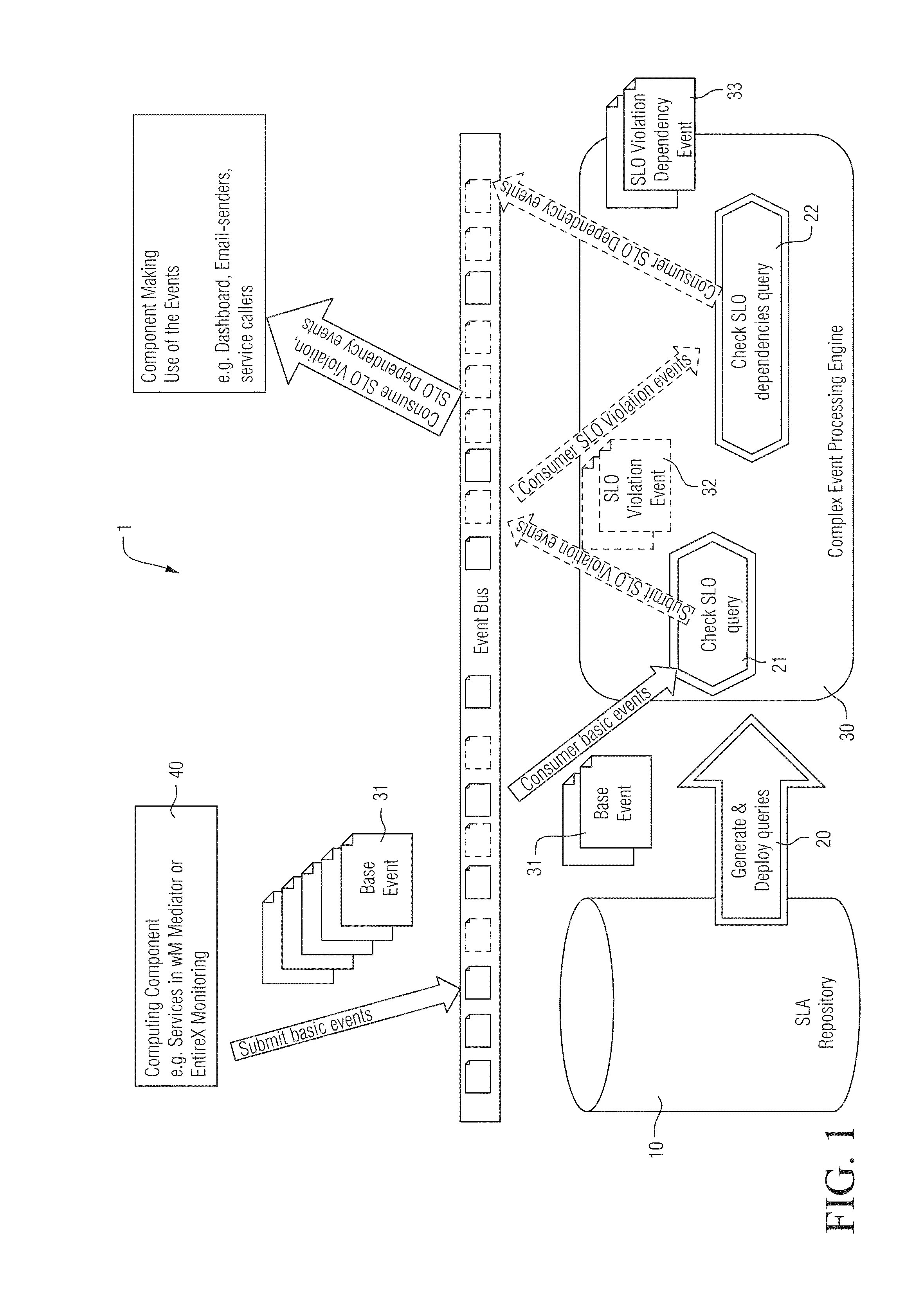
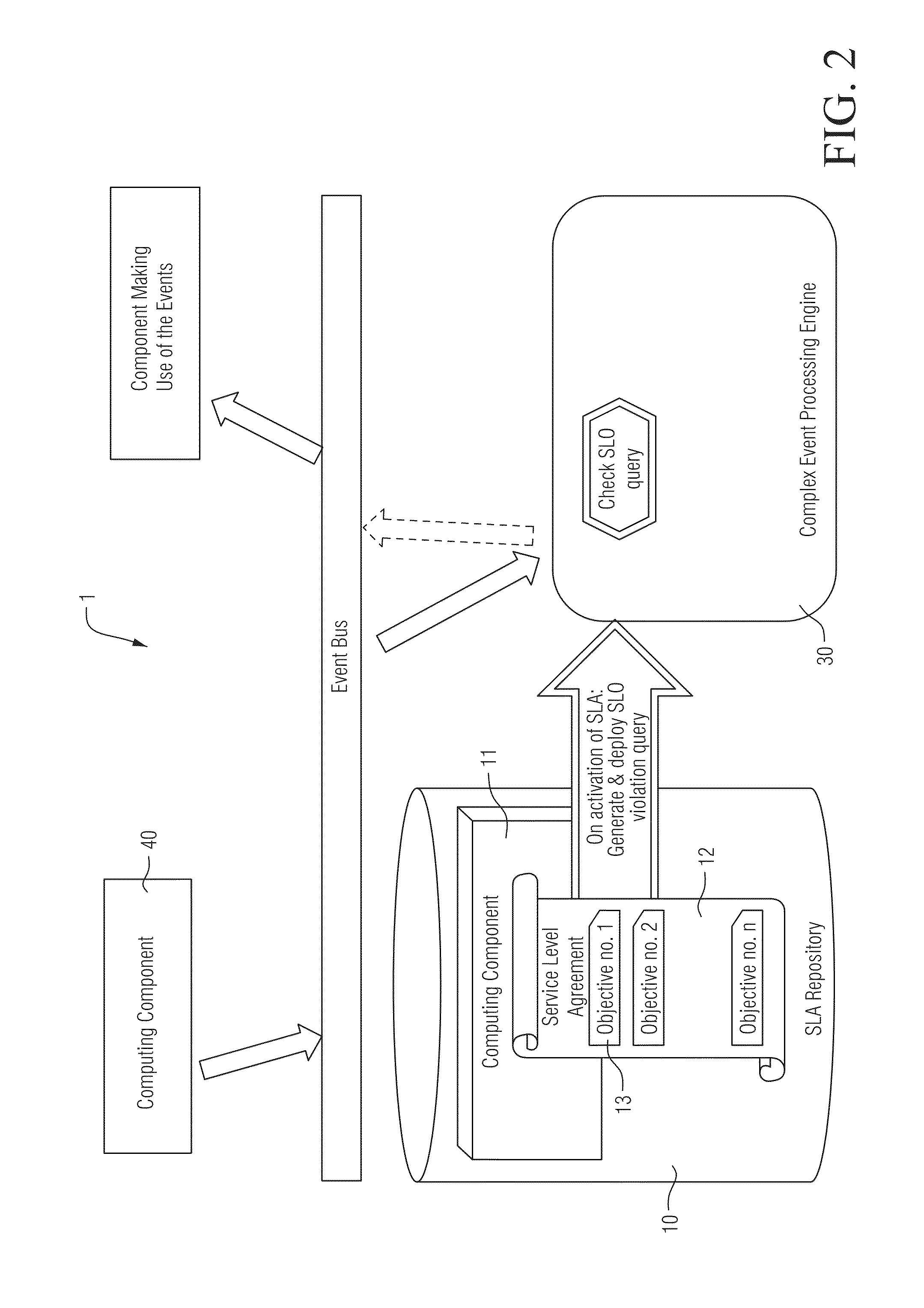
ActiveUS20140337510A1Easy and efficient and automated usageEfficient and reliable detectionError detection/correctionDigital computer detailsComplex event processingMonitoring system
Certain example embodiments relate to a monitoring system for monitoring the operation of distributed computing components. The monitoring system includes a registry for storing descriptions of the computing components and at least one associated service-level agreement (SLA) specifying at least one performance requirement; a compiler for generating at least one first and second continuous query based on the information stored in the registry; and a complex event processing (CEP) engine for executing the at least one first continuous query on input events indicating actions performed by the computing components and corresponding performance information, and for producing at least one output event indicating a violation of at least one SLA. The CEP engine also executes the at least one second continuous query on input events indicating a violation of at least one SLA, and produces at least one output event indicating a relationship between at least two SLA violations.
Owner:SOFTWARE AG
Hierarchical connected graph model for implementation of event management design
InactiveUS20050144624A1Avoid approachingDigital computer detailsMultiprogramming arrangementsOperational systemEvent type
An automated method and system for the implementation of a hierarchical event relationship network for correlation analysis in a distributed computing environment in which events are defined based on a connected graph model. Event handling information for each event type to be monitored is used to customize a plurality of rule templates for each type within an event source, where the event source is a hardware component, an application software component or an operating system platform. A plurality of event relationship network rules are verified to ensure they do not violate an event protocol. A hierarchical class definition and naming structure is generated from the plurality of event relationship network rules for each event source. Event management rules are then generated automatically for each event type from the event relationship network rules and the rule templates. The event management rules are loaded into a rule-based event manager. The performance of the rule-based event manager is then monitored.
Owner:KYNDRYL INC
Dynamically selecting or creating a policy to throttle a portion of telemetry data
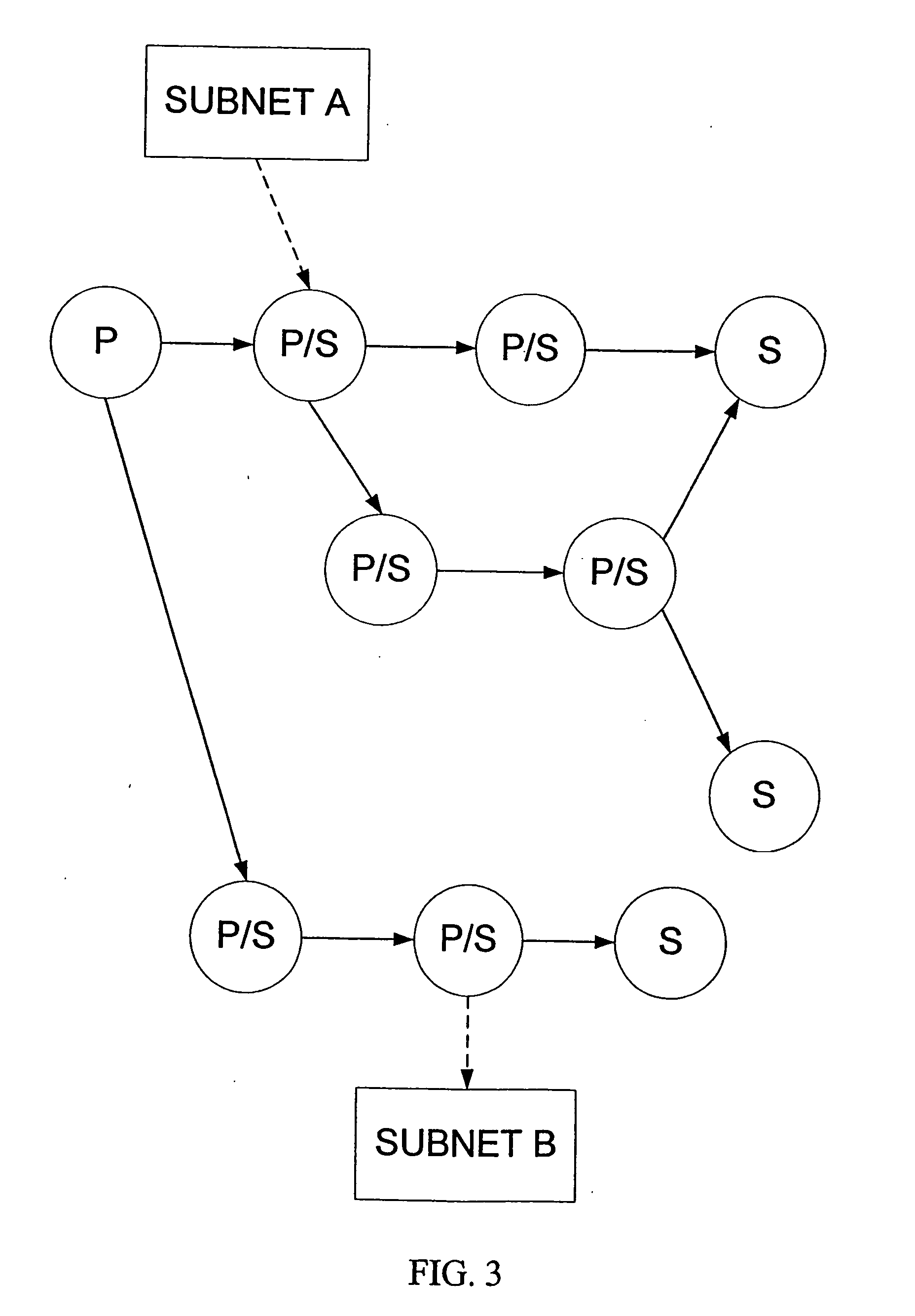
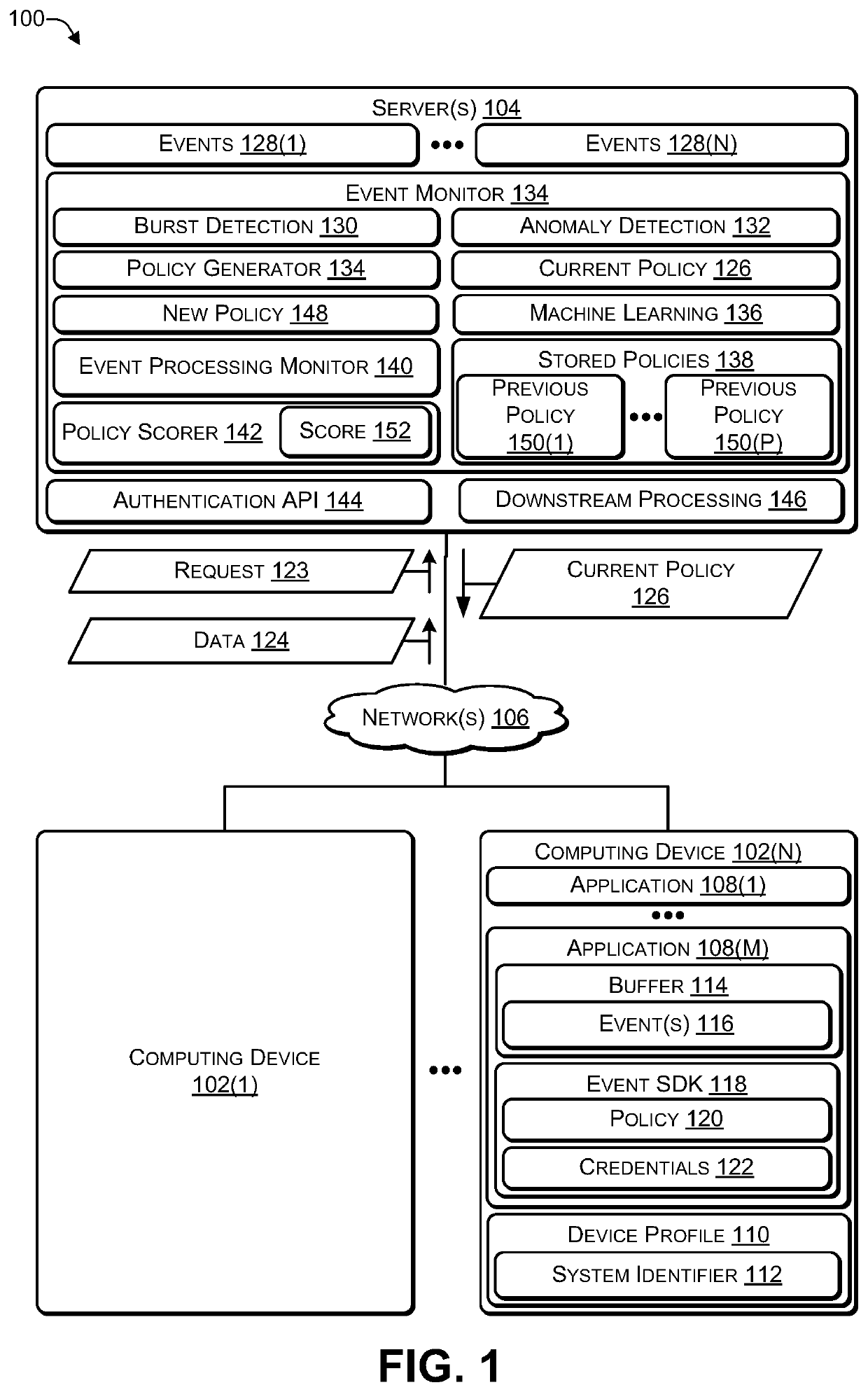
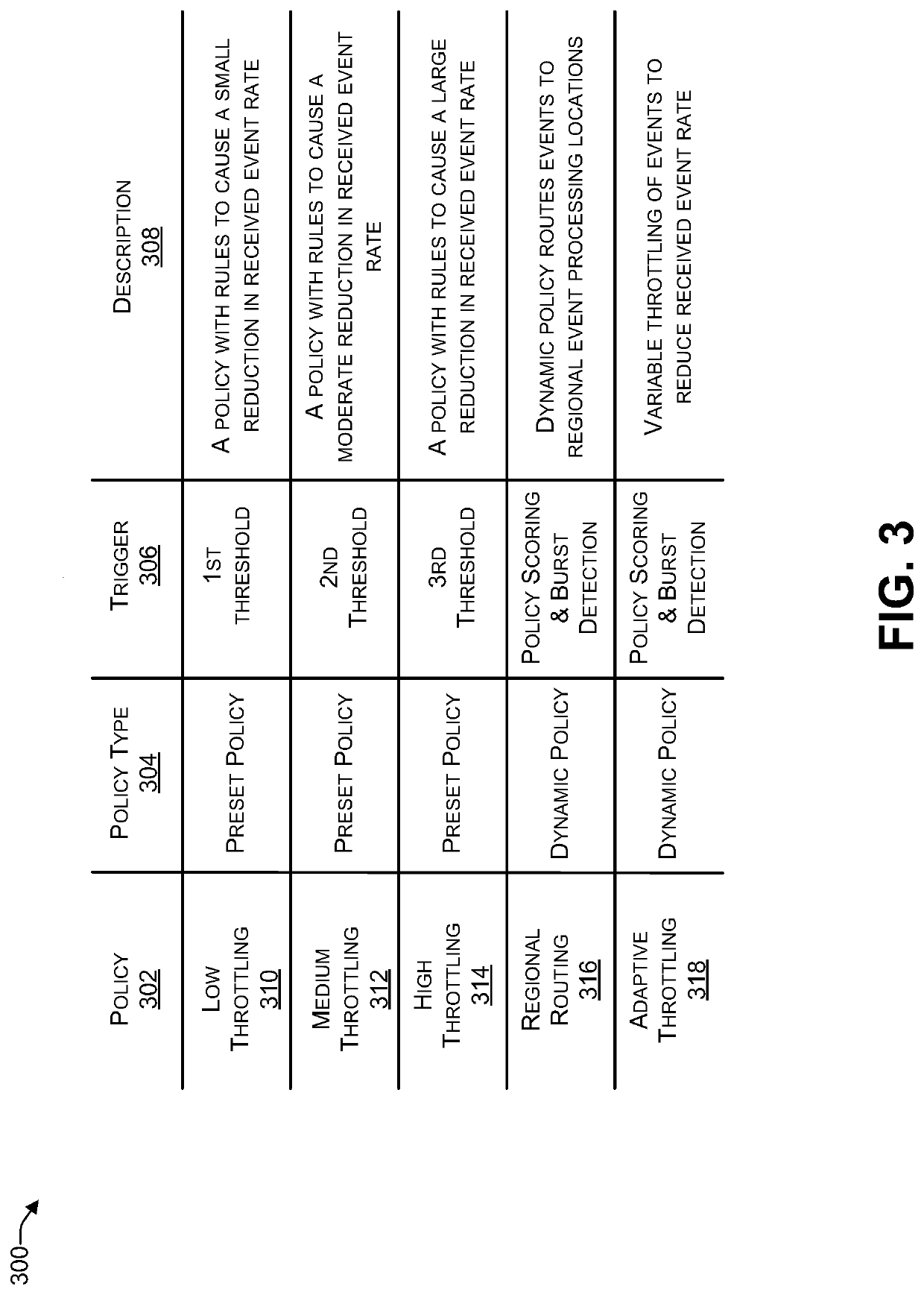
ActiveUS20200036603A1Well formedReduce incidenceMain station arrangementsSub-station arrangementsEvent (computing)Database
In some examples, a server may receive a set of events from individual computing devices of a plurality of computing devices. For example, the server may receive first data identifying a first set of events that occurred on a first computing device and receive second data identifying a second set of events that occurred on a second computing device. The server may determine an event rate at which events are being received based at least in part on: the first set of events, the second set of events, and a time interval. The server may perform an analysis of at least the first set of events and the second set of events, and create, based on the analysis, a policy to reduce the event rate. The server may provide the policy to at least the first computing device and the second computing device.
