Customizable network identity authentication method based on SM2 algorithm
A network identity and authentication method technology, applied in the field of network identity authentication, can solve problems such as low encryption strength, identity forgery, and threats to information system security, and achieve the effect of protecting security and eliminating the risk of identity forgery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
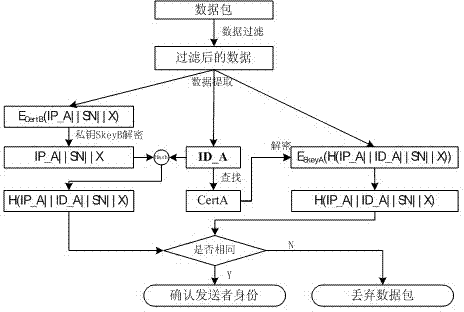
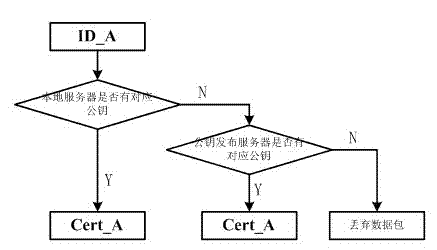
[0043] The invention proposes a self-defining identity authentication method based on the SM2 cipher algorithm, defines the content of the identity authentication data packet, and makes an agreement on the identity authentication process.
[0044] The identity authentication method embodiment that can be customized based on the SM2 cryptographic algorithm of the present invention includes the following parts:
[0045] S1 Entity A sends data packet 1 to entity B;
[0046] S2 Entity B processes data packet 1;
[0047] S3 Entity B sends data packet 2 to entity A;
[0048] S4 Entity A processes data packet 2;
[0049] S5 Entity A sends data packet 3 to entity B;
[0050] S6 Entity B processes data packet 3;
[0051] The present invention achieves the purpose of identity authentication by sending 3 data packets and correspondingly processing the data packets. The communication parties realize identity authentication by sending three identity authentication data packets. The dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com