Network security emergency responding method
A network security and emergency response technology, applied in the network field, can solve problems such as errors, unsatisfactory linkage system effects, and difficulties in comprehensively analyzing network situations in balance and coordination, and achieve the effect of accurate strategies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
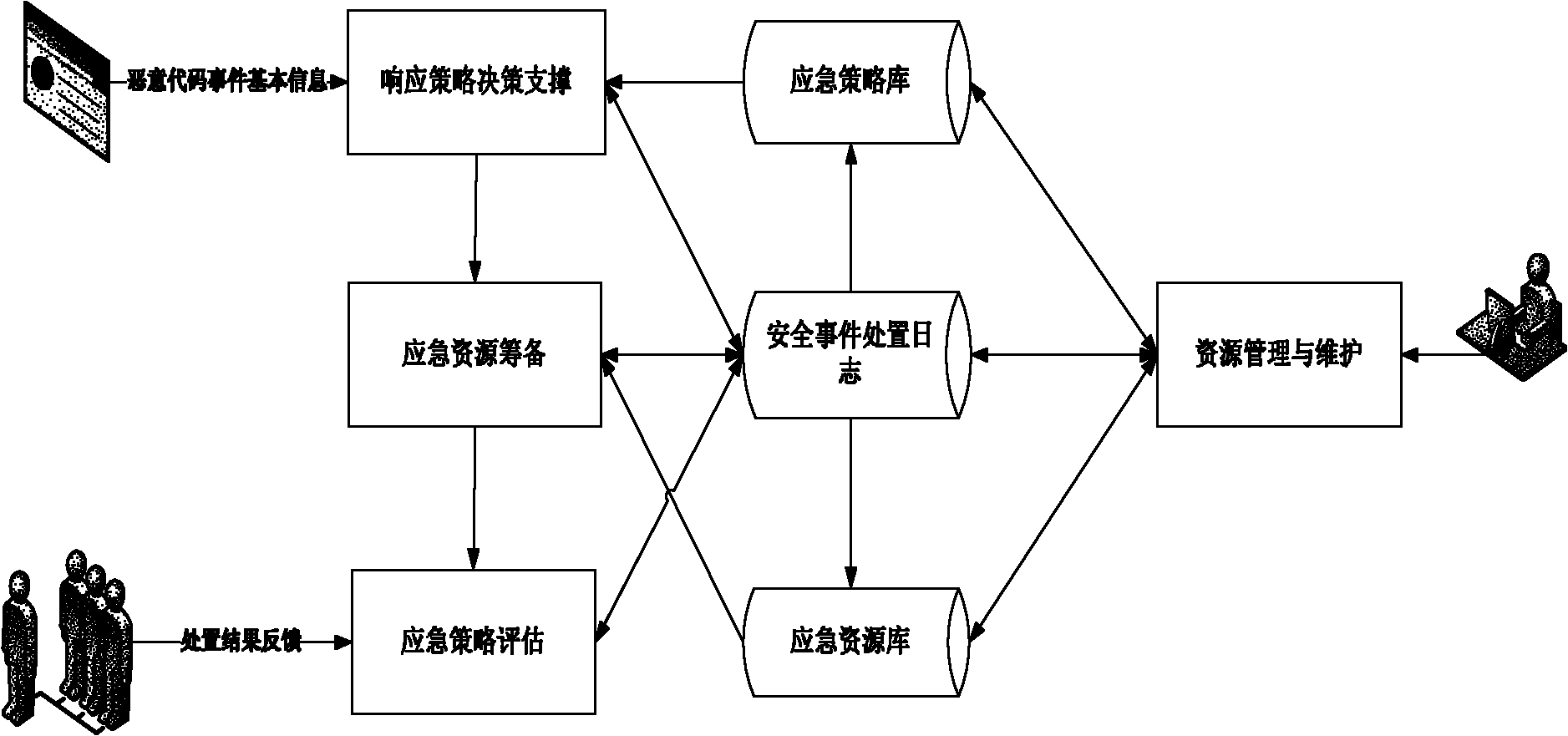
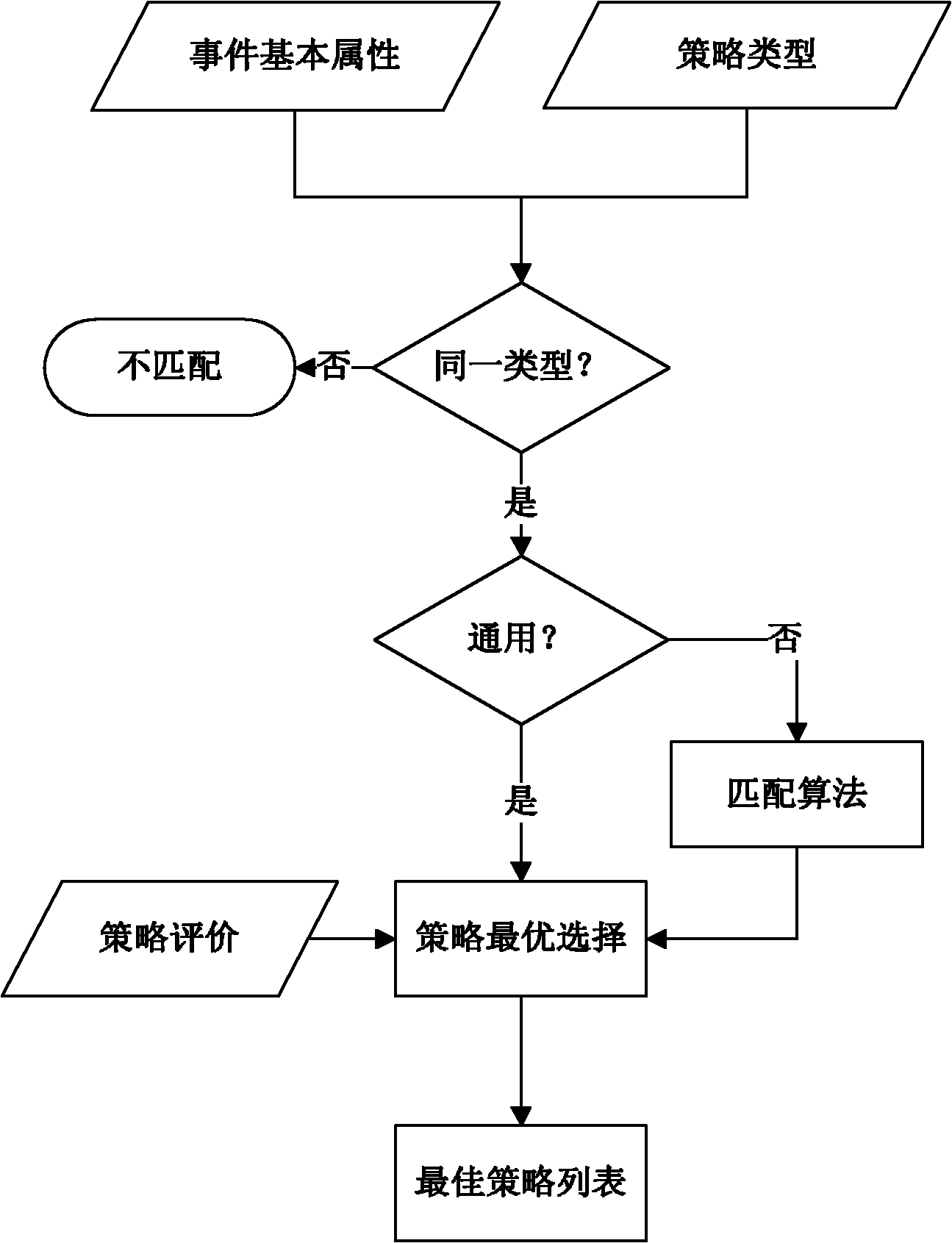
