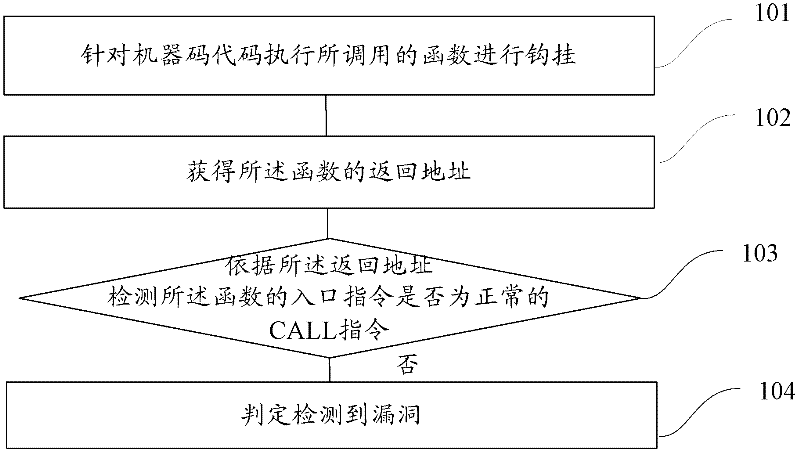
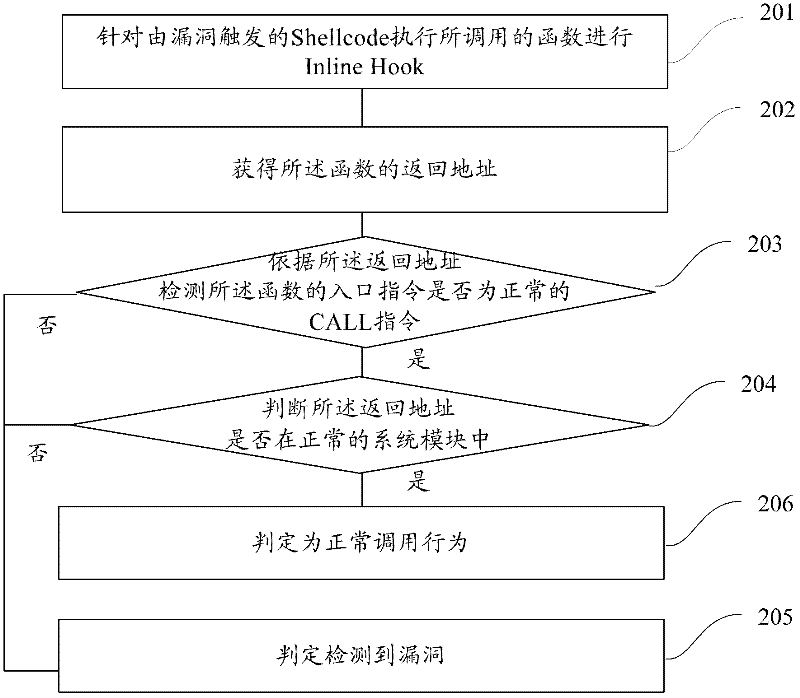
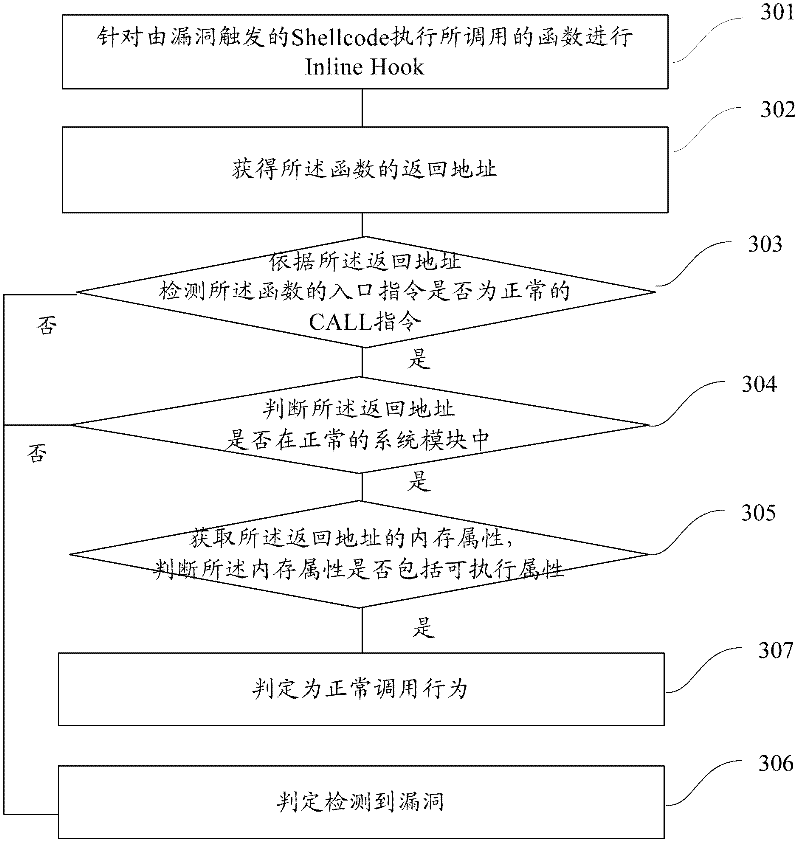
Method and system for detecting vulnerability
A vulnerability detection and vulnerability technology, which is applied in the field of information security, can solve problems such as the inability to identify web page Trojan horses, the loss of web page functions and effects, etc., and achieve the effects of improving user experience, improving security, and effectively identifying
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] In order to make the above objects, features and advantages of the present application more obvious and comprehensible, the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
[0072] Active defense against security vulnerabilities is one of the main ways to cut off the spread of Trojan viruses and infect computer terminals. Active defense against security vulnerabilities can greatly enhance the security features of the terminal system and make it more difficult for hackers to attack. For example, when a vulnerability on the Windows platform executes an overflow attack, the Shellcode of the overflow vulnerability is prevented from being intercepted by the active defense technology of the security software during execution, and the attack will completely fail.
[0073] Among them, Shellcode is actually a piece of code (it can also be filled data), which is used to send to the ser...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com