Method and device for detecting black chain
A black chain, waiting to be detected technology, applied in the field of black chain detection, can solve problems such as difficulty in timely and effective detection, waste of human resources, and inability to realize automatic detection of black chains
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
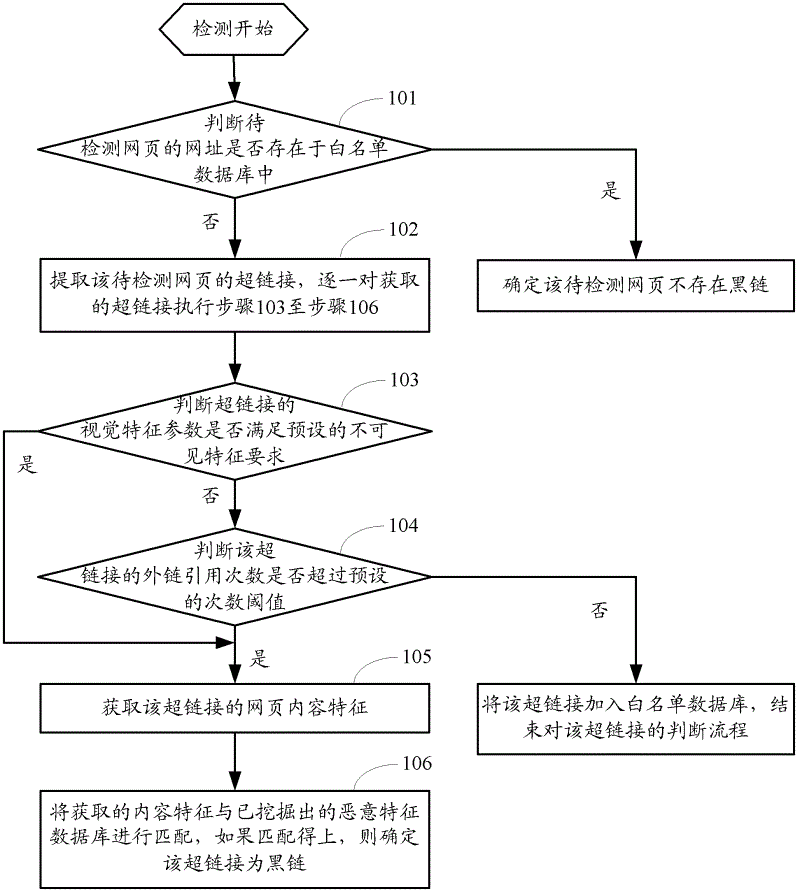
[0053] figure 1The flow chart of the method for detecting black links provided by Embodiment 1 of the present invention, such as figure 1 As shown, the method may include the following steps:
[0054] Step 101: Match the URL of the webpage to be detected with the existing whitelist database, if the webpage to be detected exists in the whitelist database, determine that there is no black link in the webpage to be detected, and end the process; otherwise, execute step 102.
[0055] When performing black chain detection, you can first call the whitelist database for detection. In the embodiment of the present invention, the urls of the confirmed webpages that are not linked to black links can be stored in the whitelist database in advance, and the whitelist database can be a dynamically updated database, which can be added manually or in In step 104 of this embodiment, when it is determined that a hyperlink is safe, the hyperlink is added to the whitelist database.
[0056] Th...
Embodiment 2
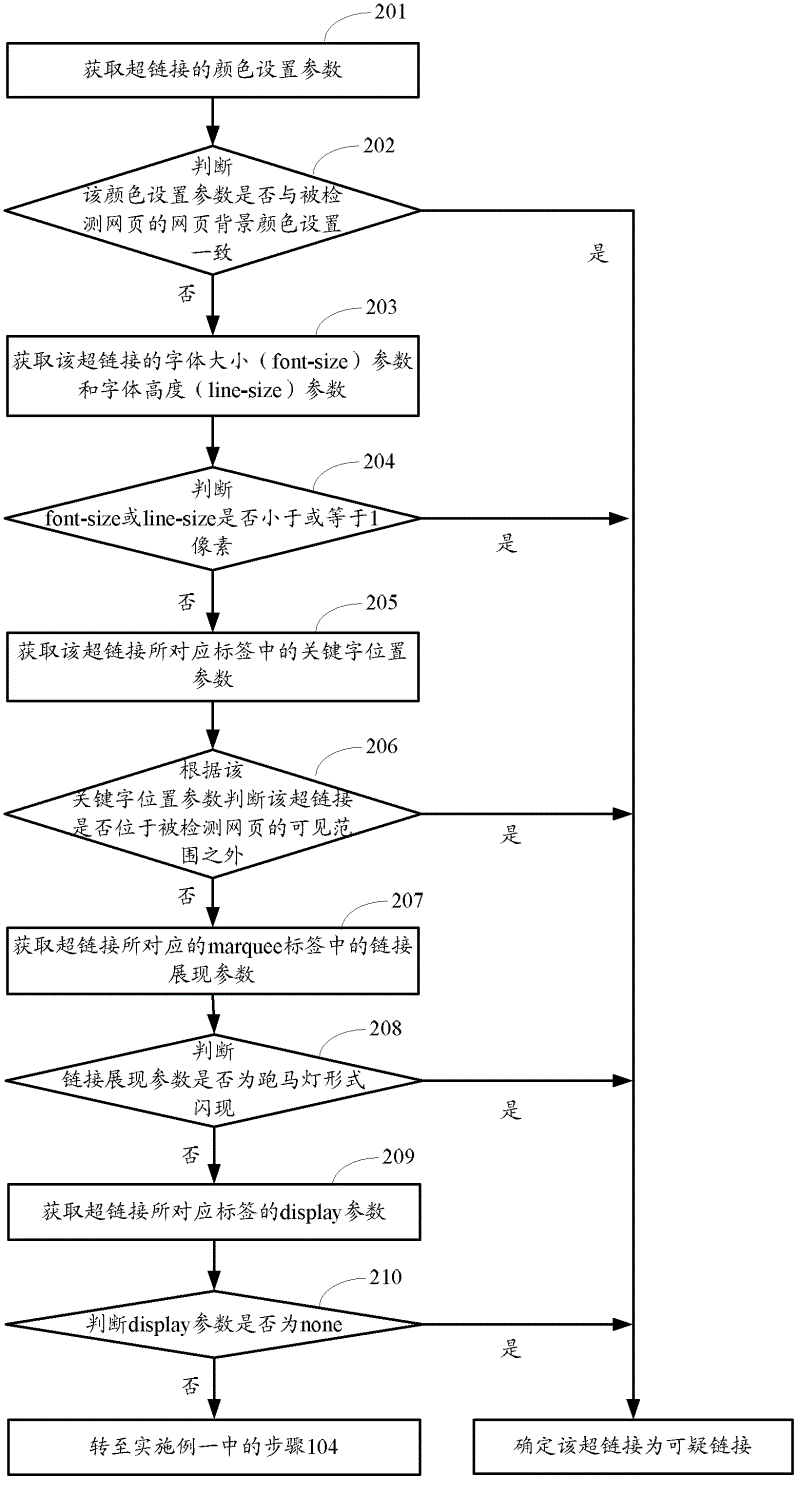
[0078] figure 2 The flow chart for detecting the visual feature parameters of hyperlinks provided by Embodiment 2 of the present invention, such as figure 2 As shown, the process may specifically include the following steps:
[0079] Step 201: Obtain color setting parameters of hyperlinks.