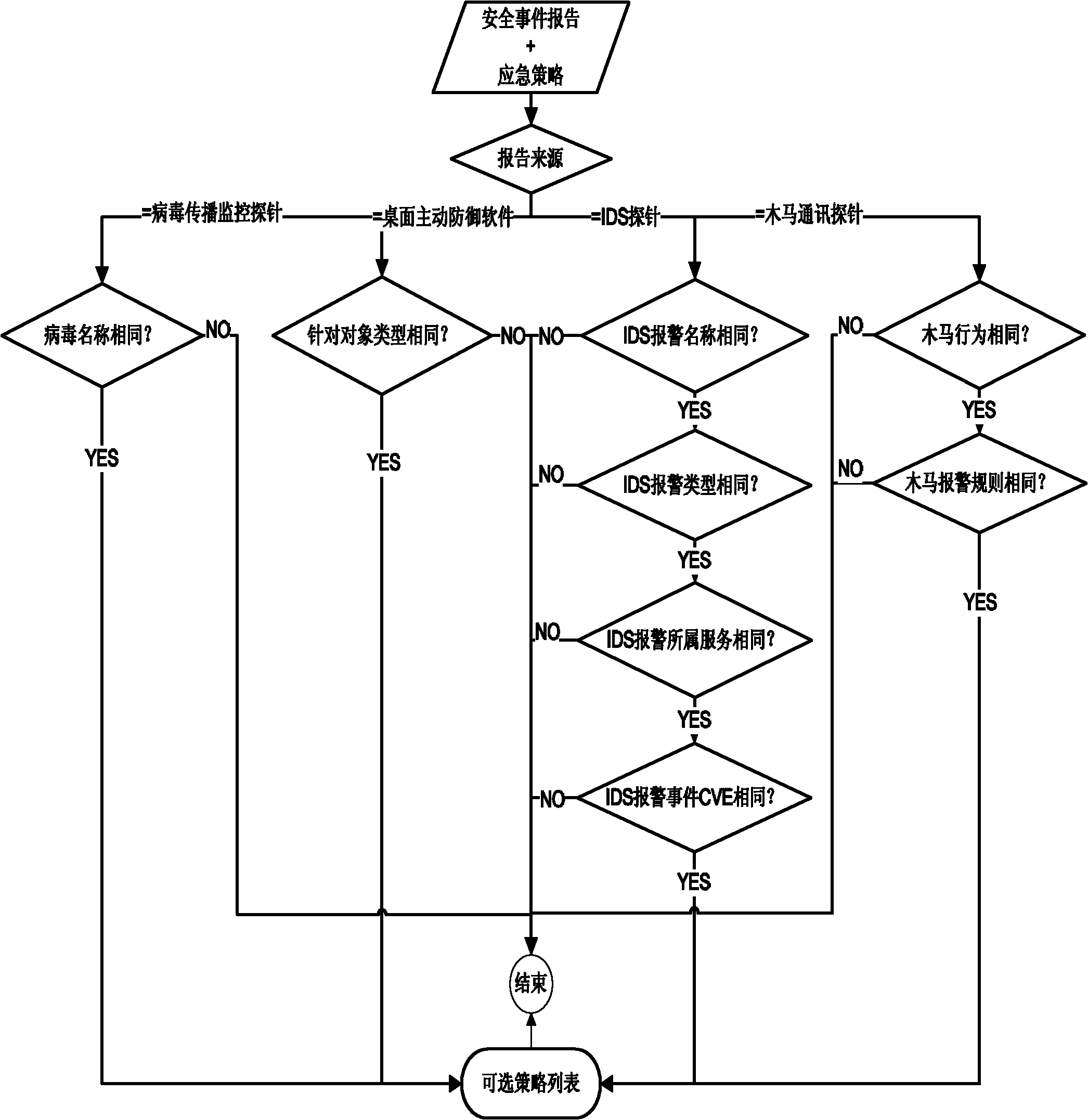
[0031] Such as figure 2 As shown, the specific implementation method of the emergency strategy recommendation process of the present invention is as follows:
[0032] 1) The basic attribute of the event is a set of attribute key-value pairs generated by the system after extracting the security event report of the network probe, which is an important basis for diagnosing the event. The specific properties vary according to different network probes, as shown in the following table:
[0033] Table 1 Basic attributes of Trojan horse communication monitoring probe alarm events
[0034]
[0035] Table 2 Basic properties of alarm events of virus spread monitoring probes
[0036] serial number
Attributes
attribute description
1
time
security incident time
2
devId
The device ip of the source probe
3
srcMac
Source Mac address
4
dstMac
Destination Mac address
5
srcIp
source ip add...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com