Method, device and system for negotiating business bearing tunnels
A technology of service bearing and tunneling, which is applied in the transmission system, data exchange through path configuration, electrical components, etc., and can solve the problem of high processing capacity requirements of user equipment and packet gateway equipment, increased message transmission delay, and high equipment cost. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
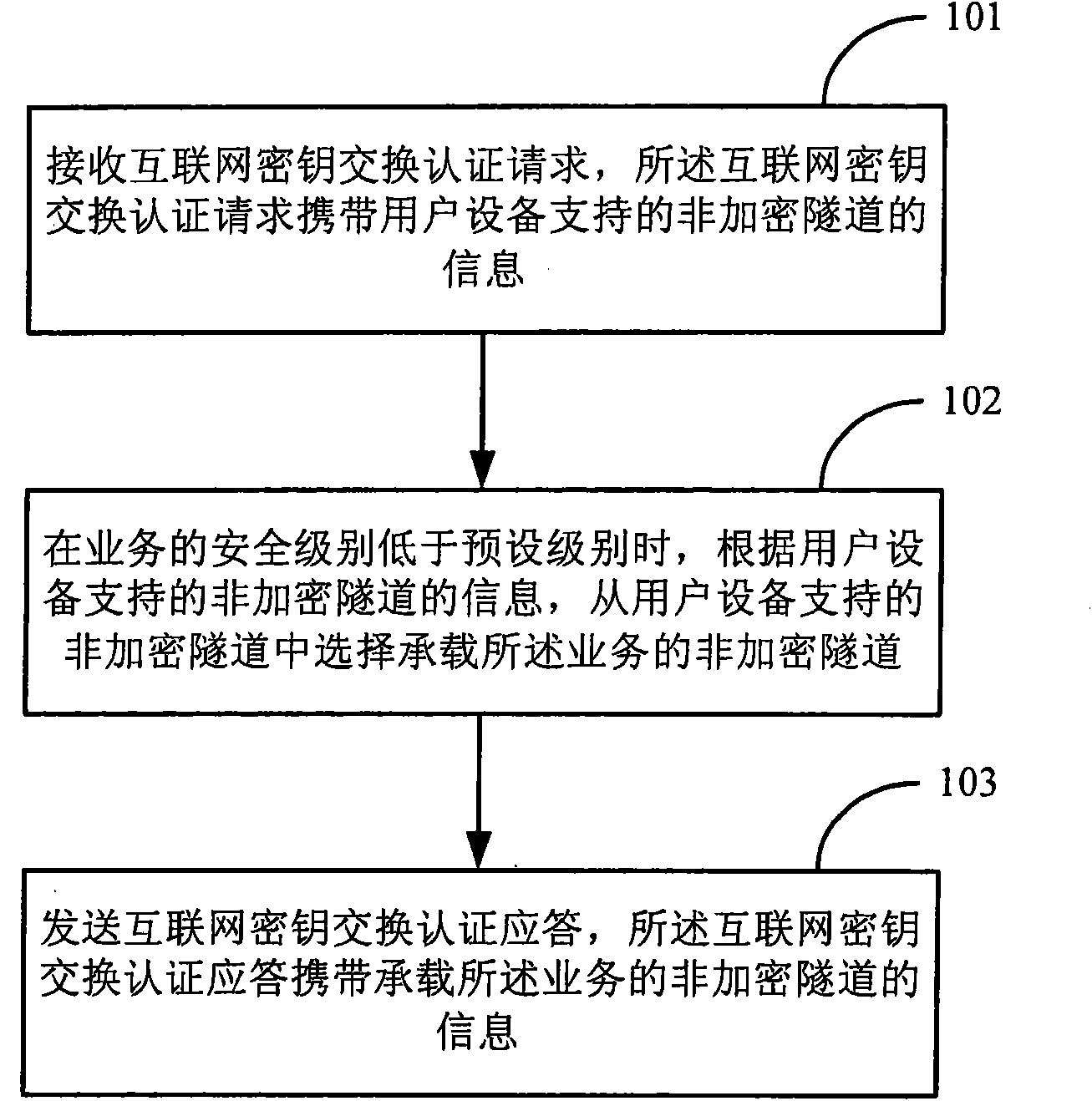
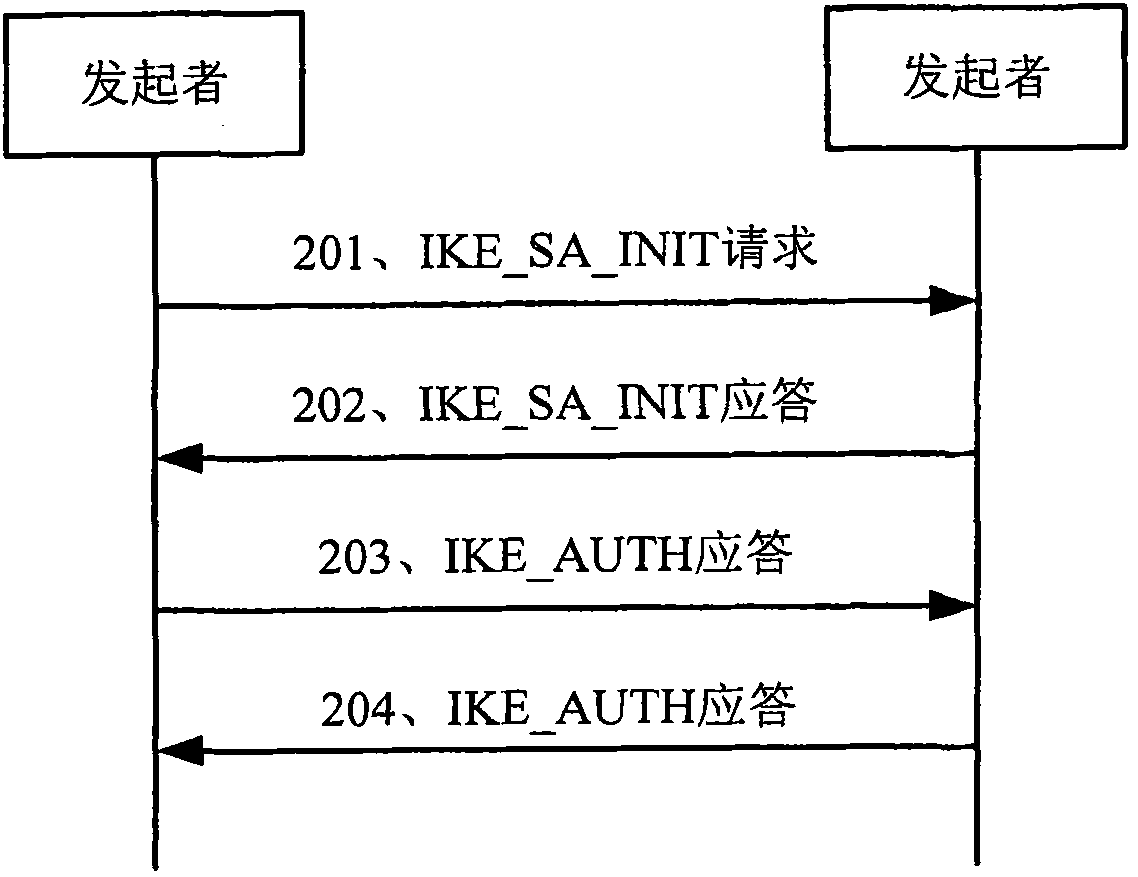
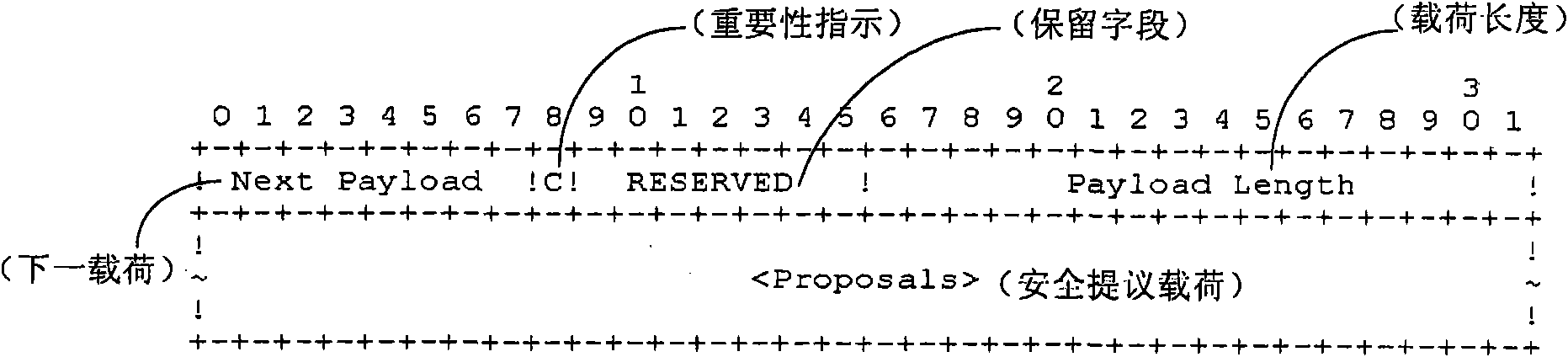
[0046] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention more clear, the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings. Here, the exemplary embodiments and descriptions of the present invention are used to explain the present invention, but not to limit the present invention.
[0047] In actual application scenarios, there are some services with high security requirements, such as the users of these services are enterprise users or these services transmit important data of enterprises, and there are also some services with low security requirements, such as The users of these services are individual users or these services transmit HTTP (Hyper Text Transport Protocol, hypertext transfer protocol) news and entertainment services; when transmitting services with low security requirements, it is unnecessary to perform encryption and decryption p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com