Block encryption apparatus, block encryption method and program
A block encryption and encryption key technology, which is applied in the field of block encryption devices, can solve problems such as insecurity, and achieve the effect of sufficient distance reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
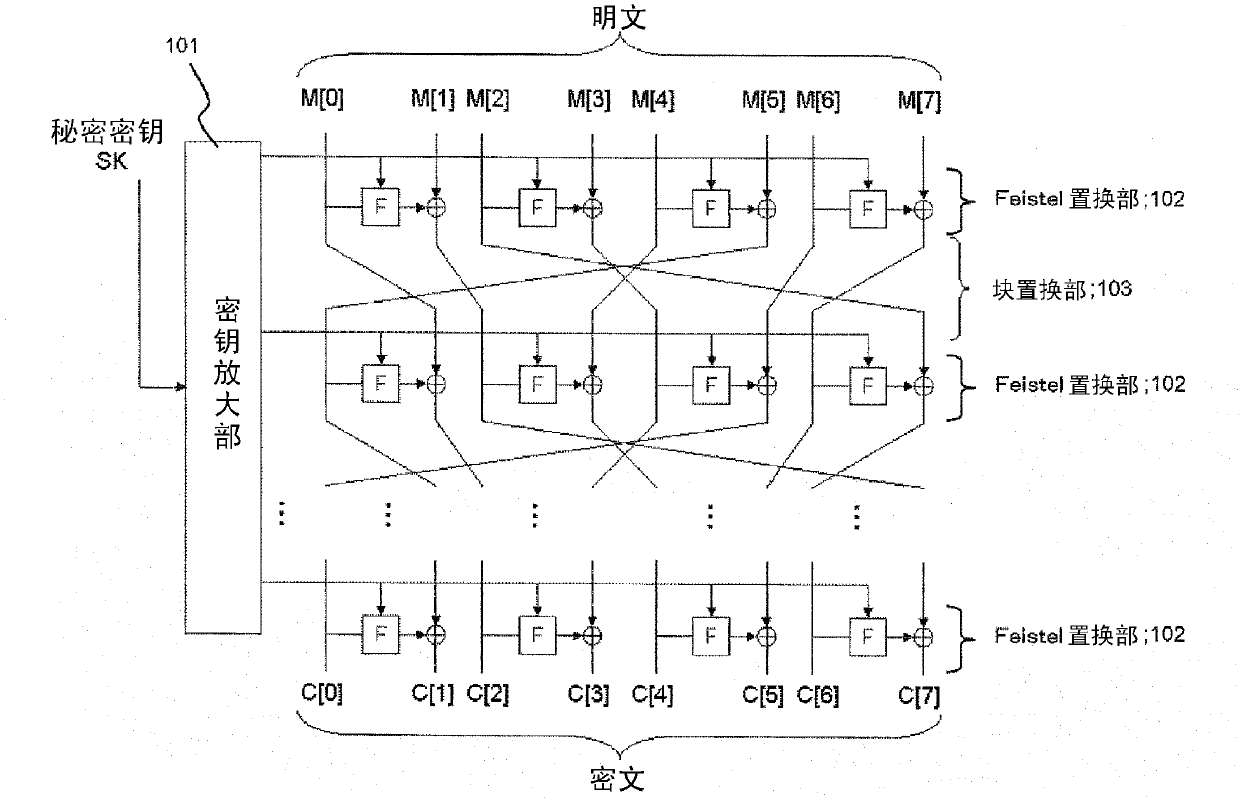
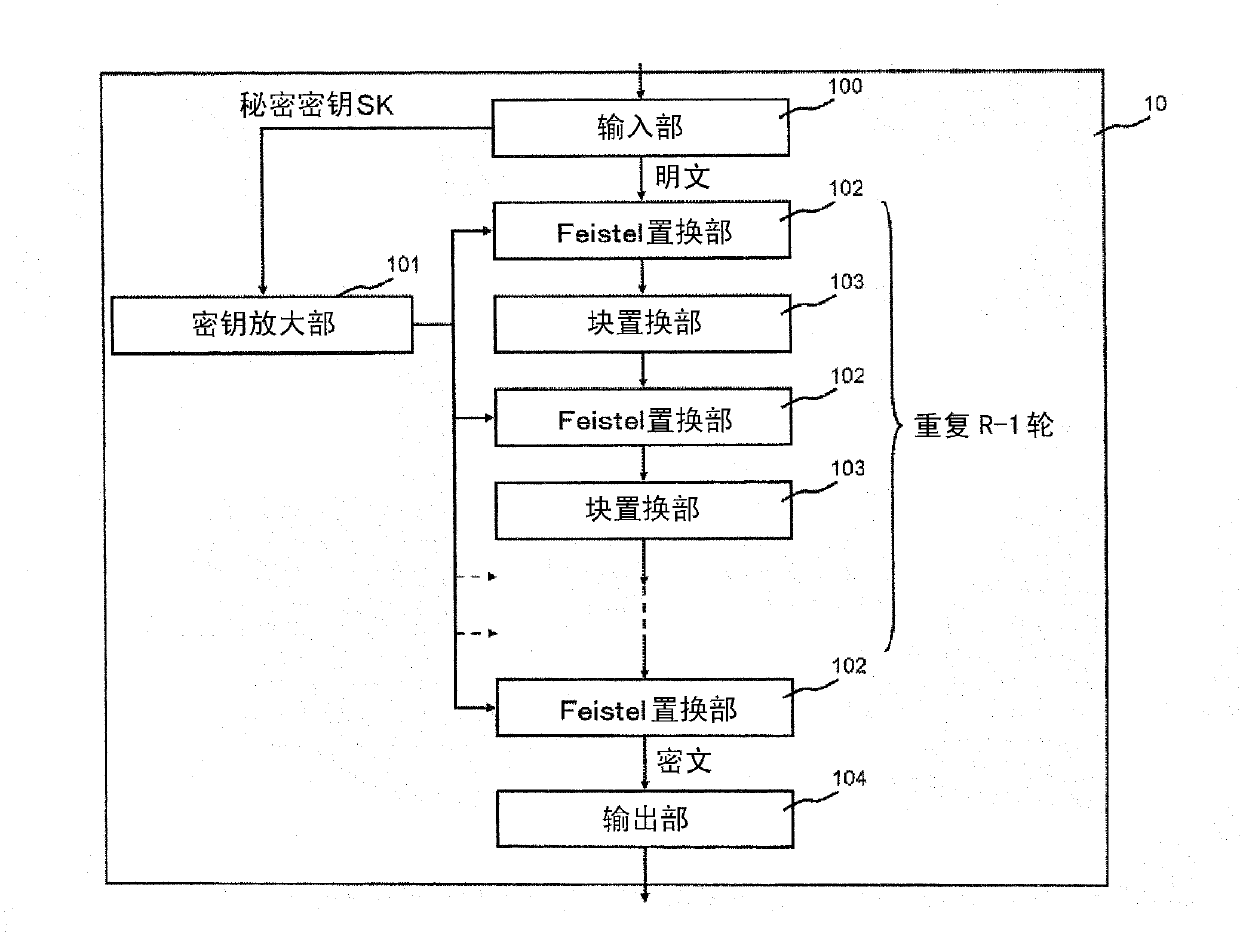
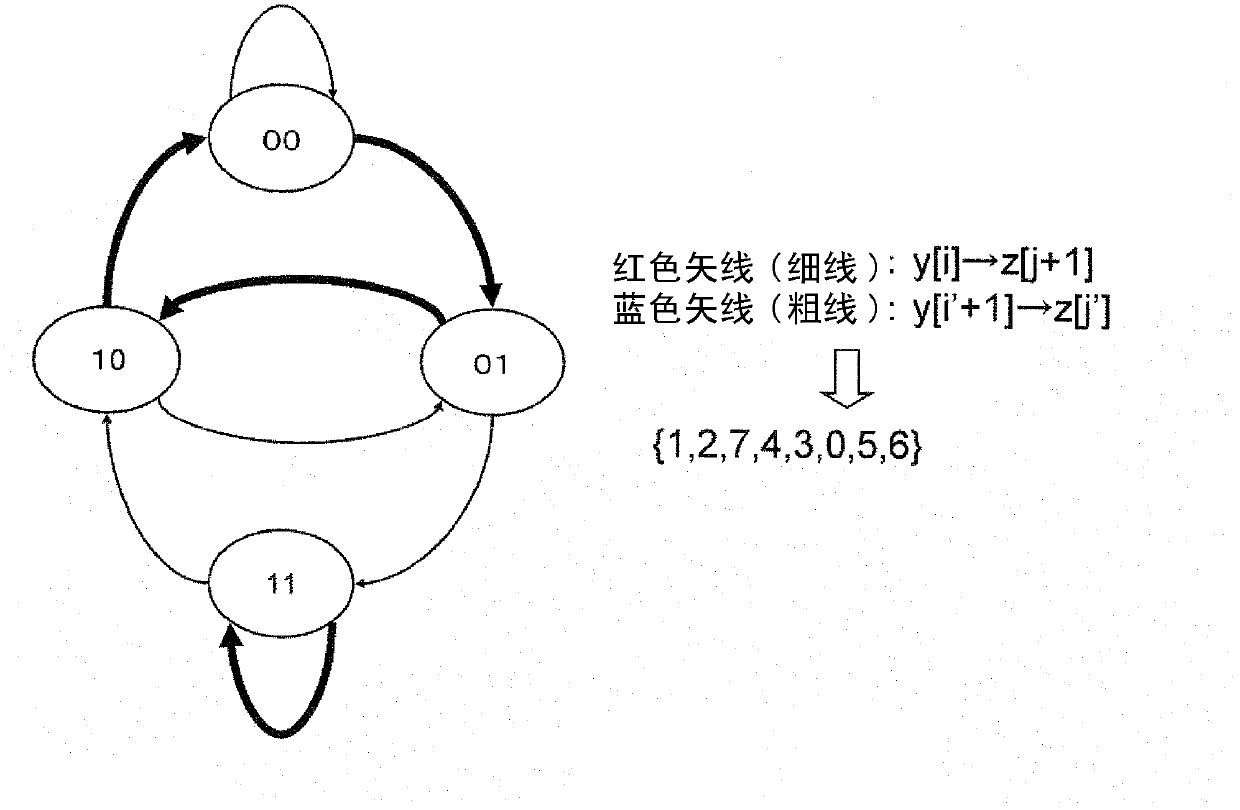
[0074] Next, a first embodiment of the present invention will be described in detail with reference to the drawings. figure 1 [Struc1] is a diagram showing the configuration of the first embodiment of the present invention. figure 2 [Block1] is a diagram showing the configuration of the first embodiment of the present invention using processing blocks.
[0075] refer to figure 2 , represents the block encryption device 10 including the following units: an input unit 100 , a key amplification unit 101 , a Feistel replacement unit 102 for R rounds, a block replacement unit 103 for R−1 rounds, and an output unit 104 .
[0076] The block encryption device 10 can be realized by various information processing devices including a CPU, a memory, a magnetic disk, and the like. In addition, each of the above-described units of the block encryption device 10 can be realized by storing a program in a disk in advance and operating the program on the CPU.
[0077] Next, each of the ab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com