Vulnerability scanner and its plug-in scheduling method
A vulnerability scanner and vulnerability scanning technology, which is applied in the field of vulnerability scanning, can solve problems such as slow scanning speed, long loading time, and increased hardware cost, and achieve the effect of increasing scanning speed, reducing hardware cost, and reducing memory capacity requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
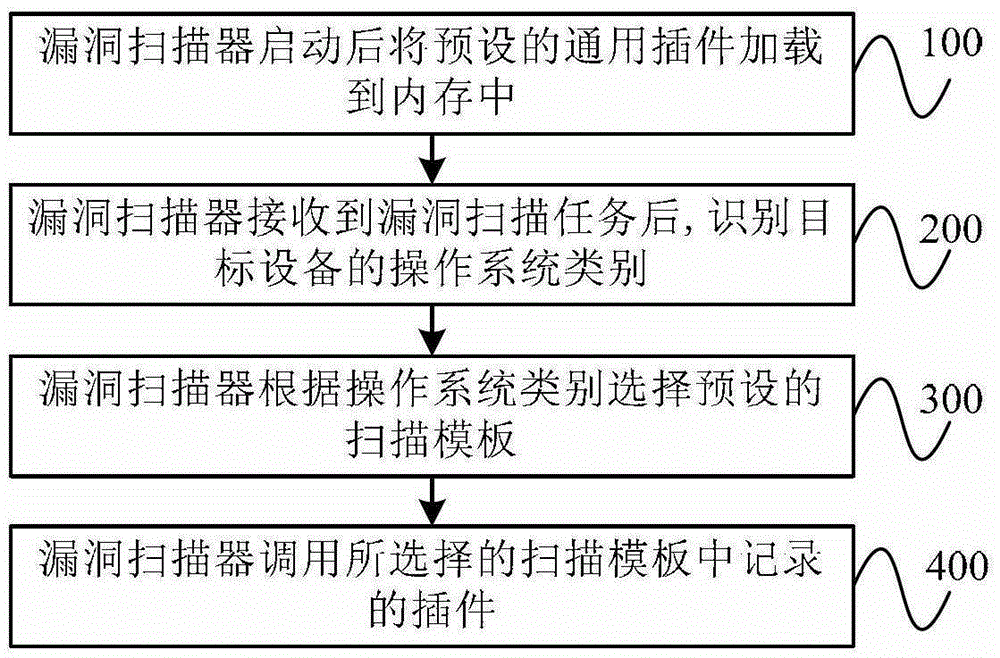
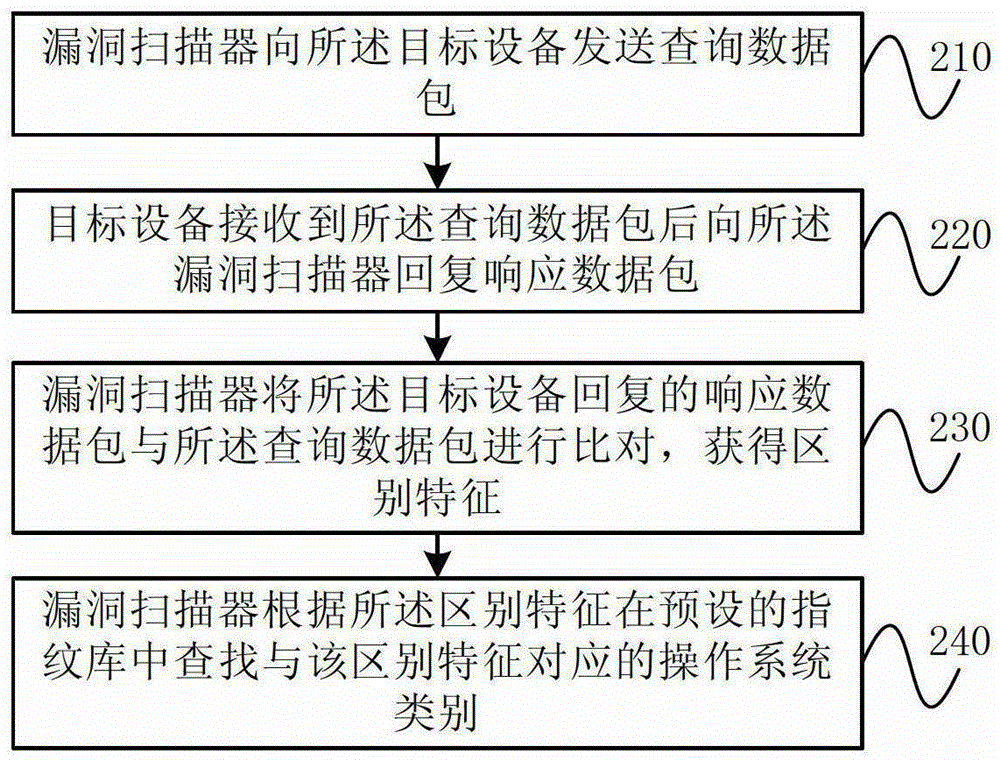
[0022] figure 1 It is a flowchart of an embodiment of a plug-in scheduling method for a vulnerability scanner according to the present invention. As shown in the figure, the method includes the following steps:
[0023] Step 100, after the vulnerability scanner is started, the preset universal plug-in is loaded into the memory.