Owner:DELL PROD LP
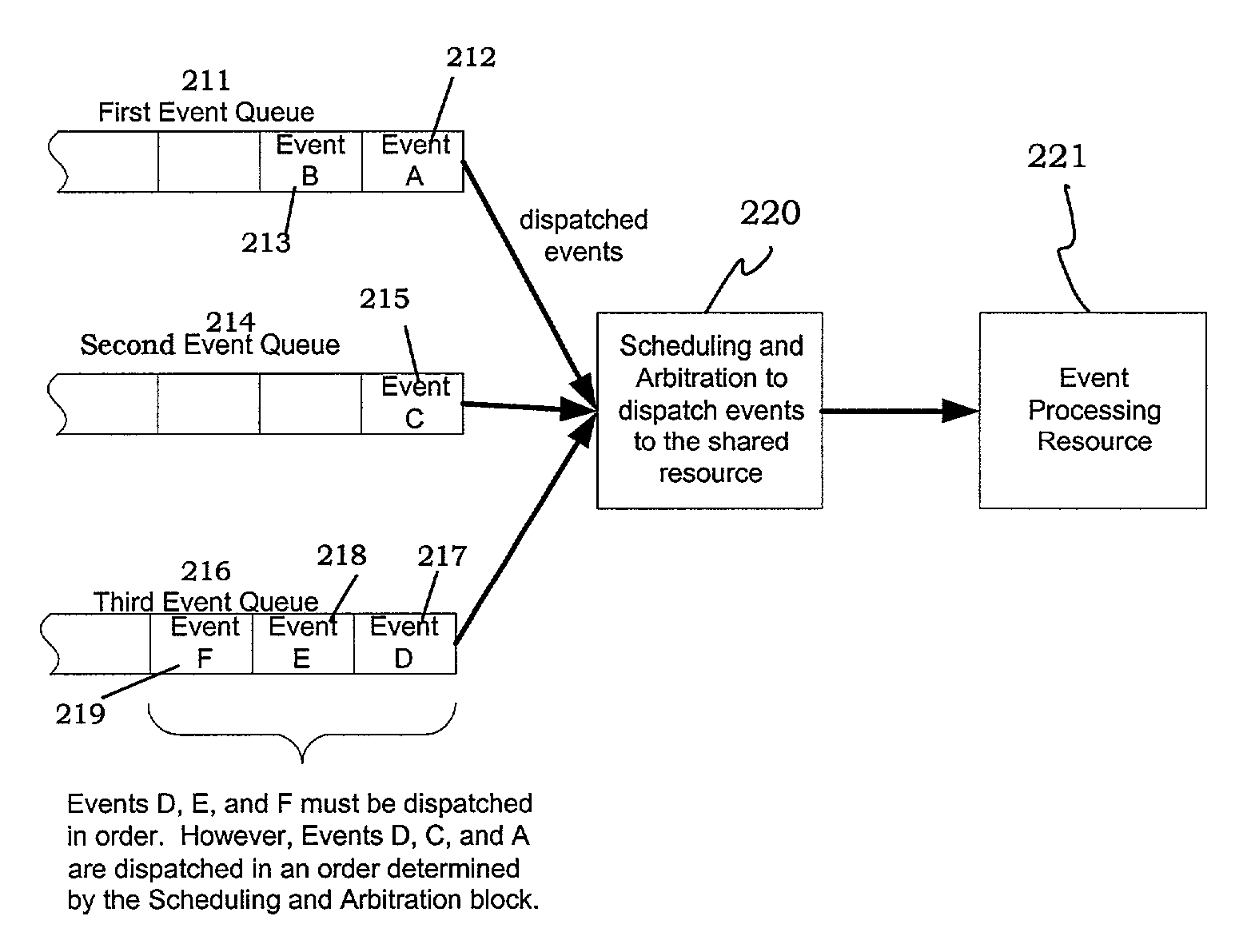
System and method for scheduling and arbitrating events in computing and networking
InactiveUS8032561B1Increase speedIncrease the number ofDigital data information retrievalData processing applicationsHardware implementationsData structure
A method for high-speed scheduling and arbitration of events for computing and networking is disclosed. The method includes the software and hardware implementation of a unique data structure, known as a pile, for scheduling and arbitration of events. According to the method, events are stored in loosely sorted order in piles, with the next event to be processed residing in the root node of the pile. The pipelining of the insertion and removal of events from the piles allows for simultaneous event removal and next event calculation. The method's inherent parallelisms thus allow for the automatic rescheduling of removed events for re-execution at a future time, also known as event swapping. The method executes in O(1) time.
Owner:ALTERA CORP
System and method for realizing cloud computing application interface integration and unified style display
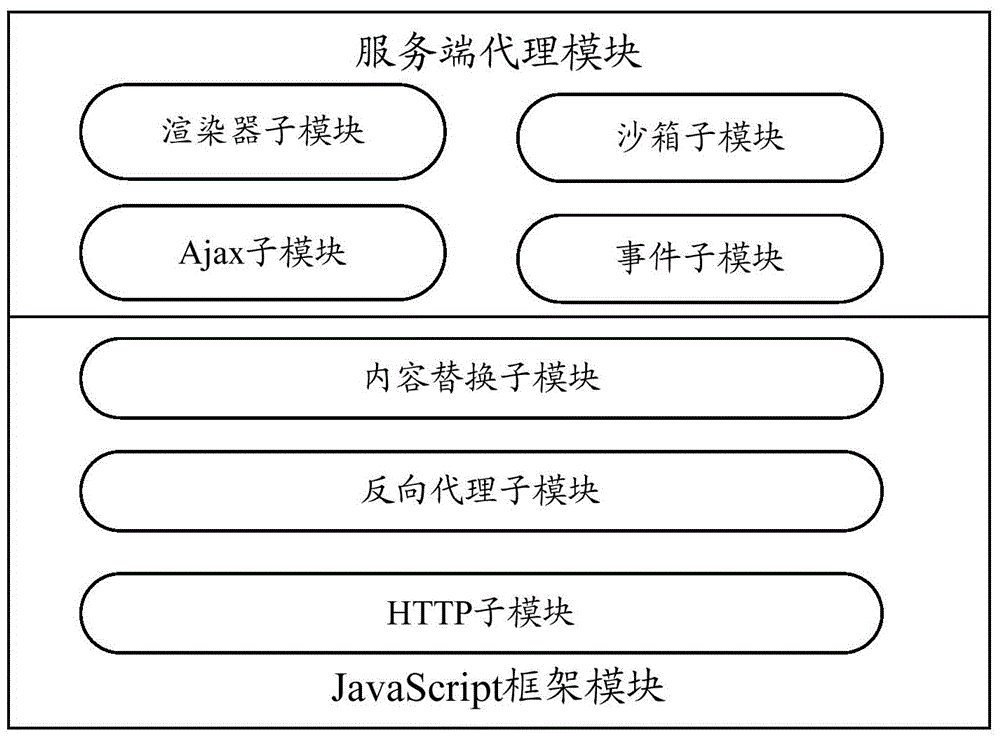
InactiveCN103605527AFlexible JavaScript InteractionQuick responseSpecific program execution arrangementsCloud computingServer agent
The invention relates to a system for realizing cloud computing application interface integration and unified style display. The system comprises a server agent module and a JavaScript frame module, wherein the server agent module comprises an HTTP (hyper text transport protocol) submodule, a reverse proxy submodule and a content replacement submodule; the JavaScript frame module comprises an event submodule, an Ajax submodule, a sand box submodule, a base submodule and a renderer submodule. According to the system and method for realizing cloud computing application interface integration and unified style display, the defects that