Security method based on radio frequency identification (RFID)
An RFID tag and security technology, applied in the computer field, can solve the problems of security management dependence and poor timeliness, and achieve the effects of timely and reliable alarm and recorded evidence, low personnel dependence, and fast instant response speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The specific embodiments of a security method using RFID provided by the present invention will be described in detail below with reference to the accompanying drawings.
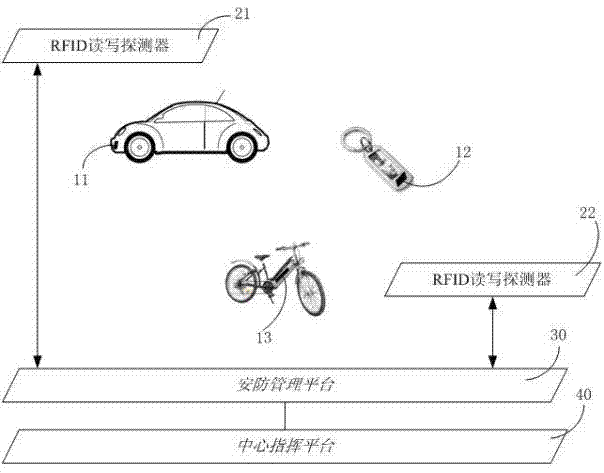
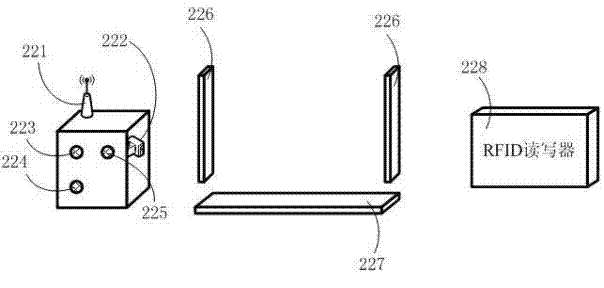
[0022] attached figure 1 Shown is a schematic structural diagram of the method according to the first embodiment of the present invention, including: a plurality of RFID tags, which are represented by tags 11 to 13 in this embodiment; a plurality of RFID read-write detectors, which are represented by detectors 21 to 22 in this embodiment Representation; security management platform 30 and central command platform 40.
[0023] The RFID tags 11-13 are placed on the monitored terminal of the security network on movable assets such as personnel or vehicles, including personnel, bicycles, electric bicycles, and automobiles. e.g. attached figure 1 Labels 11 to 13 given in are placed on key fobs, electric bicycles and cars, respectively. The label can be placed on the keychain, which is convenient for peo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com