Fine-grained semantic detection method of harmful text contents in network
A detection method and fine-grained technology, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve problems such as difficult construction, low detection performance, and low performance in text content detection, so as to improve practicability, The effect of reducing the false alarm rate and improving the detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
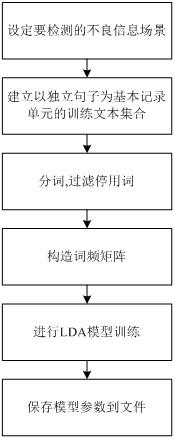
[0035] 1. The establishment of the semantic topic model of the scene.
[0036] (1) Set the bad information scene to be detected, select sentences related to the scene, and construct a text set describing the scene.
[0037] The text information related to the scene can be sourced from the Internet and extracted through manual reading to construct a text set. The text set consists of a text file where each line is a separate sentence. The sentences chosen should describe as many aspects of the scene as possible.
[0038] (2) Preprocessing of text sets
[0039] Segment each sentence in the text set, and remove some common stop words, so as to obtain a vocabulary T corresponding to the text set. Each row of the vocabulary is a word, and there are no repeated words in the vocabulary.
[0040] (3) Construct word frequency matrix
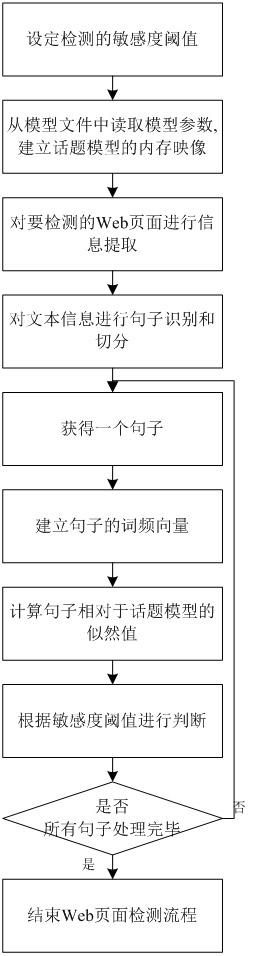
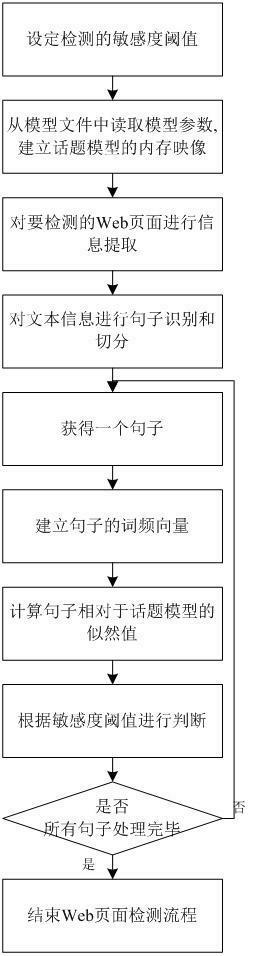
[0041] For each sentence in the text set S , constructing a row vector v i ={ c i1 , c i2 , c i3 , …, c iX}, i =1,2,…, Y , here X Indic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com