multiple system interfaces are non-uniform in styles and the interfaces are limited through JavaScript interaction in the prior art can be overcome, a unified interface through which an agent module is not needed to be provided by integrated application and a flexible JavaScript interaction high-response speed interface access effect is achieved is provided, various cost input of the application integration is reduced, more mistakes of code logics are avoided, and the system is suitable for large-scale popularization and application.
Owner:PRIMETON INFORMATION TECH
Process automation action repository and assembler
ActiveUS20190171513A1Programme-controlled manipulatorNon-redundant fault processingTime conditionSoftware engineering
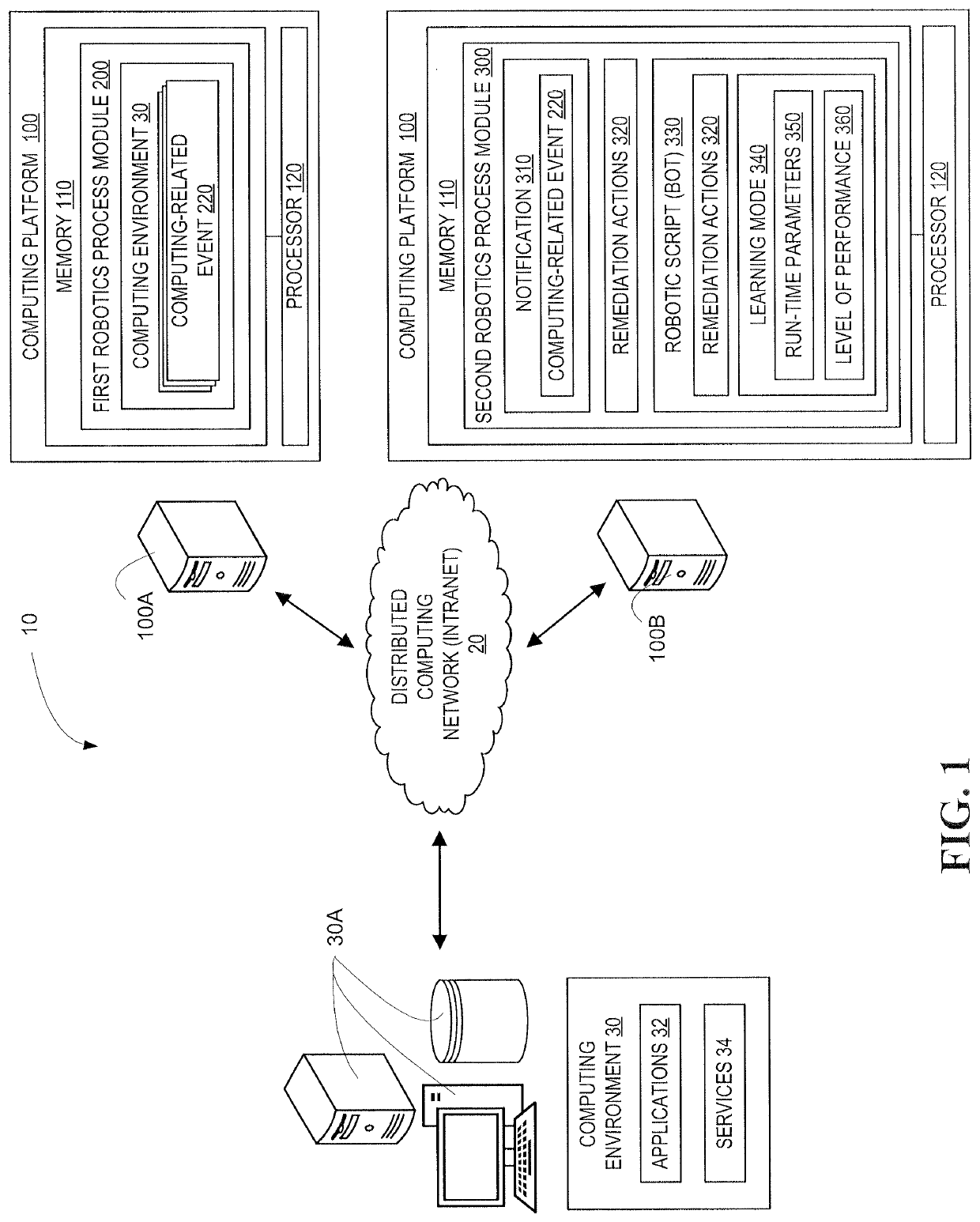
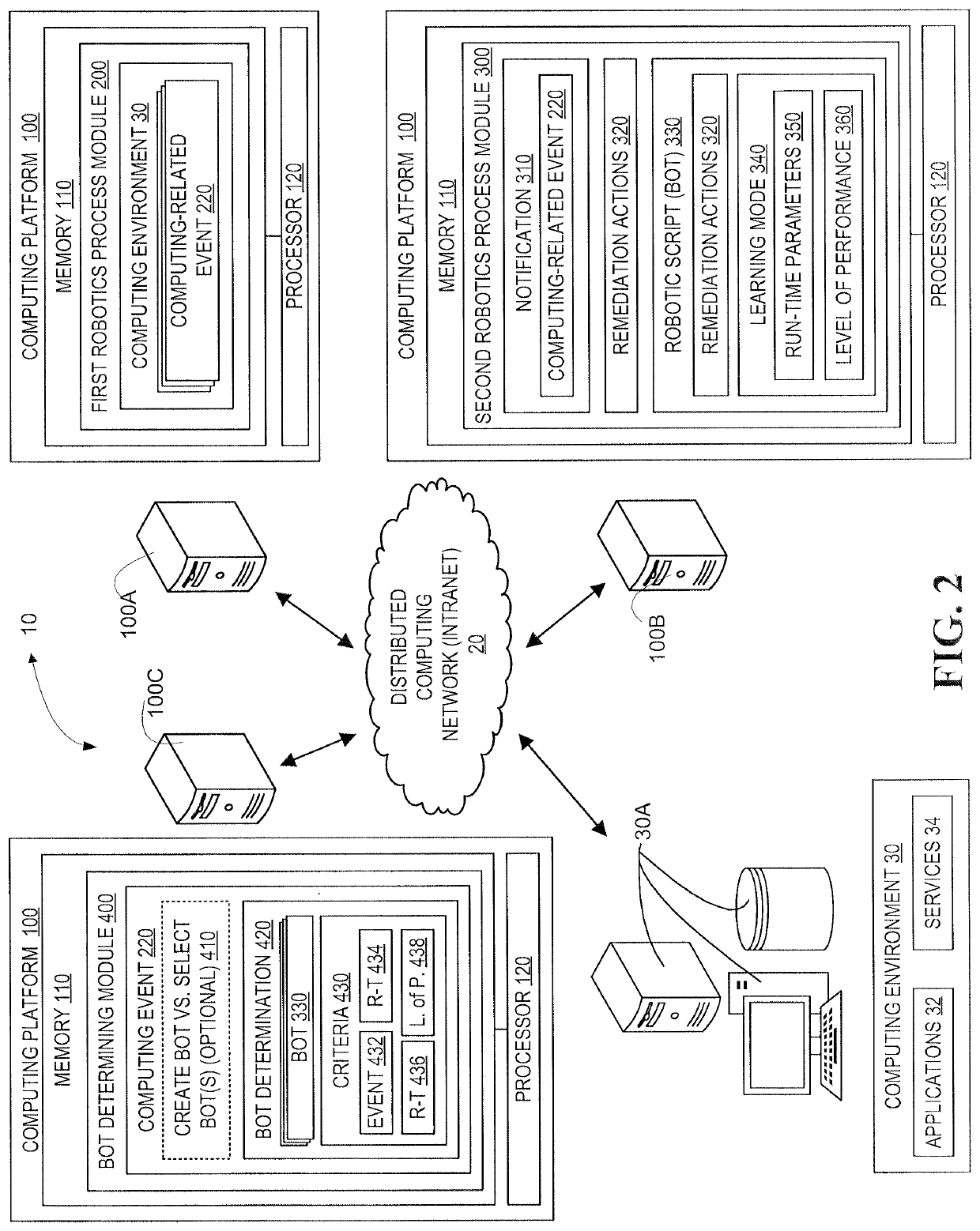
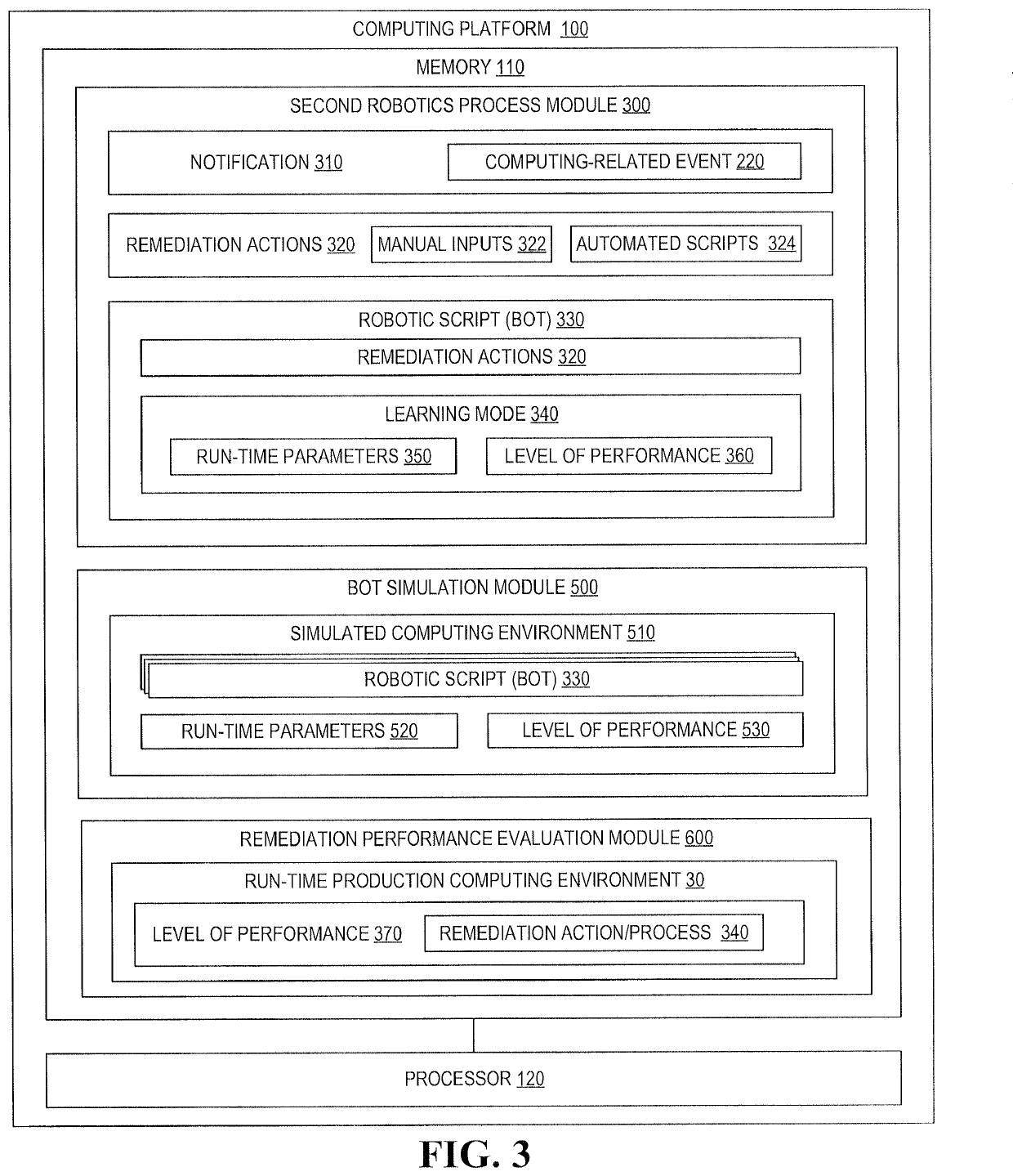
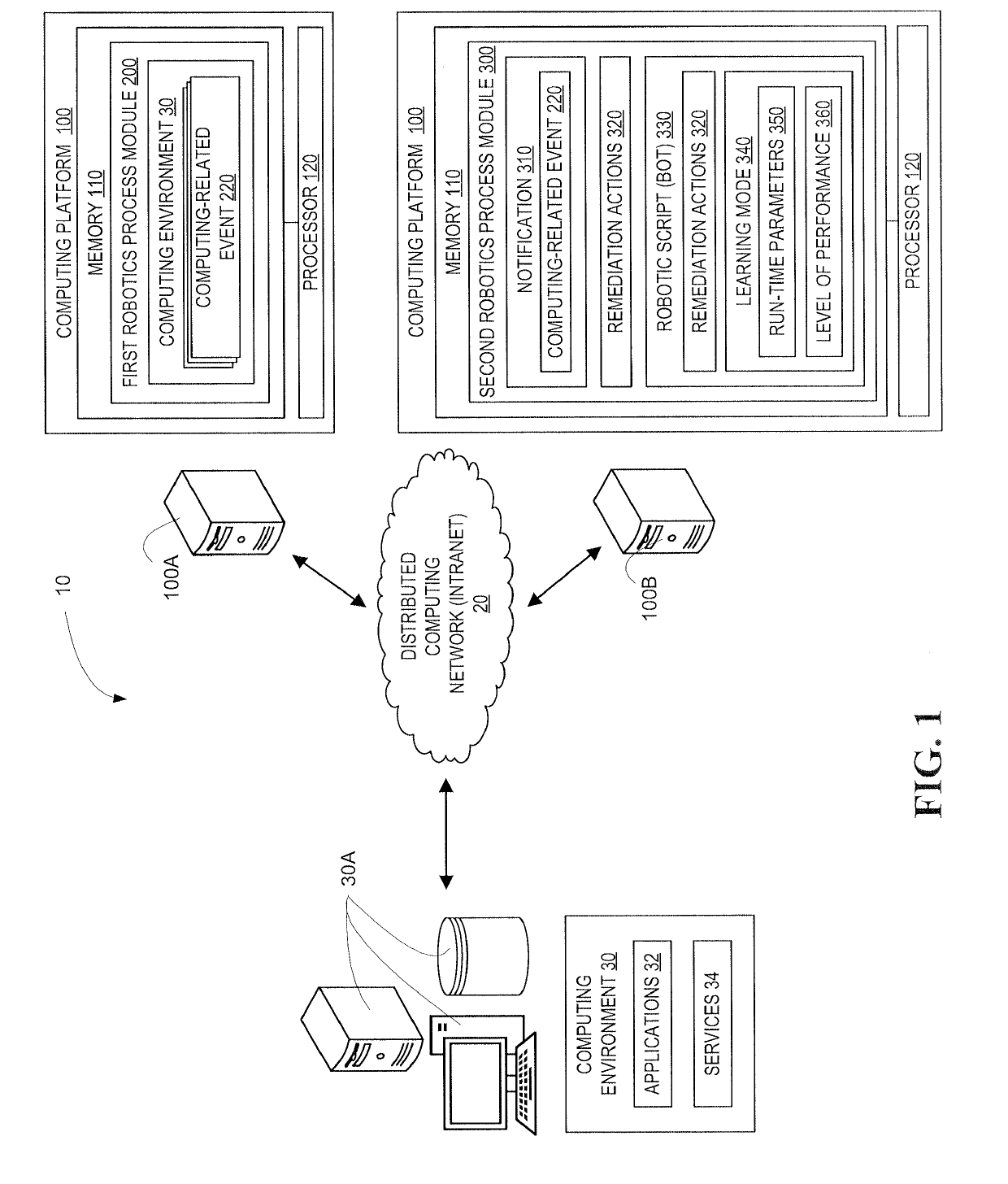
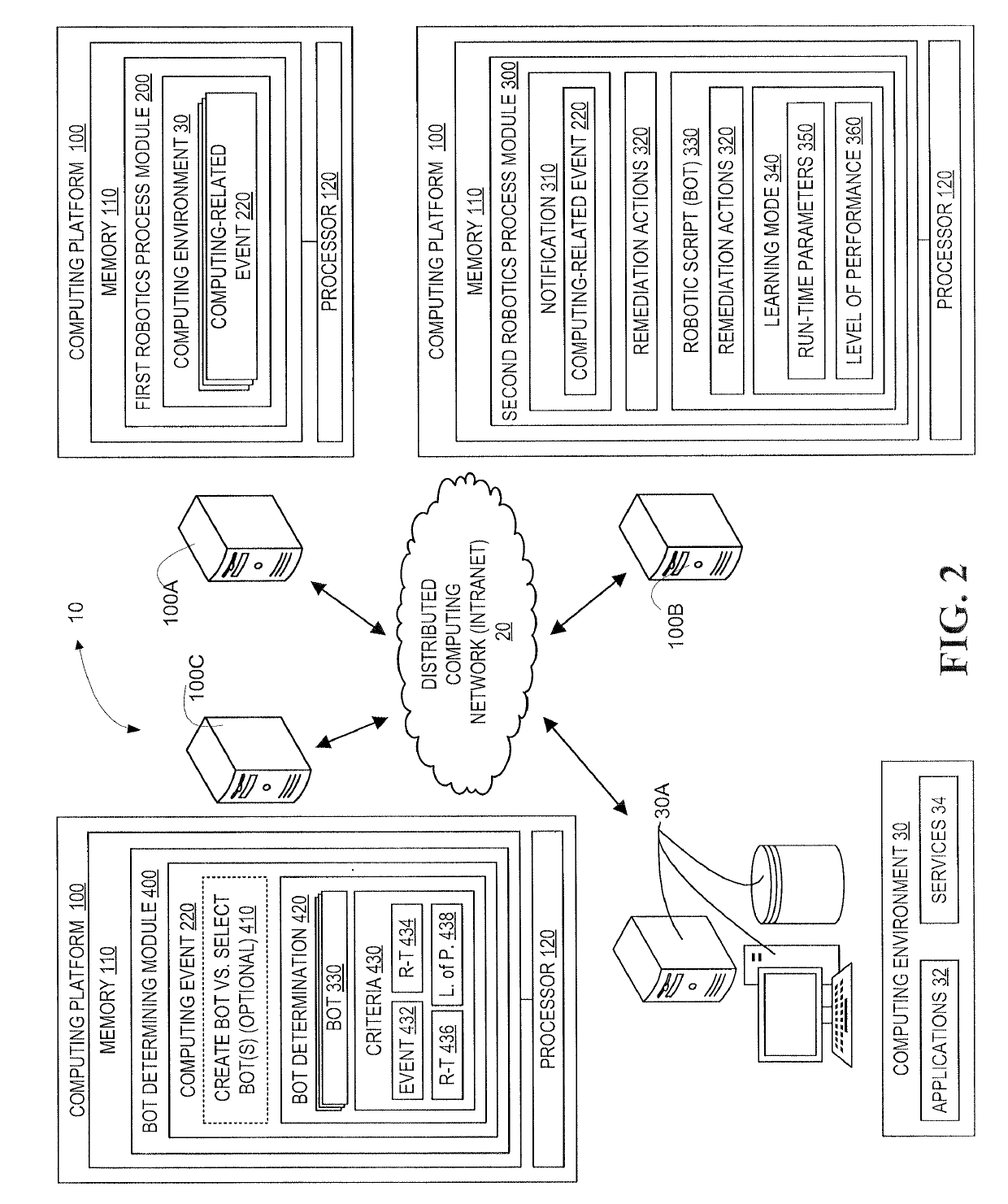
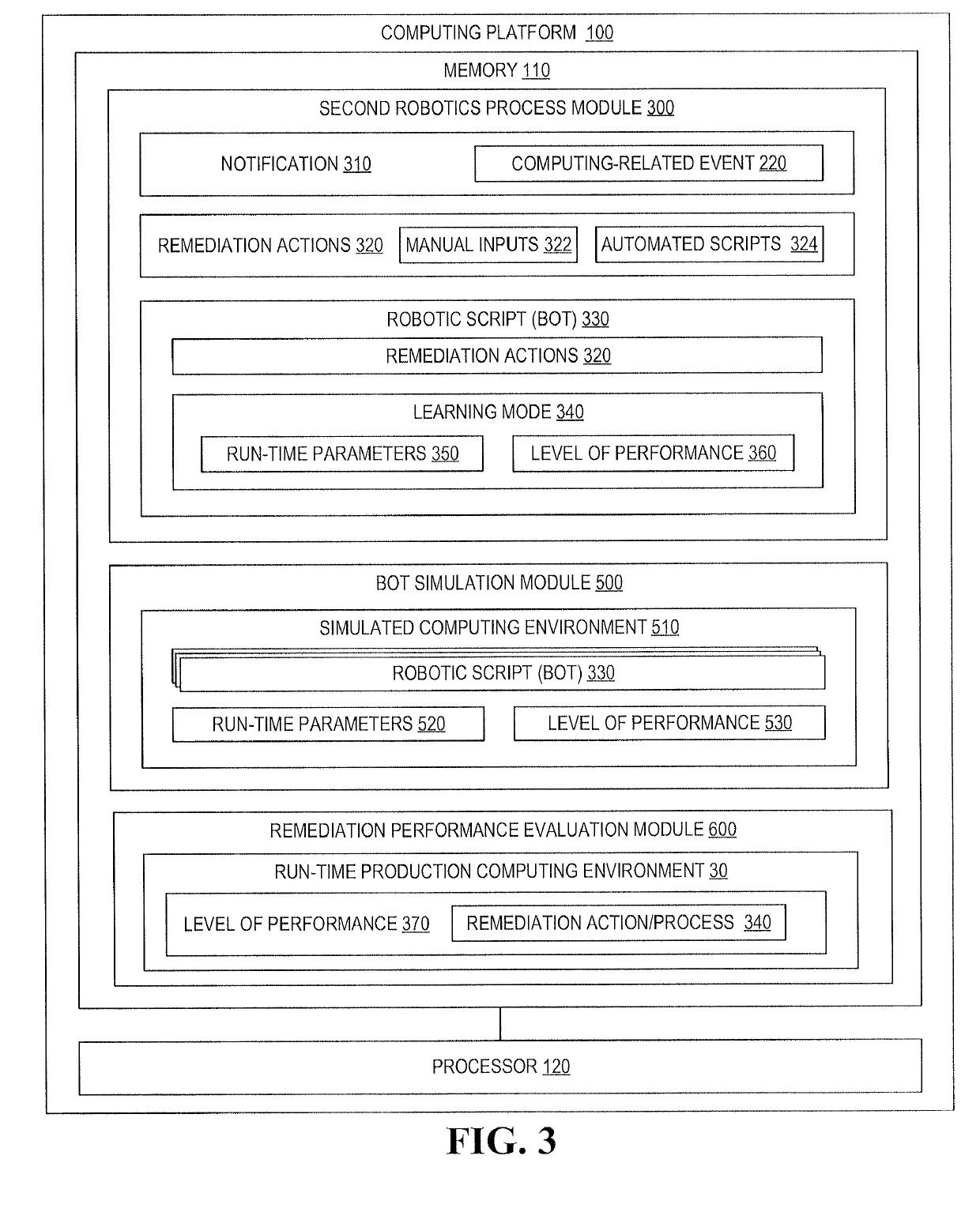
A system for remediating computing-related events by taking into account the past performance of remediation processes and the current run-time environment in which the remedy will be deployed. Robotic Process Automation is implemented to identify computing-related events requiring automation and to record actions that are taken to remediate the events. Robotic scripts (bots) are created based on the recorded actions and are implemented in a learning-mode, in which run-time conditions and level of performance are recorded, such that, run-time conditions and performance are determinative of which bot or combination of bots are implemented for subsequent occurrence of computing-related events. Additionally, remedial process associated with the bot(s) may be executed in a simulated environment prior to the production run-time computing environment to validate the bot and insure the likelihood of effective performance of the remedial process in the run-time production environment.
