Cipherkey setting method of heterogeneous wireless sensor network
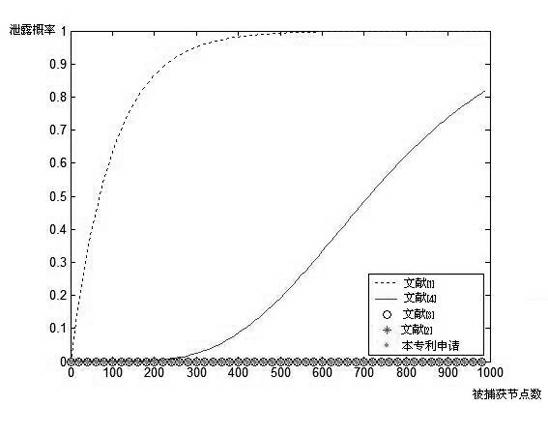
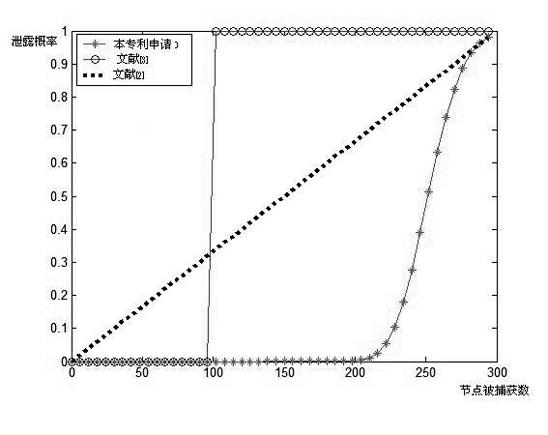
A wireless sensor, common sensor technology, applied in network topology, wireless communication, security devices, etc., can solve the problems of inability to implement security algorithms, limited storage space, limited transmission range, etc., to achieve 100% anti-capture attack capability, reduce storage Consumption, the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] Now in conjunction with accompanying drawing and embodiment the present invention is described in further detail: the present invention is realized in this way,
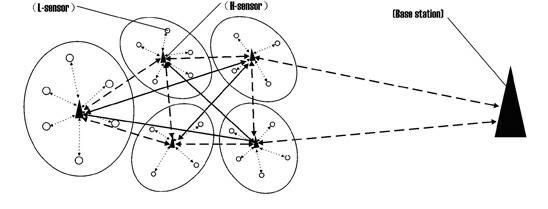
[0034] Step 1: If figure 1 As shown, a three-layer heterogeneous network structure is constructed, that is, all ordinary sensor nodes (L-sensor) constitute the bottom layer of perception, all capable nodes (H-sensor) constitute the advanced cluster head layer for collecting and transmitting information, and the base station (Base station) constitutes the uppermost layer alone;
[0035] Step 2: Generate several t-order symmetric bivariate polynomials on the finite field GF (q) (assuming the polynomials are (q is a large prime number suitable for the length of the key), and the polynomial has the characteristics of g(x, y)=g(y, x), select S randomly from several t-order symmetric bivariate polynomials (embodiment 1: S=10, the number of polynomials pre-allocated by nodes r=4; Example 2: S=15, the number of pol...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com