[0080] Step 202: Determine whether the color setting parameter is consistent with the webpage background color setting of the detected webpage, if yes, determine that the hyperlink is a suspicious link; otherwise, execute step 203.
[0081] If the color setting of the hyperlink is consistent with the background color setting of the webpage it is linked to, in this case, the hyperlink is not easy to be detected, and it is likely to be a black link. The implementation code of this black chain is:
[0082] Keywords
[0083] Step 203: Obtain the font size (font-size) parameter and font height (line-size) parameter of the hyperlink.
[0084] This step is to obtain the font parameters of ...
Embodiment 3
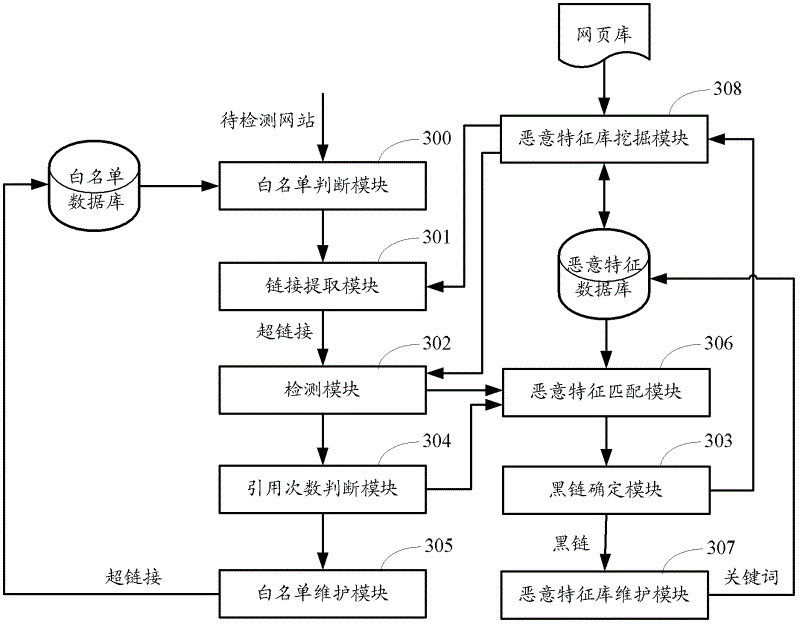
[0134] In this embodiment, the mining process of the malicious feature database is mainly described. First, the mining source of the malicious database is explained. There are mainly two sources here:
[0135] The first source: other hyperlinks in web pages containing black links. If it is determined that a certain link is a black link, it means that there is a loophole in the web page where the link is linked, and other black links are likely to be linked. Therefore, the web page containing the link in the malicious feature database can be obtained from the web page library. , the other hyperlinks in the webpage are executed one by one in the method of detecting black links described in step 103 to step 106 in the first embodiment of the present invention to detect whether other hyperlinks are black links. Of course, as described in Embodiment 1, only the method of step 103 may be used to detect black links, or steps 103 to 104 may be used to detect black links. If it is det...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com