Fuzzy vault method based on fingerprint features and Internet key exchange protocol
A key exchange protocol, a technology of fuzzy vault, applied in the field of fingerprint fuzzy vault scheme, can solve the problem of loss or theft of storage media
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The present invention will be further described below in conjunction with accompanying drawing.
[0059] 1. The detailed process of shared key binding:
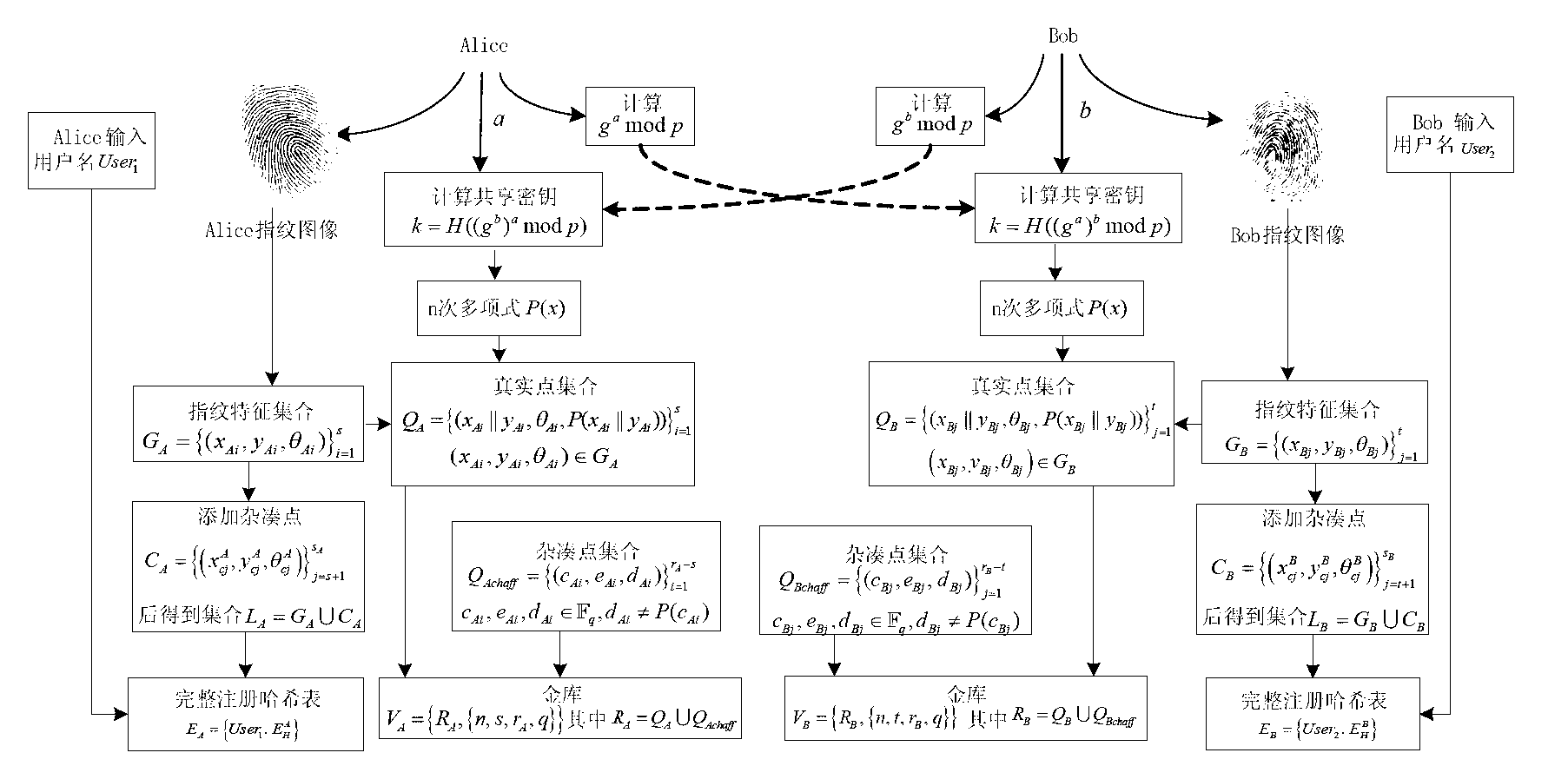
[0060] 1.1. If figure 1 As shown, user 1 Alice and user 2 Bob select a large prime number , and select for multiplying group A generator in . Alice secretly chooses an integer : , and calculate . send to Bob. Bob secretly chooses an integer : , and calculate . send to Alice. Suppose Alice and Bob want to generate a 128-bit shared key. Thus, Alice calculates , Bob calculates , selected is a hash function that generates a 128-bit number. Two users get a shared secret . Alice and Bob respectively input their personal registered user names, denoted as , .