Owner:BANK OF AMERICA CORP
Event heap: a coordination infrastructure for dynamic heterogeneous application interactions in ubiquitous computing environments
ActiveUS7702729B2Effective interactionEasy to parseMultiprogramming arrangementsMultiple digital computer combinationsTypingWorkspace
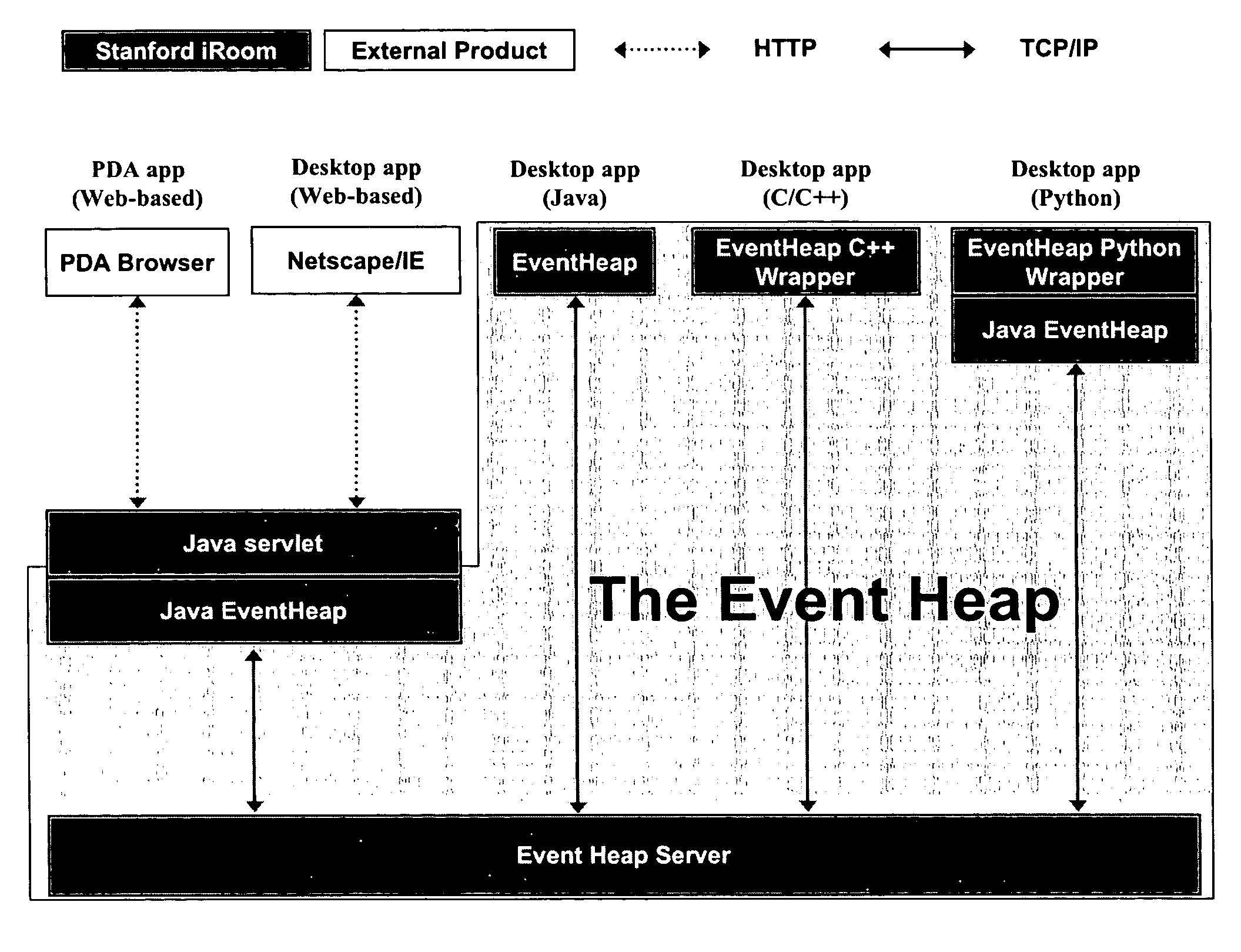
An efficient and adaptive middleware infrastructure called the Event Heap system dynamically coordinates application interactions and communications in a ubiquitous computing environment, e.g., an interactive workspace, having heterogeneous software applications running on various machines and devices across different platforms. Applications exchange events via the Event Heap. Each event is characterized by a set of unordered, named fields. Events are routed by matching certain attributes in the fields. The source and target versions of each field are automatically set when an event is posted or used as a template. The Event Heap system implements a unique combination of features, both intrinsic to tuplespaces and specific to the Event Heap, including content based addressing, support for routing patterns, standard routing fields, limited data persistence, query persistence / registration, transparent communication, self-description, flexible typing, logical / physical centralization, portable client API, at most once per source first-in-first-out ordering, and modular restartability.
Owner:TIDEBREAK
Internet-of-things enabled real-time event processing
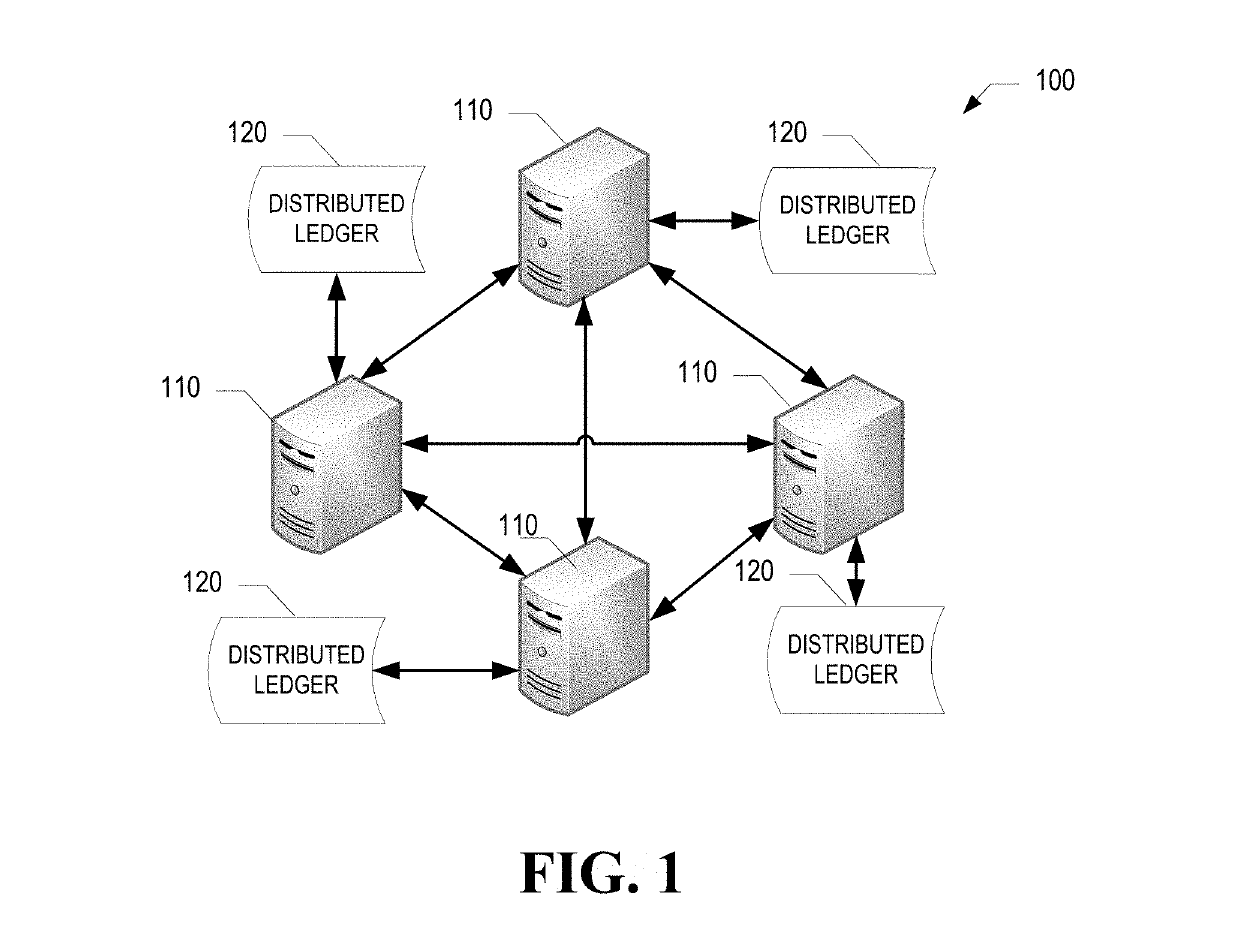
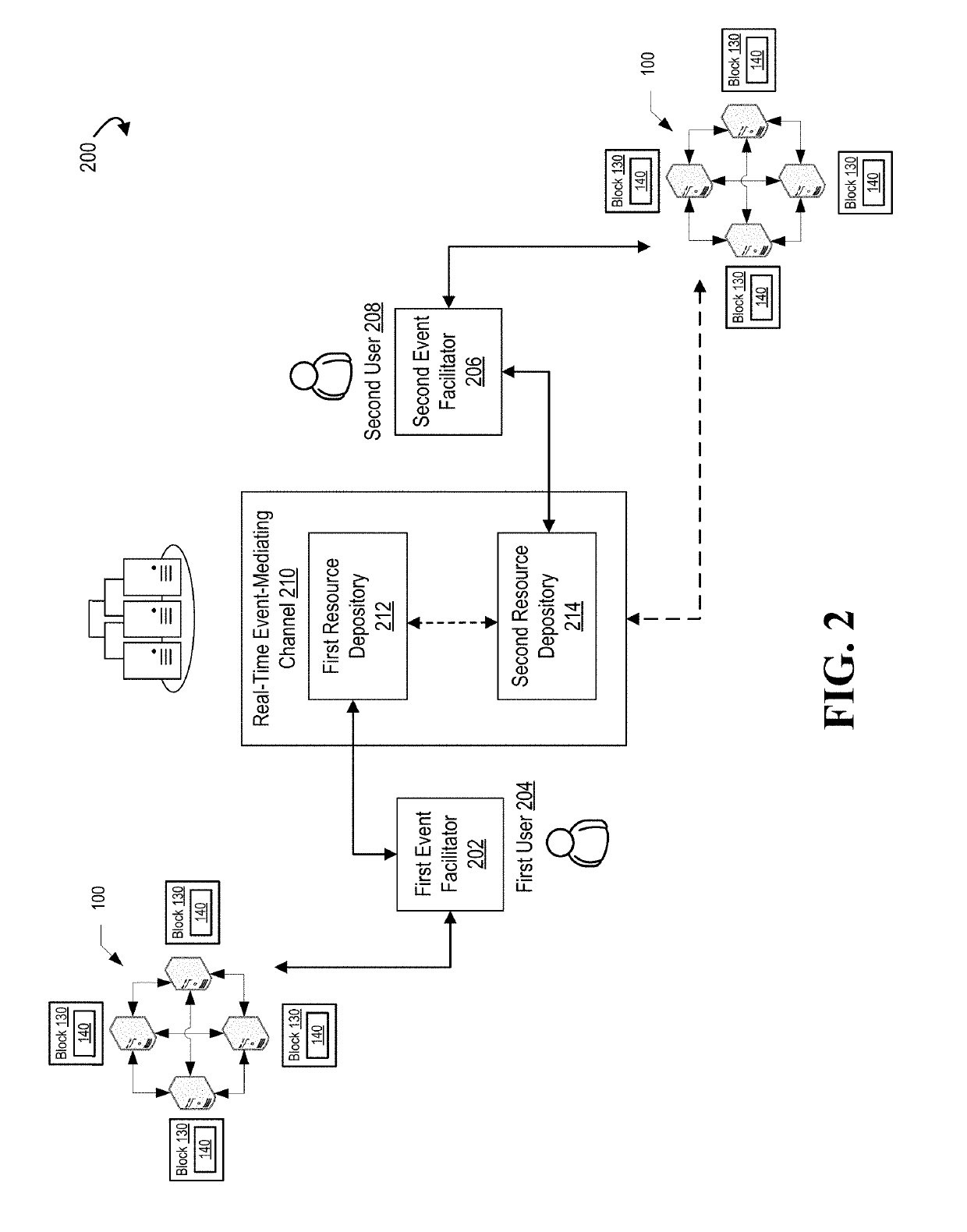
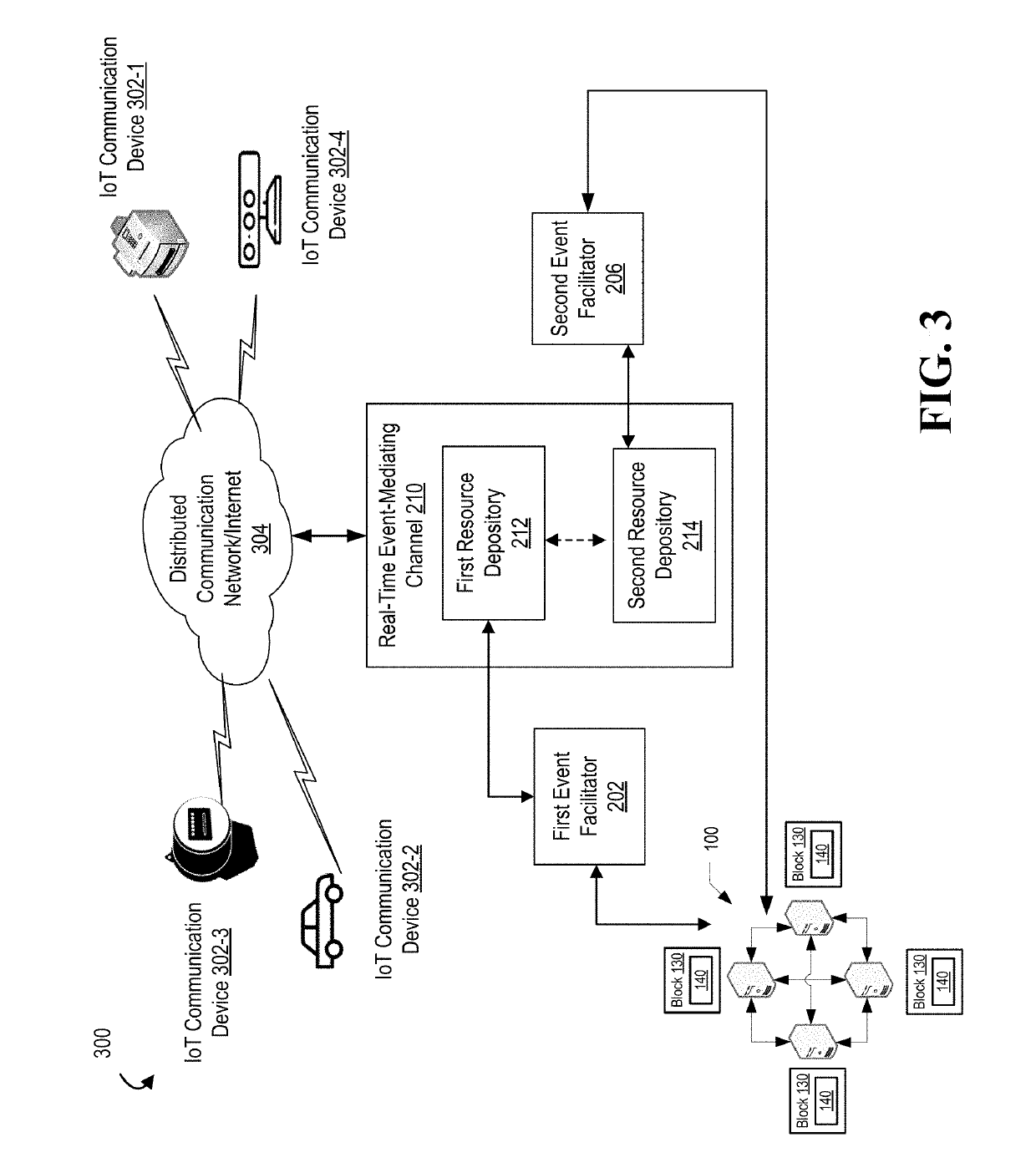
InactiveUS20190318329A1Encryption apparatus with shift registers/memoriesParticular environment based servicesBlockchainEvent correlation
The present invention provides for real-time (or near real-time) processing of computing events that are triggered by a threshold level being met by data detected at Internet-of-Things devices and, in response to meeting the threshold, communicating an event processing request to a real-time event-mediating channel. The real-time event-mediating channel is capable of processing such events in real-time or near real-time by storing event commitment records in a distributed blockchain network that authenticates a user associated with an event and authorizes an event facilitating entity to access a resource depository associated with the event.
