Applied protection method and device
A technology of protection device and target application, applied in the field of communication systems, can solve the problems of data information leakage and low security reliability of mobile terminals, and achieve the effect of improving security reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
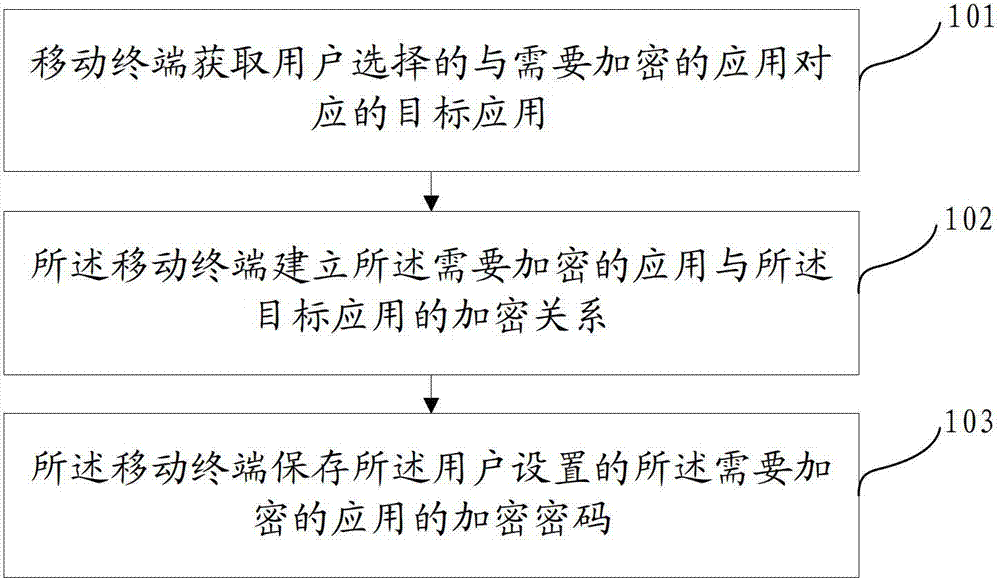
[0022] This embodiment provides an application protection method, such as figure 1 As shown, the method includes:
[0023] 101. The mobile terminal acquires a target application selected by a user and corresponding to an application requiring encryption.
[0024] Wherein, the target application may be pictures, files, music and so on.
[0025] 102. The mobile terminal establishes an encryption relationship between the application requiring encryption and the target application.
[0026] Wherein, the target application cannot be edited or deleted before the encryption relationship between the application requiring encryption and the target application is released, so as to ensure the reliability of the application encryption.
[0027] Furthermore, when the user needs to mark the target application that establishes an encryption relationship with the application that needs to be encrypted in order to strengthen the memory, the mobile terminal can mark the target application th...
Embodiment 2
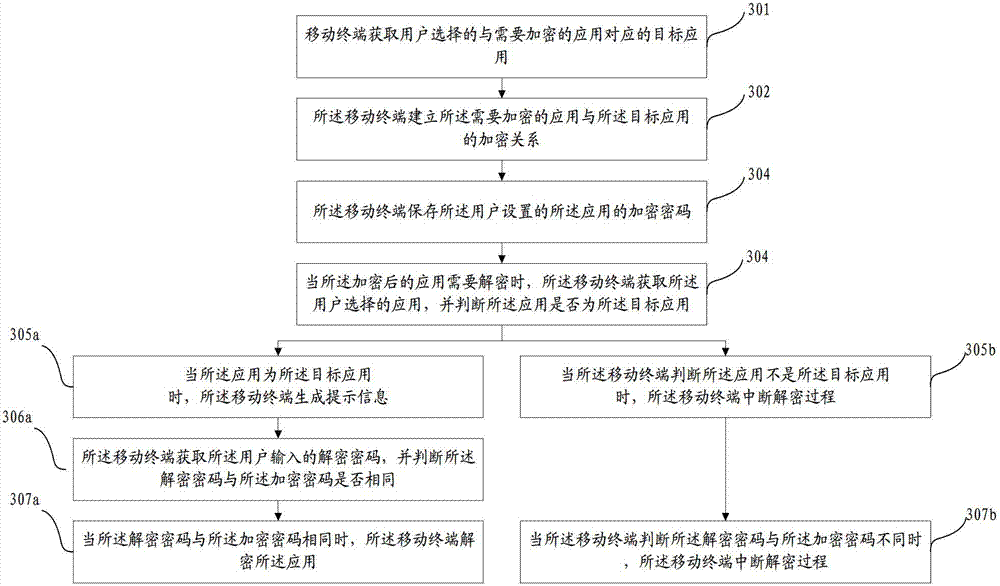
[0040] This embodiment provides an application protection method, such as image 3 As shown, the method includes:
[0041] 301. The mobile terminal acquires a target application selected by a user and corresponding to an application requiring encryption.
[0042] Wherein, the target application may be pictures, files, music and so on.
[0043] 302. The mobile terminal establishes an encryption relationship between the application requiring encryption and the target application.
[0044] Wherein, the target application cannot be edited or deleted before the encryption relationship between the application requiring encryption and the target application is released, so as to ensure the reliability of the application encryption.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com