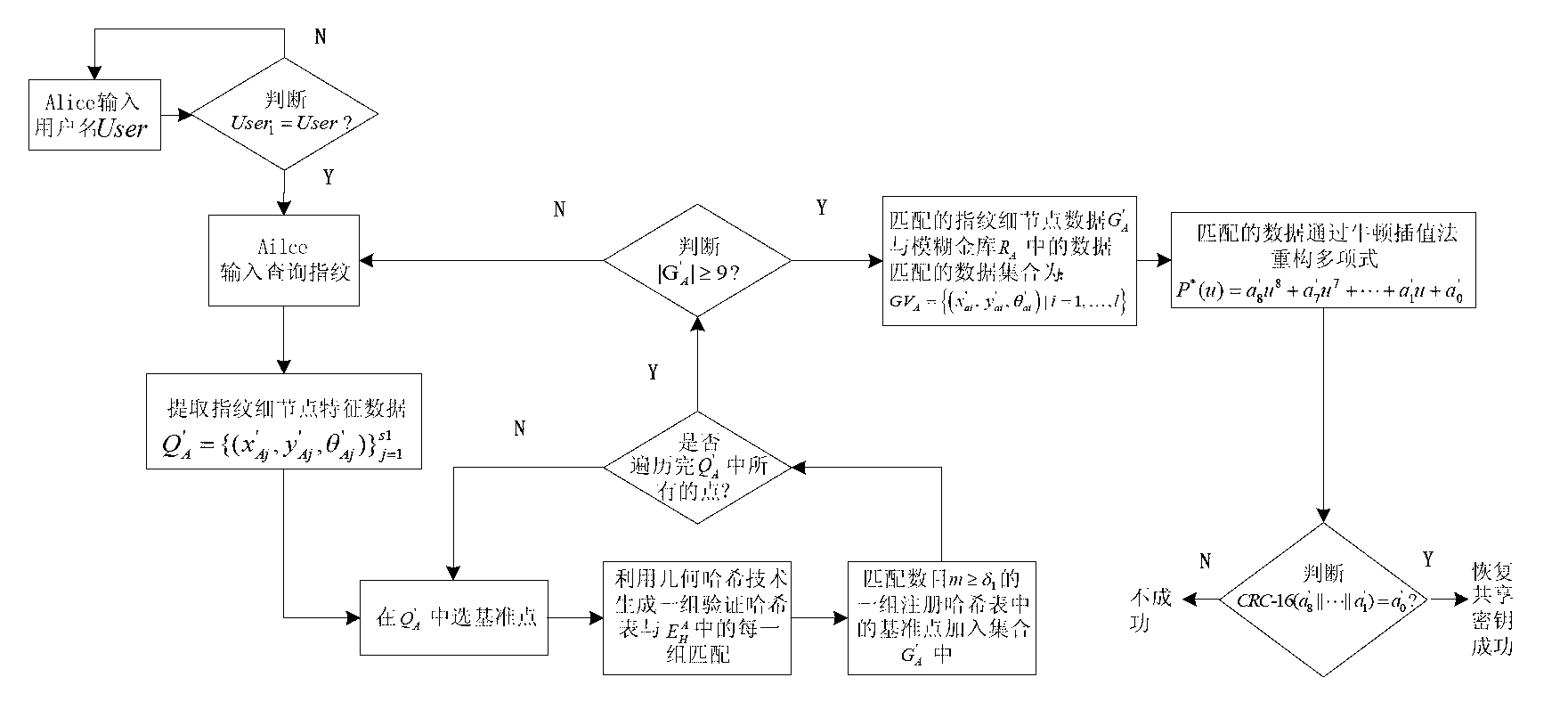
[0061] 1.2. A shared secret is created by the Diffie-Hellman key exchange protocol . The number with a length of 128 bits is used as a coefficient of the polynomial at intervals of 16 bits, and the coefficients of the 1st ord...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com