Owner:BANK OF AMERICA CORP
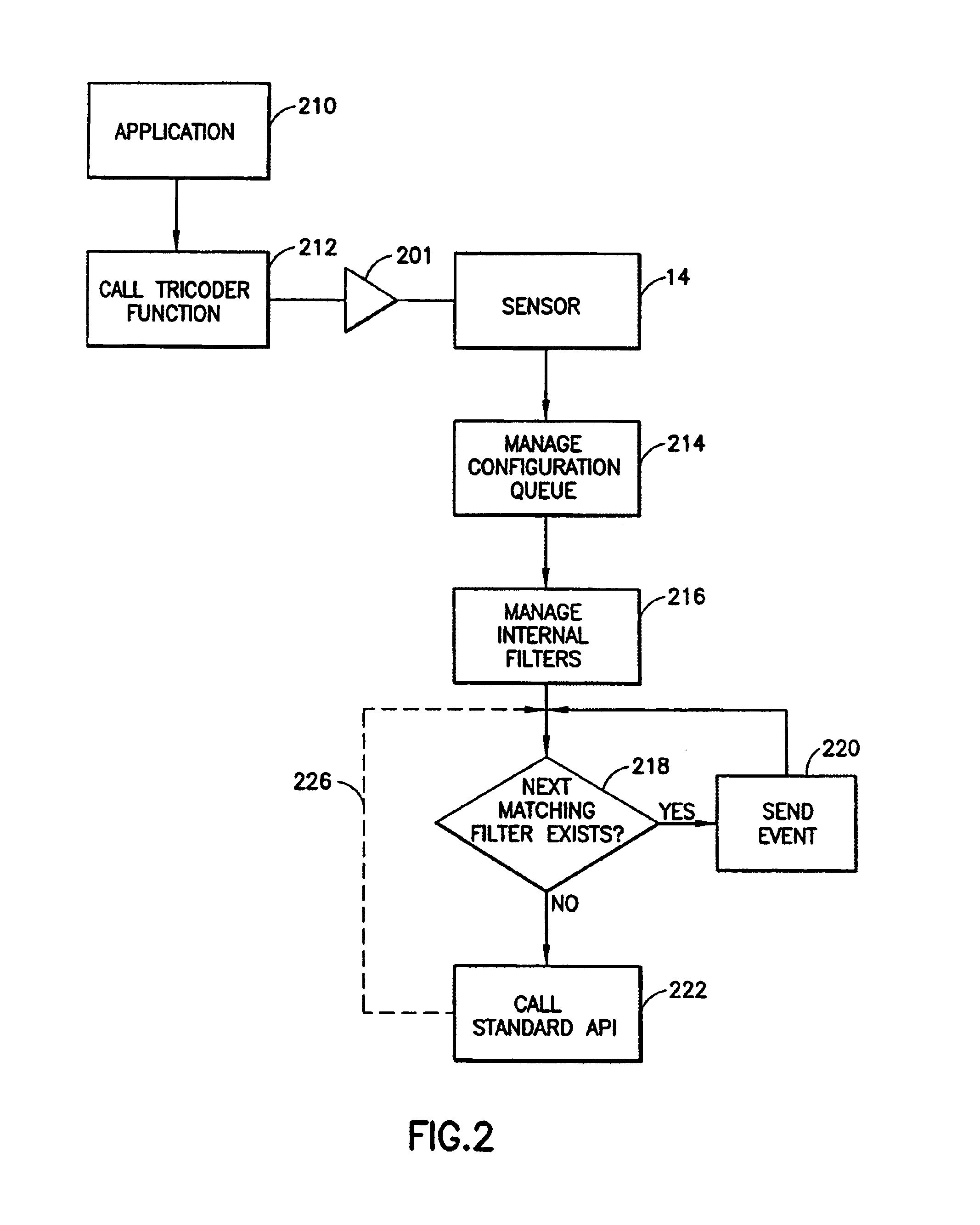
Method and apparatus for input management having a plurality of input provider types wherein staging area holds and allows access by external components
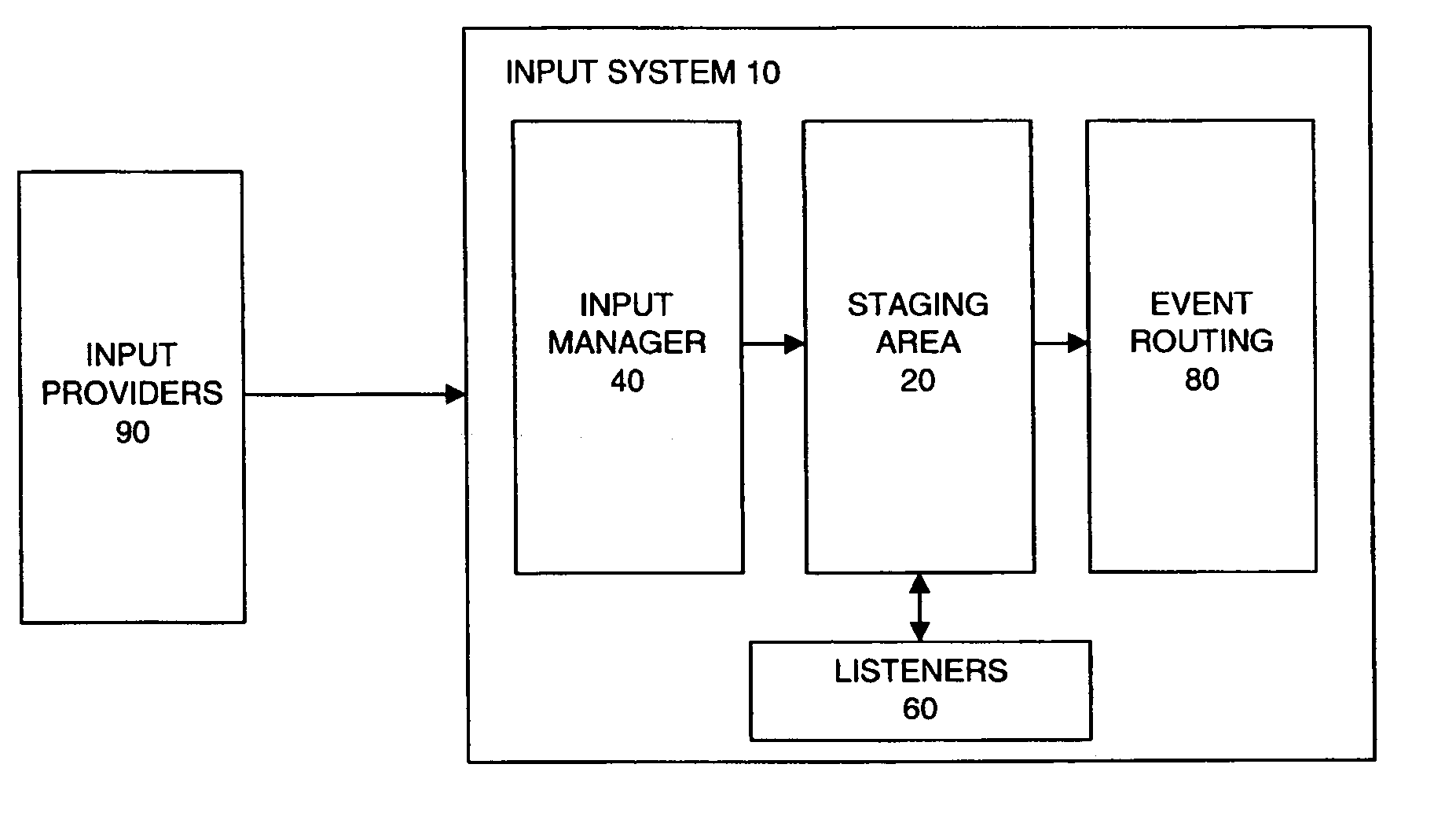
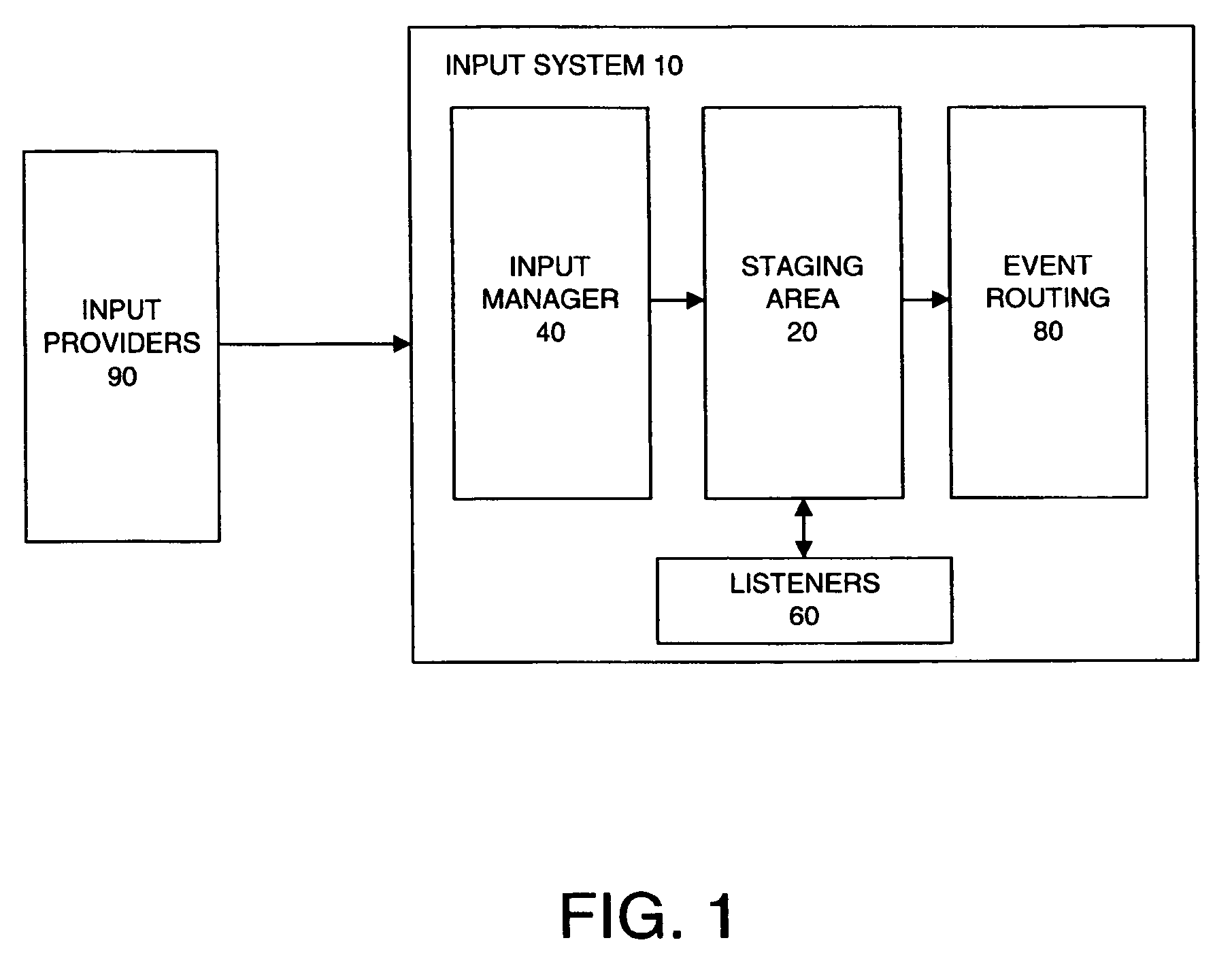
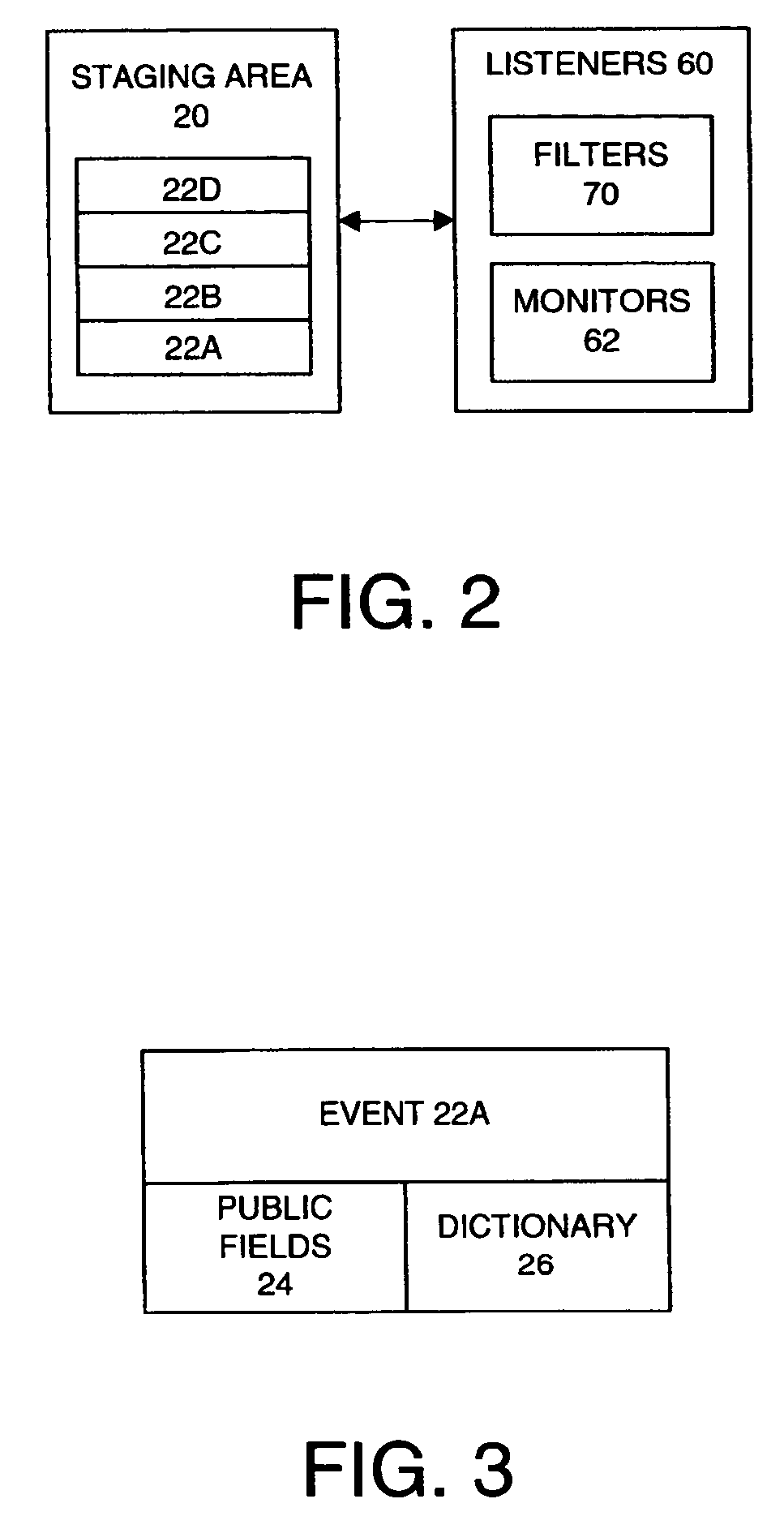
ActiveUS7093034B2Input/output for user-computer interactionInterprogram communicationEvent (computing)Computational environment
The present invention is directed to a method and system for use in a computing environment for managing input information. The system for facilitating input management in a computerized environment may include an input manager for processing events received from an input provider. The system may additionally include a staging area including a stack of events created by the input manager. The staging area allows access by external components. The external components may include a set of filters capable of accessing and manipulating the stack of input events and a set of monitors capable of monitoring manipulation of the stack of events.
