Method for establishing peer-to-peer network storage data trust model
A peer-to-peer network, trust model technology, used in data exchange networks, digital transmission systems, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
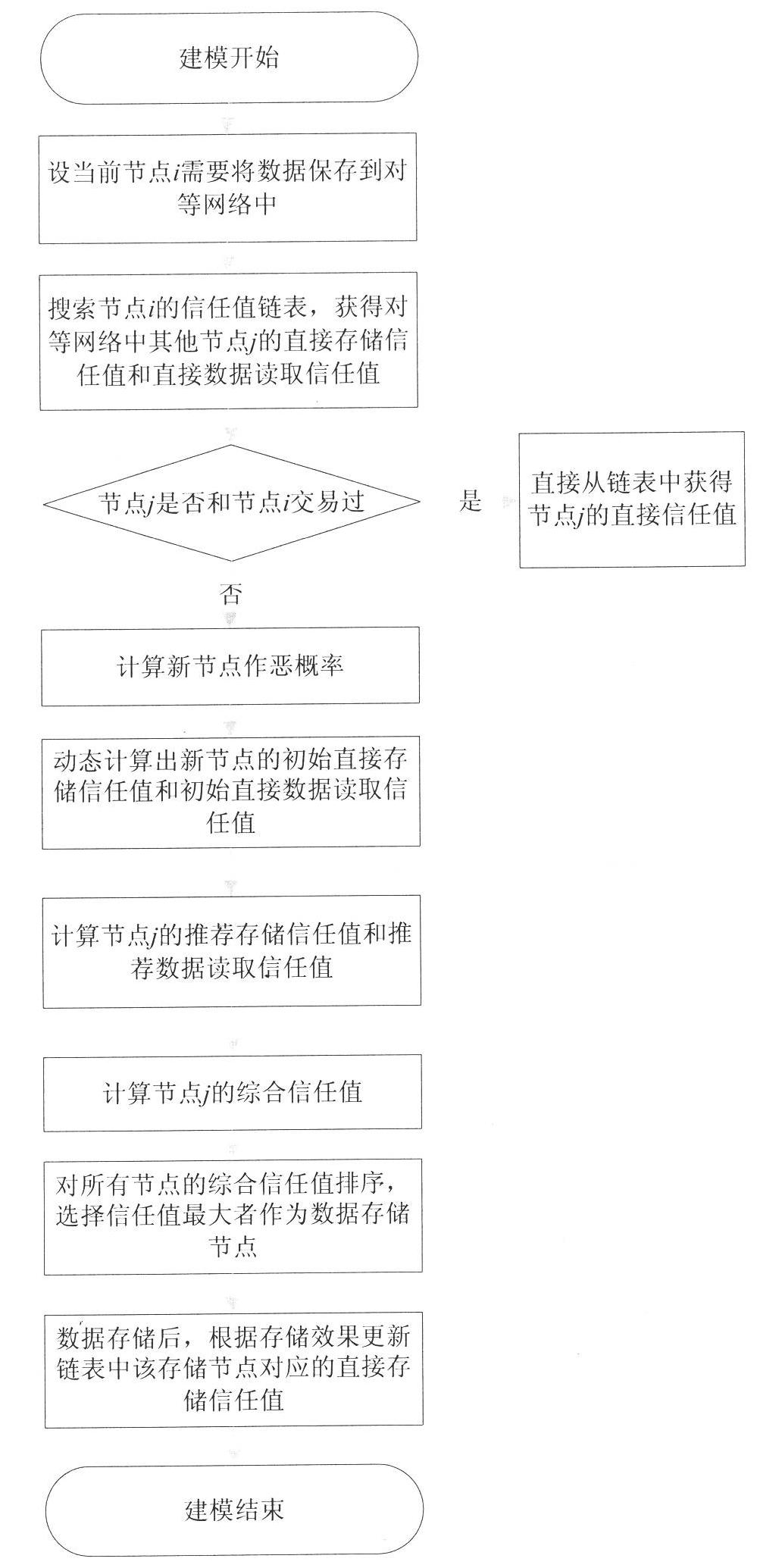
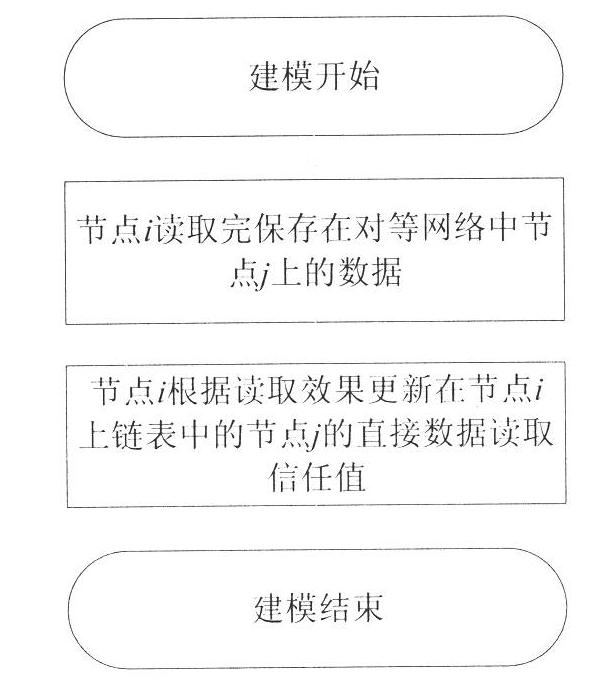
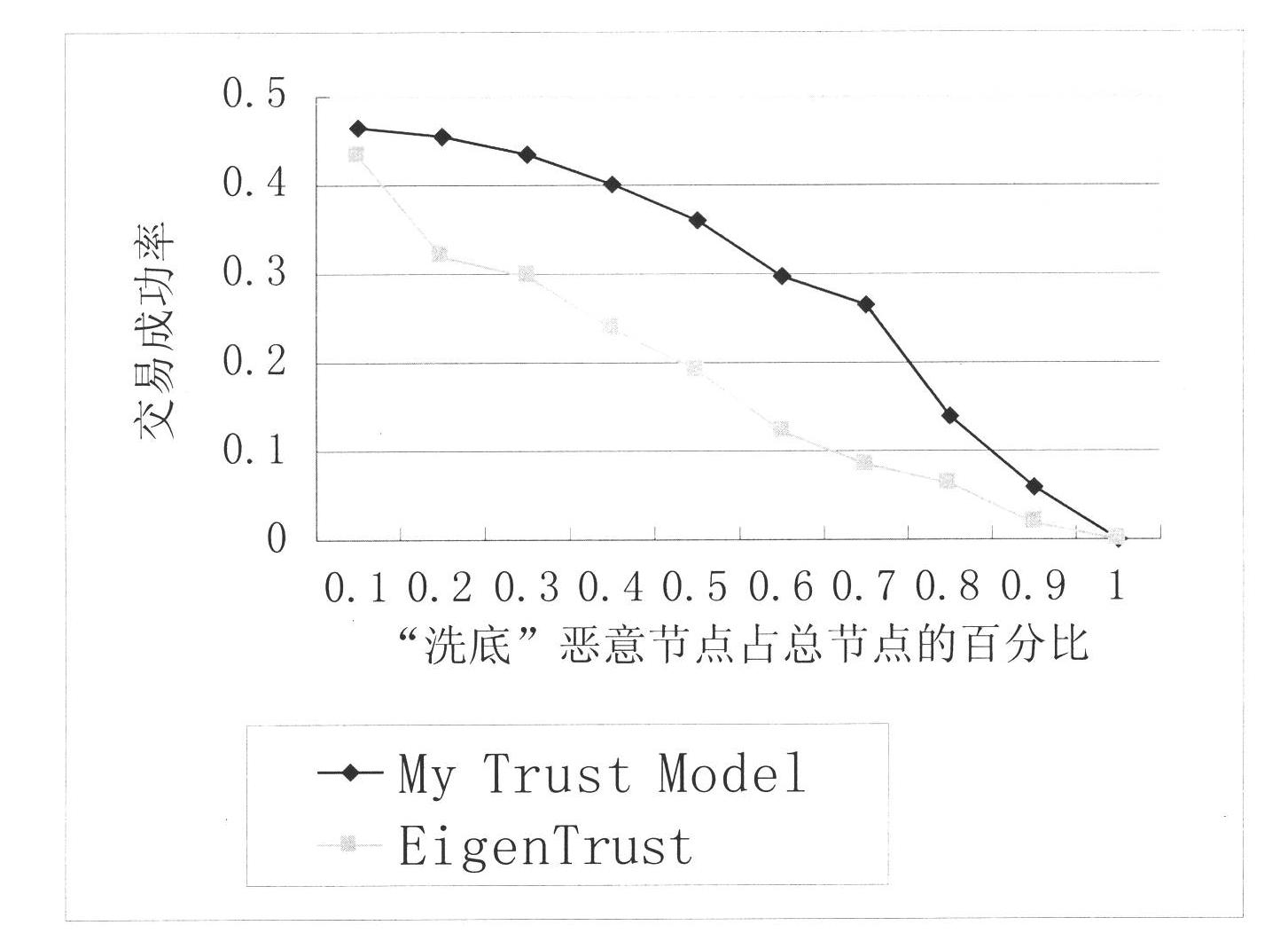
[0037] The present invention "a trust model establishment method for peer-to-peer network storage" proposes a brand-new trust model establishment method applied to peer-to-peer network storage, figure 1 and figure 2 The technical routes of the present invention in the data storage and data reading processes are respectively summarized. The technical solution will be further described below in conjunction with the accompanying drawings and examples.
[0038] In a peer-to-peer network, each peer node is assigned a globally unique identification number, and a storage space (such as a linked list) is allocated for storing information of other nodes except this node. The following example illustrates the process of establishing a trust model.
[0039] Assume that there are 5 nodes in the current peer-to-peer network, namely node 1, node 2, node 3, node 4, and node 5, and the time window is set to 10 minutes. Create a linked list with a length of 4 elements on each node, each el...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com