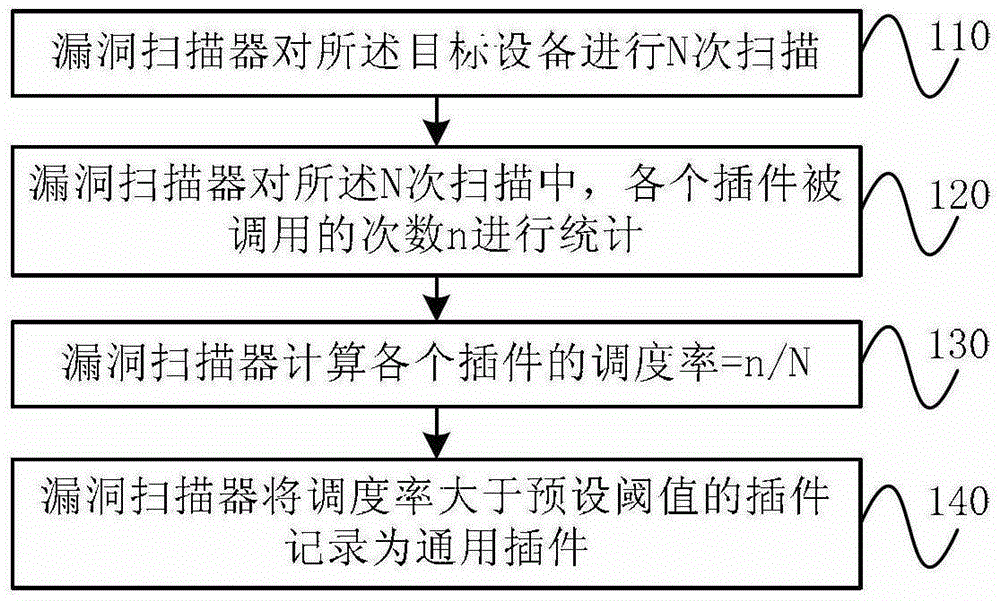
[0024] Wherein, the general-purpose plug-in refers to a plug-in whose scheduling rate is greater than a preset threshold, and the scheduling rate is a ratio obtained after statistics of a large amount of historical experience data of various operating systems, and is used as an attribute parameter of each plug-in to indicate that the How often the plug-in is called when performing a vulnerability scan. For example, if a plug-in's dispatch rate is greater than a preset threshold, it indicates that the plug-in is very likely to be called, so it should be loaded into memory.
[0025] Statistical process about the scheduling rate, such as figure 2 sho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com