Owner:MICROSOFT TECH LICENSING LLC
Globally valid measured operating system launch with hibernation support
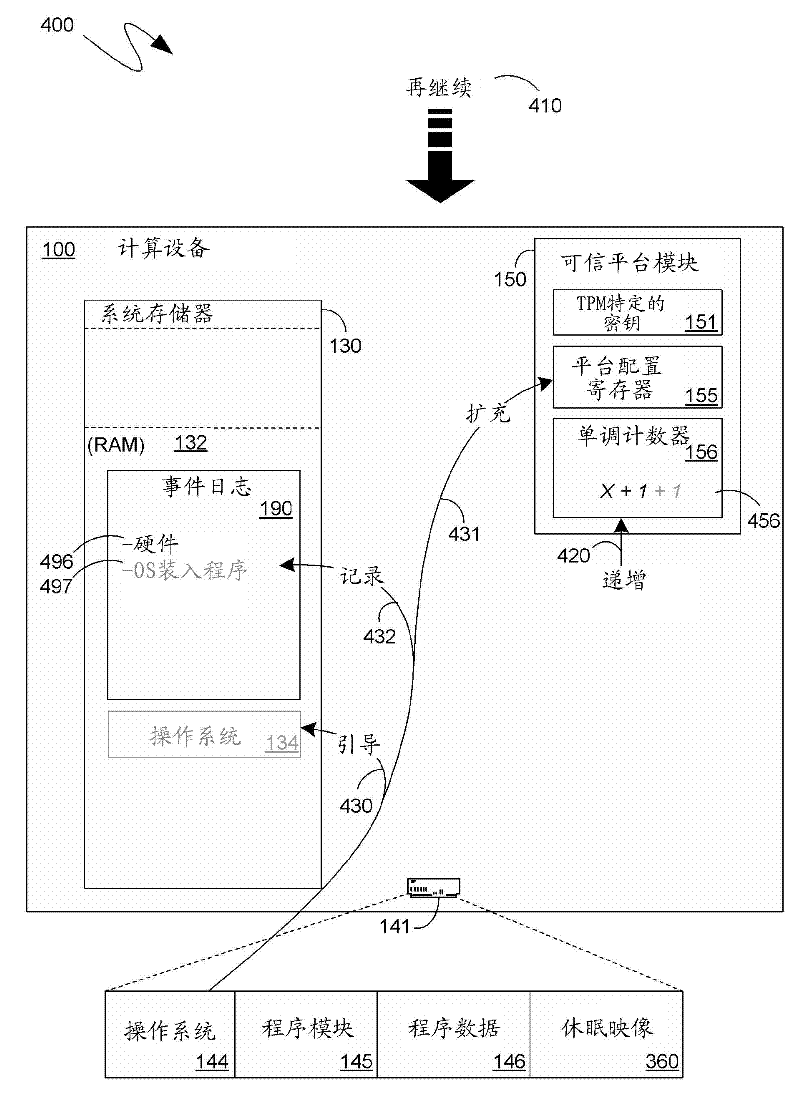
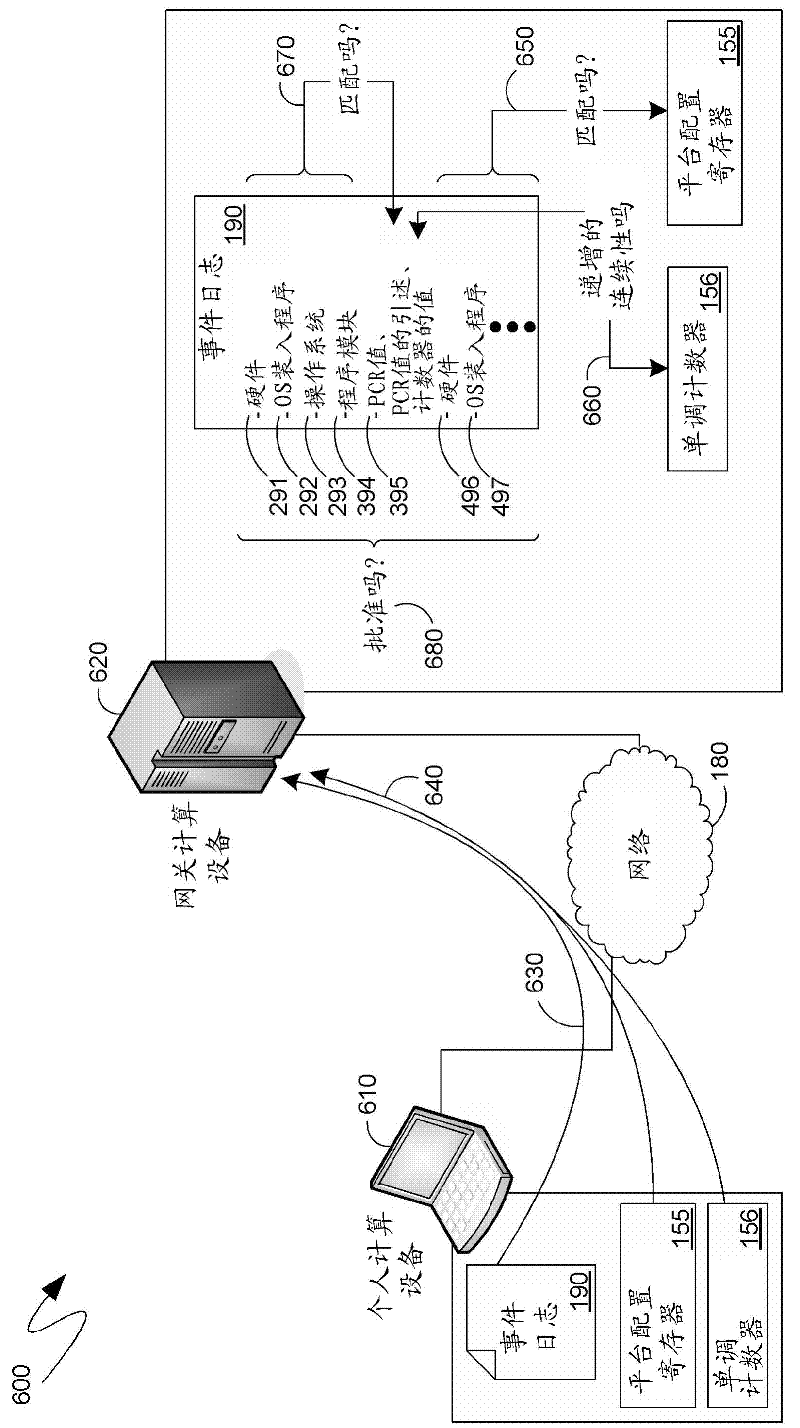
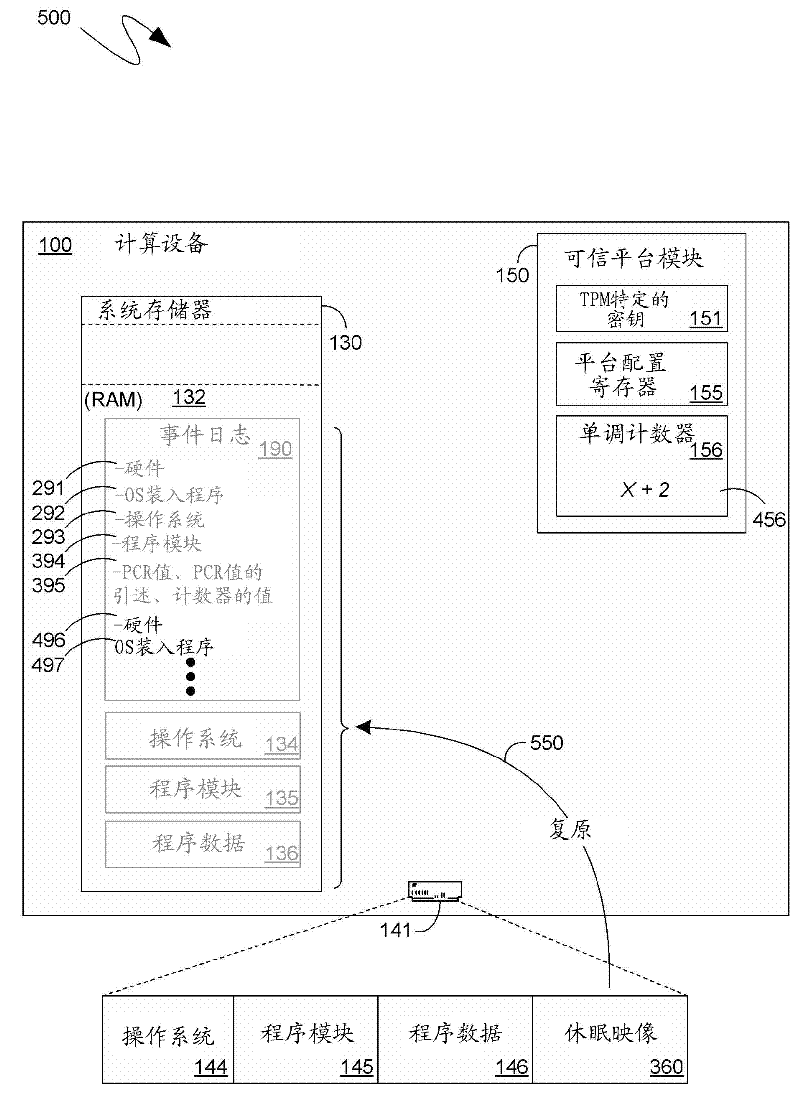
ActiveCN102509046APlatform integrity maintainanceSecuring communicationComputer hardwareOperational system
An event log can comprise, not only entries associated with components instantiated since a most recent power on of a computing device, but also entries of components instantiated prior to that power on, such as components that were instantiated, and represent, a state of the computing device prior to hibernation that has now been resumed. Upon hibernation, the current values of the Platform Configuration Registers (PCRs) of a Trusted Platform Module (trusted execution environment), as well as a quote of those current values, and a current value of a monotonic counter of the trusted execution environment can be logged. The monotonic counter can be incremented at each power on to track successive generations of the computing device and to guard against an intervening, not-logged generation. A subsequent parsing of the event log can verify the prior generational entries with reference to the PCR values in the log that are associated with those generations.
Owner:MICROSOFT TECH LICENSING LLC
Attention focusing model for nexting based on learning and reasoning
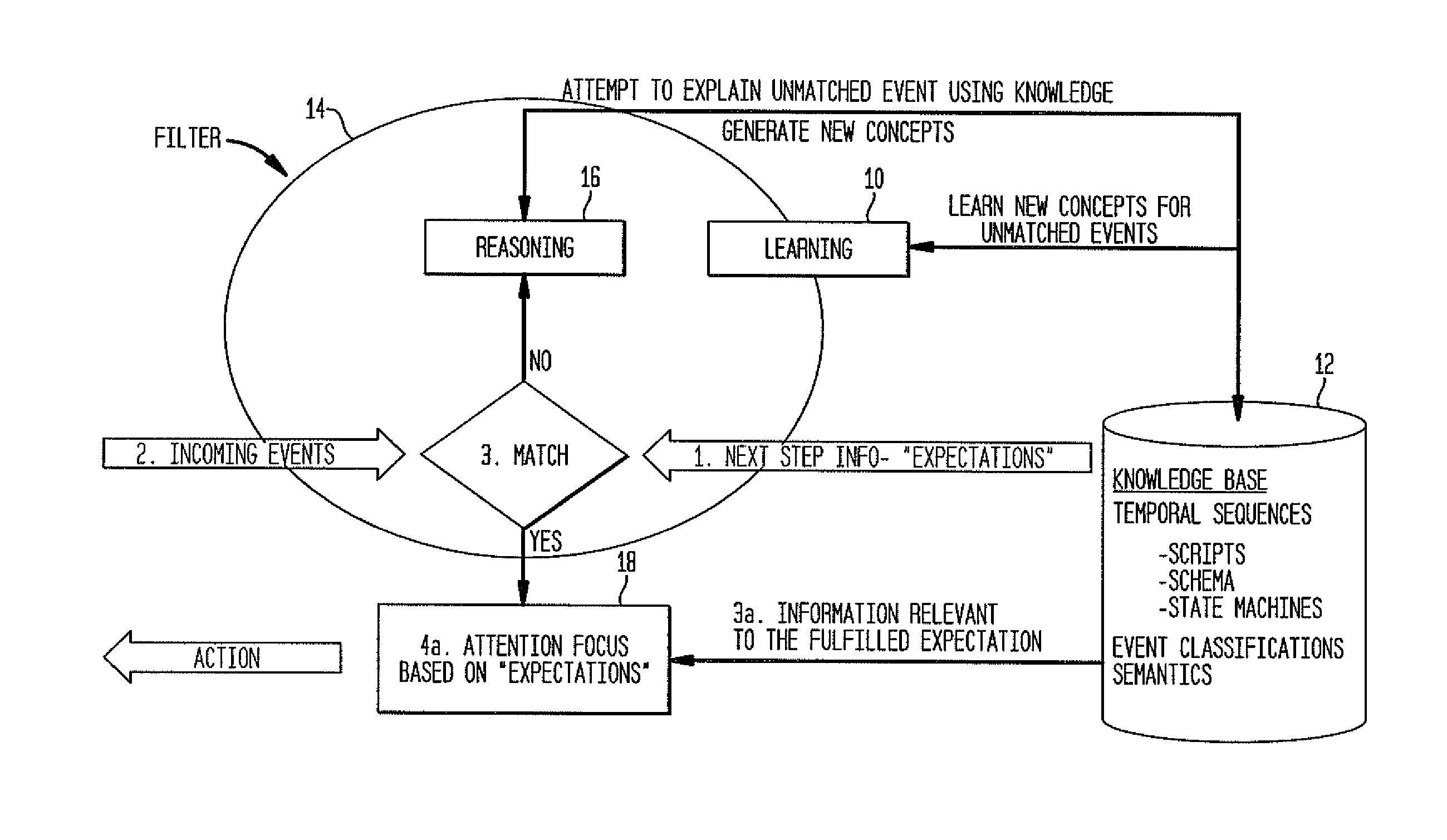
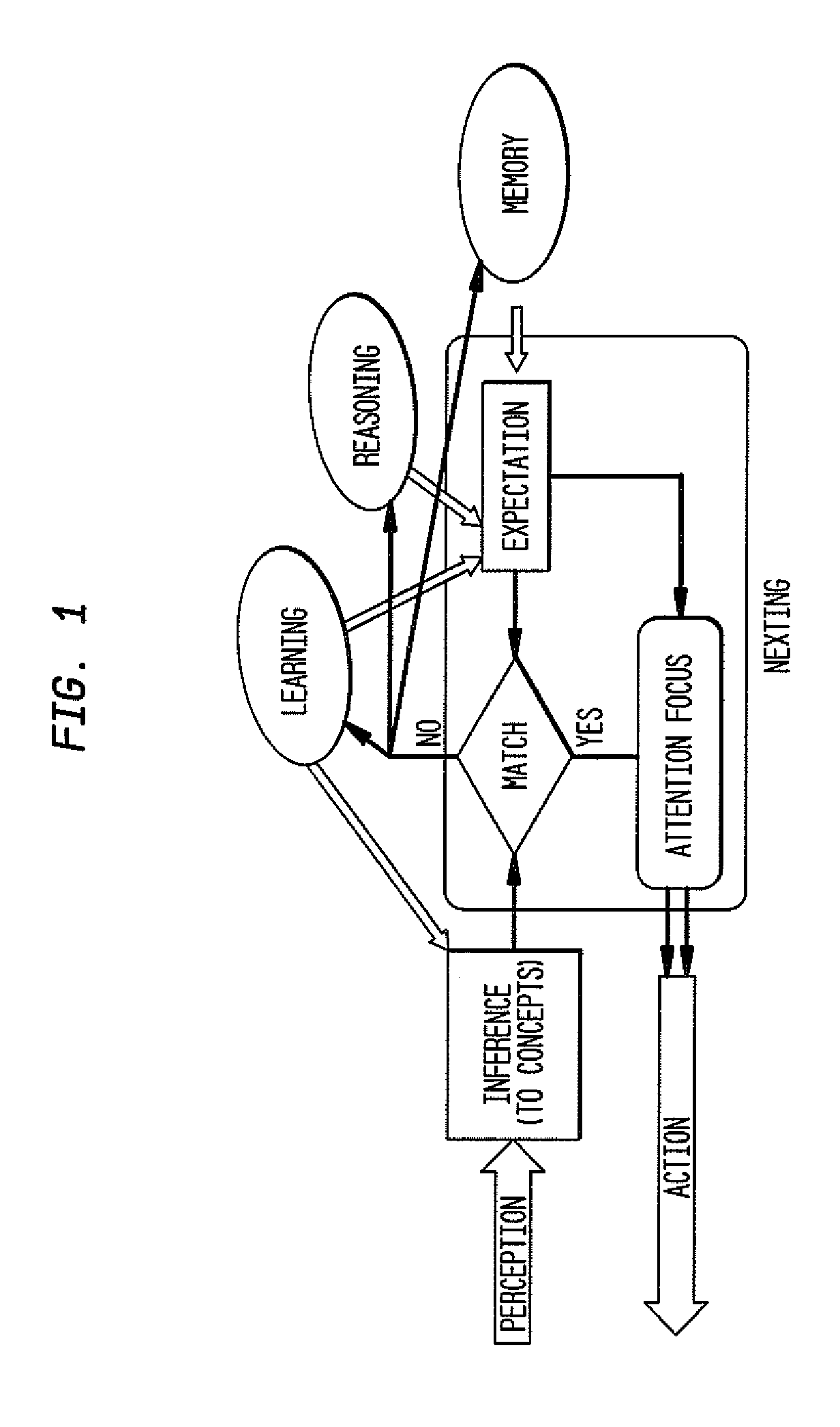
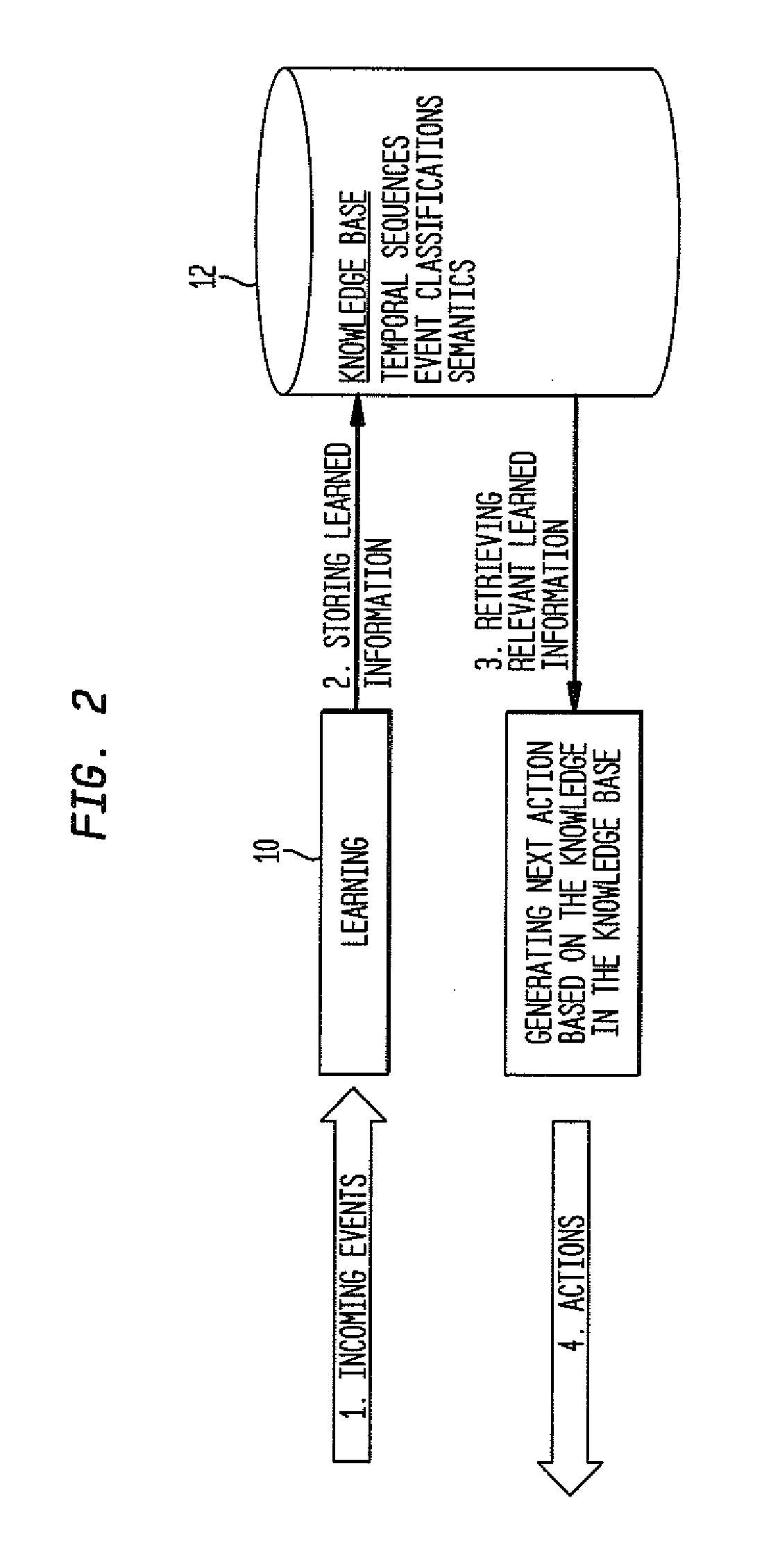
InactiveUS20120209796A1Improve efficiencyEasy to optimizeDigital computer detailsMachine learningLearning basedData mining
A system and method for nexting is presented. The method comprises computing an expected event, observing a new event, when the expected event matches the new event, processing the new event and performing action in accordance with given concepts, when the expected event does not match the new event and the new event can be explained based on the given concepts, processing the new event and performing action in accordance with the given concepts, and when the expected event does not match the new event and the new event cannot be explained based on the given concepts, employing learning mechanism and performing action decided on by the learning mechanism. In one aspect, the method comprises generating new concepts using reasoning or learning. In one aspect, the method comprises converting sensed numerical data into events of interest via the application of learned functions operating on the numerical data.
Owner:TELCORDIA TECHNOLOGIES INC
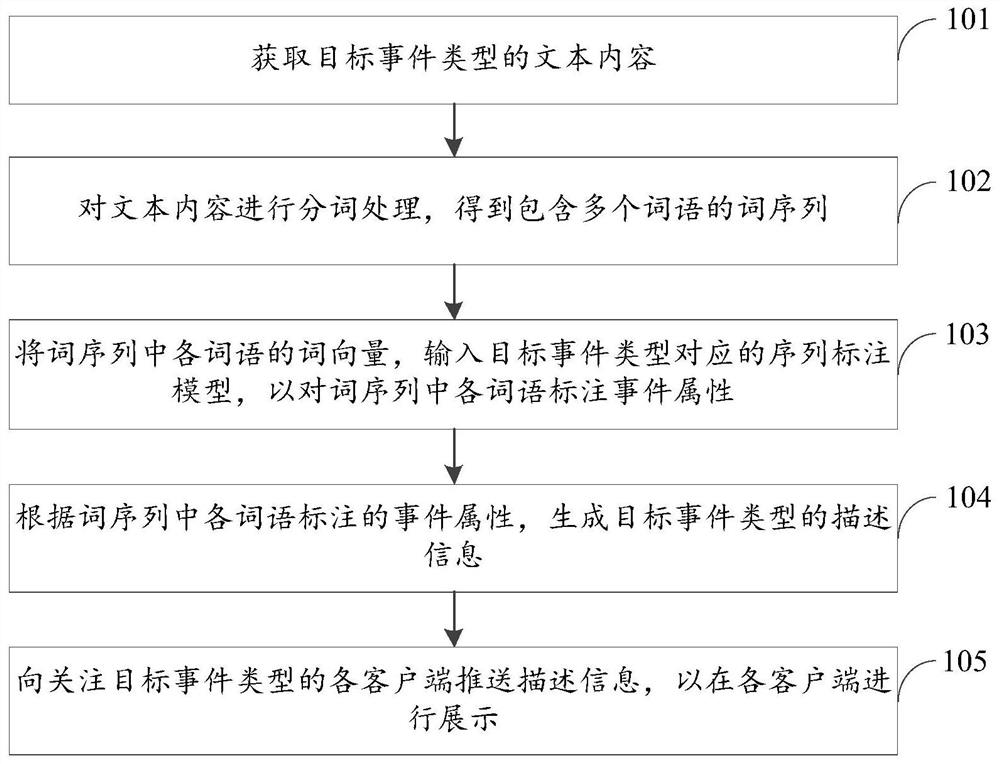
Text-based event pushing method and device, electronic equipment and storage medium
ActiveCN111966890AImprove efficiencyIncrease diversityFinanceSemantic analysisEvent typeTheoretical computer science
The invention discloses a text-based event pushing method and device, electronic equipment and a storage medium, and relates to the technical field of knowledge graphs, deep learning, natural languageprocessing and cloud computing. According to the specific implementation scheme, the method comprises the steps: obtaining text content of the target event type, performing word segmentation processing on the text content; obtaining a word sequence containing a plurality of words; inputting the word vectors of the words in the word sequence into a sequence labeling model corresponding to the target event type to mark event attributes for all words in the word sequence; according to the marked event attributes of the words in the word sequence, generating the description information of the target event type, pushing the description information to the clients paying attention to the target event type so as to be displayed on the clients. The description information of the target event typecan be automatically generated and displayed on the clients, and the efficiency and comprehensiveness of obtaining the related information of the concerned event by the user are improved.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Automated semantic modeling of system events
PendingUS20210182387A1Reduce settingsCharacter and pattern recognitionProbabilistic networksModelSimAnomalous behavior
A method to detect anomalous behavior in an execution environment. A set of system events captured from a monitored computing system are received. Using the received system events, a model is then trained using machine learning. The model is trained to automatically extract one or more features for the received set of system events, wherein a system event feature is determined by a semantic analysis and represents a semantic relationship between or among a grouping of system events that are observed to co-occur in an observation sample. An observation sample is associated with an operating scenario that has occurred in the execution environment. Once trained, and using the features, the model is used to detect anomalous behavior. As an optimization, prior to training, the set of system events are pre-processed into a reduced set of system events. The modeler may comprise a component of a malware detection system.
Owner:IBM CORP
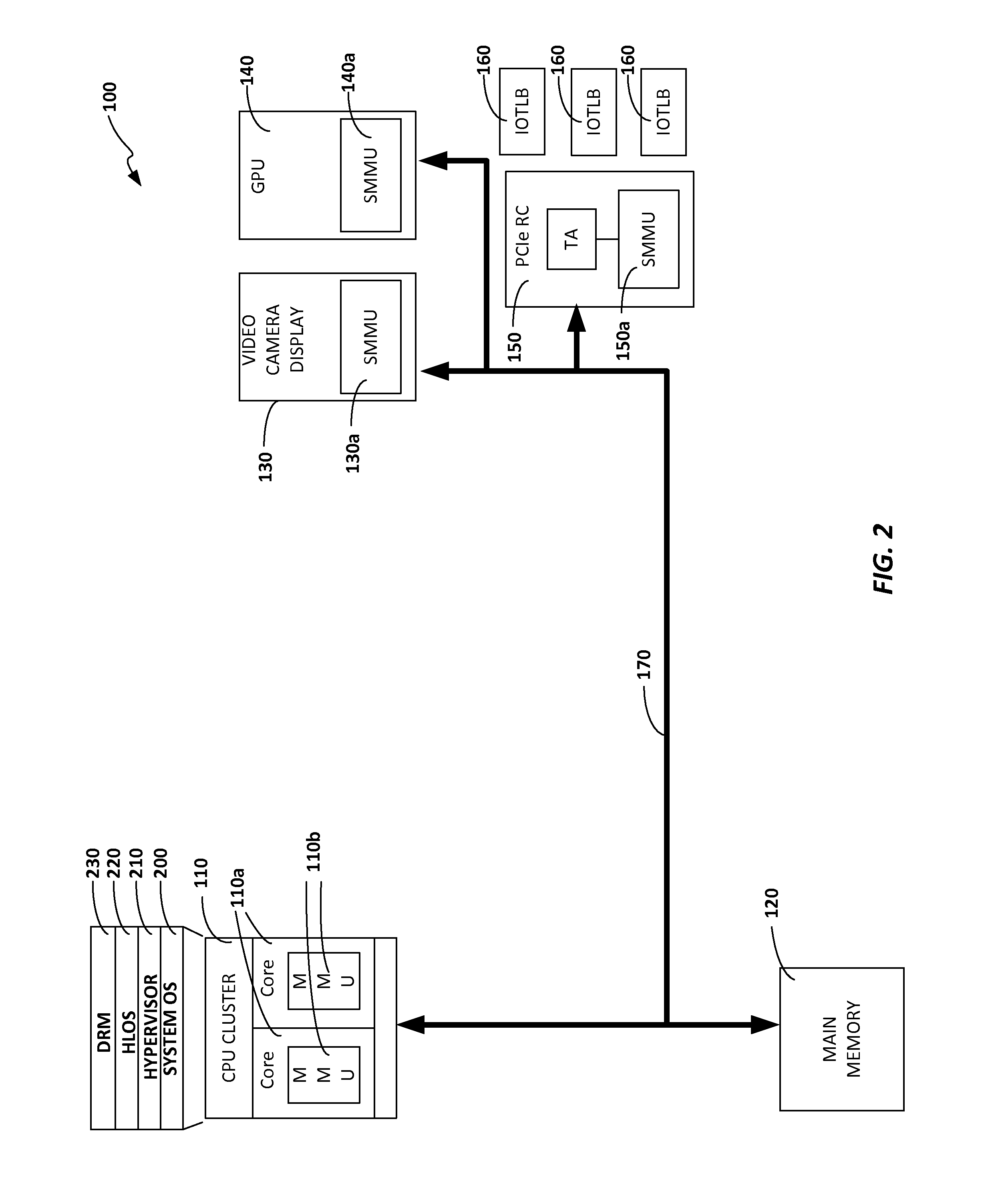
Methods and systems for reducing the amount of time and computing resources that are required to perform a hardware table walk (HWTW)
ActiveUS20140258586A1Reducing of computing resourceReducing amount of time and computing resourceMemory architecture accessing/allocationMemory adressing/allocation/relocationParallel computingEngineering
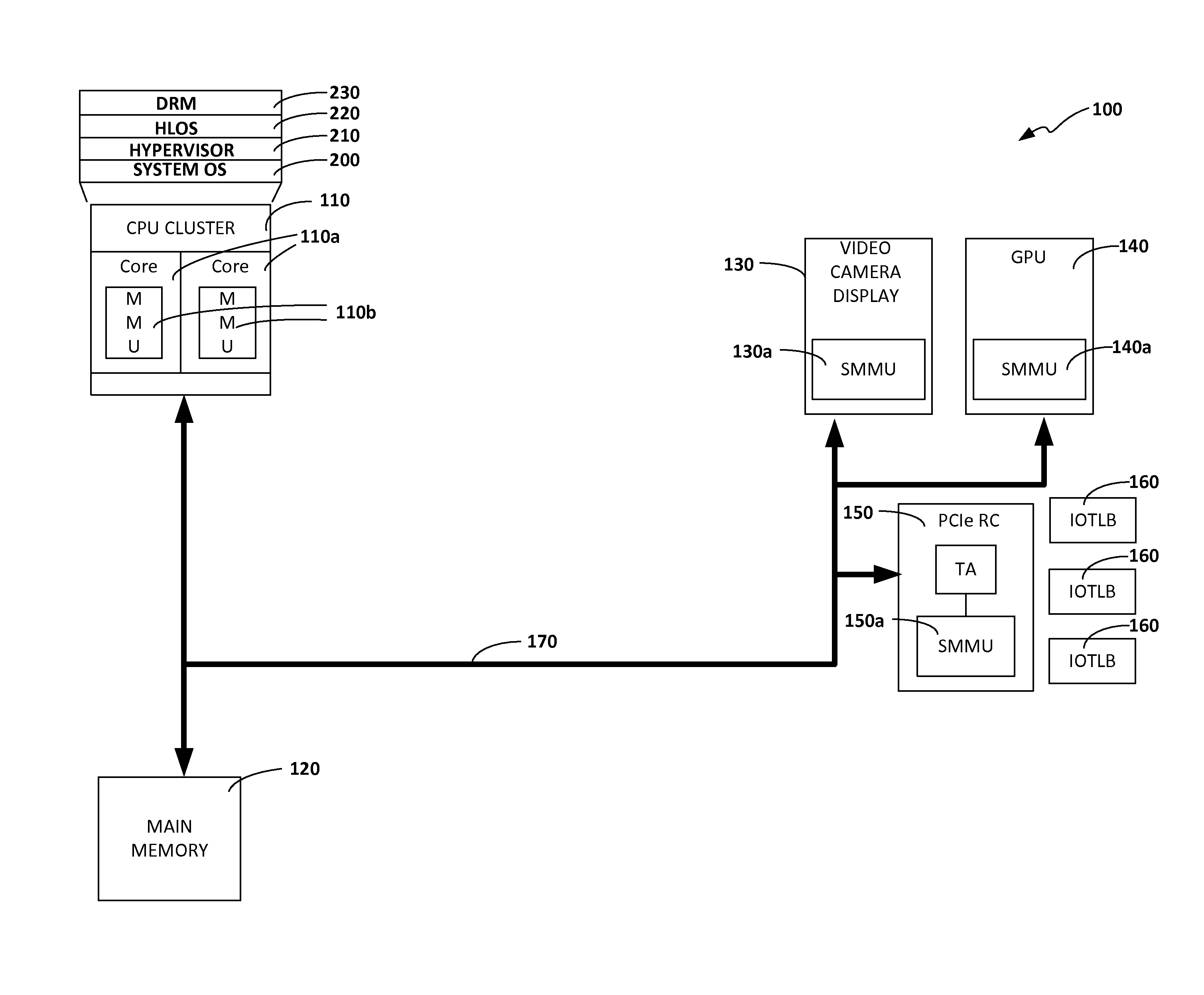
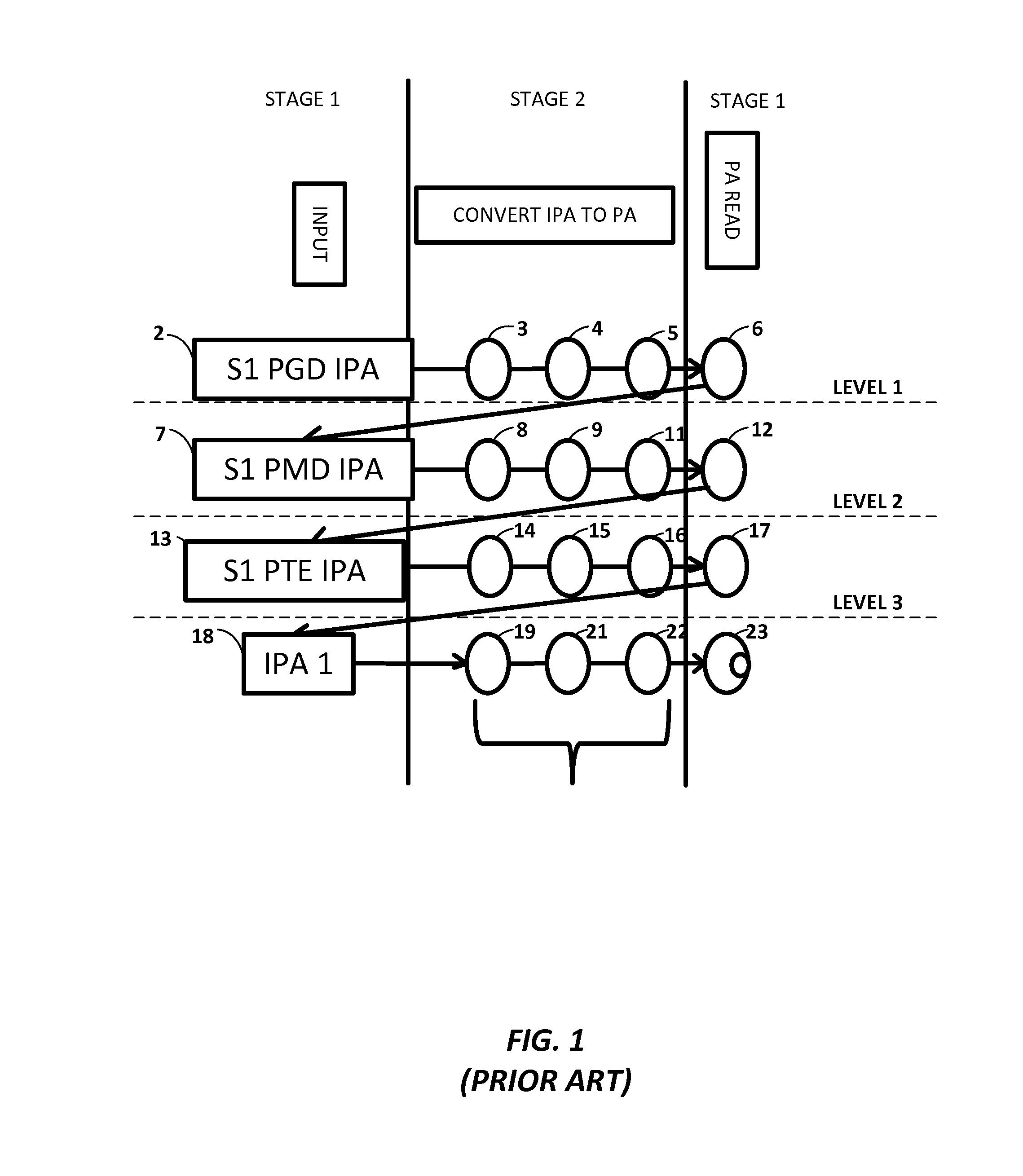
A computer system and a method are provided that reduce the amount of time and computing resources that are required to perform a hardware table walk (HWTW) in the event that a translation lookaside buffer (TLB) miss occurs. If a TLB miss occurs when performing a stage 2 (S2) HWTW to find the PA at which a stage 1 (S1) page table is stored, the MMU uses the IPA to predict the corresponding PA, thereby avoiding the need to perform any of the S2 table lookups. This greatly reduces the number of lookups that need to be performed when performing these types of HWTW read transactions, which greatly reduces processing overhead and performance penalties associated with performing these types of transactions.
Owner:QUALCOMM INC
Automated data organization
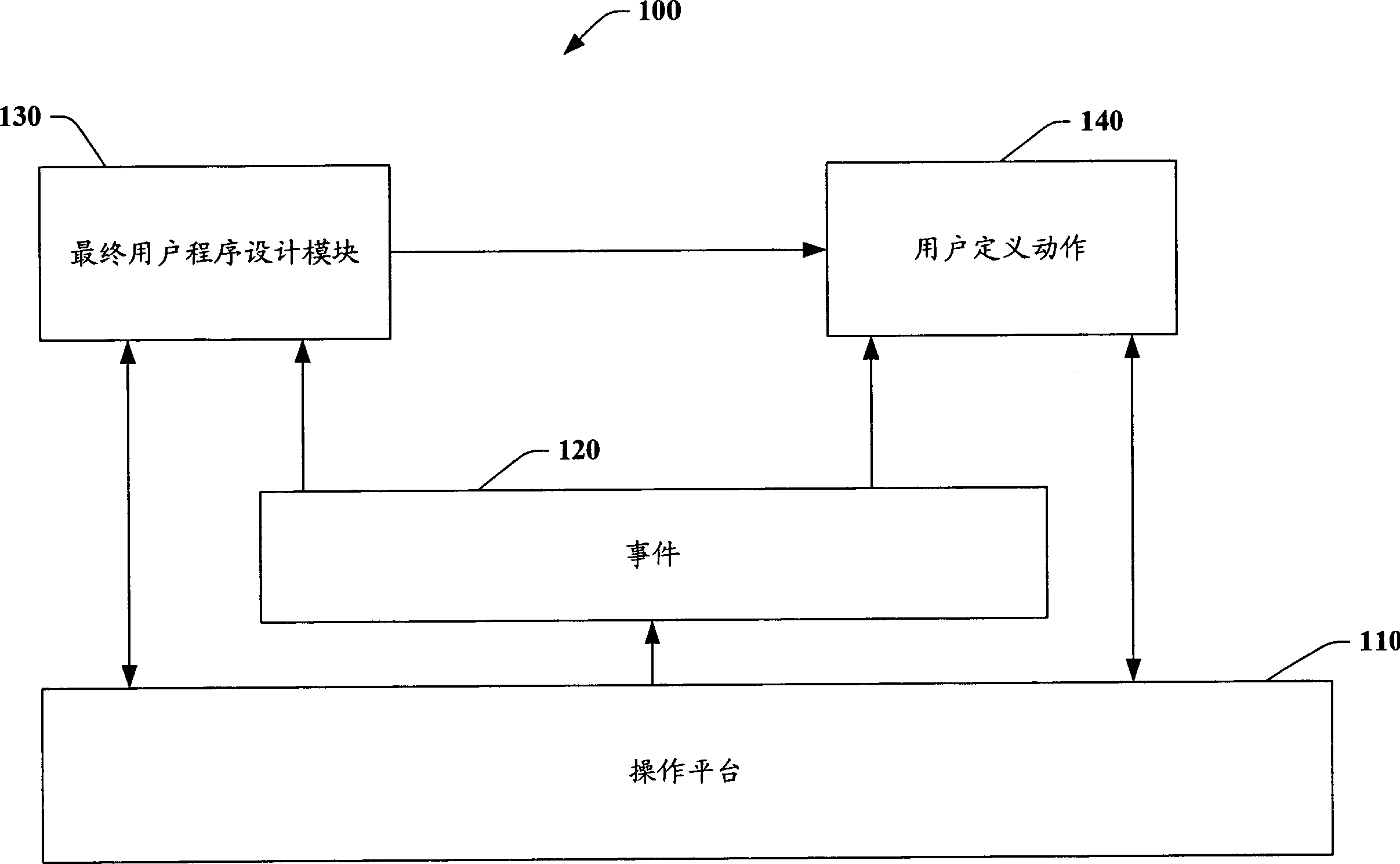
InactiveCN1828530AHelps usabilityProgram control using stored programsSpecific program execution arrangementsFile systemAutomated data processing
A system for automating data processing is presented. The system comprises an end-user programming module that is integrated with an underlying file system and that maps an event of a computing system to at least one automatic action that is defined by an end user. The system also includes an event handler that responds to events and causes the at least one automatic action to be performed. Methods of using the system are also provided.
Owner:MICROSOFT TECH LICENSING LLC
Methods and systems for inferring behavior and vulnerabilities from process models
ActiveUS20200396231A1Optimize resource allocationGood estimateMathematical modelsTransmissionAttackMonitoring system
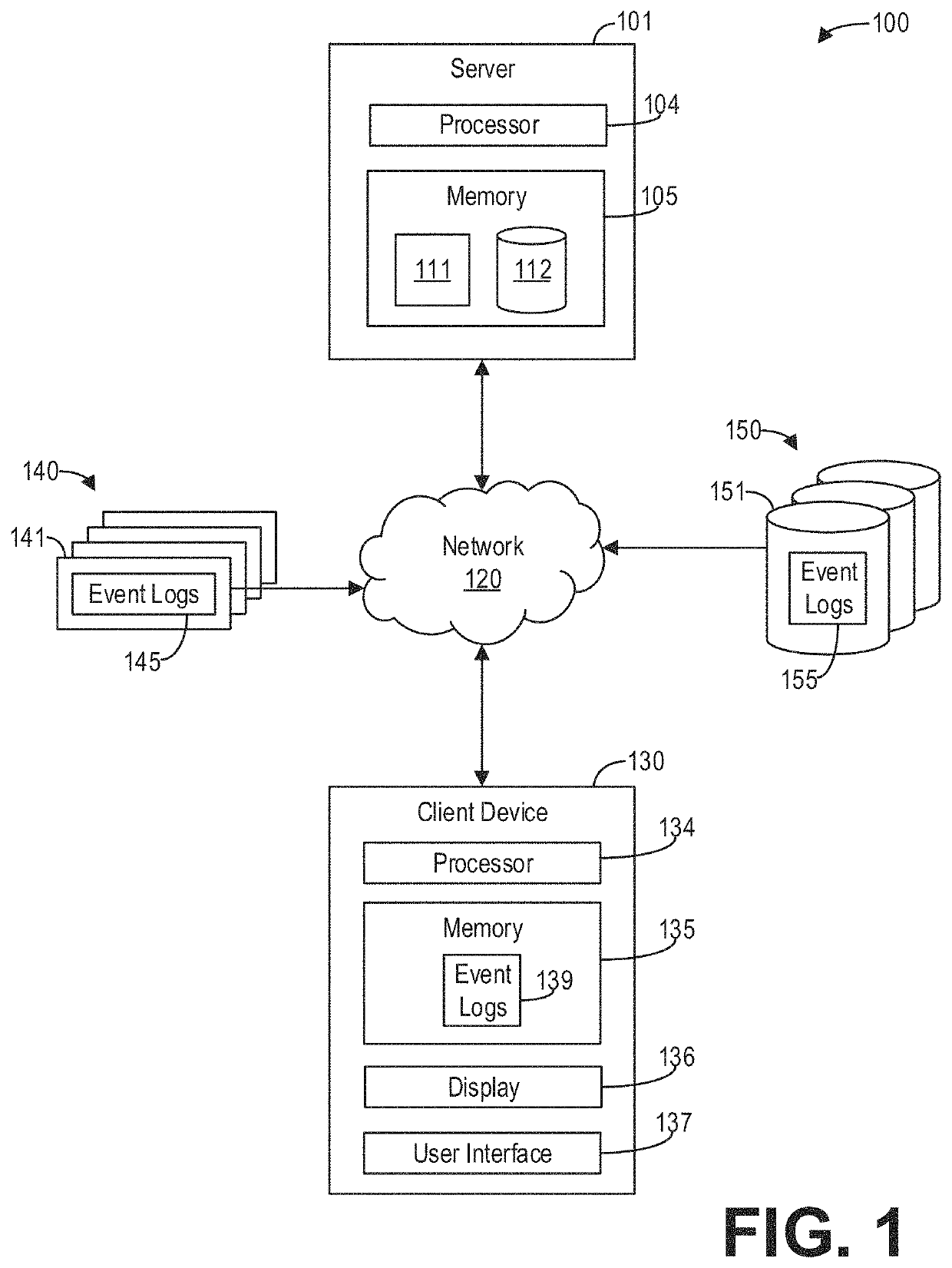
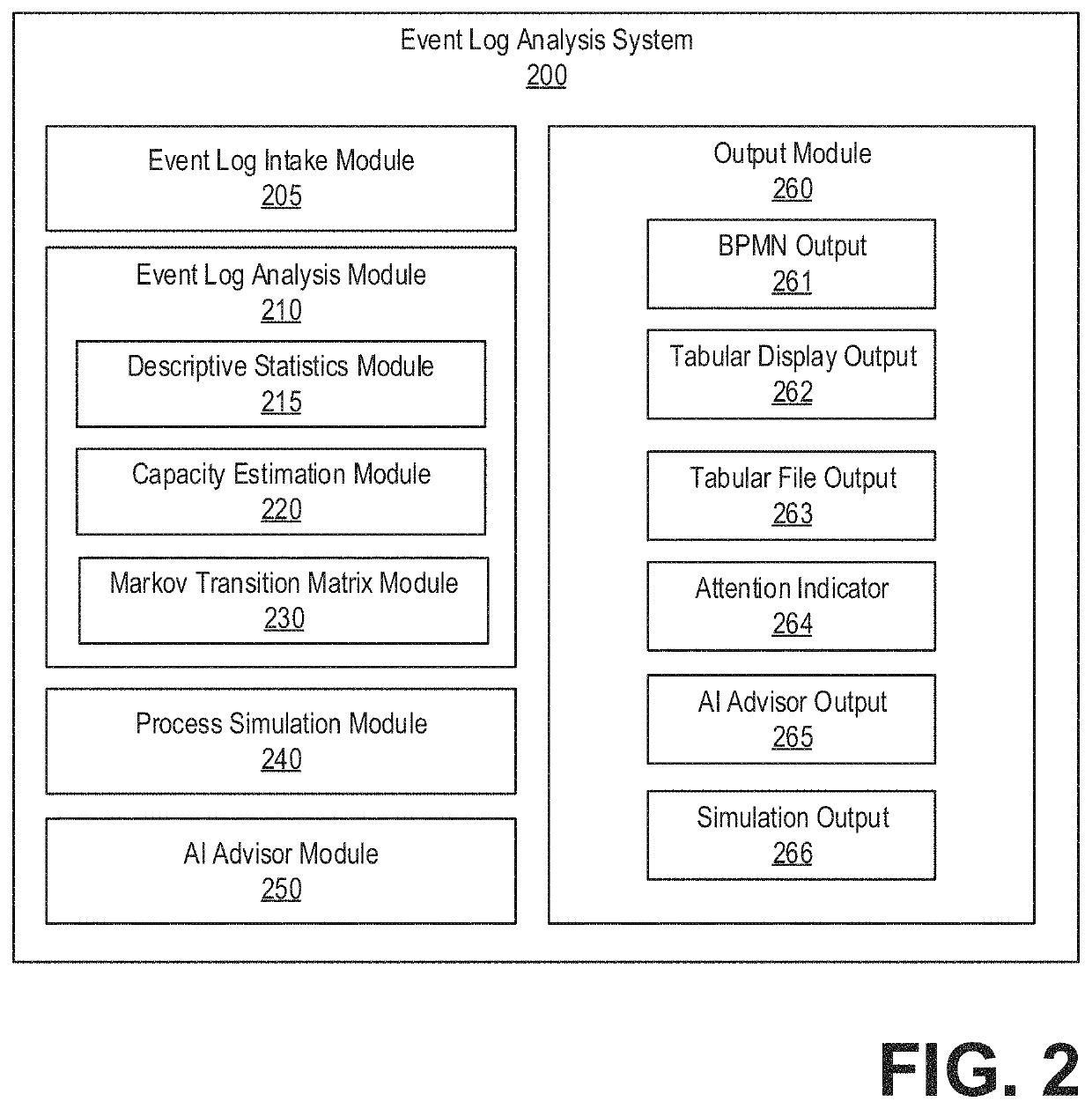
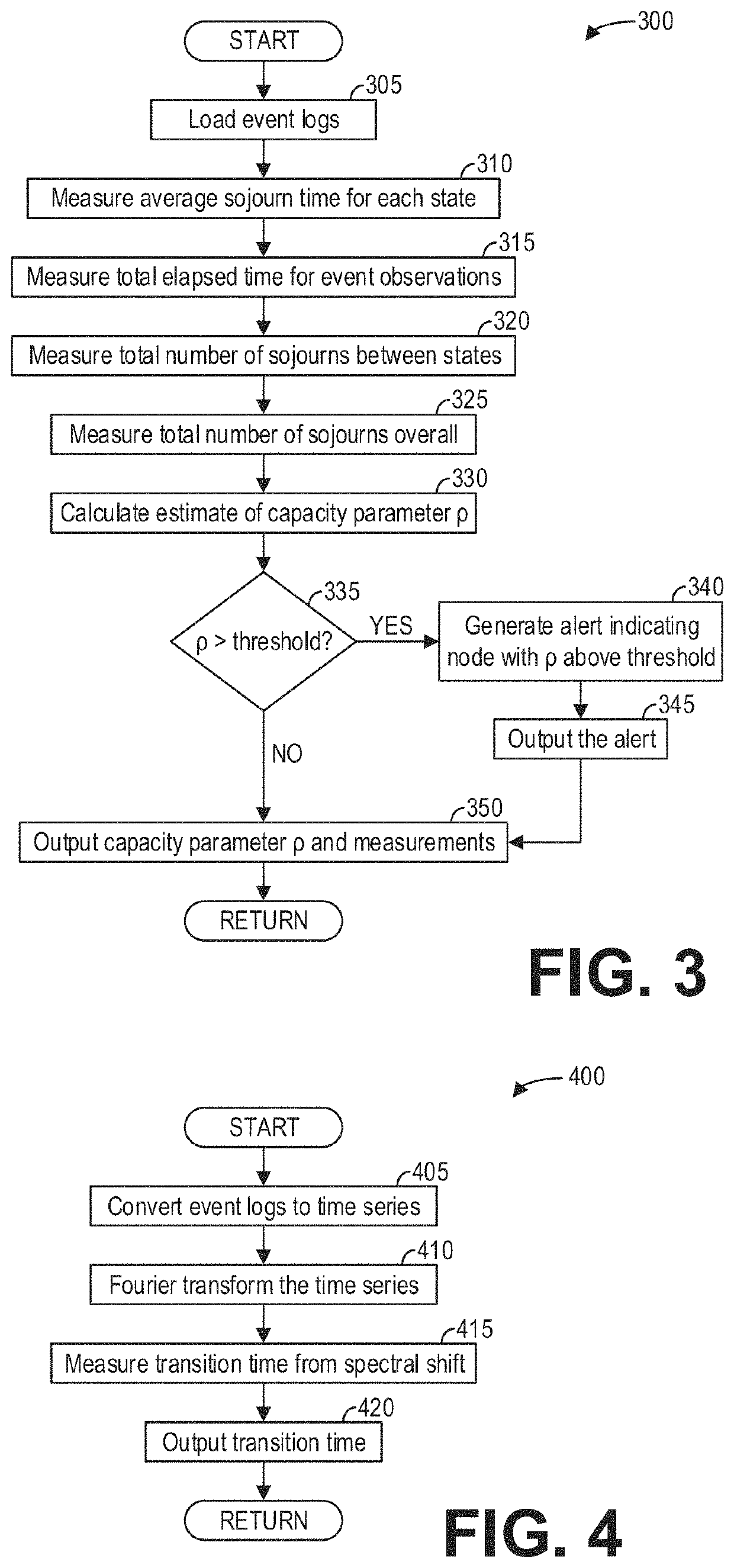
Systems and methods for process models to determine systems behavior and vulnerabilities are provided. In one embodiment, a method comprises collecting event logs from monitoring systems communicatively coupled to a computing device, each event log indicating an event occurring at a given time at a given activity within a process, measuring transition times between activities of the process from the event logs, calculating, from the measured transition times, a capacity of an activity of the activities, inferring behavior and vulnerabilities of the process based on one or more of the measured transition times and the capacity, and generating natural language output indicating the inferred behavior and vulnerabilities of the process. Further, simulations of the process are performed with statistical data regarding the event logs as input. In this way, aspects of a process such as an operational process in need of attention or vulnerable to external attacks may be rapidly identified and actions for resolution may be automatically recommended.
Owner:MORE COWBELL UNLIMITED INC
Efficient program deobfuscation through system API instrumentation
ActiveUS10565376B1Memory architecture accessing/allocationInput/output to record carriersSoftware engineeringProcess (computing)
Techniques for efficient program deobfuscation through system application program interface (API) instrumentation are disclosed. In some embodiments, a system / process / computer program product for efficient program deobfuscation through system API instrumentation includes monitoring changes in memory after a system call event during execution of a malware sample in a computing environment; and generating a signature based on an analysis of the monitored changes in memory after the system call event during execution of the malware sample in the computing environment.
Owner:PALO ALTO NETWORKS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com